A Brief Overview Including Relevance and Significance:
The modern world is grappling with increasing cybersecurity attacks, with experts calling for implementing cutting-edge defense mechanisms to combat the threats. A notable case of how Malware can adversely impact an organization is the recent attack on Etisalat, Emirates Telecommunication Group Company. The Lockbit group-led attack shows the need to develop innovative and effective solutions to counter Malware’s relentless evolution. The research’s primary goal is to evaluate Artificial Intelligence’s potential to utilize malware behavior analysis functionalities to address modern cybersecurity threats. The research is inspired by real-life scenarios like the Lockbit attack on Etisalat to analyze the contemporary malware attack mechanics and introduce an AI-driven method that will help address malware attacks and other cybersecurity threats. An in-depth investigation of recent events in the United Arab Emirates, like the Etisalat malware attack, will help the researcher understand the cybercriminals underlying tactics, including zero-day vulnerabilities and social engineering methods used. The Etisalat case offers a detailed insight into various ways malware attacks occur and why organizations globally struggle to contain them.
The research will meet its objectives by proposing an AI-driven behavior analysis and detection solution. The proposed solution will leverage modern innovations like machine learning algorithms and Big Data to identify malicious activity patterns. The approach will help with emerging threat prediction and interception before organizations and governments in the United Arab Emirates are exposed and adversely harmed. The research will utilize datasets with malicious and begnin codes to train the developed models to enhance the solution’s effectiveness and accuracy. Collaboration and coordination with cybersecurity experts, various sector stakeholders, and government levels can help refine the research methodology and validate the designed solution. A well-thought-out project plan covering eighteen months will help meet key milestones.
Relevance and Significance:
The research is highly significant and relevant in the modern administrative and business environment grappling with cybersecurity challenges, especially malware attacks. Firstly, the research aims to address the urgent need in the United Arab Emirates that is plaguing both the government and its various units and profit-making and non-profit making organizations. Cybersecurity threats have become sophisticated and increased in frequency, with organizations urgently searching for innovative defensive strategies and tactics to secure themselves from malicious actors (Demetrio et al., 2022). Secondly, the research will significantly contribute to the existing knowledge gaps. The cybersecurity field has enjoyed immense progress in recent years. However, many malware behavior analysis methods and approaches need to be properly understood. Thus, more research is needed to ensure further discovery (Poudyal & Dasgupta, 2020). Thirdly, the research will contribute to enhancing public safety. Cybersecurity threats undermine public safety, with the research helping minimize reputational damage, data theft risk, and financial losses. Fourth, the implementation of the research findings can help spur economic growth. The result intends to help organizations improve their cybersecurity practices, resulting in enhanced trust in digital transactions and processes. This can facilitate innovation in the region irrespective of the sector and encourage economic growth. The research can bridge the gap between interdisciplinary divides in the United Arab Emirates and globally. The research will help combine expertise from various security domains, mathematics, and computer science, ensuring ideas cross-pollination and improving research experience. Lastly, the research can promote breakthroughs in cybersecurity and AI because it explores and highlights their intersection. The research aims to introduce actionable insights. It will equip policymakers and other stakeholders with the tools and techniques to anticipate and defend against malware attacks. The research will also contribute to the existing discourse concerning the intersection between cybersecurity, its components, and Artificial Intelligence.
The Research Scope and Objectives:
The research scope and objective are exploring artificial intelligence technologies and analysis to enhance malware behavior analysis. The research will utilize recent high-profile events to evaluate modern malware threats. It will analyze the recent techniques and trends that cyber criminals use, whether individuals or organizations, such as zero-day vulnerability and social engineering. The research also aims to design an innovative solution utilizing artificial intelligence to prevent and detect Malware with the system proposed and developed to respond effectively to current advanced threats. The research will utilize large data sets for AI model training, helping the proposed solution recognize patterns and situations that indicate the potential presence of malicious activity. Engaging industry experts and other stakeholders helps validate the proposed solution’s efficacy. The research will also leverage cloud computing infrastructure, helping with data storage and processing and ensuring peer collaboration. Performance metrics evaluation will measure the proposed model’s effectiveness and efficiency with comparisons made to conventional and alternative models. The research intends to produce comprehensive technical and non-technical reports showing the findings and offering insight to various stakeholders, including practitioners, policymakers, and the scholars’ community. Lastly, the thesis will be submitted with the work successfully defended. Therefore, the research intends to enhance knowledge concerning AI-driven malware behavior analysis and help improve the capacity of the United Arab Emirates region to combat the growing Malware and cybersecurity threat. Therefore, its outcome benefits all stakeholders, including the industry, governmental units, academia, and the general public. It aims to help foster a resilience and innovative culture to improve ways to combat the growing cybersecurity threat.
