Abstract
The extensive use of the Internet and the rapid development of technology have had many good benefits for society, but they have also increased the number of cyber criminals who prey on unwary individuals, particularly children. Cybercriminals employ deceitful techniques to trick youngsters into disclosing personal information, participating in risky online conduct, or falling victim to financial thievery or exploitation. Increasing awareness of these hazardous behaviours is vital to safeguard youngsters from damage.
This abstract summarizes the approaches to teaching children how to identify and avoid falling prey to internet scam artists. The strategies addressed include parental monitoring, educational programs, and group engagement. Schools and other educational institutions provide programs that teach children about the dangers of cyberscams, the many types they may face, and how to detect and avoid them. Interactive technology, such as online games or simulations, provides a thrilling and immersive learning experience that teaches youngsters how to recognize and respond to fraudulent practices.
Parental supervision is essential in training children to avoid becoming victims of Internet scams. By creating guidelines and monitoring their children’s conduct, parents and teachers can teach them about online safety. Awareness-raising campaigns, seminars, and community outreach initiatives are organized with law enforcement agencies, academic institutions, and other groups.
Teaching youngsters how to recognize and avoid internet fraud has far-reaching implications. Children may be better equipped to defend themselves online, avoid being victims of online fraud, and make educated judgments when using the Internet if they have greater information. Children are encouraged to use care, judgment, and attentiveness while interacting online, and a culture of responsible digital citizenship is promoted.
1. Introduction
The Philippines’ DepEd and Commission on Higher Education (CHEd) accepted online education in 2020, making it the standard. One of the “distance learning” options used to keep the school year going despite the epidemic is an online education, commonly known as E-learning. Online learning has largely replaced face-to-face instruction, allowing students to complete their education independently of the political situation. Avoid COVID-19 by studying at home and quitting any upcoming online courses. Even though online students are virus-free, additional security problems must be addressed. Online students can communicate with their teachers and peers through various methods, including social networking sites and video conferencing software. According to the Department of Justice’s Office of Cybercrime, these sites and the Internet, in general, are vulnerable to cyberattacks that might endanger schoolchildren. Malware and phishing are two such threats.
Since the advent of virtual lecture halls, several incidents of student exposure to online hazards have been documented. Recommendations from the Department of Justice’s Cyber Crime Office to protect young students participating in online courses. At a recent conference, the DOJ’s Office of Cybercrime informed CNN Philippines that it had received instances of malicious persons hijacking online classes and showing improper content to the participants, who were largely students. Both the Polytechnic University of the Philippines (PUP) and the Far Eastern University (FEU) were attacked by hackers in June. The incident was taken very seriously because of the sensitive nature of the data held on the university’s online portals. Both colleges advised students to update their portal accounts’ default passwords. Because online dangers can come at any time and from any location, students must know how to prevent them.
Faced with increasing risks, academics have investigated several potential strategies for improving the Security of online learning. Even though the Internet provides several educational benefits, kids may experience risks and hazards when utilizing it. This study aims to see if and how much students are aware of and prepared for the hazards and advantages of online education. The debate on this problem has grown disconnected, inconsistent, and widely scattered over various venues, including news stories, scientific publications, and educational reports. We can help make online education safer and raise students’ awareness of online hazards by sharing the information in this article with them.
2. Literature Review
All software should be safe, but this is especially crucial when dealing with children. Within the realm of Security, cybersecurity is an important sub-challenge. The phrase “cybersecurity for kids” refers to investigating all potential online threats to children, creating preventative measures for children and their parents, and teaching children about the numerous cybersecurity hazards they face. Child-computer interaction (CCI) researchers have long been concerned with preserving children’s privacy and safety. Evaluate the literature to offer an overview of CCI research in 2013. The researchers identified four key topics of concern to the CCI community, including the penetration of social and cloud technologies and possible Security and privacy risks to children. Because of the remarkable degree to which today’s children are involved in technology from an early age, these privacy and security challenges are no longer restricted to CCI study.
