Introduction
In a cyber world that is in a constant state of flux with cyber threats emerging frequently, organizations need to act wisely and have prior identification of and deal with vulnerabilities within their systems, networks, and infrastructure. Along with ethical hacking and penetration testing, organizations rely on these two activities to identify their systems’ robustness, fix possible loopholes, and deploy countermeasures. Ethical hacking is the other way around for cyber defence specialists. They imitate the actual attacks without breaching any laws. Through acquiring the psychology and techniques of criminals, ethical hackers penetrate those places where hackers can obtain data and use it for their benefit, thus enabling organizations to counter threats before the occurrence of attacks.
Ethical hacking and penetration testing cannot be underrated; they offer several pros. First and foremost, these hackers apply myriad tools and approaches that make them excellently equivalent to each other in identifying vulnerabilities in operating systems, applications, networks, and processes. These vulnerabilities span from mistuned systems to bugs and security sloppy practices being used, incorrect password policies, et cetera (Devi & Kumar, 2020). Furthermore, ethical hacking exposes the system’s vulnerabilities for mimicking a probable attack, thus allowing organizations to assess the possible impact of the attempted attack and the likelihood of success beforehand. With this, they can prioritize their security efforts and allocate resources to handle the significant risks.
For instance, many fields and regulating authorities, like the payment card industry data security standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA), demand regular security audits and penetration tests to be conducted. Ethical hacking embodies the organization’s code of conduct and responsibility for maintaining security and abiding by industry standards. Besides, the knowledge and points obtained from ethical hacking activities can be employed for education, making staff and IT specialists well-trained on security matters. The ability to discern actual attack paths and their conceivable aftermaths also serves to sponsor a threat-aware culture within the organization.
Also, ethical hacking involves identifying and removing chances of risk before they are exploited, which causes organizations to take active and preventive measures. Therefore, it is better to be proactive here instead of waiting. The eyes produce more data than the brain can process, increasing the complexity and potential for errors. The goal of this assignment is to examine my ability in this area in penetration testing, vulnerability scanning and security bypass techniques. Precisely, I will hack three VMs undergoing penetration tests, namely Voltron, Magik, and Developer, by the time you have learned to master Metasploit Framework on Kali Linux (Kumar, 2022). This assignment will help me verify whether you can analyze ethical hacking methods using several methods such as enumeration, vulnerability scanning, exploit development and exploitation to attain unauthorized access to a target system.
Furthermore, I will critically examine defence solutions by pinning down the vulnerabilities exploited and give in more detail remedies for vulnerability removal, cause analysis and security improvements to beef up defence systems [For the vulnerable groups, I will examine care service options and policies in different healthcare jurisdictions. The healthcare industry profoundly impacts social justice because it is one of the sectors that is doing this task. Not only will I be able to enjoy the actual practice of security issues like ethical hacking and penetration testing, but I will also train my mind to think objectively when evaluating and remediating mistakes. Cybersecurity specialists employ these to indicate upcoming threats; therefore, the latter cannot achieve cyber-selling objectives for an organization.
Penetration Testing Methodology
Surveillance is the starting point of the ethical hacking process, during which ethical hackers try to scoop all possible information from the client’s network infrastructure. The attack process entails enumerating the attack vectors, acquiring intelligence on the technologies and services adopted, and mapping out the entire infrastructure (Yaacoub et al., 2023). Reconnaissance can encompass, but not be limited to, such tactics as OSINT (open source intelligence), social engineering, and scanning for any vulnerabilities or defects relying on publicly available sources.
Scanning and enumeration are the subsequent phases, during which the ethical hackers try to crack the target system and find the route entry. Often, for these kinds of tasks, one scans using Nmap to find open ports, run services, and figure out the operating system and the type of software used (Kumar, 2022). Also, the vulnerability scanning software is used to find what we know are vulnerabilities that could permit an attacker. The primary purpose of this phase is to develop an integrated compilation of the desired target’s net assault surface while detailing the weak points that are vulnerable to the attack.
The exploitation phase begins after the vulnerabilities have been identified. This is what hackers are designing or re-purposing existing exploits to gain initial access or to escalate the privileges in the target systems. This will likely involve customizing the attack using specific exploits like sniffer, creator of exploit, or even popular frameworks like Metasploit. The aim is to surmount the systems repetitively but in a controlled manner; the methods must be as effective as those of real-life attackers.
