Introduction
Cryptography is becoming more crucial to protect communication, data integrity, and privacy in the digital age. Prehistoric people encrypted their messages with primitive ciphers. Cryptography has changed to address new challenges and use new technologies. This progress is due to breakthroughs in mathematical theory and processing capacity and the ongoing fight between secure communications and bypassing them. Cryptography has evolved from hand-ciphers to complex digital algorithms as technology and intelligence have advanced. It has always been crucial in defense and attack.
The study mainly aims to trace cryptography’s history, particularly from mechanical to digital encryption. We will follow the development of encryption systems from the 1930s to the revolutionary 1970s and the complex present to understand how these transitions have affected modern communication. Cryptography has evolved with culture and technology, from physical instruments like the Enigma machine to digital algorithms like RSA and AES. This study will illuminate how cryptographic approaches have affected data transfer security and efficiency (Alimam et al., 2023).
Thesis Statement: The rapid growth of cryptography from mechanical methods to complex digital algorithms has dramatically impacted modern communications efficiency and security. This paper highlights the most significant innovations and discusses their current and future effects on cryptography.
Historical Overview of Cryptography
Cryptography has existed since humanity required a way to communicate secretly. Cryptography has protected sensitive data from eavesdropping since ancient times and is now essential to online international debates. Developing simple to complicated ciphers and algorithms shows the inventiveness and adaptability of individuals in this field.
Early Methods of Encryption
Cryptography was used to encrypt communications between ancient rulers and military leaders. The first encryption methods, transposition and substitution ciphers, were created for this. Substitution ciphers replace letters, while transposition ciphers reorder them. Julius Caesar employed the Caesar cipher to communicate with his generals, making it a famous substitution cipher. This encryption was simple for its time—just changing alphabetic characters by a certain amount (Bauer, 2021).
The Renaissance to the 20th Century
The Renaissance saw rapid expansion in several fields, including cryptography. After discovering that cipher security depended on encryption process secrecy and complexity, cryptographers and researchers continued to improve their methods. Polyalphabetic ciphers, which used a combination of letters to encrypt a message, were devised about the same time and made decipherment harder without the key.
Mechanical encryption technologies advanced cryptography most in the 20th Century. These communication security advances were groundbreaking because they combined cryptography and mechanical complexity. The WWII German Enigma machine is the most famous. Deciphering Enigma’s encrypted messages was nearly complicated for that era due to its sophisticated architecture and wide range of configuration options. It requested a user message, which was encrypted using rotors and displayed as a random string of letters. Decrypting a message requires the Enigma machine and its daily settings, which were adjusted to make it more durable.
The wartime Enigma machine showed the strategic use of encryption. Mathematicians like Alan Turing at Bletchley Park decoded Enigma communications to aid the war effort. Deciphering Enigma communications, often known as Ultra intelligence, is thought to have saved countless lives and shortened the war. The result demonstrated cryptography’s tactical significance and the need to improve encryption and decryption technologies (Sawyers, 2021).
Cryptography has advanced from simple shift ciphers to the complicated Enigma machine. The industry has long focused on solving insecure communication issues. Cryptoanalysis has gone as encryption technology advances and more resources are allocated. This constant progress underscores the significance of encryption in safeguarding information, just as it did under Caesar.
The transition from Mechanical to Digital Encryption
Cryptography changed as it switched from mechanical to digital encryption, like other philosophical and scientific advances after World War II. Encryption changed due to an exponential increase in processing power.
Post-World War II Developments
After World War II ended, cryptography was still essential, and new possibilities for cryptographic methods came with the advent of electronic computing devices. While early computers were primarily intended for processing data and doing calculations, they soon showed their value for cryptography. These machines could process complex algorithms at rates never seen before, laying the groundwork for a revolution in encryption approaches. Despite their cleverness, mechanical machines from the past were only usable because of the physical mechanics and the amount of manual labor required to operate them. However, electronic computers made previously impossible levels of computational power and automation possible, opening the door to far more sophisticated and secure cryptographic systems.
The 1970s: A Pivotal Era
Public-key cryptography threatened symmetric encryption in the 1970s, shaking cryptography. Key distribution and management were a nightmare when the same key was used for encryption and decryption. Leonard Adleman, Adi Shamir, and Ronald Rivest created the RSA algorithm after Martin Hellman and Whitfield Diffie introduced a two-key method in 1976. Instead of a shared secret key, participants could safely communicate using individual encryption and decryption keys.
