Introduction
The Internet of Things (IoT) is an extension of the vast area network known as the internet. There are different equipment pieces with which IoT is implanted, like gadgets, sensors, and other equipment structures. The vast area network facilitates constant communication between the devices. By the end of the year, it was anticipated that the number of IoT devices would reach almost 20 billion (Gurunath et al., 2018). This can be a problematic situation for service providers and organizations to manage. With the increase in IoT devices, it will be critical to keeping individual networks and services safe from intruders. Even though technological advancements can be viewed as a boon to the modern era, there are also some disadvantages, such as cyber-attacks and theft.
Various cutting-edge equipment has been developed to enhance communication due to technological advancements in scientific discovery today. IoT devices are one example of how the internet platform has changed. These are unconventional computing devices that can transmit data to many devices on the internet and connect wirelessly to the network (Gurunath et al., 2018). Beacons, sensors, and RFD tags have been added to the Internet of Things, enhancing their effectiveness. Notably, the Internet of Things also faces challenges that may be technical or security-related, making their communication less effective and reliable.
This research paper investigates security issues, the most prevalent privacy and security issues, and methods for making IoT devices more secure. It is hoped that the paper will assist students or scholars in comprehending the concept of the Internet of Things (IoT) in terms of its various types, legal privileges, and security issues. It will also inform them of ways to increase the IoT’s security.
Different privacy types have been introduced due to the significant advancements in the Internet of Things (IoT). These types are utilized in various fields to enhance the devices’ performance and security. The most common privileges, including but not limited to 1, are briefly discussed here.
- Airbiquity is an engineering and software company that provides connected vehicle data management and over-the-air update services.
- Ai. – They use a wide range of connected devices to provide voice-controlled home automation. In the event of an emergency in which their remote control is not easily accessible, they are also modified to control watches and phones.
- Insteon – because they help control water leaks, doors, windows, and electric appliances, they are essential in homes. Only through commands and scans.
- The privacy version of the eye lock uses iris-based authentication, requiring users to scan their eyes to access a specific location. Privacy is mainly used in the financial, mobile, and healthcare industries.
- Peak 8 link. – The wireless DoodleBug sensors help the user set up and keep track of soil levers so they can decide how to water their garden and keep it healthy.
- They provide recycling services in various retail industries by utilizing IoT-enabled container sensors.
- Analytical nexleaf. – People in the global public health and climate change sections benefit from their data analysis tools and lightweight sensor services.
- Technologies for amps. – It is utilized in assembling enterprises where it utilizes its working framework by utilizing web-associated sensors and information science. They are necessary for keeping records that owners and managers can access
- The superdestrians – It makes it easier for people to move around cities. The Superdestrians Copenhagen wheel is compatible with all bikes, increasing the pedaling power and speed.
Although most businesses take adequate security measures, there are times when data breaches and the leakage of sensitive information occur despite strict security measures. Most of the time, medium-sized businesses are more likely to be attacked because their IT infrastructure may only sometimes be sufficiently secure (Almolhis et al., 2020). The report will discuss security issues in specific IoT devices and certain organizations’ IT infrastructure. There will also be a few examples that show the problems with IoT and information technology devices.
Issues
Businesses use several IoT devices that they purchase from various manufacturers. A company has bought devices from Cisco, Linky, and Netgear. Most of these devices ought to have limited processing power, memory, and storage space. Naturally, this leads to the conclusion that these devices cannot rapidly perform complex encryption and decryption operations (Almolhis et al., 2020). This might make it harder to transfer data or information in real time securely. The Netgear GS116PP100AJS is one example of a device. A typical IoT device may be at risk for side-channel attacks like the power analysis attack.
Manufacturers may only sometimes include adequate security measures in these devices, which could become an issue in the future and make it easier for attackers to exploit a firewall structure flaw. The majority of medium-sized businesses’ devices lack adequate security features. This is mainly because there need to be more updates, and they do not happen often. Businesses buy these IoT devices with faith in the brand, but the devices are more likely to break down after some use.
According to research and surveys, particularly Cisco-branded products eventually become defective. However, despite initially providing customers with regular updates, businesses like Netgear eventually stopped doing so. As a result, these out-of-date and defective products become vulnerable to potential attacks (Ahmad et al., 2019). The fact that IoT devices do not encrypt messages before sending them to the network is another major problem. This can be dangerous and be used by hackers to steal important information.
Even though the Internet of Things (IoT) has made significant advancements, security issues remain a threat that slows down devices. The difficulties could be brought on by a technical glitch or by criminals hacking into installed systems and destroying them with evil intentions like robbery. Understanding some of the IoT’s security challenges is essential. The following security issues are associated with the Internet of Things but are not limited to them:
A lack of testing and updating
There are currently more than 23 billion connected IoT devices worldwide. This number will reach 30 billion by 2020 and 60 billion by the end of 2025. The substantial influx of new technology comes at a cost. The absence of testing and updates is the most significant security flaw. One of the biggest problems with the tech companies making these devices is that they need to deal with security flaws in the devices quickly. Most of these gadgets and Internet of Things products need more updates, and some do not get any. This indicates that a device initially thought to be safe when users purchased it eventually loses its security, making it open to hackers and other security threats (Ahmad et al., 2019). Automatic updates alleviated this issue, which was present in early computer systems. Because a single large-scale data breach can bring a company to its knees, failing to do so is detrimental to both businesses and their customers.
