Introduction
E-Government, also referred to as Digital Government, is a prevalent practice throughout the nation that has the potential to yield advantages for both the government and the general populace. Through production and delivery, Fountain (2004) facilitates the dissemination of information to people who might benefit from it. The internet can serve as a useful resource for locating these sources. During the previous week, an evaluation was conducted on three websites that have proved advantageous to digital government services, namely Data.gov, Benefits.gov, and Digitalgov.gov. The websites above are deemed beneficial resources for individuals seeking pertinent information to meet their needs. This week’s agenda entails a comprehensive examination of Mobile Applications for digital government, focusing on the essential requirements for both the government and the public. Furthermore, assessing the potential hazards associated with utilizing mobile applications and identifying the optimal strategies to mitigate such risks is imperative. Prior to analyzing mobile applications, it is imperative to acknowledge their presence.
The Connected Government Act, enacted in 2018, aims to facilitate the implementation of novel concepts and beneficial applications. The legislation above aims to enhance government services and information availability by mandating the incorporation of mobile-friendly features in all newly developed federal websites (Hassan, 2018). The Act aims to provide assistance to individuals with disabilities and low-income Americans by enabling them to access mobile devices as a resource. In what ways can a mobile application prove beneficial to both the general populace and the governing authorities? Several examples that can be advantageous for both parties include Gov2Go, HIV Care Locator, My TSA, My VolEd Path, and Snap, Send Solve (USA.gov, n.d.). Mobile applications are innovative concepts that provide the public with valuable information and simplify daily routines. Moreover, it fosters a sense of empowerment among the general populace by highlighting the availability of many resources that can be easily accessed through handheld devices. The digital government has implemented websites and mobile applications to assist the public rather than relying on physical searches and in-person inquiries.
Analysis
In order to enhance comprehension of the necessary and suggested measures, it is imperative to establish a robust security framework for the mobile application. In this presentation, I will discuss the necessary specifications and present several security frameworks to enhance our understanding. This section aims to delineate the requisite components of a Federal and Industry outlook on Mobile App Security and the optimal approach for mitigating potential hazards.
From a federal standpoint, there is a significant emphasis on planning, outlining, and strategizing (Vigliarolo, 2018) to ensure that mobile applications operate optimally, efficiently, and securely. However, where should we commence? The rationale behind the Federal government’s stringent requirements and regulations for app security warrants examination. Recently, a dearth of defense mechanisms has resulted in numerous breaches and attacks against the government and the general populace. Given the proliferation of mobile applications, the individuals in question have formulated a strategy to mitigate nefarious behavior within this domain of digital services. The Federal CIO Council and Department of Homeland Security introduced the Mobile Security Reference Architecture (MSRA) in 2013 to aid the Digital Government Strategy (DGS) reduce potential risks on mobile devices and applications. According to the Department of Homeland Security (DHS) in 2013, obtaining a DGS is necessary to effectively obtain and oversee mobile devices, applications, and data intelligently, securely, and cost-effectively.