Comparison of Mechanical vs. Digital Encryption
Moving from mechanical to digital encryption increased complexity, security, and reliability. Despite their innovation, mechanical devices were plagued by physical wear and tear, human error, and the fact that mechanical cryptography methods were more accessible to crack with enough time and effort. Digital encryption, which uses computer computing, eliminates many mechanical system restrictions and provides more reliable security.
Digital encryption allowed complex algorithms to be processed fast by computers, improving security. Complex encryption, especially public-key cryptography, has made messages more secure and difficult to decipher. Digital encryption allows longer keys and more sophisticated algorithms, making cryptography safer.
Encryption in the 1930s vs. the 1970s to Today
Since the 1930s, theoretical and technological advances have transformed encryption. This trend reflects the expanding complexity of the digital environment and the changing expectations and problems of secure communication.
1930s: The Era of Mechanical Encryption
The Enigma machine and other mechanical encryption devices were technological breakthroughs in the 1930s. WWII German forces relied on the complicated Enigma encipherment machine. This machine secured messages with rotors that changed encryption in a complex way. These technological marvels were ahead of their time but limited by their physical construction and operation. Coordination of cryptanalysis by Allied codebreakers showed they could defeat robust barriers (Javadpour et al., 2023).
1970s: Transition to Digital and the Advent of Public-Key Cryptography
The 1970s saw a turning point when digital encryption supplanted mechanical encryption. Public-key cryptography solved the long-standing problem of secure key distribution and advanced symmetric (or secret-key) encryption at this time. Diffie and Hellman devised public-key cryptography, which the RSA algorithm implemented, to secure communication without sharing a secret key.
The 1970s saw the widespread use of the Data Encryption Standard (DES) symmetric encryption technology for electronic data security. Although its keys were long and vulnerable to brute-force attacks, DES played a prominent part in the digital encryption ecosystem until more sophisticated standards replaced it.
Today: The Age of Advanced Encryption Standards and Beyond
Cyberattacks and computer power have advanced over the past Century, requiring new encryption methods. Since the early 2000s, the Advanced Encryption Standard (AES) has been the standard for digital data encryption. More robust algorithms and longer keys increase security. The latest encryption advancements include blockchain technology, quantum cryptography, and Advanced Encryption Standard (AES).
Cryptography has evolved from mechanical devices in the 1930s to digital and theoretical advances. As encryption technology improves, secure communication changes to address new dangers and opportunities (SaberiKamarposhti et al., 2024).
Impact on Modern Communications
Encryption has become essential for protecting modern communications with the internet and digital era. As more of our lives are online, encryption is crucial for privacy, information security, and national security. This relevance applies to the issues of balancing encryption strength and processing performance, end-to-end encryption in messaging apps, and secure surfing encryption techniques.
Digital Era Encryption and the Internet
Data sent between browsers and web servers is encrypted as the first line of defense against internet dangers. SSL and TLS secure connections for confidential communications and online banking. These protocols use public-key and symmetric-key encryption to create a secure session that cannot be eavesdropped. Only the receiver with the key can decipher transmitted data.
Digital communication platforms have also made end-to-end encryption in messaging apps more critical. With this technology, we can limit message access to the people conducting the chat. This includes hackers, service providers, and surveillance firms. End-to-end encryption apps like WhatsApp and Signal have made private talks safer. This ensures user discussion privacy (Kumar et al.)
The Role of Encryption in Privacy and National Security
National security and personal data protection depend on encryption. Governments and militaries must use modern cryptography to protect critical infrastructure from cyberattacks and espionage. Encryption technologies must be reliable in the age of cyberwarfare and data breaches. Countries invest heavily in cryptographic algorithms because they are both a security measure and a weapon in cyberspace.
Challenges: Balancing Encryption Strength with Computational Efficiency
The rising complexity of encryption technology presents considerable obstacles. Finding an excellent, robust encryption-computational speed balance is difficult. Performance and usability may suffer if more robust encryption methods require more computing resources. Speed and efficiency trump security in this society; therefore, this balance is crucial.
Encryption and cryptanalysis, deciphering encrypted data, are also at odds. Cryptoanalysis changes to stay up with cryptographers’ ever-improving methods. This cat-and-mouse game affects data security and cryptography standards.
Advances in cryptography are crucial. Digital communication security evolves with new technologies and threats. One example is cryptographic methods that can withstand quantum computers, which could completely degrade encryption standards. As blockchain technology integrates, decentralized and secure communication potential arises (Oppliger, 2021).