The number of internet-connected devices held by youngsters has reached an all-time high. They learn how to use technology rapidly and effectively. This age group is increasingly using the Internet and social media. Conducted a review of the literature on children’s internet use and uncovered many dangers that children face when using the Internet (Rahman et al.,2020). The authors divided the problems they discovered into five categories: content hazards, contact risks, youngsters being targeted as clients, financial risks, and worries about online privacy. Authors divide content dangers into three broad categories: illegal (such as content about child sexual exploitation), harmful or age-inappropriate (such as pornography), and harmful advice (such as content that could influence a child to use alcohol and drugs, commit suicide, or develop various psychological or dietary disorders). The authors emphasize two types of contact-related harm: cyberbullying and cyber grooming. This study gives a risk taxonomy and a high-level software architecture designed with current internet security and privacy concerns in mind.
According to research, children who spend much time on social media are more likely to be injured. Younger children were assumed to be less in danger (particularly from privacy issues) than teens since they may not utilize social media or spend as much time online. However, this claim may no longer be valid. Younger children who do not use social media may be concerned about the privacy threats posed by today’s smart devices. Livingston et al. (2015) examined 26 major research investigating the privacy hazards of smart gadgets for children. The study’s authors identified two categories of threats (technical and domain-specific) and suggested solutions for each. The authors discovered three major privacy risks in their investigation of smart toys: use, retention, and disclosure limitation; consent and choice; and openness, transparency, and notice.
The following are the first three ISO privacy principles. In addition, the authors proposed domain-specific and technological solutions for dealing with privacy problems in smart toys. Because of the expansion of digital spaces and technological advancements, cyberbullying has received increased public and academic attention as a severe danger to online safety. Pinter et al. conducted a comprehensive evaluation of 132 peer-reviewed articles on the issue of internet safety for teenagers in 2017 and identified key themes. One of the numerous striking outcomes from the review research was that cyberbullying was addressed in 66% of the assessed literature. Several comprehensive literature studies dealing directly with cyberbullying were discovered. Aponte and Richards present research on improper behaviour by or toward children online (and sometimes offline). The researchers have focused on cyberbullying and identified its origins, as well as the myriad risks and effects that come with it.
Only a few of the various kinds of cyberbullying highlighted by the researchers include flaming, cyber-harassment, denigration, impersonation, masquerading, outing, dishonesty, ostracism, and exclusion. The authors first identified the risks, then examined existing non-technological and technological strategies implemented or proposed to reduce or avoid the likelihood and impact of the various types of cyberbullying they identified, and finally provided some recommendations for preventing the risks and their effects. In review studies, several more academics have examined cyberbullying from a number of angles. For example, explored the causes, consequences, and context of cyberbullying among teenagers. Defined cyberbullying and investigated other related issues such as perpetrator roles, victim demographics, the causes of cyberbullying, the differences between cyberbullying and more traditional forms of bullying, and the impact of gender on cyberbullying. Their evaluation of the literature directed at youths aged 12 to 18 includes an investigation of therapies for depressive symptoms caused by cyberbullying.
Teenagers, in particular, are frequently concerned about being exposed to unsuitable information. To determine the repercussions of young exposure to pornographic information on the Internet. A recent study review examined the ramifications of young people’s online access to sexually explicit information. The researchers focused on how teens’ changing brains and personalities affected their viewpoints, behaviours, and self-perceptions. The viability of employing gaming technology to improve numerous critical aspects of security education and awareness. The authors of this paper look at studies of games’ potential to teach players about cybersecurity.
The writers undertake a literature review first and then explore potential applications in the game business. This study offered evidence that gaming may be a useful method for boosting cybersecurity awareness, but it also identified several limitations that should be considered in future research. Investigated and graded seven distinct cybersecurity video games in 2015. The researchers analyzed the games’ performance in delivering the content and keeping students engaged, with the ultimate objective of establishing new gaming platforms to educate cybersecurity.