According to the Department of Homeland Security in 2013, MSRA also guarantees the confidentiality, integrity, and availability of data accessed through a mobile computing solution, ensuring the secure operation of mobile applications. MSRA and DGS are platforms for app developers and business leaders who intend to broaden their reach through mobile applications. In our subject matter, the Federal government’s perspective is establishing guidelines and strategies for individuals or entities developing mobile applications for future use. What are the guidelines and visual representations suggested by the federal government to adhere to? The following is an illustrative representation that can serve as a primary reference point:
Figure 1. Mobile Application Lifecycle Management
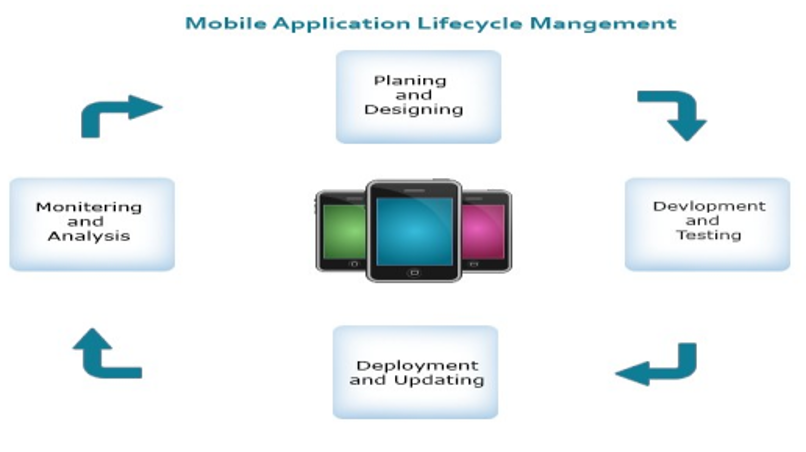
Upon examination of the diagram, it is evident that the Federal Government has granted approval to MAM as a software that enables the application and enforcement of corporate policies on mobile applications, as well as the restriction of sharing corporate data among said applications (Steele, 2018). A diagram is useful for presenting mobile application security as it effectively arranges the key aspects that require emphasis. As per the guidelines provided by the Federal Trade Commission in 2017, it is recommended that an individual be designated with the responsibility of ensuring the security of an application prior to its release. Additionally, it is advised to take inventory of the collected and retained data and implement measures for safeguarding the servers. Additionally, it is imperative to thoroughly test the application multiple times, as many app developers need to pay more attention to this crucial step. The suggestions offer valuable insights for establishing a robust mobile application lifecycle management framework capable of withstanding potential security risks. Thus, the Model-Analysis-Match (MAM) framework is useful for initiating and comprehensively evaluating any concerns related to an application. Mobile Application Management (MAM) is a type of Mobile Security Risk Assessment (MSRA) that has the potential to enhance security measures through its ability to facilitate broad distribution, configuration, data control, and lifecycle management for particular applications that are installed on mobile devices (DHS, 2013).
Figure 2. Mobile application management (MAM) in the mobile lifecycle.
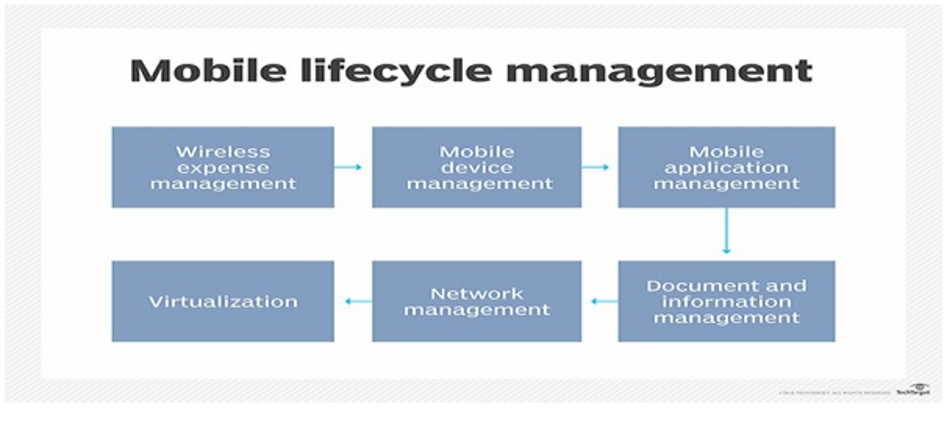
Upon examining the mobile lifecycle depicted in Figure 2, it is evident that each category, commencing with Wireless Expense Management and culminating in Virtualization, necessitates a comprehensive analysis that focuses on security and attentiveness to achieve a successful outcome with the application. During the mobile device management (MDM) stage, the primary emphasis should be on managing applications, data, and configuration settings on mobile devices. According to the Department of Homeland Security (DHS) in 2013, the centralization and optimization of mobile communications’ functionality and security management can be achieved by implementing Mobile Device Management (MDM). According to Vigliarolo (2018), the Federal government suggests that it is more challenging than it appears to establish a security team for each group or team, and therefore recommends that such a team be incorporated from the outset. Employing a security team makes it possible to identify and mitigate any potential vulnerabilities or concerns throughout the mobile application lifecycle, thereby enabling the enhancement of app security. A comprehensive mobile application management framework can be visualized upon the successful completion of all phases in the mobile application lifecycle.