Cryptography trends could transform global communication. Quantum cryptography and other encryption advances are making Internet transactions safer, more private, and more dependable. Cryptography, an ancient art and science, will grow to defend our digital world as we travel this dynamic planet.
References
Alimam, H., Mazzuto, G., Ortenzi, M., Ciarapica, F. E., & Bevilacqua, M. (2023). Intelligent Retrofitting Paradigm for Conventional Machines towards the Digital Triplet Hierarchy. Sustainability, 15(2), 1441.
Bauer, C. (2021). Secret history: The story of cryptology. CRC Press.
Javadpour, A., Ja’fari, F., Taleb, T., Zhao, Y., Bin, Y., & Benzaïd, C. (2023). Encryption as a Service for IoT: Opportunities, Challenges and Solutions. IEEE Internet of Things Journal.
Kumar, N. V., Divya, A. S., Sree, B. K., & Daniel, M. P. An Investigation on” Unlocking the Potential: Advances and Challenges in Quantum Computing.
Oppliger, R. (2021). Cryptography 101: From Theory to Practice. Artech House.
SaberiKamarposhti, M., Ghorbani, A., & Yadollahi, M. (2024). A comprehensive survey on image encryption: Taxonomy, challenges, and future directions. Chaos, Solitons & Fractals, 178, 114361.
Sawyers, R. (2021). The History of American Cryptology Before World War II.
Appendix
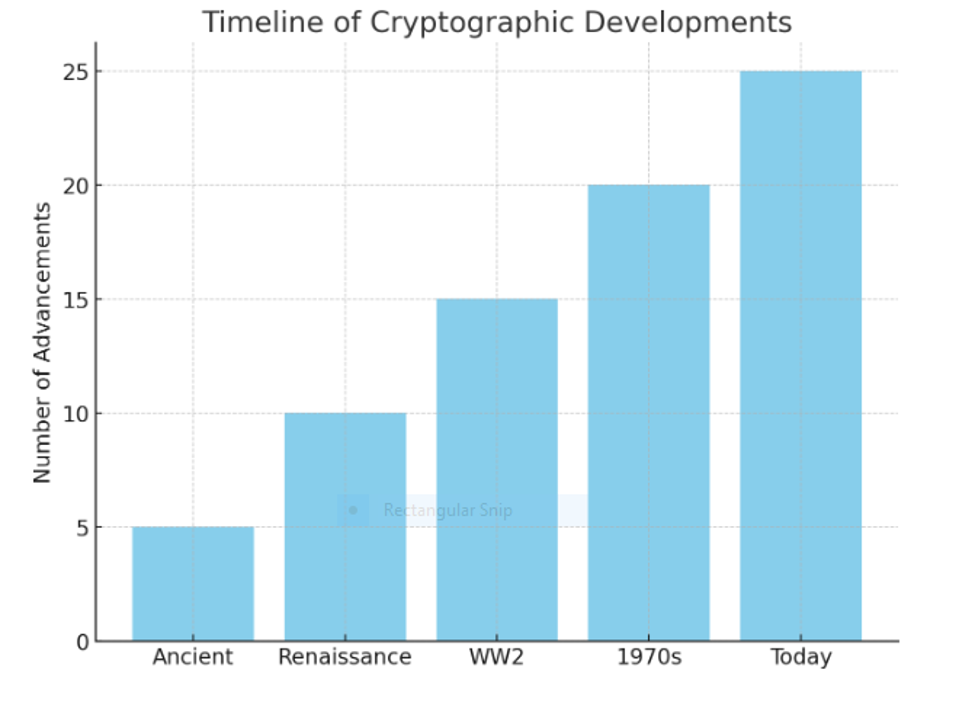
Timeline of Cryptographic Developments Bar Graph: This graph demonstrates the changing difficulty and number of cryptography advances from ancient times.