Default passwords and brute-force passwords
The Mirai botnet, which has been used in some of the most significant and disruptive DDoS attacks, is the best illustration of the issues that arise when devices are shipped with default passwords and consumers are not instructed to change soon as they receive them. According to several government reports, manufacturers should avoid selling IoT devices with default settings. Credentials can be hacked, like using “admin” as a username or password. However, at this point, these are merely guidelines, and there are no legal sanctions in place to encourage manufacturers to abandon this harmful strategy (Hosenkhan & Pattanayak, 2020). Due to weak credentials and login data, almost all IoT devices are susceptible to password hacking and brute-forcing. Consequently, a brute-force attack can target any business that uses factory default credentials on its devices and its assets, customers, and sensitive data.
Malware and ransomware for IoT devices
The number of viruses and ransomware used to exploit IoT devices will also increase in the coming years. Ransomware and malware are the most prevalent IoT security threats. Hybridization of malware and ransomware strains is increasing to combine the two types of attacks. In contrast, traditional ransomware uses encryption to lock users entirely out of various platforms and devices. The ransomware attacks may aim to steal user data while reducing and disabling device functionality (Hosenkhan & Pattanayak, 2020). For instance, gathering sensitive data from various locations, including your house, workplace, or even the neighborhood gas station, can easily be accomplished using a straightforward IP camera. After that, the webcam can be locked and the video sent to an infected website. From there, the website can use the malware access point to extract sensitive data and demand a ransom to unlock the device and restore the data. Future attack permutations will become more unpredictable as the number of IoT devices grows.
IoT botnets focused on cryptocurrency.
Hackers looking to capitalize on the cryptocurrency craze are finding the intense mining competition and the recent rise in cryptocurrency value alluring. The most dangerous IoT botnets target cryptocurrency; most people believe that blockchain is invulnerable to hackers, but there appear to be more attacks on the blockchain industry. The biggest flaw is the blockchain app development that runs on it, not the blockchain itself. This user data is frequently given to many different businesses or sold to them. This violates our privacy and data security rights and makes people more distrustful. We must establish specific privacy and compliance guidelines that redact and anonymize sensitive data before storing and disassociating IoT data payloads from information that could be used to identify us personally. Information that has been stored and is not generally required should be securely discarded. The most challenging part will be adhering to numerous legal and regulatory structures if the data is saved.
Literature Review
According to Sultan et al. (2019), security concerns include protecting connected devices and the web in the Internet of Things by machinery. After several high-profile incidents in which a shared IoT device was used to penetrate the more extensive web, IoT sanctuary needs to be the subject of investigation. Because it ensures the safety of webs connected to IoT devices, taking precautions against those devices is essential. The innovativeness exacerbates the storage issue. This issue arises when connected devices constantly control large machines and send and receive sensitive data. The Internet of Things (IoT) may also introduce new vulnerabilities in an organization, despite the significance of the new data and insightful insights it provides. Innovativeness must now consider the security implications of an IoT deployment due to these new vulnerabilities.
In addition, when it comes to the endpoint hardening, some tools may function normally and not contribute to the retreat that can be observed consistently. Accordingly, building such gadgets that interfere resistant or interfere obviously might be necessary since this endpoint fortifying can help prevent potential trespassers from getting to the records in such gadgets. The data is protected by endpoint strengthening from hackers buying and using weapons (Sial, 2019). Endpoint hardening typically entails installing an encrusted method requiring intruders to circumvent several preplanned obstacles to protect the device and its files from intruders, who may be considered unauthorized accessors in this instance. Additionally, according to Mohanta et al. (2020), organizations should protect against well-known flaws like open password probes, serial ports, and Transmission Control Protocol (TCP) ports. IoT devices must introduce their uniqueness to justify dependence carefully when they want to connect to a network. For instance, since it provides a secure foundation for the identity and reliance of devices, Public Key Infrastructure (PKI) may help manage the IoT’s uniqueness.
In order to guarantee the safety and security of computers, businesses must adhere to network security measures. According to Mohanta et al. (2020), the application of robust user verification and access regulator appliances, which ensure that only accredited individuals have access to websites and data, are two examples of the kinds of security measures an organization can take to improve network security. The code word must be elegant enough to withstand educated guessing and brute force methods. Two-factor authentication, which requires the user to enter a secret word and use an additional verification factor, such as accidental encryption generated by SMS transcript messaging, should be used by organizations. Another way to improve network security is to use robust encryption on as many secure protocols as possible. Because the Internet of Things (IoT) entails an assembly of network procedures used at various strata, such strong encryption plays a crucial role in protecting any communication between devices that could be hacked (Shakya, 2022). Transport cover and web cover codes can provide several obstacles for network-based intruders.
The number of web links between an IoT device and the web must be reduced as one of the “shall” requirements for IoT device network communications. In particular, before being compressed and transmitted over the communication system, data should be assembled into as large a piece as possible by the IoT device solicitation. According to Kagita et al. (2020), if the IoT provision permits, the Internet of Things device application must employ a random design for network connection requests and avoid synchronized behavior with other Internet of Things devices. The use of the Internet of Things should implement appropriate safeguards to prevent unauthorized or uncertain device management functionality, such as firmware updates to the IoT software. All native and remote device management features will be covered by firmware update procedures (Thakkar & Lohiya, 2021). In addition, the use of IoT devices must adapt to changes in the speed of portable web forms and files at any given time, regardless of where they are located.