Figure 3. The completed version of MAM.
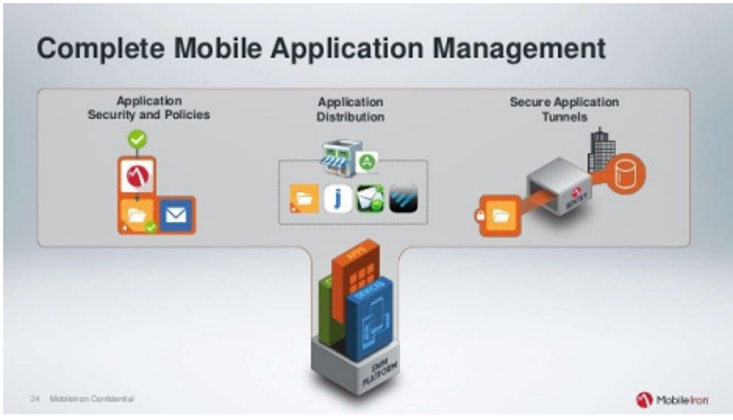
The mere completion of MAM does not ensure the absence of risks. However, potential hazards lie in waiting for an opening when a vulnerability is exposed. What types of risks would it encounter? Various categories of risks may exist, including internal risks stemming from the application and external risks arising from a potential attack. Furthermore, I consider three potential risks to be harmful, namely the collection of personally identifiable information (PII) from either a device or the public, insecure storage of data, and SQL injection. All risks possess the potential to compromise an individual’s privacy and engage in theft. Therefore, implementing robust security measures and policies to prevent malicious activity is imperative.
From an industry standpoint, the focus should be on more than just implementing measures to guarantee a mobile application’s appropriate structure, adequate safeguarding, and security. Rather, it is crucial to acknowledge the underlying objective of the application. In our discussion of the Federal viewpoint on mobile application security, we delved extensively into the technical aspects of mobile applications to ensure their seamless operation and mitigate internal and external risks. Regarding the industry viewpoint, an assessment will be conducted on the Threat model, a methodical approach that commences with a comprehensive system comprehension (OWSAP, 2017). Incorporating the threat model into the system necessitates a concentrated emphasis on several key factors, including the architecture of the mobile application, mobile data, identification of potential threat agents, various methods of attack, and the implementation of appropriate controls. The threat model is also discernible within a Software Development Life Cycle (SDLC) process, which will be expounded upon in a subsequent section.
Figure 4. Mobile Threat Agent Identifiers & Types
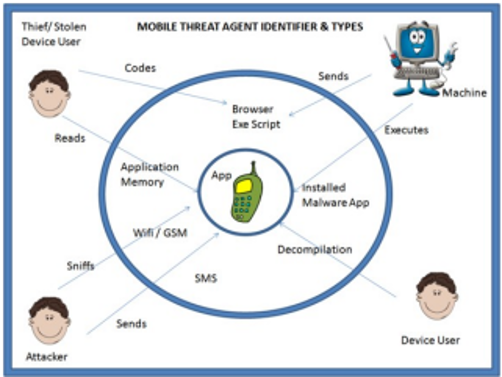
The diagram above depicts the threat model, which encompasses the architecture of mobile applications, mobile data, identification of threat agents, attack methodologies, and corresponding controls. Each process stage delineates its function in the threat model, which I will subsequently identify. The architecture of a mobile application refers to how the system ought to be structured, taking into account device-specific characteristics, wireless transmission protocols, data transmission mediums, interaction with hardware components, and other applications (OWSAP, 2017). The compatibility between the mobile device and the application is a crucial factor in achieving success with the app. The mobile data process encompasses using questionnaires by app developers to ascertain the specific data stored within the application. In developing a game, what is the rationale behind obtaining user contact information, and what is its intended function? The process of identifying threat agents involves the identification of potential sources of harm and the associated risks that an application may encounter. By identifying the threat agent, mobile application developers can comprehensively understand the appropriate security measures to be implemented. This entails a systematic approach to defining the threats relevant to the mobile application (OSWAP, 2017). The utilization of attack methods can aid in identifying prevalent threats and attacks, thereby reducing potential risks (OSWAP, 2017). The system can identify various techniques an assailant employs to access the information. Finally, the controls refer to the measures that must be taken to prevent the occurrence of these risks. The process involves the identification of threat agents and attack methods to determine the necessary controls for preventing potential attacks and threats. The inquiry pertains to the measures implemented for preventing and detecting attacks, reducing the impact of an attack, and safeguarding users’ private information through privacy controls, according to the OWASP report of 2017. The Control phase holds significant importance in threat modeling, enabling the industry to proactively establish security measures and safeguards in anticipation of potential malicious activities.
