Healthcare is one of the critical industries in any environment; the most significant challenge this industry faces is the need to seek specialized assistance and consultation from specialists in different parts of the world (Senbekov et al., 2020). This barrier has led to the frustrations of patients and the underutilization of healthcare professionals. There is a need to develop a system that would be integrated with the existing one to allow patients to visit doctors virtually for proper consultations and diagnosis. The proposed system will be integrated with the existing hospital system to ensure security and compliance with HIPPA laws and regulations since it is a hospital setting.
System Design for an Integrated Secure Virtual Communication Platform
Requirements Gathering
The requirement-gathering phase’s main aim was to develop a system that would assist Healthcare providers and patients in meeting virtually by investigating their needs and expectations. This phase was done by interviewing doctors to determine their needs and challenges when diagnosing patients through the now-available means. Furthermore, patients were interviewed on their needs and challenges when consulting a healthcare provider from long distances, either through phone or video calls.
Design Phase
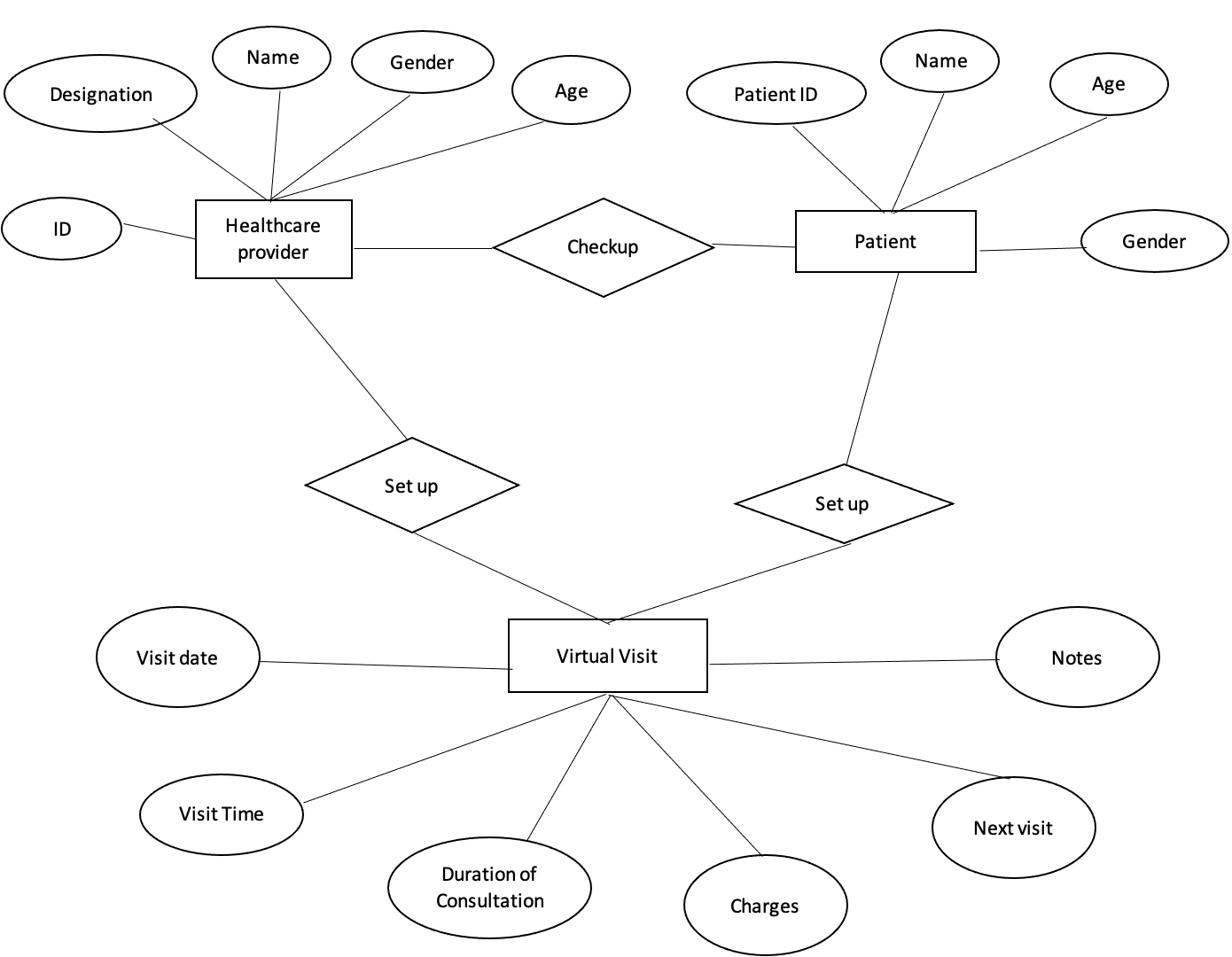
The main entities or stakeholders in the design of this system are patients, IT staff, healthcare providers, Doctors, nurses, and specialists (Samuel et al., 2021), (EdrawMax, 2023). The need for an appropriate design to ensure the system is secure and complies with federal law requirements such as HIPAA and Sarbanes-Oxley
ERD
Data Flow Diagram
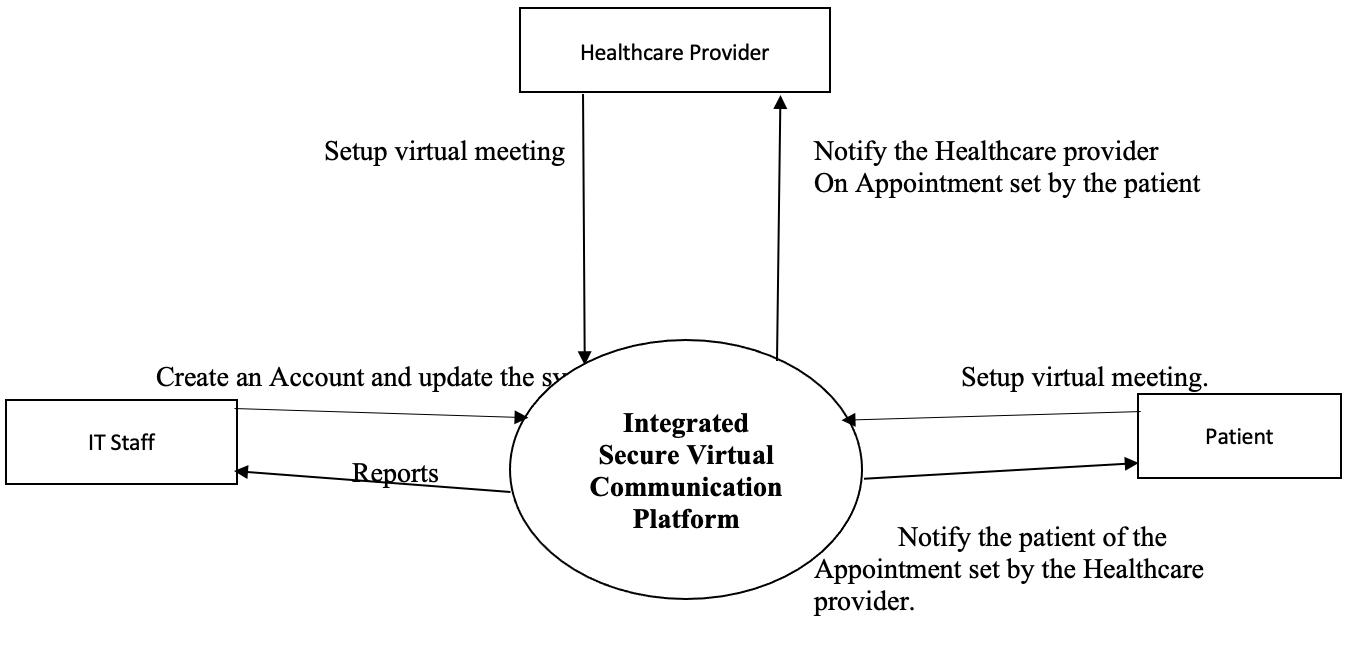
Workflow Analysis and Optimization
The current system only allows patients to visit healthcare practitioners physically, and when there is a need for virtual consultations, Microsoft Team or google meet the application. This was tiresome to the doctor as they needed help to get notifications clearly on the days and times of the Appointment (Kadhim et al., 2020). Furthermore, patients also needed help accessing the virtual meeting applications, and a daily physical meeting was tiresome to healthcare practitioners as they needed to update records regularly.
