Introduction
Limetree Inc., one of the known firms in research and development, has created a place for itself in the competitive markets of biotechnology and health care, working closely with the federal government and several private companies. The vigorous growth of this dynamic organization and the increasing complexity of its operations have, in turn, escalated its exposure to information security vulnerabilities. The organization is dedicated to maintaining a strong information security framework, as noted by its measures to monitor compliance with relevant regulations and protect sensitive data, including personal health information (PHI) important to its research programs. However, recent breaches in security brought into sharp focus potential flaws in the system and processes that require full-fledged evaluation and fine-tuning of its information security posture.
In its internal architecture, Limetree Inc. implements an open concept plan that includes workspace areas without partitions and separated only by glass, with locking cabinets available for keeping personal and business materials. This arrangement, however, needs to be revised to keep the physical safety and integrity of information. Jack Sterling, Security Manager, commented, “The technical landscape seems to be a mishmash of advanced technologies and considerable gaps in the practices of security, such as inadequate settings of browser security, no encryption of sensitive data at rest, and, more generally, a dearth of comprehensive security policies and protocols for incident response. These lay the foundation for conducting a critical analysis into the security breach that Limetree Inc. has succumbed to, not only to identify the origins of the breach but to devise strategic ways of averting its reoccurrence so that continued growth can be secured for the firm and so that protection of its valuable research contributions may be secured as well.
Security Breach
Attack Location
The latest security breach that had taken place at Limetree Inc. struck at the heart of the company’s operations: the databases holding personal health information (PHI) and confidential company data. This is a conscious attack aimed at the critical data resources of Limetree Inc. and is another demonstration of a strategic one right at the company’s core asset—its research data. The sophistication of the attack and the choice of target reveal calculated intent to undermine operational integrity in the company and the theft of sensitive information—information that forms the backbone of research projects in healthcare and biotechnology at Limetree Inc. It is not an opportunistic ‘smash and grab’ cyber attack on peripheral corporate IT assets but an insidious penetration of the company’s crown jewel digital repositories (Farid et al., 2023). An attack of that nature not only jeopardizes the confidentiality and integrity of critical data but also poses significant threats to the reputation of the company, its competitive edge, and compliance with data protection regulations.
Attack Method and Type
The manner and type of attack launched against Limetree Inc. were carefully prepared and carried through, working on definite holes within its IT infrastructure. So, the attackers used phishing in combination with deploying malware, passing through these low-security configurations of the MS Edge browser used in the organization and allowing them to effectively bypass this and gain unauthorized access to the company network. Phishing was used to target the employees of the organization in order to get their credentials or innocently install malware onto their gadgets. Meanwhile, the security vulnerabilities in the browser were exploited to remotely deploy malware applets. This coordinated attack strategy, therefore, not only underscores the technical prowess that is evidenced on the part of the attackers but also underscores the critical vulnerabilities that exist within Limetree Inc.’s cybersecurity defenses—with particular attention being paid to the lack of robust browser security settings and a definitive lack of employee awareness and training about cybersecurity threats. The first point of exploitation was the poor security settings of the MS Edge browser that were set with minimum protection, thus enabling the remote installation of malicious applets.
Vulnerabilities
The initial vulnerability that allowed an opening into Limetree Inc. was networks, putting the integrity relative to the systems and data at risk (Alshaikh et al., 2023). To compound the breach, there was a lack of network segmentation and wireless LAN to wired LAN authentication. The wrong segmentation was the root of the spread of an unauthorized backdoor over the network, which made it much easier for the attackers to move quickly and penetrate the sensitive parts of the IT infrastructure. The SQL database was an outstanding target of the attack because it stored unencrypted information, mainly personal health information (PHI) (Lali & Chakor, 2023). Such was identified as one of the significant vulnerabilities that directly permitted the compromise of confidential data in its at-rest environment within the server environment. Identified as a vulnerable condition from the breach, these are some of the results of the incident response work.
If it was a revelation of the technical weaknesses in its cybersecurity walls for Limetree Inc., it was an eye-opener as to some major security policy and practice holes within the organization. It is due to the lack of a documented security policy, computer use policy, and formal incident response plan that the organization needs to prepare to detect, respond, and recover from the breach (Alshaikh et al., 2023). This unpreparedness impeded Limetree Inc. in adequately managing the incident and preventing its consequences. Moreover, the discovery came about the need for more security awareness among the employees and the absence of regular security training. This human factor vulnerability contributed significantly to the success of the breach since employees were not likely to notice or appropriately respond to the adversaries’ attempts at phishing or other social engineering attacks. The combined effect of such vulnerabilities, apart from facilitating the breach, also amplified its effect, thus compromising both the security and privacy of assets held by Limetree Inc. and further exposing the organization to a whole range of operational, reputational, and regulatory risks of high nature.