Researchers found beneficial and ineffective components of gameplay, as well as many ways for teaching cybersecurity to youngsters, as a result of the examination. According to the researchers, the findings of their evaluations were to be used as inspiration for future cybersecurity-themed games aimed at children. The review papers cited above are all pertinent to our study, but they scrape the surface. In this literature review, we examine cybersecurity flaws in greater depth. We selected research that looked at a wide range of cyber hazards to children rather than focusing on just one. We also investigated several techniques of evaluation and the hazards they provide, and various approaches to raise cybersecurity awareness. This review study is the only one that we know comes close to matching the scope and breadth of our work.
2.1 Theoretic framework
Internet security and hazards should be grasped theoretically. Two hypotheses prompted this study’s research:
Organizational Theory
Teachers and school authorities may use the framework offered by organizational theory. This concept is being used to create standards for cybersecurity classroom education. Teachers and school authorities are responsible for preparing their students for the threats they may encounter online. This principle can be used to eliminate ambiguity. Using this method, we may identify the most important features of internet security.
Students Voice
Students may express their opinions and feelings. Hearing from students is critical to enhancing school reform efforts’ quality, relevance, and success. Understanding internet safety necessitates hearing from students’ perspectives. Through an information revolution, student voices create a space where others may find good, true, and thought-provoking content.
Synthesis
How can I, as a researcher, ensure that my students may safely utilize the Internet for online learning? This has both good and bad implications for online education. As a result, many students have the opportunity to experiment with various online learning tools and apps and get insight into what can and cannot be done in this context. Students will learn self-discipline, responsibility, and how to adjust to changing situations. Unfortunately, many students cannot benefit from online education because they need access to computers, cell phones, and other critical technologies. These are two examples of possible process changes. As a result, students in their last year of high school at Emilio Aguinaldo College-Cavite should discuss how to be safe while studying online.
3. Methodology
3.1 Research methodology
A sequential exploratory strategy was applied for senior high school students at EAC-Cavate. According to Creswell and Plano Clark (2018), a sequential exploratory design integrates qualitative and quantitative data collecting and analysis in several steps. Researchers collect and analyze qualitative data in the first step to inform the next data collection stage, which may include a survey or other types of quantitative data collection. The Qualitative Analysis’ Conceptual Foundations When the researcher is interested in the participants’ interpretations of an event or phenomenon, a qualitative design is utilized in qualitative research. A correlational technique will be applied for the quantitative components of the investigation (Edwards et al.,2020). As a consequence, a non-experimental research approach is one in which the researcher studies two variables, comprehends and evaluates their statistical relationship without the influence of any other factors, and draws conclusions based on the findings.
3.2 Sampling Technique
The researchers employed a technique known as “convenience sampling as a non-probability sampling strategy in which participants are chosen depending on their availability and level of readiness. Students commonly use this sampling approach due to its low cost and ease. The researchers employed a sample size of one hundred pupils from EAC-Cavite Senior High School. Senior High School Students’ Attitudes Towards Research: An exploratory research was conducted to determine the sample size for the current investigation. Senior high school students at EAC-Cavite are eligible, but their willingness to participate depends on the researcher’s contact. Participants will be chosen by convenience sampling from all graduating high school students at Emilio Aguinaldo College-Cavite.
3.3 Research Instrument
The researchers devised a questionnaire and an interview to serve as data-gathering techniques. Reading various sources, such as undergraduate theses and the Internet, laid the groundwork for the questionnaire’s acceptance and growth. Participants submitted their responses using Google Forms.
The survey was broken into four sections. The first section covers how well you comprehend the Internet’s dangers. The second section discusses how well-informed people are about online hazards. The final section discusses why being aware of potential Internet risks is so important. The fourth section discusses the importance of cybersecurity expertise. The qualitative approach interviews were conducted through Google Meet. Users of Google Meet can conduct video conferences for businesses or schools. The data was compiled using note-taking and recording procedures.