After gaining access, strengthening the position and acquiring elevated privileges constitute the post-exploitation stage. In their second stage, ethical hackers pour their efforts into maintaining their footing on the already penetrated systems, carrying out a fresh survey to harness further vulnerabilities or find more sensitive info, and finally fulfilling the primary test’s purpose(s) of techniques that may include uprising privileges, crossing over to the other side for test purposes, obtaining data information or maintaining access for future testing.
Another critical phase is the reporting. This reach phase documents the findings and communicates the results to the client. This report is a significant part of the first part. It summarizes the weaknesses detected, their exploitation methods, and the possible consequences on the organization and its data processing or operations. The action plan also suggests how to achieve the given goal. It also includes steps that will help to improve the current security level of the target machines and networks. Organizing the report formally and fluently with minimum words will be the key to the success of communication and further actions of the organization based on the data.
The structured way of functioning will enable ethical hackers to conclude that an organization is fit to battle the cyber threat; it will help to identify the threat and develop defence mechanisms. In each phase of the process, the next one is based, ending with a general overview of the significant factors and the steps to include in the cybersecurity plan.
Metasploit Framework Overview
Metasploit is an efficient and easy-to-use tool that many cybersecurity experts, ethical hackers, and penetration testers use. Using the Open Source Framework created by Rapid7 as a basis, various security tasks like vulnerability scanning, exploiting the found vulnerabilities, and the post-exploitation process can all be performed with one single tool.
At its core, the Metasploit Framework consists of several vital components that enable its functionality:
Leverages is a medium in which written scripts upfront hack vulnerabilities in an application, operating system, or network. This exploit allows an attacker to intrude on any system, increase the privileges, or even directly execute codes on the target device. Metasploit has a considerable list of exploits from the cyber community, which regards the platforms and applications for the latest conversions and contributions keeping in space with the evolving cyber world.
Payloads are the actual instructions or commands they intentionally insert to take execution on the target system after the exploit that has been used to gain access. The payload can have different configurations. It may be a simple reverse shell that will give me interactive command line access to the shattered system or an advanced payload that can do file transfers and keylogging, or it can even deploy additional malware. The Metasploit allows you to choose from various custom-made payloads for different situations and goals.
Auxiliary modules are usually packed with non-exploit functions such as hardcore scanners, port scanners, and other information-gathering functions. This can incorporate exploitation procedures such as identifying the targets, enumerating the system information, fuzzing the utilities for vulnerabilities, and other pre-exploitation exploits. The support elements are indispensable for intelligence gathering and technology preparation for usage stages.
The Meterpreter is a robust load-adjusting module that gives way to advanced interaction. It is used after an exploitation act. This ensures that many functions are at work, including providing the file systems with browsing, performing remote code execution, collecting keystrokes, capturing screenshots, and a wide range of other options. Meterpreter is flexible and can be customized according to additional scripts and modules, which makes it helpful in building complicated schemes and breaching further access in compromised systems.
The Metasploit Framework considers user structuring via a module-driven architecture, letting users seamlessly add new exploits, payloads and auxiliary modules to the module base as they become available. Due to its modularity, developers can customize their tools to develop single or multiple scripts specific to pen testing scenarios. It undertakes various tasks ranging from detection and inventory to exploiting discovered vulnerabilities. In addition, it acts as a payload shaper for the initial access and privilege escalation. At the final stage of the operation, it assists in achieving an intended objective.
Through the vast database, high universality, and enthusiastic support from the community, Metasploit Framework has become a toolkit that is indispensable for many ethical hackers and security experts to help them test systems and networks for weaknesses and fix problems.
Network Scanning

I was scanning for open ports.