Problem Statement:
The Issues that the Research Intends to Solve:
The research aims to deal with the challenge facing the United Arab Emirates region concerning Malware’s increased frequency and sophistication. The problem has proven to be a critical challenge with the region and the world grappling with addressing the ever-evolving malware threat. Real-life scenarios and expert analysis have demonstrated that conventional approaches are inadequate for advanced threat detection, anticipation, and prevention. The inadequacy of conventional means has resulted in reputational damage, financial losses, and data breaches. Therefore, the region is yearning for an innovative solution to help the region’s organizations, individuals, and governmental units with malware threat anticipation, identification, and neutralization, avoiding harm. The current approaches make it challenging for players to understand malware behavior analysis. Therefore, introducing an AI-driven malware behavior analysis solution can address the existing gaps and improve cybersecurity practices (Mathane & Lakshmi, 2021). It will also serve as a foundation and framework that can be improved upon by subsequent studies. The innovative solution will leverage modern approaches, including large data sets and machine learning algorithms. Therefore, the research will strengthen digital networks and systems resilience. The challenge facing the United Arab Emirates and the world is significant when highlighted within the context of real-world applications and current literature. The real-world scenarios, including that of Etisalat and consistent attacks on government infrastructure, show that innovative solutions are urgently needed to promote infrastructure and network security, encourage economic growth, and promote public safety.
The Problem’s Importance within the Real World and Existing Literature Context:
The problem’s importance can be emphasized by looking at one of the recent malware attack cases in the United Arab Emirates. Etisalat is the world’s 18th largest mobile network company and a UAE state-owned telecom giant. Therefore, the recent malware attack is consequential because of its risk to the mobile network operator giant, the millions of subscribers it serves, and those who rely on the state-owned organization’s services. On February 6, 2024, a Lockbit executed ransomware and uploaded sensitive files that were Etisalat-owned on its website. The criminals wanted $100,000 from anyone interested in downloading the sensitive data (Jain, 2024). The company hesitated to respond or confirm the attack, leaving millions of stakeholders and subscribers uncertain. The incident showed that even the most sophisticated organizations in the United Arab Emirates are not protected from malware attacks, demonstrating the growing challenge of cybersecurity threats.
The Etisalat situation shows that the research problem represents important issues because of the growing frequency and complexity of malware attacks. Malware attacks threaten individual privacy, economic stability and prosperity, and national interests (Smith et al., 2020). The inadequacy of the existing defense mechanisms and practices means that unless effective and innovative solutions such as the AI-drive malware behavior analysis model are implemented, organizations will be exposed to many threats, resulting in costly financial and non-financial damages. The research aims to leverage technology to develop an AI-driven solution to mitigate and anticipate current and emerging Malware. Therefore, the research demonstrates great potential to help protect individuals and organizations from the ever-evolving cybersecurity threat.
Preliminary Project Plan Outlining the Thesis Key Milestone and Activities:
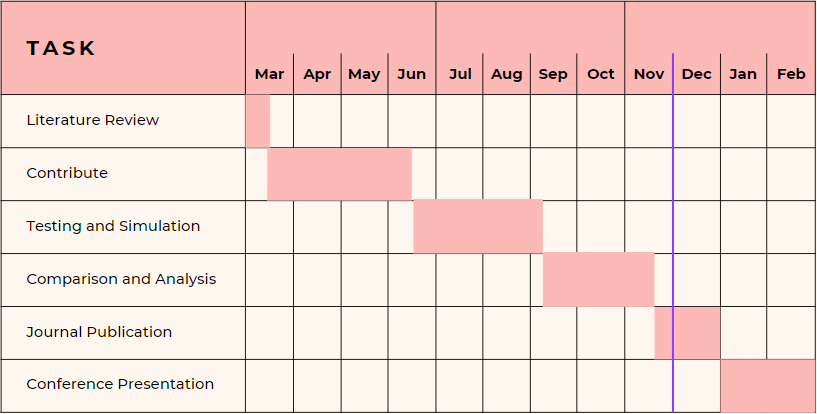
| Milestone | Task or Activity | Time-Frame |
| Background and Literature Review | Perform a detailed literature review that analyzes existing methods and techniques concerning AI-driven malware analysis.