3.4 Data Gathering Procedure
A questionnaire is a research instrument consisting of a sequence of questions and responses from which respondents can select. Respondents will submit their replies using the Google Form. The questionnaire utilized was industry standard. There will be an anticipated response type and multiple choice and scaled questions. Its contents will be objectively examined.
3.5 Data Analysis Procedure
Data collection and analysis occur concurrently in a basic interpretive qualitative study design. All of the interviews for this analysis were taped and transcribed. As she listened to each interview, the researcher reviewed the transcripts for correctness. Each participant’s response to each question was considered a single data point throughout the coding procedure. Gibbs defines coding as “how you define what the data you are analyzing are about.” A ranked and topicalized presentation was created using the classified information.
Quantitative data were obtained using survey questions made in Google Forms and evaluated using a correlational approach (Wang et al.,2019). According to the University of the West of England (2020), correlation is a tool for studying the relationship between two quantifiable, reliable data, such as age and blood pressure. The researchers utilized Pearson’s coefficient of correlation (r) to examine the data collected for this layout. It keeps track of how many times the two objects are linked.
Figure 1
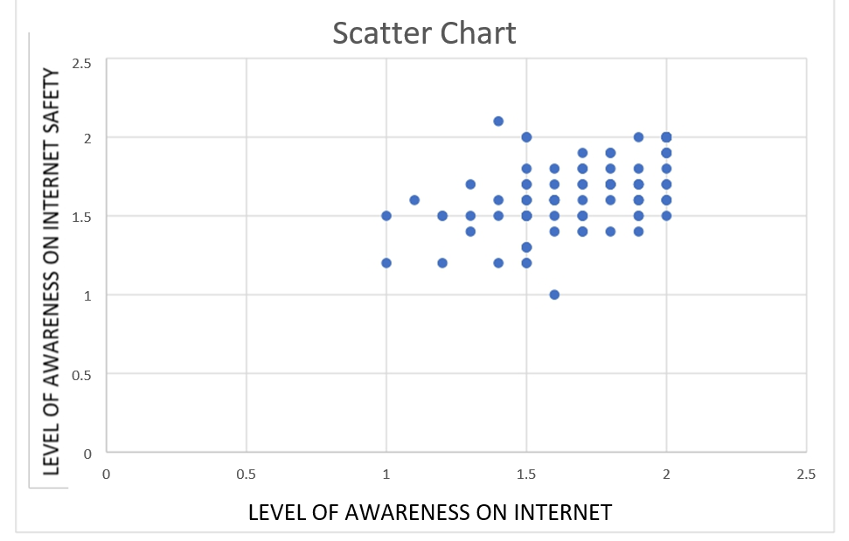
Figure 1: Displays a correlation graphic between the two variables, x and y. The variables rise simultaneously, although some points appear scattered and fall at random on the plot, indicating a moderately positive correlation between the variables with a correlation coefficient (r) of 0.5706.
Figure 2
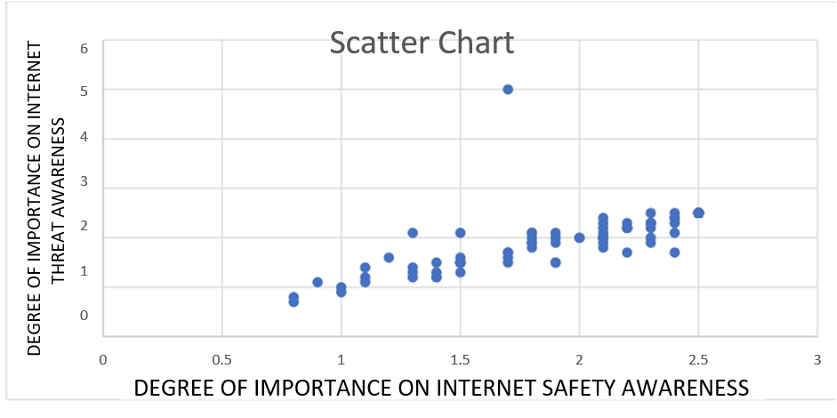
Figure 2: Displays the correlation diagram between variables x and y. The correlation coefficient (r) or r = 0.7493 implies a substantial positive association between the variables.