However, the Internet of Things device solicitation must monitor the number of web links it requests over a predetermined time frame. The IoT usage will stop requiring web connectivity until the duration ends if the number of connection attempts exceeds a predetermined value. According to (Thakkar & Lohiya (2020), the extreme value will be set so that the Internet of Things service provider can offer it. In addition, the IoT solicitation must evaluate the capacity of the files it transmits and accepts over a predetermined period. As a result, the Internet of Things device will stop transferring and accepting files until the time limit has run out if the size of the files that are sent and received exceeds a certain threshold.
The IoT Service Provider will determine the extreme value, and if the Internet of Things device exceeds that value, a notification will be sent to the IoT checkpoint. Additionally, the use of the Internet of Things will be planned to ensure that the applications’ web message task is not burdensome, particularly during times of high web usage; this means that the design maximizes the use of “off-peak” ours as directed by the portable web operator (Thakkar & Lohiya, 2021). In conclusion, organizations can ensure the provision of audit trails and standard endpoint detection by utilizing security information and event management, central log management, ensuring adequate log storage, enabling detailed logging, activating audit logging, and making the most of the three synchronized time sources. Additionally, organizations can ensure the detection of endpoints that are usually compromised.
IT Infrastructure Security issues
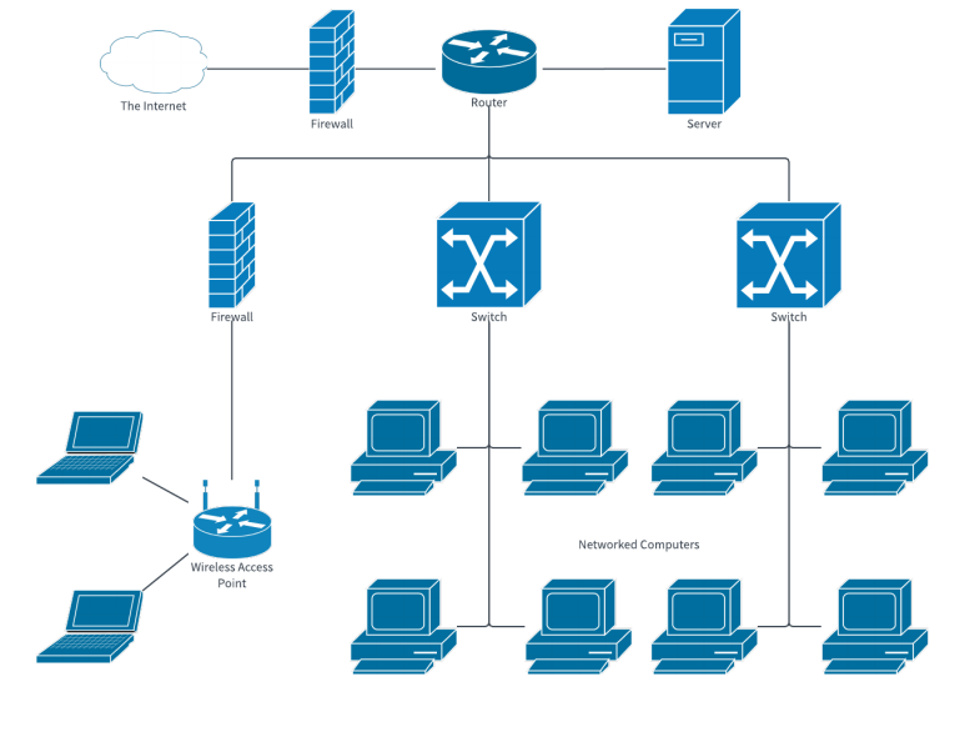
Attacks typically target medium-sized businesses’ IT infrastructure more frequently than more giant multinational corporations. As seen in the image above, the structure of most networks resembles a tree. The root nodes in the topology are connected to numerous smaller nodes, which in turn are connected to numerous switches. The network’s computers are connected to these switches, which complete the structure (Mirza et al., 2022). This topology is utilized by the company, particularly the medium-sized ones, to enable them to add additional nodes following their requirements, thereby contributing to further expansion of the network structure. Due to its size, a computer virus can easily sneak into such a system undetected. In addition, there is the issue of outdated and faulty devices that might be unable to stop the virus from entering.
Over 30% of users are affected by a variety of computer viruses and malware, according to the statistics (Mirza et al., 2022). The Trojan horse is generally regarded as the most prevalent virus, and upon entering a system, it begins rapidly reproducing itself. Adware and spyware are two different kinds of viruses. Pop-ups are used by specialist software to monitor user data and information. Computer worms, which are malware programs designed to replicate themselves quickly and can be highly contagious, are another threat.
In addition to their inadequate security measures, these medium-sized businesses’ infrastructure lacks an appropriate and efficient defense mechanism. These networks contain several gaps and cracks that skilled hackers can exploit. Furthermore, this network lacks adequate security management and is open, as shown in the preceding Figure.