The new system would be integrated to address these challenges by providing a web portal and mobile applications that could schedule virtual visits and have a notification for regular reminders. The system is set to send automated reminders to healthcare practitioners and patients; it will also allow the patients to key in some of their details and the healthcare practitioners. The virtual system will be directly linked to the hospital’s Electronic Health Records system and allow automatic synchronization and update of the records (Jin et al., 2020). Throughout the integration process, security and HIPPA regulations will be strictly followed; this includes securing the messaging channels between the two parties to ensure confidential information is secured through encryption and secure storage, which automatically ensures compliance with the set HIPPA standards (Senbekov et al., 2020). Furthermore, Authentication through One Time Password and user access control would also be used to secure further the existing and the new system is integrated; this will ensure compliance with HIPAA.
System Implementation
The new system will be coded with the necessary modules to create different functionality and error-reporting environments. Different backend modules would be developed to handle user verification and authentication, data exchange and transfer, and messaging platforms. APIs for real-time video conferencing would be created, and a module to handle security for HIPAA compliance would also be developed accordingly (Senbekov et al., 2020). An environment to handle error detection for proper reporting and handling by IT staff would be created, and they would be able to generate log files for detection and reporting.
Testing
Before installing and adopting the new system and integrating it with the existing one, the developers will do several tests to ensure the system is running as required and is reliable. All functionalities and security needs have been met (Jamil et al., 2020). Unit testing by developers will be done on individual models and components they create independently to ensure effective design has been met. User acceptance testing, which is a critical part of the acceptance of the system by the users, healthcare practitioners, and patients, will be done through the development of test cases (Petersen et al., 2020). This will ensure the system meets the users’ needs, and the feedback generated will be considered before the system goes live and updated by the developers accordingly.