Incident Response
Purpose
The main reason for an incident response plan is to constitute a methodical, systematic approach to dealing with the aftermath following any security breach or cyber attack. The objective is to lessen the impact on the company, minimize the time and cost of recovery, and reduce the chances of the same incident occurring in the future. An effective incident response plan is supposed to cover not only the immediate threats but also the overall security posture of the organization. In Limetree Inc.’s case, developing a wholesome incident response plan is crucial (Shinde & Kulkarni, 2021). This is the preparedness plan to quickly and efficiently act against security incidents, thus keeping the company’s assets, reputation, and stakeholders’ trust unspoiled.
Examples
Phishing attacks present one of the security incidents Limetree Inc. has to be ready to face. This can include various forms, such as email phishing, where the attackers aim to receive sensitive information through a fraudulent email. Another form is spear phishing, where the targets are specific individuals of the organization, and thus, it tricks them into giving out confidential data (Jain & Gupta, 2022) and setting up a rogue Wi-Fi network with Wi-Fi evil twin, duping employees to connect to the evil twin and compromise their credentials. Redirect the victims to the malicious websites through pharming, which, in all fairness, are typed in the correct order. Finally, vishing uses telephone calls in order to retrieve sensitive information by pretending to be some legal body. These examples highlight the diverse character of the threats Limetree Inc. is exposed to and, thus, the necessity for a robust incident response mechanism (Alkhalil et al., 2021).
Roles and Responsibilities
One of the critical factors in an effective response to a security incident is a clear definition of roles and responsibilities. Within the organization of Limetree Inc., this involves the Security Manager, Jack Sterling, whose role is to oversee overall security strategy and incident response. The Chief Information Officer (CIO) defines the way forward with respect to security in the company’s IT infrastructure while considering business goals. The Systems and Network Administrators are the point of implementation of measures and responses for the technical part. Meanwhile, department heads and human resources are engaged in ensuring compliance with the security policy and cross-communicating in the organization (Whitman & Mattord, 2021). This joint effort of these stakeholders is intended to address security incidents and work on alleviation, which makes evident the joint responsibility in ensuring security for the company’s digital assets.
Current Incident Response Process
The present incident response process is highly flawed in its capability to handle and fend off security breaches. A standardized, formalized incident response framework is necessary for the company to be safe, as it is the procedure that defines the identification, analysis, and handling of the security incident. The absence of such a framework means that the incident management is ad hoc, with responses being late and not coordinated, leading to further escalation of the impacts of the breaches. On the other hand, no documented procedures exist on how incidents should be reported and escalated; hence, the communication with respective stakeholders is very inconsistent. As such, this inefficient incident response process weakens the security posture at Limetree Inc.
Actions
When the security breach occurred, the security manager took a number of remedial actions that aimed to mitigate the effect of the breach attack. However, the lack of a well-documented incident response plan resulted in a seemingly disjointed and possibly inefficient response. The specific actions taken were not detailed, implying that they might have been more reactive than proactive in handling an incident. This may involve an immediate reaction to contain and mitigate but may not include a strategic plan to enhance overall security. The lack of an articulated response strategy might have watered down the effectiveness of these actions by not being able to have any actual response about the underlying vulnerabilities and to prevent further breaches in the future. These approaches underline the requirement of structured and systematic incident response, which is not limited to immediate actions but also bears a strategic response for enhancing the organization’s overall security framework.
Business Continuity
Additionally, incident response actions that Limetree Inc. executed after the breach compromise indicated major gaps in the company’s ability to ensure the continuity of business. All the reactive measures taken did not aid in facilitating a quick resumption of normal operation. If incidents like this are not backed by a clear incident response and business continuity plan, then the system might probably be exposed to prolonged systems downtime, operational disturbances, and maybe even financial losses. Whether these are effective in supporting business continuity or not remains vague, so they are part of some incident response framework where business continuity planning should be incorporated. This will enable Limetree Inc. to prepare in an effective and timely manner for responding to incidents and maintaining or swiftly re-establishing normal operations with minimum adverse impact on business operations.