Contributing novel frameworks evaluation and relevant case studies analysis Latest AI-driven malware analysis advances with deep learning and machine learning algorism analyzed Opportunities and gaps identification to enhance malware analysis |
27th Feb-15th March 2024 |
| Contribute | AI-driven malware analysis concept and framework development. This should performed based on the opportunities, areas of improvement, and gaps identified
Data sets, deep learning, and machine learning algorithms integration. Intended to develop an effective framework The developed framework should be accessible and user-friendly |
16th March-16 June 2024 |
| Simulation and testing | Simulate different scenarios aiming to test the concept’s efficacy. The phase will use benchmark data sets for the developed framework validation.
The developed framework performance measurement against the determined metrics. These metrics include recall, precision, and positive rate. Framework optimization and streamlining to minimize errors and enhance its performance capability |
17th June-17th September |
| Comparison and analysis against the current techniques and concepts | An in-depth comparison between the existing approaches to malware anticipation and detection and the established framework is performed. Aimed at evaluating weaknesses, strengths, and opportunities for improvement
Understanding the proposed framework differentiators and unique value proposition Determining enhancement and improvement areas |
20th September -18th November 2024 |
| Journal Submission | Findings published in a reputable and well-known scientific journal database. Intended to ensure that the wider community can access the research
Disseminating the findings from the work done to various stakeholders, especially policymakers, practitioners, and the academic world |
25th November to 31st December 2024 |
| Conference presentation | Using conferences and seminars to share the overall process findings and gather important feedback from experts and other parties
Having peer conversations and networking to gain more in-depth insight into emerging and current AI-driven trends can help improve the framework based on opportunities identified relationship strengthening to facilitate and allow future engagements and collaborations |
1st January- 1st March 2025 |
Research Methods and Materials to be used:
The research methods and materials will include a systematic literature review, experimental design, data collection, expert interviews about Malware and AI-driven technologies, software engineering practices, and algorithm development. The systematic literature review is intended to help analyze existing methods and techniques concerning AI-driven malware. The research will utilize scientific databases such as IEEE Explore, arXiv, Google Scholar, ProQuest, and ACM digital library to search and access relevant publications. Expert interviews will help collaborate with well-known and reputable cybersecurity and Artificial Intelligence researchers to gain professional insights and expert opinions. A well-designed data collection approach will help validate and test the proposed solution. The research also intends to utilize controlled experiments to compare the proposed solution to address malware challenges with the existing concepts and techniques. The experimental design will help evaluate the proposed solution’s performance using critical metrics. Software engineering practices will help manage the proposed solution development lifecycle effectively.
Conclusion:
AI-driven malware behavior analysis solutions can help address the current malware threat facing the United Arab Emirates governmental units, non-profit and profit-making organizations, and the general public. The study uses technological developments, including Artificial Intelligence and machine learning, to develop an AI-driven behavior analysis solution. The proposed solution will help anticipate and predict the potential presence of Malware, enhancing the detection and prevention processes. The proposed solution will contribute to a safer digital environment in the United Arab Emirates.
References
Demetrio, L., Coull, S. E., Biggio, B., Lagorio, G., Armando, A., & Roli, F. (2021). Adversarial examples: A survey and experimental evaluation of practical attacks on machine learning for Windows malware detection. ACM Transactions on Privacy and Security (TOPS), 24(4), 1-31.
Smith, M. R., Johnson, N. T., Ingram, J. B., Carbajal, A. J., Haus, B. I., Domschot, E., … & Kegelmeyer, W. P. (2020, November). Mind the gap: On bridging the semantic gap between machine learning and malware analysis, in Proceedings of the 13th ACM Workshop on Artificial Intelligence and Security (pp. 49-60).
Mathane, V., & Lakshmi, P. V. (2021). Predictive analysis of ransomware attacks using context-aware AI in IoT systems—International Journal of Advanced Computer Science and Applications, 12(4).
Jain, S. (2024). UAE Telecom Giant ETISALAT Hit by LockBit, $100K Demanded for Data Release. The Cyber Express. https://thecyberexpress.com/cyberattack-on-etisalat-lockbit-demands-ransom/
Poudyal, S., & Dasgupta, D. (2020, December). AI-powered ransomware detection framework. In 2020 IEEE Symposium Series on Computational Intelligence (SSCI) (pp. 1154-1161). IEEE.
Appendix: Project Plan
 write
write