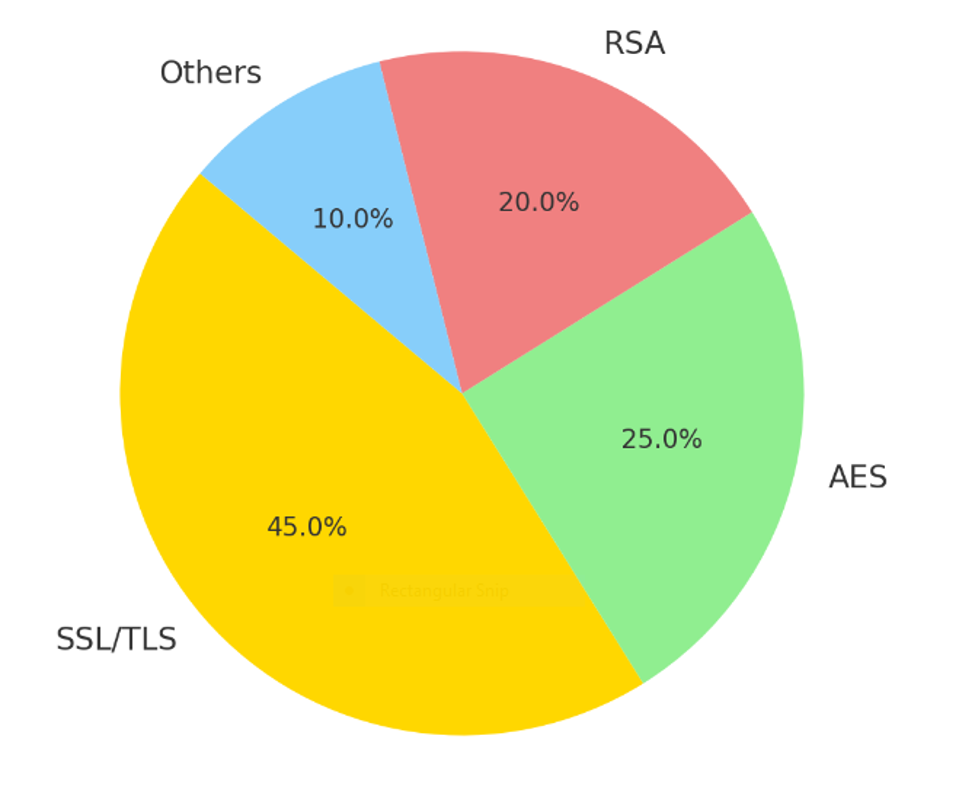
Usage of Encryption Protocols Pie Chart: SSL/TLS leads the encryption protocol list, followed by AES, RSA, and others. The many encryption technologies used to secure online communications are shown in this pie chart.
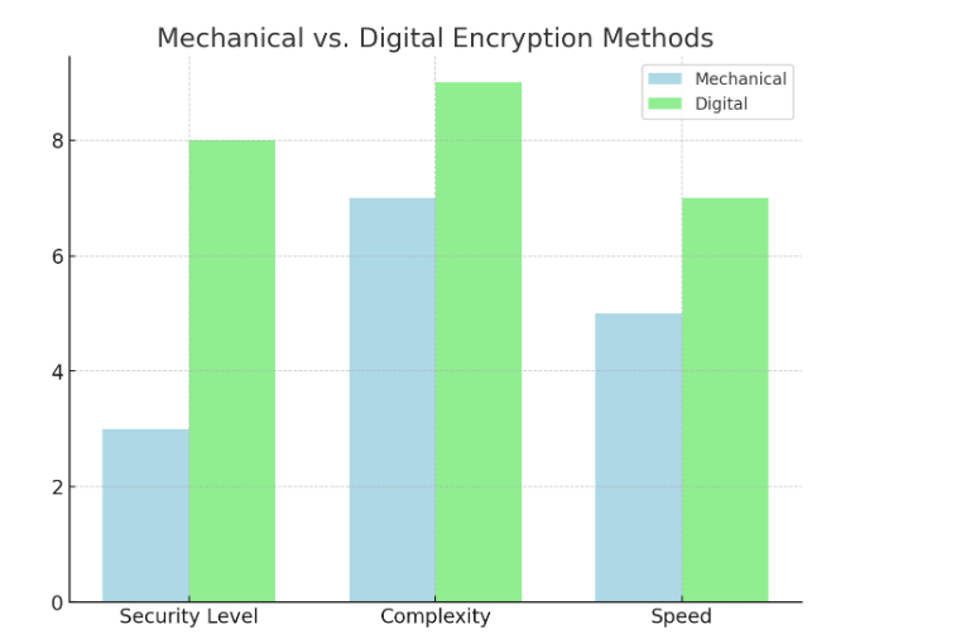
Comparison of Mechanical vs. Digital Encryption Methods Bar Graph: Digital encryption methods outperform mechanical ones in security, complexity, and speed, demonstrating encryption technology’s progress.