Scenarios of attack
An actual example of an IoT device attack
The Internet of Things (IoT) is expanding at an unprecedentedly rapid rate. One of the many uses and utilities of IoT devices is sending and collecting data from faraway locations so essential events can be detected more quickly and easily (Mirza et al., 2022). There is a well-known instance of Mirai botnet attacks in which IoT devices like thermostats, webcams, and sensors were the targets. These attacks resulted in a massive distributed denial of service attack in 2016. The majority of IoT devices could not connect to the internet or WAN due to this. The attackers could remotely control a collection of internet-connected computers known as bots. These connected devices could send a lot of web traffic to the IoT devices until they could not connect to the internet and die.
An actual example of an It infrastructure attack
An illustration of an IT infrastructure attack was Adobe’s 2013 attack, which resulted in the theft of passwords, usernames, and even credit card numbers from over 2 million private accounts. The company, as well as users worldwide, were significantly impacted. These criminals were also accused of stealing banking data (Abdullah et al., 2019). The attackers wanted to get many customers’ information and accounts. The entire Cold Fusion product’s source code and portions of Adobe Reader and Photoshop’s source codes were among the estimated 40 GB of stolen code.
The 2011 attack in which crucial customer information was leaked from the company “SONY” is another example of an It infrastructure attack. SQL injection was the attack’s strategy. The attackers stole over a hundred terabytes of customer data, including important confidential information, personal data, and film scripts.
Methods
The configuration of an intelligent environment and self-aware, independent devices, such as smart living, innovative items, wise health, and smart cities, are the primary goals of the Internet of Things. In the following section, we will discuss how IoT can be used for home automation, the medical field, and the industry.
Industrial IoT
The Internet of Things (IoT) has made it possible to build effective industrial systems and applications. An authorized individual can monitor a vehicle’s current location and movement in an intelligent IoT transportation system. The authorized individual can also predict its future location and road traffic. In an earlier stage, unique RFID-identified objects were referred to as IoT. The term “Internet of Things” is associated with mobile devices, sensors, GPS devices, actuators, and other devices. The security of information and data privacy are the two main factors determining the acceptance of new IoT technologies and the services they provide (Kumar & Mallick, 2018). The Internet of Things (IoT) makes it possible to connect many things and automatically monitor, track, and collect meaningful and private data. Due to the high number of attacks on IoT, privacy protection is a more pressing concern in an IoT environment than in a traditional network.
The Internet of Things in Personal Medical Devices
IoT devices are also frequently utilized in healthcare systems for patient monitoring and evaluation. Personal Medical Devices, or PMDs, can be implanted inside a patient’s body or externally attached to that patient’s body to monitor their health. PMDs are tiny electronic gadgets that are getting more and more popular. By 2019, it is anticipated that these devices will have a market value of approximately 17 billion dollars (Burhan et al., 2018). These devices communicate with a base station via a wireless interface, which can also change the device’s parameters, read the device’s status, and provide medical reports. The wireless interface severely compromises the patient’s privacy and security.
These devices’ wireless interfaces are very vulnerable to cyberattacks that could jeopardize patients’ security, privacy, and safety. The primary objective in health care is to protect patient privacy from malicious attacks by maintaining network security. When criminals target mobile devices, they have predetermined objectives (Burhan et al., 2018). They usually want to steal information, attack devices to use up their resources, or shut down applications that track a patient’s condition. Eavesdropping, in which the patient’s privacy is breached; integrity error, in which the message is altered; and availability issues, such as battery-draining attacks, are just a few of the many types of attacks on medical devices. The following are some cyber security threats that affect the safety, privacy, and security of patient medical data:
- Any task that requires battery power requires PMDs. As a result, these devices must be able to handle some encryption. Integrity, confidentiality, availability, and privacy are all at risk if the device is a part of multiple networks.
- Because PMDs lack a wireless communication authentication mechanism. As a result, unauthorized individuals may easily access the device’s data.
- The absence of secure authentication exposes the devices to numerous additional security risks that could result in malicious attacks. An antagonist may launch denial of Service (DoS) attacks.
- Because patient data are transmitted over a transmission medium, unauthorized parties may alter them, compromising a patient’s privacy.
The Internet of Things in the Smart Home
As the number of IoT services for the smart home grows daily, digital devices can now communicate with one another effectively by using IP addresses. In a smart home environment, all devices are connected to the internet. The likelihood of malicious attacks also rises with the number of devices in the smart home environment (Burhan et al., 2018). Malicious attacks are also reduced when smart home devices are operated independently. At the moment, smart home devices can be accessed from any location at any time via the internet. As a result, malicious attacks on these devices are more likely.