Enumeration/Vulnerability Scanning
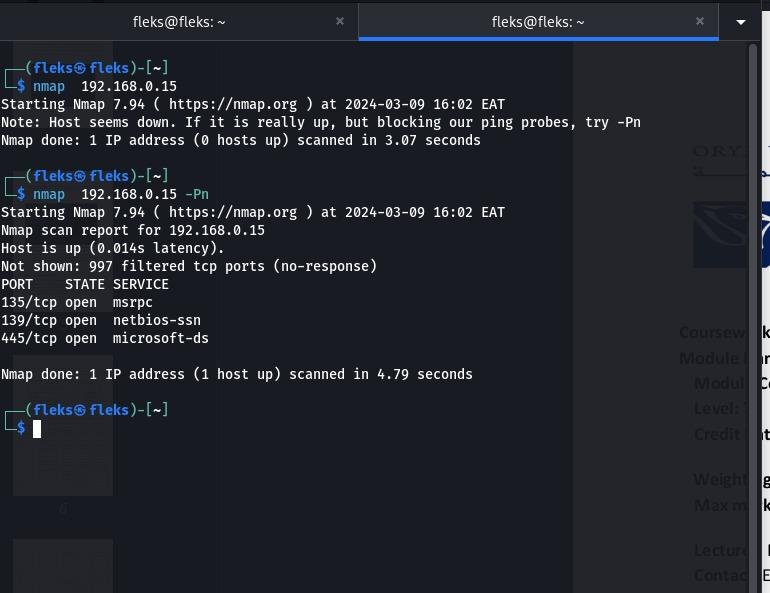
I successfully identified potential vulnerabilities and flaws in the target systems. I scanned the network for vulnerabilities.

Exploit Development
Developing exploits using Metasploit. Successful execution of the exploit,

Successful Exploitation + Privilege Escalation
Shows that I could leverage identified vulnerabilities and execute exploits to gain unauthorized access to the target systems. Successful exploitation and gaining of access

Vulnerability Fix + Recommendations
Fixing vulnerabilities on your network is crucial to maintaining a strong security posture and protecting against potential cyber threats. I Started by conducting regular vulnerability assessments to identify weaknesses in my systems, applications, and network infrastructure. I Utilize vulnerability scanning tools and consult reputable databases to stay informed about the latest known vulnerabilities (Yaacoub et al., 2023). Once vulnerabilities are identified, I prioritize them based on the theoretical risk and impact on their organization.
I apply vendor-provided security patches and updates for high-risk vulnerabilities promptly to eliminate the flaws. Ensure your systems are configured securely by following industry best practices and hardening guidelines specific to your environment. I Implemented robust access controls, enabling only necessary services and restricting access to sensitive resources. Regularly review and update your security policies, procedures, and incident response plans to address newly discovered vulnerabilities effectively. Foster a culture that is security-oriented by providing cyber training to employees. Stress to employees that following security protocols is essential and that every individual should report potential security lapses (Kumar, 2022). Always keep your network under surveillance, tracing any suspicious activity or compromise threats on network security. Crisis management is very critical, and I suggest prevention in advance.
Vulnerability Analysis and Remediation
The generation of extensive vulnerability analysis and the delivery of suitable remedy suggestions are among the principal tasks taken by penetration testing professionals. Through a knowledgeable understanding of the realities of the exploited vulnerabilities, the underlying weaknesses that are the contributors, and the strategies to mitigate them, organizations can build a better security posture for themselves and strengthen the existing defences against potential threats. In this paper, I will show a successful attack exploiting the vulnerabilities of the target virtual machines. It is crucial to analyze every vulnerability for a deeper understanding of the security issues concerned with the system. In conducting this review, great care should be taken to precisely indicate each of these vulnerabilities that the attacker succeeded in breaching the systems (Devi & Kumar, 2020). This may be achieved by referencing available databases such as the Common Vulnerabilities and Exposures (CVE) database and consultation with known security sites with accurate and quality content.
In addition, undertaking this with a root cause analysis that will assist in finding out the deciding factors that resulted in the prevalence of the vulnerabilities is also crucial. Such investigation can bring to light various issues, such as vulnerable code practices, difficult-to-maintain systems, outdated software packages, and weak security controls. With this, one should not fail to check the probability of the violated vulnerabilities affecting the entire organization (Kumar, 2022). This evaluation focuses on data security parameters to address the aspects of facility security, data integrity, and data availability, as well as existing financial damages such as losing money, reputational damage, or non-compliance with the regulations.
Providing a clear, detailed list of all the identified vulnerabilities and the recommended fixes, or in some cases, presentations, is a necessary component of the remediation process. The remediation process comprises the following two steps. The first is to advise respective software vendors on necessary software updates if the vulnerability is related to the older version or if there is any other patching software. Secondly, users should be advised to update to the latest secure version. For the latter case, where such vulnerability inherently stems from the wrong way of system configuration, proper instruction is called for significantly to reconfigure the affected components and thus be free from the vulnerability exposure. When vulnerabilities come from uncovered design flaws or non-secure programming methods, offering a basis for architectural modifications or a method of secure programming is required.