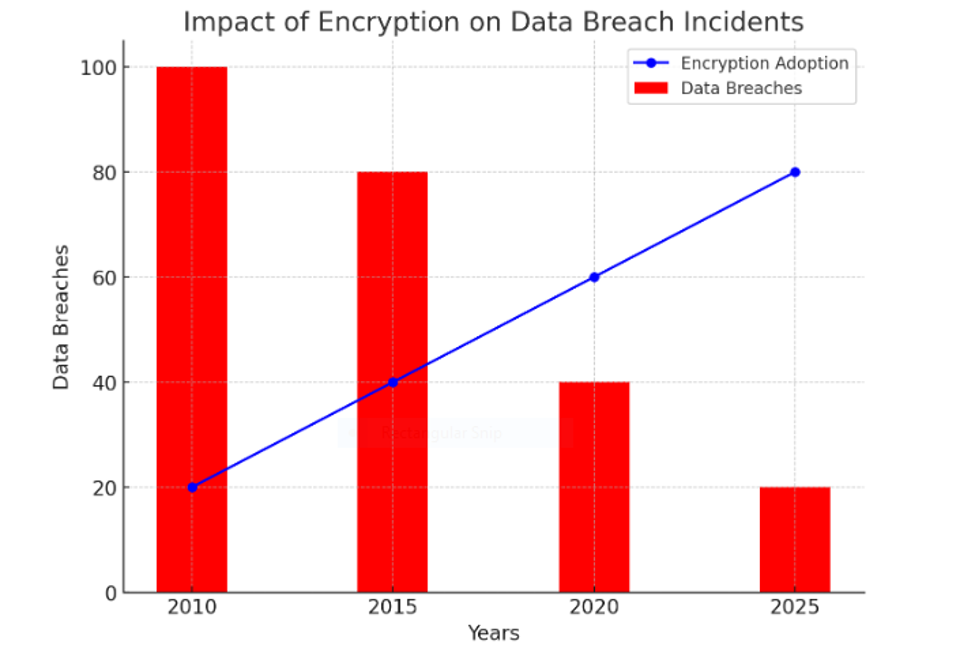
Impact of Encryption on Data Breach Incidents Bar Graph: In the graph, data breaches decrease as encryption use increases, showing a link between encryption and data security.
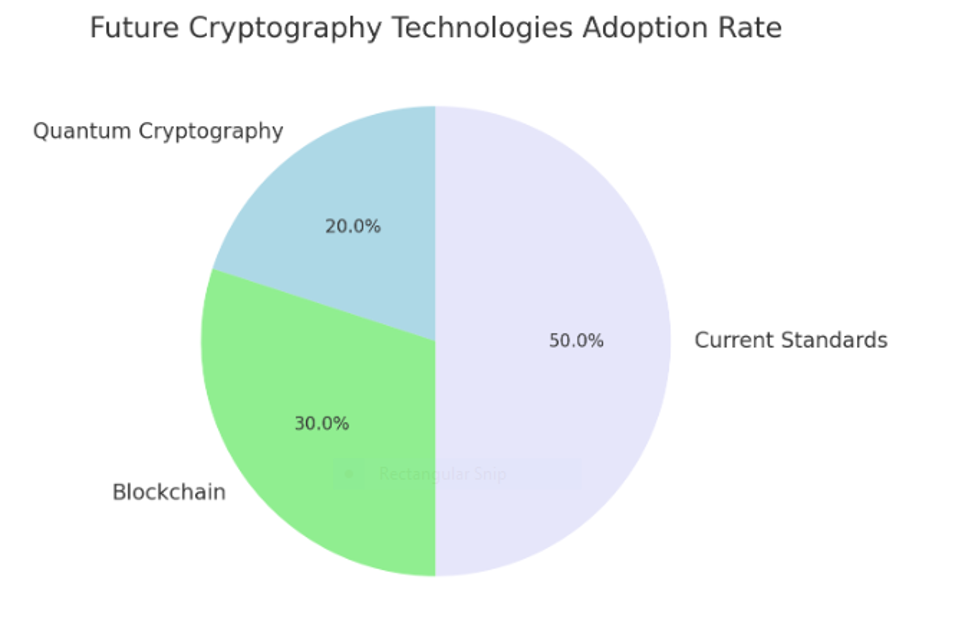
Future Cryptography Technologies Adoption Rate Pie Chart: This chart projects increasing acceptance of quantum cryptography and blockchain, along with current standards.
 write
write