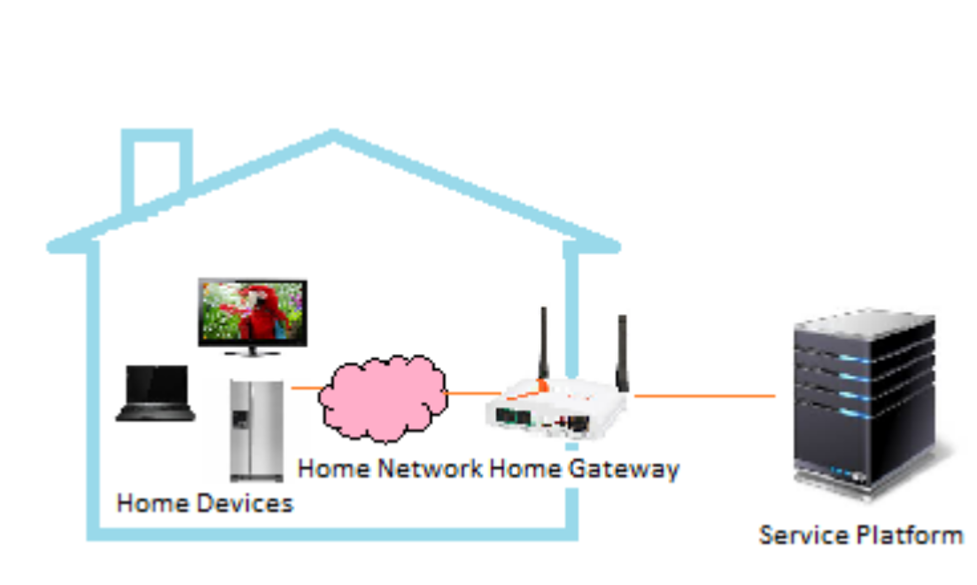
There are four components to a smart home: as depicted in Fig., the service platform, intelligent devices, home gateway, and home network 2. Numerous connected devices in the intelligent home intelligently share information over a home network. As a result, smart devices connected to the external network have a home gateway that controls how information flows between them. The service platform uses the services of a service provider to bring various services to the home network.
Discussions
In the Internet of Things (IoT), all devices and people are connected to provide services at any time or location. Most internet-connected devices lack compelling security features, making them vulnerable to privacy and security concerns like authenticity, integrity, and confidentiality, among others. In order to safeguard the Internet of Things from malicious attacks, certain security requirements must be met (Pal & Jadidi, 2021). A brief discussion of some of the essential capabilities of a secure network can be found here.
Resistant to assaults: If the system experiences a failure while transmitting data, it ought to be able to recover independently. For instance, a server operating in a multi-user environment must be capable of self-defense against intrusion or eavesdropping. If it were to go down, it would automatically recover without informing users that it was down.
Data Validation: The data and the information that goes with it must be verified. Data transmission from only authentic devices is permitted by employing an authentication mechanism.
Security measures: Access control is restricted to authorized individuals only. The system administrator must manage users’ usernames and passwords, and access rights must be defined for each user to access only the relevant parts of the database or programs.
Privacy for clients: The information and data should be secure. To protect the client’s privacy, authorized individuals should only access personal data. Any unrelated authenticated user from the system or any other type of client cannot access the client’s private information.
IoT Security Threats and Challenges
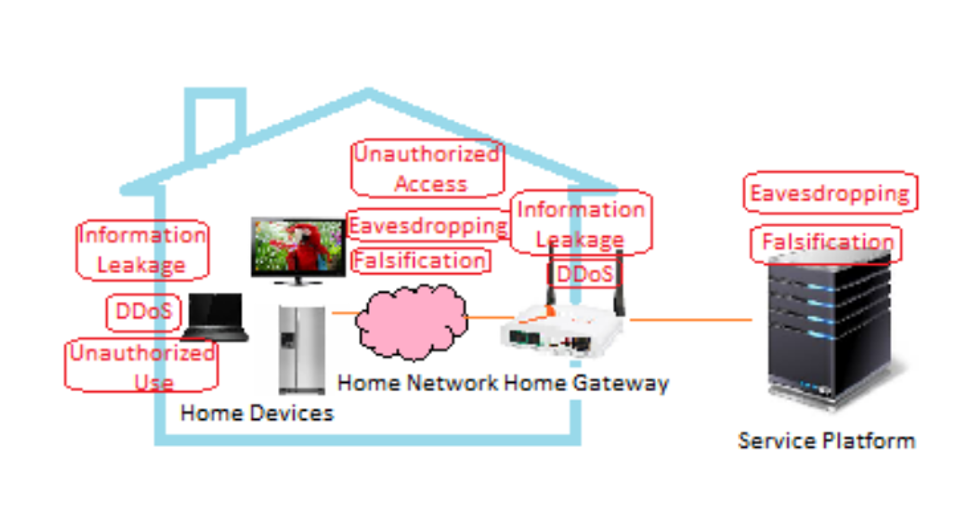
The Internet of Things has altered our way of life. The Internet of Things (IoT) has many advantages, but it also faces several security risks that we face every day. Most of the security dangers are connected with data spillage and administration loss. Security threats directly impact the physical security risk in the Internet of Things. The Internet of Things comprises different platforms and devices, each with its credentials. Because of this, each system has its own set of security requirements (Tyagi et al., 2020). Because much personal information is shared between various types, the user’s privacy is also the most critical aspect in Fig. 3. IoT-related threats to the smart home of equipment. Subsequently, a safe component is expected to safeguard the individual data. In addition, for IoT services, various devices communicate over various networks. This indicates numerous security issues at the network layer and user privacy. Additionally, user privacy can be compromised in a variety of ways. The following are some IoT security risks:
- Data life cycle protection through E2E: A complete network provides end-to-end data protection in an IoT environment to guarantee data safety. The data is instantly shared with other connected devices and collected from various connected devices. As a result, a framework is needed to manage information privacy throughout the entire data life cycle and protect the confidentiality of the data.