New Incident Response Process
Follow-on would include getting rid of the threat, recovery of the compromised systems, as well as post-incident analysis for learning and improvements. Develop and integrate a comprehensive incident response plan defining particular roles, responsibilities, and procedures to be followed for effective incident management to ensure a proactive process in order to reduce the impact of incidents, returning operations rapidly to normal business continuity.
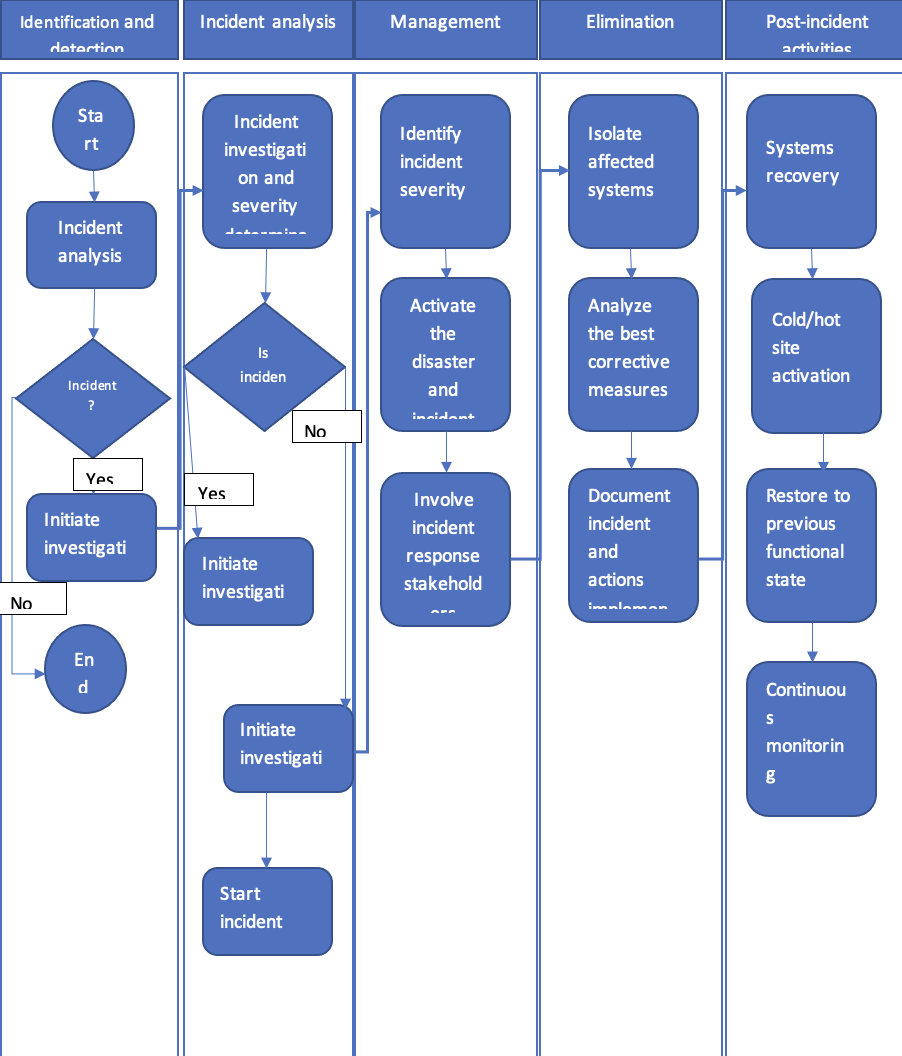
Impact
Application
In this section, there existed a data breach from a research and development firm, which involves the healthcare and biotechnology sectors, which may subject the firm to various government and industry regulations. In a nutshell, the Health Insurance Portability and Accountability Act (HIPAA) applies the high standards of safeguarding Personal Health Information (PHI). As it applies in the work of Limetree Inc. with health data, compliance with the standards of HIPAA is mandatory to avoid exposure to unauthorized access in such circumstances as, in this case, when work is being completed for a health care provider. In conclusion, it behooves organizations to further their trust, safety, and security behaviors, as the 2023 Executive Order speaks to, in the areas of biotechnology and online research—in regard to Artificial Intelligence systems. This thus stresses the need for firm information control security establishment threats, hence making the operational framework within Limetree Inc. enforceable.