4. Implementation
Developing ways to teach children about online fraudsters necessitates a multifaceted approach, including various stakeholders, including parents, educators, law enforcement, and the general public. Keep the following in mind while employing such techniques:
Community-based projects or the incorporation of educational programs into school curricula should be used to raise awareness about cyber fraudsters. These programs should be age-appropriate, interesting, and tailored to the specific needs of children at distinct developmental stages. The content should address topics such as recognizing common cyber scamming strategies, understanding the risks of sharing personal information online, and learning how to prevent being a victim of cyber scammers. Collaboration with teachers, schools, and other educational groups may help ensure that projects are effectively implemented and reach many children.
Interactive Tools:It is feasible to teach children about online fraud fun and excitingly by utilizing interactive tools such as online games, simulations, or quizzes. These websites can provide children with real-world examples that they can use to practice critical thinking and identify potential internet scams. They can also underline the need to protect personal information and practice safe online behaviours. Collaboration with designers and technology specialists may aid in developing interactive tools that interest children and encourage them to take an active role in their learning.
Parental guidance:Parents and other people who care for children must teach them about internet fraud. They should be made aware of the threats presented by cyber fraud and advised on how to convey online safety to their children. This includes creating clear standards and limits for internet usage, teaching children to be cautious when sharing personal information online, and going through defensive measures for potential online scams (Zhang-Kennedy & Chiasson, 2021). Parental involvement and control of children’s online activities can reinforce the lessons imparted through educational programs and interactive technology.
Community Involvement:Coordination to teach children about cyber scams with the community’s assistance is easier. Cooperation with law enforcement agencies, neighbourhood groups, and other community stakeholders can help raise awareness of the hazards of cyber fraud through campaigns, workshops, or outreach activities. Involving the greater community may help create a good environment encouraging young people to practice safe online behaviour and seek help when they encounter cyber fraud.
Adopting ways to teach children against online scammers: should be a continual process that includes regular review and constant progress. Tracking the success of instructional endeavours, interactive technology, and community participation activities can assist in identifying areas for improvement and give recommendations for future planning. Feedback from children, parents, teachers, and other stakeholders may be obtained to help develop the plan and provide critical insights into the effectiveness of the measures.
Finally, implementing techniques to teach children about cyber-scammers necessitates a collective effort involving parents, schools, law enforcement, and the greater community. Through educational programs, interactive technologies, parental supervision, and community participation, children may be provided with the knowledge and skills they need to detect and avoid falling for online fraud. Regular assessment and continuous improvement are required to ensure the efficacy of these measures and preserve children’s online safety in today’s digital world.
5. Results and discussion
Teaching youngsters about cybercriminal methods is important to securing their online safety. Parents may safeguard their children from internet harm by teaching them about the hazards and countermeasures hackers use. Investing in online fraud education for minors may result in the following benefits:
Teaching youngsters about typical types of online fraud, such as phishing, social engineering, and identity theft, raise their awareness of potential online dangers. They can detect possible risks, avoid questionable communications and websites, and report unusual or harmful online conduct.
Learning about internet schemes can help children develop critical thinking abilities by training them to question the authenticity of information and the demands they meet online. Adolescents can learn to judge the credibility of online communications and bargains as they acquire experience, protecting themselves from scammers and unwelcome requests for personal information.
Teaching youngsters about cybercriminal strategies may encourage safe online habits such as avoiding giving personal information, using strong passwords, keeping all software and antivirus applications up to date, and being cautious when engaging with strangers online. These safeguards are essential for protecting children’s internet privacy and safety.
When young people learn to detect and avoid typical scams, their confidence in dealing with online dangers grows. They may learn to ignore doubtful requests for personal information, to seek the advice of a trustworthy adult when in doubt, and to report incidents of online deceit. Adolescents may protect themselves and their companions from fraud by properly controlling their online identities.