- Prepare for safety measures: IoT devices communicate and connect differently depending on the situation. As a result, the devices need to be able to keep up the level of security. For instance, if the home network’s sensors and local devices can safely communicate, their communication with external devices should also adhere to the same security policy.
- Accessible privacy and security: A large portion of the security and protection concerns are summoned by the misconfiguration of clients. Users will find it challenging and unrealistic to implement such intricate security mechanisms and privacy policies. Security and privacy policies that can be applied automatically must be chosen.
Smart Home Security Threats
Most service providers do not consider security parameters early on, and smart home services may be vulnerable to cyberattacks. Eavesdropping, information leakage, and Distributed Denial of Service (DDoS) attacks are just a few potential security risks associated with a smart home. Unauthorized access poses a threat to smart home networks. The following is a discussion of the potential threats to smart home security (see Figure. 3).
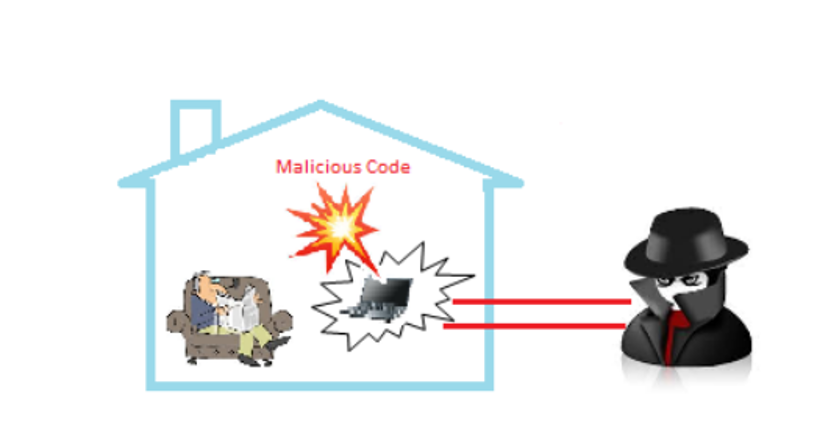
Intrusion: As depicted in Figure, the attacker can enter the smart home without damaging the doorway if the smart door lock is compromised by malicious codes or accessed by an unauthorized party. 4. This effect could lead to the destruction of property or the loss of life (Sengupta et al., 2020). Passwords that contain at least ten characters should be changed frequently to prevent such attacks because it is very difficult for attackers to break long passwords. Access control and a mechanism for authentication can also be used.
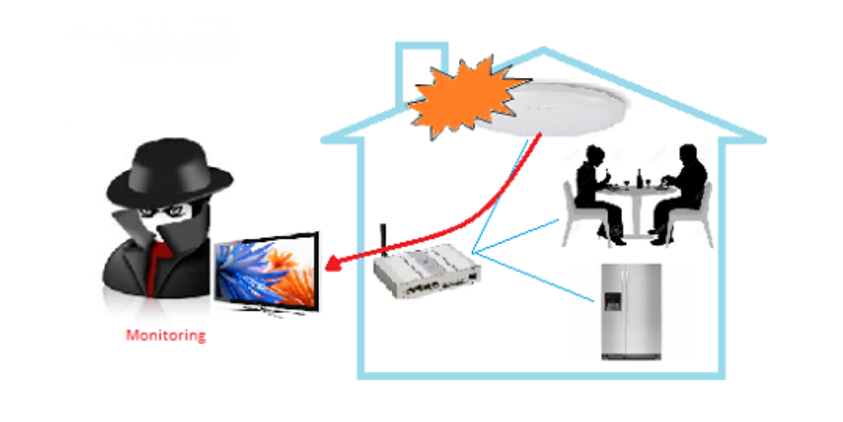
Personal information leakage and monitoring: A smart home’s primary purpose is to ensure safety. As a result, numerous sensors are utilized for various purposes, including housebreaking, baby monitoring, fire monitoring. As depicted in Figure, an intruder could monitor the house and gain access to personal information if these sensors were hacked. 5. Data encryption between the gateway and sensors or user authentication to detect unauthorized parties must be used to avoid this attack.
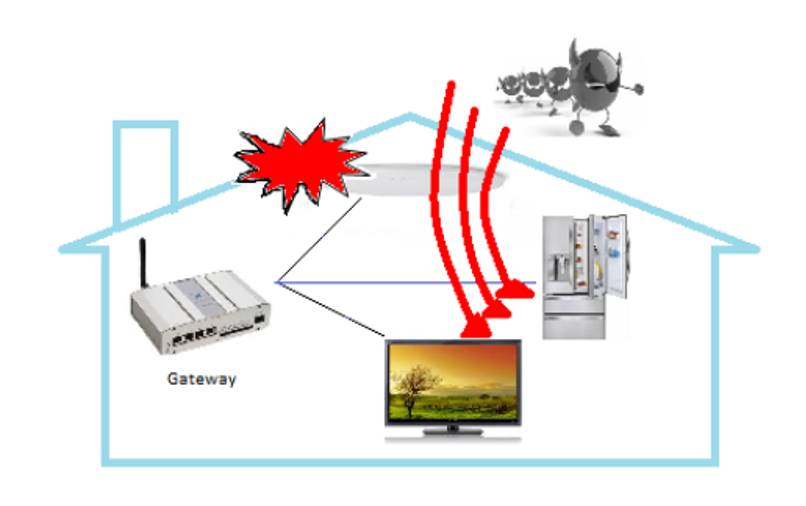
DoS and DDoS: Attackers may gain access to the smart home network and use Clear To Send (CTS) or Request To Send (RTS) to send many messages to smart devices. Figure depicts that they can also use malicious code to target a device and launch DoS attacks on other connected smart home devices. 6. As a result, these attacks drain resources from smart devices, making it impossible for them to perform their intended functions. Utilizing authentication to prevent and identify unauthorized access is critical to avoiding this attack.