Figure 5. Attack Workflow
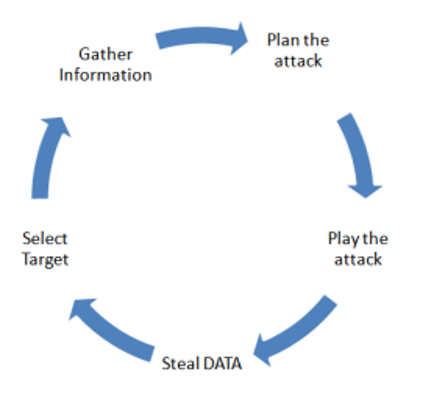
The aforementioned diagram has the potential to be advantageous to the industry as it effectively illustrates the strategic planning and execution of an attacker’s assault. While it may not serve as a risk mitigation measure, it can serve as a point of reference for industries to identify a potential attacker’s modus operandi or strategy. In light of an assailant’s objective to illicitly obtain confidential information about an organization, it is imperative that the industry in question proactively strategizes attack mitigation methods. Per OWSAP (2017), malevolent actors may endeavor to infiltrate a system by utilizing a “Man in the Middle” stratagem, commandeering wireless transmissions, disseminating malware via the application store, and leveraging sundry techniques to exploit the organization. By utilizing the attack workflow diagram as a point of reference, it is imperative to acknowledge the root cause of a successful attack by identifying the exploited vulnerability.
Prior to the occurrence of an attack, the primary objective is to implement controls capable of mitigating risks that may compromise the industry’s security, with a particular emphasis on preventing damage to the mobile application. In this section, the Control stage pertains to recognizing an attack’s primary target and informing the industry and the federal government about potential vulnerabilities. The three primary categories of security controls are Preventative, Detective, and Responsive. The security above has been devised to utilize cyber offenses to inform cyber defense, specifically emphasizing high-yield domains. They aim to ensure that security investments are targeted toward mitigating the most critical threats while maximizing the use of automation to enforce security controls and eliminate the possibility of human errors, as stated by Secureworks (2013).
Figure 6. Mobile App Development.

Upon comprehending the necessary components of the three distinct categories of security controls, an organization can effectively establish the optimal defense or critical control mechanism to mitigate potential attacks. Rather than framing these hazards as attacks, viewing them as security threats to mobile applications is more appropriate. According to a report by Secureworks in 2018, the most significant security risks include unsecured WiFi, apps containing malicious code, vulnerabilities in operating systems, data leaks, and cryptography issues. Implementing targeted security measures, including but not limited to Device security, Malware defense, and Threat intelligence, can yield significant advantages for both the private sector and the federal government. Specifically, developing a comprehensive security strategy capable of ensuring regulatory compliance, mitigating the risk of cyber-attacks, and safeguarding sensitive user information is a key benefit of such measures (Secureworks, 2018).