Raising knowledge about cyber-scamming tactics is an effective way to reduce children’s vulnerability to online fraud. Children with more information, critical thinking skills, secure online habits, and confidence in dealing with dangers are less likely to be duped by online fraudsters and experience financial loss or identity theft.
Children are aware of cybercrime may become champions for online safety at home and in their communities. They may seek to teach their classmates and maybe even their parents about the hazards of online fraud(Richardson et al.,2017). This might have a beneficial knock-on impact, with more people becoming aware of the need for safe online conduct and be encouraged to adopt it.
Investing in initiatives that teach young people how to spot and avoid internet deceit can pay off handsomely. It can give students the information, critical thinking skills, secure online behaviours, and self-assurance they need to identify and prevent online fraud. Raising a generation of cautious and observant Internet users can contribute to making the Internet a safe place for youngsters to explore. As a result, the chance of online fraud will diminish.
Discussion
Because of the proliferation of online risks, it is critical to educate youngsters about the strategies used by cybercriminals nowadays. One way to help youngsters become mature, safe Internet users is to teach them about the hazards of cyber fraud and how to protect themselves. When teaching youngsters about internet scams, keep the following points in mind.
- Get a head start: Teaching young children about internet safety is critical. As soon as youngsters are introduced to computers or the Internet, parents and teachers should begin educating them about the hazards of cyber fraud.
- Children should be informed about cyber fraud, including phishing, online identity theft, bogus websites, online grooming, and social networking scams. Use age-appropriate language and examples to help youngsters understand how these systems work.
- Teach kids the importance of keeping their name, address, phone number, and other personal information secret and never sharing it publicly or online. Inform them that con artists may use this information to attack their family members.
- Create Skepticism Teach your children to be cautious of Internet offers that appear too good to be true and apply critical thinking skills when they get unsolicited communication, such as emails, messages, friend requests, etc. Encourage youngsters to question and check the truth of Internet content before clicking on links or sharing personal information.
- Teach your children safe online practices include avoiding encounters with strangers, not installing software or apps from unknown sources, and keeping their passwords and login information private (even from friends).
- Investigate the Consequences of Cyber Scams. It is critical to teach youngsters about the consequences of falling victim to cyber scams, which include money loss, identity theft, emotional pain, and reputational injury. Inform them that online fraud is a serious crime with significant implications for the victims. Consult a trustworthy and responsible adult, such as a parent, teacher, or guidance counsellor, when in doubt. Instil confidence in your children to question or report any dubious internet information.
- Keep communication lines open by allowing youngsters to share their internet activity freely. Make a safe area for youngsters to talk about their experiences with internet scams without fear of repercussions (Lagazio et al.,2014). Children learn through watching their parents and other authorized people. Show how to be a responsible Internet user by withholding unneeded information and always using common sense.
- Because cyber scams are always developing, it is critical to remain current on con artists’ latest trends and strategies. Maintain current knowledge of the latest kinds of Internet fraud so that you can aid your children in being attentive and secure.
Finally, the safety of children must educate them on the strategies used by internet scam artists. We can give age-appropriate instruction, stimulate critical thinking, model secure online conduct, and keep communication lines open to help youngsters become responsible Internet users and avoid falling prey to online scams.
Recommendations
Here are some ideas for educating children about the tactics used by internet scammers:
- Use Age-Appropriate Language: When discussing online fraud with children, use language appropriate for their maturity level. Instead of complex explanations and technical jargon, use simple language everyone can comprehend.
- Utilize Interactive and Engaging Techniques: Use interactive and engaging strategies to make learning more pleasurable and remembered. To vividly and effectively teach the concepts of online fraud, use age-appropriate games, videos, and interactive activities.
- Use Real-Life Examples: Give children real-life examples to help them understand how internet scams work. Share news articles or stories of cases of people falling victim to cyber scams, stressing the outcomes. This can help children grasp the gravity and consequences of online deception.
- Instil the Value of Privacy: Teach children the importance of protecting their online identities. Emphasize the significance of never disclosing personal information, such as your full name, address, phone number, or password, with anybody you do not trust or without their consent.