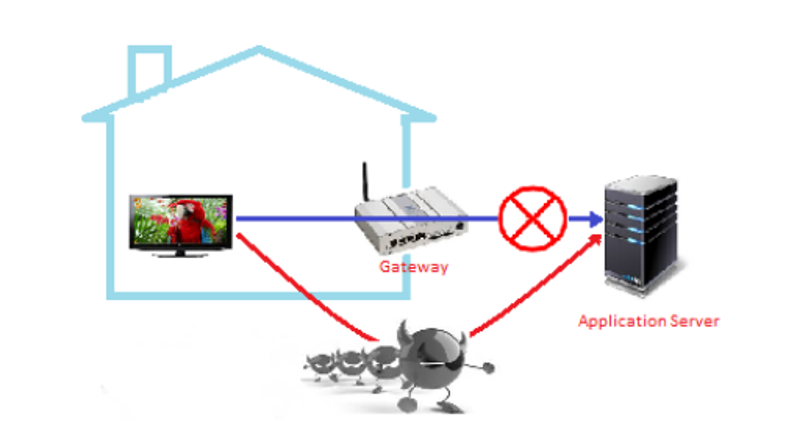
Exaggeration: As depicted in Figure, the attacker can change the routing table in the gateway to collect packets during smart home device communication with the application server. 7. An attacker can get around the forged certificate even though the SSL (secure socket layer) method is being used. The attacker may either reveal the confidential nature of the data or misunderstand its contents in this manner. The smart home network should be protected from this attack using the SSL technique and the appropriate authentication mechanism. Additionally, it is essential to prevent unauthorized devices from gaining access to the smart home network.
Strategies for IoT security
There are various ways to reduce risks and secure IoT network devices. Some of them are more advanced than others because they offer varying levels of protection. Depending on your threat model and whether the risk outweighs the effort, you may or may not implement all of the recommended security measures. Beginning with the simplest solutions and moving on to more complex ones.
Safe Internet Connection
A secure internet connection begins with the router, the point of connection between your Internet of Things devices, your network, and the rest of the internet. It’s a simple opening for pariahs to assault, assuming it is left open. On routers, replace the default network name, admin username, and password with safe alternatives that you frequently change (Panchiwala & Shah, 2020). Second, pick the router’s highest possible encryption level. If your current router only supports lower levels of encryption, you might want to switch to one that supports WPA2 encryption. Separating your IoT devices from your devices on separate networks can even improve internet security.
Create a System for Monitoring
In environments that host intricate networks of IoT devices and utilize them to execute key activities and analyze sensitive data, it is essential to keep a close eye on the health of the devices and the data flow. A monitoring system notifies you when something goes wrong and monitors the health of your equipment. It could be a strange data flow, a possible link to the internet and other network devices, or a suspicion of unintentional access.
Conclusion
The report has examined several current network security issues, as can be inferred from its conclusion. IoT devices frequently lack minimum security firewalls that would help prevent cyberattacks. There are a few genuine occasions of digital assaults that have been canvassed in the paper alongside the procedures for relieving these dangers. It’s possible that IoT devices don’t have enough security features. However, constant research and development allow businesses and individuals to equip themselves with efficient tools and techniques that can help them combat these risks.
Since the Internet of Things (IoT) came into being, it is abundantly clear that communication technology has advanced significantly, speeding up communication and enhancing people’s quality of life. To simplify work processes, various privacy models have been developed and implemented. In addition, despite the positive effects that the Internet of Things has had on society, they have also contributed to an increase in criminal activity, such as hacking, due to the numerous difficulties they face due to the presence of criminals and reckless users. The Internet of Things is plagued by security, performance, and data storage issues, which are being addressed by several solutions.
Recommendation
Before releasing IoT devices to the public, manufacturers should test them for security and dependability. The government should ensure that the Internet of Things (IoT) devices distributed to individuals and organizations meet at least the minimum requirements. Businesses should guarantee that they only invest in products with a solid reputation and dependability.
Refreshes aren’t just for a superior UI or more elements. They frequently fix old issues and patch security flaws. Your network is susceptible to attacks if the software on your Internet of Things devices is not kept up to date, particularly if they are frequently connected to the internet. There are several ways to protect your internet connection, such as encrypting data that leaves your internal network and concealing any sensitive information or vulnerabilities. One of the simplest methods is to use a VPN. A VPN increases security by concealing a device’s IP address and encrypting all data sent and received. The “kill-switch” feature of most VPNs also allows you to disconnect your internet connection if the VPN goes down. Your IoT device will never be exposed to the open internet because of this.