Moreover, sharing the development of notable vulnerability fixes and general security suggestions that can be used to maintain a company’s security is very important, too. The examples go beyond access control implementation and introduce the principle of least privilege into the systems, security monitoring procedures, incident response planning and security-conscious culture reinforcement through member training and awareness.
The implementation of a vulnerability assessment and the provision of a remediation roadmap that also addresses the issues arising during the penetration testing attempt shall safeguard not only the system against the specific vulnerabilities exploited but also enable the organization to increase the level of security throughout its systems. This proactive measure of vulnerability management is essential for scaling up your cybersecurity defence against the multiple types of cyberattacks, which have very high chances of being accelerated today.
Conclusion
I am confident that this penetration test assignment has been very educational and has provided you with significant practical experiences in safer computing and information security. Hack illustrates your ability to perform various steps of the penetration testing lifecycle, for instance, the surveillance, scanning, exploitation, post-exploitation, and reporting phases, by targeting three virtual machines: Voltron, Magik and Developer. While traversing throughout this task, I gained critical skills and knowledge, including but not limited to acquiring through a diverse range of tools and techniques to test the system for various critical soft areas and then developing and implementing those attack methods to gain unauthorized access to a target system. The hands-on experience has stimulated my thinking about what mental framework the miscreants might use and what tactics they are likely to employ. As a result, I can now better predict and squarely deal with the situation.
Moreover, I have critically audited the vulnerabilities exposed during penetration testing through root cause analysis and developed detailed recommendations for vulnerability fixes. Such cognitive ability thus stands above as the critical element in addressing vulnerabilities and enabling the entire security place of the institutions (Yaacoub et al., 2023). Another remarkable aspect of my success was the technical part, which helped me enhance my skills in reporting, giving precise information, and replying to complex technical issues for different audiences. The most important thing is timely reporting and understanding of the activity, as this would lead to an informed decision-making process and the taking of essential security measures. The practical assignment reflects that more than just simulating the events that occur in the real world is required in the IT world. As a result, demanding regular security assessments and penetration testing from industry and regulatory bodies ensures that cybersecurity measures are taken on time. The upkeep of such an effort requires those working in delicate environments to stick with them so that their organizations are deemed trustworthy.
However, With the cyber threat environment chronicling a swift change, it is paramount for organizations to endeavour to choose the reactive approach to enact security measures. Ethical hacking and penetration testing are undoubtedly the best preventive measures that act at their forefront to avoid the possibility of malicious actors taking advantage of the bugs. In constantly keeping up with these advancements, organizations remain ahead of potential risks, alleviate security hazards, and thus increase and improve their cybersecurity. Nevertheless, moral hacking attempts’ lessons and wisdom can be indispensable for adopting a security-aware culture within organizations. By informing stakeholders and users about the different kinds of attack vectors and the possible results, stakeholders and users can see the need for security measures to improve and can recommend better practices more clearly.
A desire to advance my cybersecurity career is planted here in my mind, and I can be assured that the knowledge and skills acquired on ethical hacking, vulnerability assessment, and penetration tests shall serve as a solid foundation for possible future opportunities to sharpen my expertise in these fields of IT security. Staying up-to-date with the latest threats, vulnerabilities, and mitigation techniques will provide adequate security solutions and safeguard organizations against ever-evolving cyber threats.
Bibliography
Devi, R.S. and Kumar, M.M., (2020, June). Testing for security weakness of web applications using ethical hacking. In 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI)(48184) (pp. 354–361). IEEE.https://10.1109/ICOEI48184.2020.9143018.
Kumar, D.S., Yadav, D.R., Kaushik, D.P., Tilak Babu, S.B.G., Dubey, D.R.K. and Subramanian, D.M., 2022. Effective cyber security using IoT to prevent E-threats and hacking during COVID-19. International Journal of Electrical and Electronics Research, 10(2), pp.111-116.https://doi.org/10.37391/IJEER.100210
Yaacoub, J.P.A., Noura, H.N., Salman, O. and Chehab, A., (2023). Ethical hacking for IoT: Security issues, challenges, solutions and recommendations. Internet of Things and Cyber-Physical Systems, 3, pp.280–308.https://doi.org/10.1016/j.iotcps.2023.04.002
 write
write