Impact
Moreover, compliance with these regulations has a substantial impact on Limetree Inc., majorly through the need for firm information control security establishment. Complying with the HIPAA regulations, in support of the Executive Order, guards the organization against the new threats that might compromise quality in research and development. The introduction of these regulatory mechanisms is expected to make the operational environment secure, hence credible for the operations of Limetree Inc., and to attract collaboration with governmental agencies and private corporations. On the other hand, it also means that Limetree Inc. has to be prepared to invest substantial means—both financial and human resources—to be in compliance. Such investments are instrumental in maintaining a good business position of regulatory-compliant operations, which, in turn, can significantly limit the risk in terms of both frequency and severity of breaches.
Financial and Legal Implications
The legal and financial dimensions of the security breach to Limetree Inc. involve the spending of money on the acquisition of expertise and technology vis-à-vis cybersecurity against future incurrences. Moreover, the breaches often result in business disruption that, in turn, provoke probable cancellations of the contracts and financial losses. For that matter, non-compliance with rules like HIPAA and the outlined standards by the National Institute of Standards and Technology (NIST) often calls for a heavy penalty. From the legal viewpoint, Limetree Inc. is prone to breaches of the industry’s statutes, for instance, HIPAA, which may result in lawsuit claims by individuals whose PHI was abused (Seh et al., 2020). There are legally binding obligations on notifications of breaches to the clients, the company, and other regulatory bodies. Moreover, breaches would not only lead to the respective breach of contracts with clients looking for litigation for damages as a result of failures in data protection.
Security Test Plan
Scope
The scope of this Limetree Inc. cybersecurity risk assessment is designed to ensure overall analysis of its cybersecurity framework with a particular focus on the vulnerabilities exposed by the recent security breach for their identification and rectification. This assessment will be congruent with recognized cybersecurity industry standards, including the standards promulgated by the National Institute of Standards and Technology (NIST) and the associated risk management frameworks. It will involve the detailed scrutiny of the level of security for the applications and databases breached, analysis of the network configurations, and judgments of the adequacy of the policies and procedures followed for the implementation of security and instances related to the incidents. This should be carried out with attention not only to the weaknesses in the near future that this breach has highlighted but also to continue strengthening the ability of the organization to protect itself against more attacks.
Resources
The risk assessment exercise will require a multidimensional array of resources, which include gaining the knowledge of subject matter experts and leveraging technologies. The heart of these shall be a certified cybersecurity team that avails itself of the services of an ethical hacker, security analyst, and compliance auditor. These professionals will thus use various sophisticated penetration testing tools (like Nessus and Metasploit), vulnerability scanners, and network security analyzers. A percentage of the resources will also be set aside for the training of the IT staff from Limetree with the idea of making them aware of the security policies, incident response handling, and the standards on cybersecurity to be followed and adhered to. This holistic resource allocation is premised on analyzing security breaches and the absolute need to be aligned with the standard cybersecurity guidelines issued by NIST to ensure a resilient and robust security posture.
Hardware and Software
The hardware and software of the whole set of systems, as identified in the analysis of the security breach, were the subject of the risk assessment. These constitute the desktop applications that include MS Edge, Firefox, Google Chrome, MS Office, Adobe Flash, and Adobe Acrobat, among others, creating a possible way in. This will also look into the network infrastructure of the company, which includes its mail servers, application servers, file servers, and printer servers, together with its firewall devices (Biden, 2023). Also, the SQL Database, the virus software (McAfee), and several operating systems will be probed for security configuration to bring out any vulnerability that may exist (Trump et al., 2023). Per this security test plan, the hardware and software items supposedly in place would strive to strengthen the barrier against the threats in cyberspace, which resonates with the recommended cybersecurity standards by competently relevant bodies such as NIST.
Tools
By doing so, it is important for the organization to identify a collection of tools to provide an organized and effective means to identify the vulnerabilities and security breaches in place. This will include vulnerability scanning tools that are essential in the identification of those system vulnerabilities that attackers would expose. The third category of the tools, penetration testing tools, will provide a simulation of cyber attacks to make an assessment of the organization’s Limetree network and applications. Microsoft Defender ATP, Symantrop Endpoint Protection, and other tools for checking possible problems of endpoint security vulnerabilities. Other wireless network security tools such as Aircrack-ng and Wireshark will be used to analyze the traffic in a wireless network, noting unauthorized access and weaknesses. The tools chosen had to be strong and in compliance with set cybersecurity standards to cover all aspects of security that have to be considered regarding digital assets at Limetree Inc.