- Teach Children to Think Critically: Children should be taught to think critically as they traverse the digital world. Teach your children to be cautious of any online offers, demands, or messages that sound suspicious or overly tempting (Quayyum et al.,2021). Encourage the development of healthy Skepticism in youngsters, as well as the ability to appraise the authenticity of internet material.
- Discuss Red Flags: Teach children about common red flags that may indicate cyber fraud, such as requests for personal information, unsolicited emails or texts, ominous-looking URLs or files, and threatening or urgent language. Teach youngsters to be cautious and vigilant when they see these online warning signs.
- Discuss Social Engineering tactics: Explain to children the social engineering tactics used by online fraudsters, such as impersonating someone else, manipulating emotions, or creating a sense of urgency. Discuss the techniques that con artists may employ to get someone to provide personal information or engage in harmful activity.
- Teach youngsters to avoid connecting with strangers online, clicking on unexpected links or downloading unknown software, and not to give their passwords or other important information to anybody, including their friends.
- Encourage children to report suspicious requests: Create an environment where children feel secure reporting any suspicious requests or circumstances they encounter online. Encourage children to tell a trustworthy adult, such as a parent, teacher, or counsellor, about anything that makes them suspect.
- Encourage Open contact: Maintain open lines of contact with your children and encourage ongoing talks about their online use. Create a judgment-free, safe environment where children may openly share concerns or questions about internet safety or cyber fraud.
By following these guidelines, you may teach children about the techniques used by online fraudsters and help them obtain the information and skills required to defend themselves. Keep in mind that cyber threats are always evolving, so it is critical to examine these lessons on a regular basis and remain up to date on the most recent advancements in online fraud.
6. Conclusion
In this age of widespread digital technology, educating young people about cyber criminals and their strategies to conduct fraud is critical. Because children are so readily persuaded, providing them with the knowledge and skills they need to be safe online is critical. Finally, the greatest method to safeguard children against online predators is to educate them about cyberscams and how they operate. Early instruction, a comprehensive approach, interactive methods, empowering children to be cautious and critical, and continuous reinforcement can raise children’s awareness of cybercriminals and protect them from falling for online fraud. We can help youngsters develop into responsible digital citizens who can detect and avoid possible threats by providing them with the knowledge and skills they need to stay safe online.
References
Edwards, M., Rashid, A., & Rayson, P. (2015). A systematic survey of online data mining
technology intended for law enforcement. ACM Computing Surveys (CSUR), 48(1), 1–54.
Lagazio, M., Sherif, N., & Cushman, M. (2014). A multi-level approach to understanding the
impact of cybercrime on the financial sector. Computers & Security, pp. 45, 58–74.
Livingstone, S., Davidson, J., Bryce, J., Batool, S., Haughton, C., & Nandi, A. (2017). Children’s
online activities, risks and safety: a literature review by the UKCCIS evidence group.
Quayyum, F., Cruzes, D. S., & Jaccheri, L. (2021). Cybersecurity awareness for children: A
systematic literature review. International Journal of Child-Computer Interaction, 30, 100343.
Rahman, N. A. A., Sairi, I., Zizi, N. A. M., & Khalid, F. (2020). The importance of cybersecurity
education in school. International Journal of Information and Education
Technology, 10(5), 378-382.
Richardson, M. D., Lemoine, P. A., Stephens, W. E., & Waller, R. E. (2020). Planning for Cyber
Security in Schools: The Human Factor. Educational Planning, 27(2), 23–39.
Wang, Y., Han, J. H., & Beynon-Davies, P. (2019). Understanding blockchain technology for
future supply chains: a systematic literature review and research agenda. Supply Chain
Management: An International Journal, 24(1), 62–84.
Zhang-Kennedy, L., & Chiasson, S. (2021). A systematic review of multimedia tools for
cybersecurity awareness and education. ACM Computing Surveys (CSUR), 54(1), 1-39.
 write
write