Abstract
Ransomware is one of the most widespread cybersecurity dangers, posing a threat to businesses and IT users all around the world. Ransomware has evolved into serious and painful danger to people, governments, and businesses over the last several decades. Ransomware is a kind of virus that takes control of a user’s files and other computing resources by exploiting different security methods such as encryption. The attackers then demand money in return for the data that has been locked up. Cybercriminals frequently make a lot of money by propagating new ransomware versions. Cybercriminals are increasingly making money from ransomware assaults. Ransomware’s effects, unlike other types of malware, are permanent and difficult to counteract without the creator’s assistance. The article explores the current status of ransomware research, detection, and preventive strategies. The research investigates the elements that drive the propagation of ransomware attacks, as well as relevant preventative and forecast methods. In addition, the article delves into the topic of ransomware, including future developments and conclusions.
Introduction
In recent years, ransomware has grown in popularity as one of the most expensive and damaging cybersecurity threats. Cybercriminals utilize ransomware attacks to keep data systems or files hostage in return for a ransom or payment from people, businesses, and the private and public sectors (Falk, R. and Brown, 2021). Unlike other forms of cyberattacks, which often include the theft of financial or healthcare information, ransomware assaults target victims directly, holding their data systems and files hostage until a ransom payment is made (Nieuwenhuizen, 2017). According to recent research reports, ransomware assaults have expanded quickly over the years, and successful attacks have resulted in tremendous rewards for the hackers. According to Yaqoob et al. (2017), 40 percent of the crypto locker-affected persons consented to pay the ransom requested.
The hackers have a strong incentive to attack additional systems as a result of this. As a result, ransomware is a huge cybersecurity problem that has drawn the attention of a number of academics, researchers, developers, and security professionals who are actively looking for countermeasures. The subject of ransomware attacks is examined in this article.
Overview
By stealing and making unavailable user file resources and other relevant computing resources, ransomware attacks are common. The victim is then asked to pay a ransom in return for the data systems and files that have been stolen (Richardson, R., and North, 2017). Extortion is often carried out by preying on victims’ fears of losing important information, sensitive data, or computing resources. The first ransomware assault took place in 1989 when the AIDS Trojan malware was published. Other sorts of assaults, such as Denial of Resources (DoR), emerged as a result of the advent of ransomware (Dudley, 2019). The effects of ransomware, especially those that use encryption methods, are irrevocable. The monetary rewards derived from ransomware are important elements in the spread of ransomware. The amount of money paid as a ransom by a victim user often varies from $300 to $500 for individuals and $10000 to $15000 for businesses ( Haque, S. and Bhuiyan, 2017). Despite the fact that people and businesses are advised not to pay ransoms, it is sometimes the only method for users to recover access to their protected information. As shown in the diagram below, there are various key areas of study in the ransomware domain.
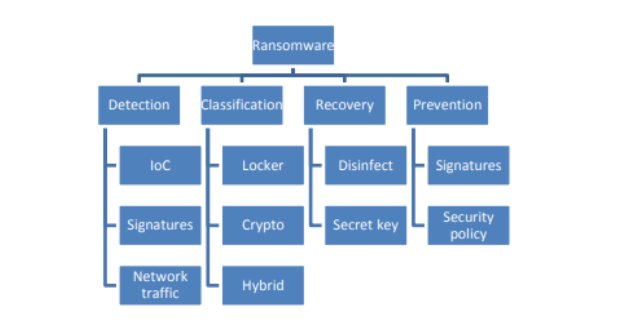
Fig. 1 Ransomware domain of research
Infection vectors
Cybercriminals use a variety of methods to disseminate ransomware. It also includes a number of other components. For example, attackers may send a spam email containing URLs that route users to malicious websites carrying exploit codes that compel them to download ransomware using the system’s security vulnerabilities (Patyal et al., 2017). The ransomware assaults may be propagated using email accounts that include suspicious attachments or malicious URLs that can be downloaded. Furthermore, ransomware attacks may be transmitted through drive downloads, which are only a clever technique for infecting victims’ computers (Zakaria et al.,2017). In many circumstances, victims are directed to a hacked website where harmful exploitable code is concealed on a legitimate website and executed. These approaches are extensively used by cybercriminals to install malicious software on susceptible computer systems.
According to statistics, ransomware assaults through infected emails have increased by 600 percent as a result of Covid-19, and experts project that ransomware attacks will occur every 11 seconds in 2021 (Sobers, 2021). The average ransom money demanded by attackers has risen from $ 5000 in 2018 to over $ 200000 in 2020. An insurance company paid $40 million for the most well-known ransomware claim in 2021, establishing a new worldwide record (Sobers, 2021). In 2017, ransomware attacks cost more than $5 billion in lost time and ransom paid as a result of the attacks. Data backups are the greatest strategy to safeguard companies and people against Ransomware threats. Ransomware threatens to encrypt users’ data, therefore having clean data that users can restore from backup is the best way to recover from an assault. It’s critical to back up data against ransomware. This is because, when ransomware hits, if enterprises and individuals have a clean backup of their data and can prevent the virus from accessing the backup and encrypting it as well, they will have a simple and secure means to restore data without paying the ransom (Posey, 2019). Data backup is essential because having clean backups ensures that data can be recovered following a ransomware attack.