Best Practice Recommendations
The guidelines above serve as recommendations to be adhered to when enhancing the quality of mobile app development for industrial and federal government purposes. In order to further augment this section, I suggest conducting mobile application penetration testing. According to Secureworks (2013), incorporating White box testing and Black Box testing enables the identification of any possible vulnerabilities, such as inadequate security configurations, unencrypted passwords, or unidentified defects. Two types of testing can be employed to gain insight into an attacker’s ability to exploit vulnerabilities in a mobile application: testing against a knowledgeable attacker and testing against an uninformed attacker. As cybersecurity attacks are constantly evolving, the experts will be better equipped to provide additional recommendations for improvement and devise optimal strategies.
Furthermore, in order to attain exemplary security for a mobile application, it is imperative to conduct simulated attacks to evaluate the security capabilities and limitations of the application, thereby testing for potential vulnerabilities. The present study involves analyzing internal controls and examining code to investigate potential malware and associated risks. The Act of overseeing the application interface and infrastructure to identify any potential security vulnerabilities, enhancing the overall security stance, and devising a practical security strategy with professional advice, has been proposed by Secureworks (2013). Incorporating these recommended best practices entails a responsibility on the part of the organization to safeguard users who obtain the application.
Summary
By implementing optimal methodologies, it is possible to develop a comprehensive approach to mitigate potential hazards and safeguard the confidentiality and integrity of mobile applications offered by the government, industry, and their respective users. As mobile applications continue to develop and evolve, we are presented with an opportunity to safeguard the potential of their capabilities within the current economic landscape. The insufficiency of assistance in online services has resulted in numerous occurrences and violations, leading to an average total expense of $3.62 million for a data breach in 2017. Given the popularity of mobile applications in business, assuming that the economy will not suffer the same harm as the 2017 online security breach did makes sense. Implementing security controls, education, and awareness can reduce the overall cost of a data breach or other incident, limiting the associated risks and threats. It is recommended that both the industry and federal government adhere to these best practices, as doing so may positively impact the global security of mobile applications.
Reference
Baumgärtner, C. (2014). Mobile App Management (MAM) for Developers and IT Administrators. Retrieved from: https://www.slideshare.net/MobileSolutionsDTAG/mobile-app-management-mamfor-developersand-itadministrators Figure 3
DHS. (2013, May 23). Mobile Security Reference Architecture. Retrieved from: https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/1151/2016/10/Mobile-SecurityReference-Architecture.pdf
Fountain, J. (2004). Digital Government and Public Health. Retrieved from: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC1277943/
FTC. (2017). App Developers: Start with Security. Retrieved from: https://www.ftc.gov/tips-advice/business-center/guidance/app-developers-start-security
Hassan, M. (2018). Bipartisan Hassan-Gardner Connected Government Act Signed into Law. Retrieved from: https://www.hassan.senate.gov/news/press-releases/bipartisan-hassangardner-connected-government-act-signed-into-law
OWASP. (2017). OWASP Mobile Security Project. Retrieved from: https://www.owasp.org/index.php/OWASP_Mobile_Security_Project#tab=MThreat_Model_Project Figures 4 and 5
Panacea InfoTech. (2019). Ways How You Can Boost the Quality of Your Mobile App Development. Retrieved from: https://www.panaceatek.com/ways-can-boost-quality-mobile-appdevelopment/
SMC Solutions. (2013). Mobile Application Lifecycle. Retrieved from: http://www.smcsol.com/methodology/mob_app_lifecycle.html Figure 1
Steel, C. (2018, February). Mobile application management (MAM). Retrieved from: https://searchmobilecomputing.techtarget.com/definition/mobile-application-management-MAM Figure 2
USA.gov. (n.d.). Federal Government Mobile Apps Directory. Retrieved from: https://www.usa.gov/mobile-apps
Vigliarolo, B. (2018). How to build a secure mobile app: 10 tips. Retrieved from: https://www.techrepublic.com/article/how-to-build-a-secure-mobile-app-10-tips/
 write
write