Timeline and Benchmarks
The security test plan will take place over eight weeks, with a structure around specific benchmarks to facilitate a complete and effective risk assessment. Initial assessments will be filled with meetings with stakeholders to get their perspectives, and weeks one and two are going to define the scope of the risk assessment. During weeks 3-4, vulnerability assessment and penetration testing will be undertaken, and corresponding security policies and procedures will be formulated. By weeks 5-6, the group will formulate and implement quick-win security measures to counter critical threats, especially in improving firewall configurations. The final weeks, 7-8, are given to training the employees, awareness, network segmentation, and enhancement of authentication, ending in compliance check, reporting, incident response, and implementation. The road map establishes the structure to enable adaptive responses for the discoveries of, and the reactions to, vulnerabilities.
Approach
The developed approach to the security test plan has its basis in a systematic and comprehensive strategy founded on the analysis of a security breach and the alignment with established cybersecurity standards such as NIST and HIPAA. This strategy emphasizes carrying out sufficient risk analysis, using chosen tools for vulnerability scanning and penetration testing. It lays stress on the creation of solid security policies and processes, design and application of rapid security measures, and shows commitment to continuous improvement. Network segmentation, improved authentication, staff awareness, and training are critical components of this approach. These are the intended principles that the organization is to follow, not only to make a partial improvement in mitigating identified direct risks from the security breach analysis but also in making the organization’s overall security posture towards future threats that may materialize a better one, ensuring sensitive data and systems are secure.
Risk Remediation
Security Controls
Various controls need to be implemented to ensure that a security breach is avoided in the future and that what is on the table is not repeated. Multi-factor authentication (MFA) should be employed in all the systems where possible, with reduced risk of unauthorized access. Second, deploy an advanced EDR that continually monitors against malicious activity and automatically responds. Third, regular security awareness training for all employees is responsible for the development of a culture of security mindfulness by addressing the human factor of cybersecurity vulnerabilities. Fourth, all sensitive data at rest and in transit is encrypted to protect against any possible vulnerability of information interception, therefore making it unintelligible. Finally, a zero-trust architecture whereby every effort to have access to system resources is verified will reduce the chances of insider threats and increase the surface area that can be attacked. The security, as mentioned earlier, controls will be implemented to address the pointed vulnerability in infrastructure.
Vulnerabilities
The security controls will be implemented in order to address the vulnerability in the infrastructure. Such security controls would stand in line with the best practices in cybersecurity and regulatory guidelines, thereby creating a strong frame for protection against future incidents. Multi-factor authentication eliminates, or at least reduces, the possibility of compromised credentials – again, a weak point repeatedly exploited by phishing attacks. If deployed in the current security posture, an EDR solution provides real-time monitoring and automated response to activities recognized as suspicious, thus patching a significant gap. Security awareness training mitigates the vulnerability from the unawareness of any employee, thus very significantly reducing the chance of any social engineering attack being successful. Through encryption of sensitive data, the confidentiality and integrity of information are guaranteed even in unauthorized access cases, especially in case a breach of data occurs. In other words, Zero Trust architecture systematically decreases network and application vulnerabilities through stringent access controls and continuous verification, which, in turn, reduces the organization’s overall risk profile.
Evaluation
Effective security controls are enforced only through strict and proper evaluation criteria. Clear criteria are set for every control, be it the reduction in the number of successful phishing attacks post-implementation of MFA and security awareness training or the detection and response rate of the EDR solution to simulated attack scenarios. Regular penetration tests and vulnerability assessments are supposed to establish how much the system is resistant to attempted breaches in a given manner and target a few of those areas that have been compromised. Moreover, aligning the compliance audits with HIPAA and NIST frameworks would further legitimize compliance. This, combined with the approval to ask for employee feedback on the effectiveness of the programs and the usability of the tools for security, would give a base for continuous improvement. The process of evaluation will be iterative, and the findings will lead to improvements in the security controls that will cater to the needs of the security threats that will keep evolving as per the organization’s needs.
Conclusion
Communication
In conclusion, as part of conducting the risk assessment, several issues in interpersonal communication were identified, with special emphasis on the lack of a good communication plan and proper channels of communication between departments. Problems that can be mentioned include delays in exchanging relevant information on the security vulnerability between the IT department and other units due to misunderstandings. Resolution efforts were through the creation of regular inter-departmental meetings and a communication platform, centralization of flows of information with capabilities for real-time updates, and facilitation in the ensuring of stakeholders being informed and aligned as well on security protocols and strategies for responses in case of incidences.