Furthermore, Security testing will be done on the new system before integration to identify possible threats that may leave the system vulnerable. Security Testing also ensures the hospital is compliant with HIPAA and Sarbanes-Oxley law. Lastly, integration testing is critical since we would be connecting the new system with existing systems; this will ensure the new modules work correctly together and the exchange of data and functionalities exchange correctly (Software Testing Help, 2019).
Deployment and Operation
Before the actual deployment, there needs to be a plan in place to manage this process. The planning would begin with identifying the stakeholders and notifying them of your planned installation and when there might be a system downtime. Then you gather all the necessary resources to ensure the implementation process does not fail; when all the above is ready, install and configure the system based on the hospital’s needs and in the appropriate infrastructure. The installation might take some time because it is a lengthy process that will also involve migrating some data from the existing system to the new one; this process needs to be monitored to ensure data integrity and accuracy.
Training should also be done for hospital staff, patients, and IT staff to ensure they get enough knowledge on how to effectively use the system and maintain the security of the system. A user guide and manual should be provided for referral and onboarding of staff. Lastly, after all, this is done, it should be communicated to the board and high-level stakeholders, and necessary documents be handed over to them. This will ensure successful change management.
System Maintenance
This is also a critical aspect in system analysis and design since a system is usually considered to be alive, so it needs to be maintained to ensure it does not fail; it is secure and operational. The secure virtual communication system will be maintained through Regular System monitoring using tools that monitor overall performance, connectivity, responsivity, resources, and response actions. Software updates and patches are also a way of performing maintenance; patches and bugs that arise need to be dealt with once discovered, as explained by a blog for Boston University, 2022. Also, new user requirements will be added to inform of software updates and upgrades to improve system functionalities. Security audits and s security tests are also a form of maintenance that ensure the available security measures can still protect the system and if there is a need to add more security features. This further ensures that the system and organizations comply with HIPAA laws.
Conclusion
System analysis and design is a crucial component in software development and management. Implementing our Integrated Secure Virtual Communication Platform is critical to solving the communication barrier between healthcare providers and Patients who have a challenge in terms of geographical proximity. Integrating the Integrated Secure Virtual Communication Platform will improve patients’ access to specialized treatment and utilize healthcare providers effectively. Using software development methodologies and design gives us a better view of how the system works and how to ensure security and compliance with HIPAA and other regulatory standards.
References
Boston University. (2022). Understanding Patches and Software Updates: TechWeb : Boston University. Www.bu.edu. https://www.bu.edu/tech/support/information-security/security-for-everyone/understanding-patches-and-software-updates/
EdrawMax. (2023). ER Diagrams for Hospital Management System: A Complete Tutorial | Edraw. Edrawsoft. https://www.edrawsoft.com/article/er-diagrams-for-hospital-management-system.html
Jamil, F., Ahmad, S., Iqbal, N., & Kim, D.-H. (2020). Towards a Remote Monitoring of Patient Vital Signs Based on IoT-Based Blockchain Integrity Management Platforms in Smart Hospitals. Sensors, 20(8), 2195. https://doi.org/10.3390/s20082195
Jin, M. X., Kim, S. Y., Miller, L. J., Behari, G., & Correa, R. (2020). Telemedicine: Current Impact on the Future. Cureus, 12(8), e9891. https://doi.org/10.7759/cureus.9891
Kadhim, K. T., Alsahlany, A. M., Wadi, S. M., & Kadhum, H. T. (2020). An Overview of Patient’s Health Status Monitoring System Based on Internet of Things (IoT). Wireless Personal Communications, 114(3), 2235–2262. https://doi.org/10.1007/s11277-020-07474-0
Petersen, F., Jacobs, M., & Pather, S. (2020). Barriers for User Acceptance of Mobile Health Applications for Diabetic Patients: Applying the UTAUT Model. Lecture Notes in Computer Science, 5(9), 61–72. https://doi.org/10.1007/978-3-030-45002-1_6
Samuel, H., Hassan, F., & Zaíane, O. (2021). The Need for Medical Professionals to Join Patients in the Online Health Social Media Discourse. Proceedings of the 14th International Joint Conference on Biomedical Engineering Systems and Technologies, 9(5). https://doi.org/10.5220/0010325806370644
Senbekov, M., Saliev, T., Bukeyeva, Z., Almabayeva, A., Zhanaliyeva, M., Aitenova, N., Toishibekov, Y., & Fakhradiyev, I. (2020). The Recent Progress and Applications of Digital Technologies in Healthcare: A Review. International Journal of Telemedicine and Applications, 2020(1), 1–18. https://doi.org/10.1155/2020/8830200
Shukla, S., George, J. P., Tiwari, K., & Kureethara, J. V. (2022). Data Security. Data Ethics and Challenges, 3(11), 41–59. https://doi.org/10.1007/978-981-19-0752-4_3
Software Testing Help. (2019, December 12). What is Integration Testing (Tutorial with Integration Testing Example). Softwaretestinghelp.com. https://www.softwaretestinghelp.com/what-is-integration-testing/
 write
write