Data can always be recovered using backups. Data recovery via backups is critical since it is less expensive, more dependable, and does not need to pay money to hackers (Pritchard, 2020). According to Sophos, attackers were successful in encrypting data in roughly 75% of ransomware assaults in 2019. The majority of the businesses were able to restore their data, but backup recovery was twice as common as paying the ransom, and it cost them less than half as much. Backed-up data may also be safeguarded by using immutable storage. Write-Once-Read-Many (WORM) storage, also known as immutable object storage, may store data in a bucket and deadlock it to prevent further alteration. Changed block monitoring is used by several disk-based backup systems to protect data at the block level and defend archives as they change.
The problem is that ransomware changes a lot of storage blocks, and the backup network can end up storing encrypted data (Posey, 2019). Before the assault happens, a good backup system should restore the data to its previous condition. Backups might be protected against malware assaults if they are stored on immutable storage. It allows the backup system to keep a sufficient number of retrieval points while protecting the existing storage blocks from modification, enabling the backup system to restore data to its original condition before the assault.
Another good technique to prevent backups against ransomware attacks is to increase backup frequency. Even if the organization is able to completely recover the backup data, the frequency of backups will affect how much data is lost in a ransomware attack (Korolov, 2021). Companies could improve backup frequency to limit the quantity of data lost following a ransomware attack. For example, if data is backed up every 10 minutes, the organization might lose up to 10 minutes’ worth of information in an attack since that data was not backed up yet and could not be recovered.
Categories of Ransomware attacks
Locker and Crypto ransomware are the two most common forms of ransomware attacks. The locker ransomware outbreak encrypts data files on victims’ devices and prevents them from accessing computer system functions. In the case of Internet of Things devices, the locker ransomware assault tends to impair the whole device’s functioning, including disabling all user interfaces, deactivating all inbuilt sensors, and launching DoS attacks to slow down the device’s performance. Crypto ransomware is a kind of ransomware that encrypts chosen files and directories on infected computers and platforms. The Crypto ransomware assault prevents users from accessing computer files.
The crypto-ransomware attack often employs both public and private keys, with data being encrypted using the public key and decrypted with the secret key (Ganorkar and Kandasamy, 2017). Once it has infected the computer system, it prevents the user from accessing the files by encrypting all of the targeted data files; it then prompts victim users by sending them a threatening ransom message informing them of what has happened to their data files and instructions on how to obtain a back decryption key that will allow them to access their files.
Ransomware analysis
Ransomware analysis plays an important role in ransomware research; as a result, ransomware analysis as a component aids in ransomware detection, classification, and prevention (Beaman et al., 2021). A greater understanding of the ransomware lifecycle and assault stages, as well as its hidden goals, is critical for developing protective and effective countermeasures.
The lifecycle of ransomware begins with the distribution of malicious malware and ends with the victim receiving a cash claim (Anghel, M., and Racautanu, 2019). As a result, at this point in the lifecycle, a number of activities are taken to effectively steal the user’s resources and data. To get the ransomware inside the victim’s PC, the drive-by download, mail attachment, or code dropper are used initially (Garg et al., 2018). The malicious application initiates activities on the host system upon its arrival. These tasks include deactivating shadow copies, producing a unique machine ID, collecting external IP addresses, and installing software to execute at boot time. Despite this, in the third stage, the ransomware connects its command and control servers to get the encryption key.
The procedure also looks for user-related files with certain extensions, such as data files, in the fourth stage (Martnez-Garca, 2020). Moving the data on the target to a new location and afterward encrypting them is the fifth stage in the encryption process. Step five involves renaming the encrypted files before deleting the originals. Finally, the malicious software presents the claim containing the ransom demands to the victim, either on a desktop screen or as a text file, as the final step.
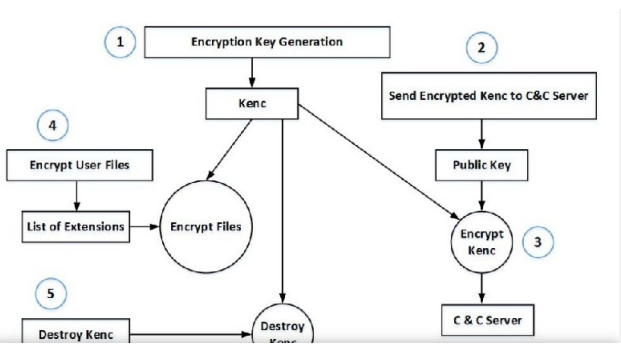
Fig 2. General Lifecycle of a ransomware attack (Anghel, M. and Racautanu, 2019).