Organizational Culture and Reputation
The security breach disclosed, besides technical vulnerabilities, deep fateful organizational culture issues, including resistance to changes and a lack of security awareness. It underpins the predominant culture of complacency to security issues, a lack of continuous training, and a lack of a proactive stance towards security matters. That culture made it very difficult to enforce new security policies and measures that were necessary to be put in place to ward off the possibility of such things happening again. It sullied the company’s reputation a great deal, particularly in the way sensitive healthcare information was being dealt with. This transitory decline happened in business opportunities and collaborations due to the erosion of client and partner trust. This incident has been a turning point for Limetree Inc. in the way that security was something to pay more attention to and communicate more transparently to the stakeholders to ensure the safety of the data and avoid any upcoming incident.
Recommendations
For Limetree Inc. to be better placed to alleviate the chances of communication and organizational cultural problems in the future from its risk assessment, the following are some of the strategies the firm should take. First, the firm should institute a continuous education program on cybersecurity awareness for all employees to establish a culture of vigilance, sharing responsibility, and information security. Secondly, set a clear incident management framework where communication in all cases is transparent, with clear communication channels internally and externally, and all stakeholders are informed of risks, breaches, and remediation efforts. Thirdly, senior management should take the lead in all cybersecurity initiatives, which should embed security as a value in organizational culture. It further involves allocating adequate resources to security improvements and rewarding proactive security behavior in the staff. The rationale underpinning these recommendations is that both communication and cultural challenges will need to be multifaceted to address—comprising the confluence of education, structural changes, and leadership buy-in to fundamentally change Limetree Inc.’s security stance.
References
Alkhalil, Z., Hewage, C., Nawaf, L., & Khan, I. (2021). Phishing attacks: A recent comprehensive study and a new anatomy. Frontiers in Computer Science, 3, 563060.
Alshaikh, M., Chang, S., Ahmad, A., Maynard, S. B., & Alammary, A. (2023, August 07). Embedding information security management in organizations: improving participation and engagement through intra-organizational Liaison. Security Journal, 36, 530–557. https://doi.org/10.1057/s41284-022-00352-3.
Biden, J. (2023, October 30). Executive Order on the Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence. The White House. https://www.whitehouse.gov/briefing-room/presidential-actions/2023/10/30/executive-order-on-the-safe-secure-and-trustworthy-development-and-use-of-artificial-intelligence/
Farid, G., Warraich, N. F., & Iftikhar, S. (2023). Digital information security management policy in academic libraries: A systematic review (2010–2022). Journal of Information Science, 0(0). https://doi.org/10.1177/01655515231160026.
Jain, A. K., & Gupta, B. B. (2022). A survey of phishing attack techniques, defence mechanisms and open research challenges. Enterprise Information Systems, 16(4), 527-565.
Lali, K., & Chakor, A. (2023, May 8). Improving the security and reliability of a quality marketing information system: A priority prerequisite for good strategic management of a successful entrepreneurial project. Data and Metadata, 2, 40. https://dm.saludcyt.ar/index.php/dm/article/view/40.
Seh, A. H., Zarour, M., Alenezi, M., Sarkar, A. K., Agrawal, A., Kumar, R., & Khan, R. A. (2020). Healthcare data breaches: Insights and implications. Healthcare, 8(2), 133. NCBI. https://doi.org/10.3390/healthcare8020133
Shinde, N., & Kulkarni, P. (2021). Cyber incident response and planning: a flexible approach. Computer Fraud & Security, 2021(1), 14-19.
Tejay, G. P. S., & Mohammed, Z. A. (2023). Cultivating security culture for information security success: A mixed-methods study based on anthropological perspective. Information & Management, 60(3), 103751. https://doi.org/10.1016/j.im.2022.103751.
Trump, B., Cummings, C., Klasa, K., Galaitsi, S., & Linkov, I. (2023). Governing biotechnology to provide safety and security and address ethical, legal, and social implications. Frontiers in Genetics, 13. https://doi.org/10.3389/fgene.2022.1052371
Whitman, M. E., & Mattord, H. J. (2021). Principles of incident response and disaster recovery. Cengage Learning.
 write
write