References
Abdullah, A., Hamad, R., Abdulrahman, M., Moala, H., & Elkhediri, S. (2019, May). CyberSecurity: a review of internet of things (IoT) security issues, challenges, and techniques. In 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS) (pp. 1-6). IEEE. https://ieeexplore.ieee.org/abstract/document/8769560/
Ahmad, M., Younis, T., Habib, M. A., Ashraf, R., & Ahmed, S. H. (2019). A review of current security issues in the Internet of Things. Recent trends and advances in wireless and IoT-enabled networks, pp. 11–23. https://link.springer.com/chapter/10.1007/978-3-319-99966-1_2
Almolhis, N., Alashjaee, A. M., Duraibi, S., Alqahtani, F., & Moussa, A. N. (2020, February). The security issues in IoT-cloud: a review. In 2020 16th IEEE International Colloquium on Signal Processing & Its Applications (CSPA) (pp. 191–196). IEEE. https://ieeexplore.ieee.org/abstract/document/9068693/
Burhan, M., Rehman, R. A., Khan, B., & Kim, B. S. (2018). IoT elements, layered architectures, and security issues: A comprehensive survey. Sensors, 18(9), 2796. https://www.mdpi.com/331358
Gurunath, R., Agarwal, M., Nandi, A., & Samanta, D. (2018, August). An overview: security issue in IoT network. In 2018 2nd International Conference on I-SMAC (IoT in Social, Mobile, Analytics, and Cloud)(I-SMAC) I-SMAC (IoT in Social, Mobile, Analytics, and Cloud)(I-SMAC), 2018 2nd International Conference on (pp. 104–107). IEEE. https://ieeexplore.ieee.org/abstract/document/8653728/
Hosenkhan, M. R., & Pattanayak, B. K. (2020). Security issues in the internet of things (IoT): a comprehensive review. New Paradigm in Decision Science and Management, 359-369. https://link.springer.com/chapter/10.1007/978-981-13-9330-3_36
Kagita, M. K., Thilakarathne, N., Rajput, D. S., & Lanka, D. S. (2020). A detailed study of security and privacy issues of the Internet of Things. arXiv preprint arXiv:2009.06341. https://arxiv.org/abs/2009.06341
Kumar, N. M., & Mallick, P. K. (2018). Blockchain technology for security issues and challenges in IoT. Procedia Computer Science, 132, 1815-1823. https://www.sciencedirect.com/science/article/pii/S187705091830872X
Mirza, M. A., Mahboob, R. M. M., Jahangir, H., Khawar, M., & Imam, M. (2022). Security Issues of IoT in Healthcare Sector: A Systematic Review. Soft Computing for Security Applications, 699-721. https://link.springer.com/chapter/10.1007/978-981-16-5301-8_50
Mohanta, B. K., Jena, D., Satapathy, U., & Patnaik, S. (2020). Survey on IoT security: Challenges and solution using machine learning, artificial intelligence, and blockchain technology. Internet of Things, 11, 100227. https://www.sciencedirect.com/science/article/pii/S2542660520300603
Pal, S., & Jadidi, Z. (2021). Analysis of security issues and countermeasures for the industrial internet of things. Applied Sciences, 11(20), 9393. https://www.mdpi.com/2076-3417/11/20/9393
Panchiwala, S., & Shah, M. (2020). A comprehensive study on critical security issues and challenges of the IoT world. Journal of Data, Information, and Management, 2(4), 257-278. https://link.springer.com/article/10.1007/s42488-020-00030-2
Sengupta, J., Ruj, S., & Bit, S. D. (2020). A comprehensive survey on attacks, security issues, and blockchain solutions for IoT and IIoT. Journal of Network and Computer Applications, 149, 102481. https://www.sciencedirect.com/science/article/pii/S1084804519303418
Shakya, S. (2022). A Perspective Review of Security Issues in IoT with Cloud Environment. Journal of IoT in Social, Mobile, Analytics, and Cloud, 4(2), 84–93. https://irojournals.com/iroismac/V4/I2/02.pdf
Sial, M. F. K. (2019). Security issues in the Internet of Things: A comprehensive review. American Academic Scientific Research Journal for Engineering, Technology, and Sciences, 53(1), 207-214. http://www.asrjetsjournal.org/index.php/American_Scientific_Journal/article/view/4565
Sultan, A., Mushtaq, M. A., & Abubakar, M. (2019, March). IoT security issues via blockchain: a review paper. In Proceedings of the 2019 International Conference on Blockchain Technology (pp. 60-65). https://dl.acm.org/doi/abs/10.1145/3320154.3320163
Thakkar, A., & Lohiya, R. (2021). A review on machine learning and deep learning perspectives of IDS for IoT: recent updates, security issues, and challenges. Archives of Computational Methods in Engineering, 28(4), 3211-3243. https://link.springer.com/article/10.1007/s11831-020-09496-0
Tyagi, A. K., Agarwal, K., Goyal, D., & Sreenath, N. (2020). A review on security and privacy issues in the internet of things. Advances in computing and intelligent systems, pp. 489–502. https://link.springer.com/chapter/10.1007/978-981-15-0222-4_46
 write
write