Ransomware phases
However, when it comes to the stages of a ransomware attack, ransomware takes a similar strategy to classical malware that exploits the system’s weaknesses (Brewer, R., 2016). To take control of the victim’s laptop, ransomware uses a variety of attack vectors, including email attachments and compromised websites. In order to carry out its assaults successfully, ransomware goes through many stages. The malicious malware is sent to the victim’s machine during the initial distribution phase (Beaman et al., 2021). Several actions occur as soon as it arrives. File searching, communication, infection, extortion, and encryption are all examples of these activities. Extortion, searching, and money claims are the three steps of ransomware attacks. The searching phase is used to obtain information and learn about the surroundings. Urooj et al. 2021) say that the user’s resources are targeted in this way. Quantifying risks, such as determining the vulnerability of a certain asset and its worth, as well as estimating the threat’s probability, are all part of risk determination.
A strategy for implementing safety improvements based on risk evaluation is included in control suggestions. It also contains a cost-benefit analysis to show that the expense of additional security measures may be justified by risk reduction. The last step is to record the findings in a report that will aid senior management in making choices on financial, policy, operational, procedural, and administrative adjustments. Vulnerabilities, threats, and risks are defined in the report, along with specific control suggestions (Wangen et al., 2018).
Future developments of ransomware
The definition of a ransomware assault is fluid and ever-changing. As attackers create assaults directed at new targets, the number and complexity of ransomware attacks continue to rise. According to Boatman (2014), 81 percent of ransomware attacks are motivated by financial gain and cause significant harm to businesses. With the number of hackers expanding and devising extortion strategies, ransomware attacks have become a big danger to commercial enterprises throughout the globe. The number of cybercrime threats has increased in the aftermath of the Covid-19 pandemic. This is because ransomware attack extortion has become a popular alternative to conventional cybercrime threats and fraud. New cybersecurity techniques and procedures are necessary to identify harmful programs and prevent them from destroying data files and systems, in order to protect computer users from becoming victims of ransomware perpetrators (Tuttle, 2016). As a result, it is up to users to comprehend the nature of ransomware attacks and properly investigate them in order to devise suitable defenses.
Conclusion
Ransomware is a serious and hazardous cybersecurity threat to people, businesses, and the government; ransomware is used by hackers to extort a large sum of money from victims who wish to recover access to their locked systems and information. As a consequence, there is a growing need to develop realistic ways of dealing with this danger in order to avoid business interruption. The best technique for recovering data after an assault is to keep data backups. To decrease the quantity of data lost during ransomware attacks, businesses and individuals should endeavor to maintain an offline data backup system and update it on a regular basis.
References
Anghel, M. and Racautanu, A., 2019. A note on different types of ransomware attacks. IACR Cryptol. ePrint Arch., 2019, p.605.
Beaman, C., Barkworth, A., Akande, T.D., Hakak, S., and Khan, M.K., 2021. Ransomware: Recent Advances, Analysis, Challenges and Future Research Directions. Computers & Security, p.102490.
Boatman, K., 2014. Beware of the rise of ransomware.
Brewer, R., 2016. Ransomware attacks: detection, prevention and cure. Network Security, 2016(9), pp.5-9. Dudley, R., 2019. The extortion economy: How insurance companies are fueling a rise in ransomware attacks. Pro Publica.
Falk, R. and Brown, A.L., 2021. Exfiltrate, encrypt, extort: the global rise of ransomware and Australia’s policy options.
Ganorkar, S.S. and Kandasamy, K., 2017. Understanding and defending cryptoransomware. ARPN Journal of Engineering and Applied Sciences, 12(12), pp.3920-3925.
Garg, D., Thakral, A., Nalwa, T. and Choudhury, T., 2018, June. A Past Examination and Future Expectation: Ransomware. In 2018 International Conference on Advances in Computing and Communication Engineering (ICACCE) (pp. 243-247). IEEE.
Haque, S. and Bhuiyan, T., 2017. Rise of Ransomware and the Readiness of Bangladesh. International Conference on Latest Trends in Engineering and Technology.
Korolov, M. (2021, August 12). Ransomware recovery: 8 steps to successfully restore from backup. Retrieved from the CSO United States: https://www.csoonline.com/article/3627828/ransomware-recovery-8-steps-tosuccessfully-restore-from-backup.html
Muthuppalaniappan, Menaka. Academic.oup.com, Oxford Academic, 27 Sept. 2020, https://academic.oup.com/intqhc/article/33/1/mzaa117/5912483?login=true
Pranggono, Bernardi, and Abdullahi Arabo. “Covid‐19 Pandemic Cybersecurity Issues.” Wiley Online Library, John Wiley & Sons, Ltd, 14 Oct. 2020, https://onlinelibrary.wiley.com/doi/full/10.1002/itl2.247
Posey, B. (2019, October 22). How To Ransomware-Proof Your Backups: 4 Key Best Practices.
Retrieved from Redmond: https://redmondmag.com/articles/2019/10/22/how-toransomware-proof-your-backups.aspx
Richardson, R. and North, MM, 2017. Ransomware: Evolution, mitigation and prevention. International Management Review, 13(1), p.10.
Tuttle, H., 2016. The rise of ransomware. Risk Management, 63(10), p.36.
Urooj, U., Maarof, M.A.B. and Al-rimy, B.A.S., 2021, January. A proposed Adaptive PreEncryption Crypto-Ransomware Early Detection Model. In 2021 3rd International Cyber Resilience Conference (CRC) (pp. 1-6). IEEE.
 write
write