Abstract
Data outsourcing is becoming more prevalent as effective strategies enable businesses to depend on outside providers for data management and storage. Data transfer is turning into a significant problem as information system outsourcing rises. Data security has become a global issue for governments and businesses. The paper discusses how an organization might deal with problems with data-sharing while outsourcing service providers. The findings indicate that a well-drafted contract will reduce the danger that outsourcing data presents. However, most service agreements do not adequately address the difficulties of data collecting. Data breaches, integration problems, and illegal access to private data are some of the challenges that might arise with outsourcing data. Organizations must thus use the finest techniques to guarantee that data is handled correctly when it is outsourced to a service provider. The successful implementation of the outsourced project and the outsourcing partnership depend on the data exchange. To secure data effectively while outsourcing, it is crucial that both the customer and service provider use the optimal security measures.
Introduction
The outsourcing of information technology (IT) infrastructure has increased dramatically across all sectors, including the government, industrial, and pharmaceutical industries (Elias Malope & Naidoo, 2020). More and more businesses are teaming up with third-party software and service providers to handle their IT-related needs, such as application development, system integration, and IT management. Outsourced data may help businesses run more smoothly and effectively in the marketplace if done correctly. While many businesses have found success outsourcing their development efforts to a software service provider, many have also found that data transmission is a significant barrier. Data inconsistencies on the part of the vendor may lead to poor project results, compromised security, and even the loss of information should include the outsourcing agreement between the client and vendor end (Hintze, 2018). Data maintenance problems create difficulties for the client and the outsourced service provider. There is an increasing tendency toward maintenance; however, few service contracts adequately handle data outsourcing or management concerns (Elias Malope & Naidoo, 2020). As more and more businesses are turning to third-party suppliers and service providers, this paper will discuss how such businesses might handle data sharing issues.
Definition of terms
Information systems (IS) outsourcing is the practice of a business delegating its IS responsibilities to outside service providers in order to reap financial, technical, and strategic advantages (Almutairi & Riddle, 2018). Information systems outsourcing is the choice made by the company to outsource some or all of its IS operations to accomplish its objectives.
Data management is creating and applying rules, processes, and procedures to manage an enterprise’s whole data lifecycle requirements (El Arass & Souissi, 2018). When data is gathered and maintained by a software vendor or service provider, problems may arise if the upkeep management is improper. Adequate data management necessitates the gathering, analyzing, and using models for decision-making to ensure efficient data upkeep. Over the last several decades, a growing practice has been to outsource all or a significant portion of data maintenance to a third-party service provider as part of a maintenance service contract.
Literature Review
One potential benefit of outsourcing IT is that it allows the business to devote more resources to other areas, such as brand building, customer service improvement, and product development (Elias & Naidoo, 2020). IT outsourcing providers’ potential to provide more advanced IT capabilities might improve the company’s efficiency and output. Another benefit of outsourcing IT is that it provides companies with access to IT experts that have received extensive training and certification. According to Gurung and Prater (2017), IT service providers should not rely on a single person’s expertise but instead should put together a group of people who have shown themselves as competent in the field. Because of this, the business may avoid having to pay to train new IT workers. The figure below shows how businesses are increasing their investment in IT outsourcing due to its immense benefits and opportunities it exposes the businesses too.
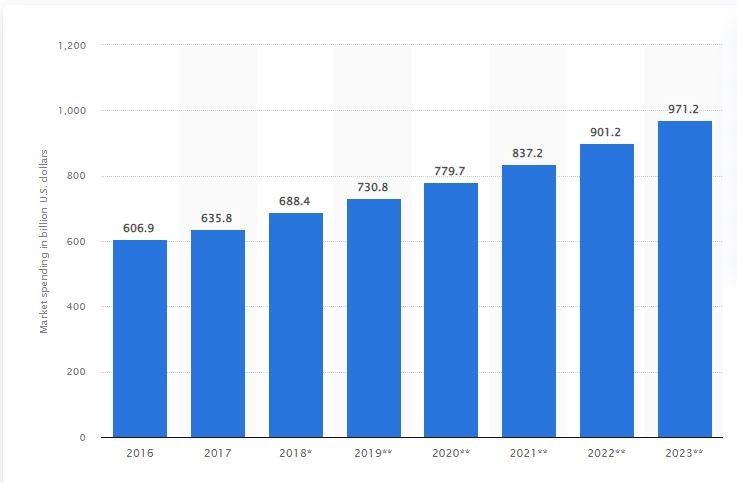
Figure 1: Global spending on IT outsourcing services in 2018. (Statistica,2019).
By using the service provider’s buying power and supplier connections, outsourcing IT allows organizations to save money on capital-intensive IT resources, including hardware, software, licenses, and in-house IT staff (Gurung & Prater, 2017). When customers outsource their IT services, they have access to cutting-edge tools that allow them to expand and improve their operations. Organizations may save operational costs by outsourcing the hosting and maintenance of their IT services to a service provider, who will also be in charge of IT infrastructure updates, security patches, skill development, and general maintenance (Elias & Naidoo, 2020). Additionally, outsourcing IT helps lessen the possibility of IT failures. TA service providers’ better-pooled skills and expertise allow them to assume responsibility for issues like adherence, data leaks, contingency planning, and recovery plans (Gurung & Prater, 2017). Compliance, security, and dependability of IT services are all potential threats, but they may be mitigated when reputable IT service providers collaborate with other skilled third parties to maintain their current data centres up to date with legislation and technology ( Gurung & Prater, 2017).
Outsourcing provides businesses enticing benefits, including cost savings, the capacity to focus on core company operations, flexibility, and quality enhancement (Almutairi & Riddle, 2018). Security issues, such as breaches of confidentiality and availability failures of IS services [3], are more likely to occur in the outsourcing setting due to the less stable surroundings and increased systems integration. Almutairi & Riddle (2018) contend that serious difficulties and worries accompany the growing reliance on technology and the need to outsource IT requirements in businesses. Migration processes, technological operations, and data security are all technical difficulties; interpersonal conflicts and misunderstandings are examples of human difficulties. Almutairi & Riddle (2018) proposed the OSCR framework to efficiently handle the security and compliance risks related to IS outsourcing. It intends to provide businesses with a thorough technique to reduce, neutralize, or remove security threats in the early phases of project execution. The suggested framework is flexible, straightforward, and simple and may be used for any outsourced IT project.
Park et al. (2021) state that most healthcare companies are very concerned about keeping the privacy and security of their patients’ massive volumes of medical data. Healthcare professionals and academics have paid close attention to the security and privacy of electronic health records (EHRs). Numerous encoding and decryption techniques and critical management systems have been developed to assure security. Nevertheless, sharing and scalability problems have suggested additional security mechanisms. However, these innovations can lead to other challenges, such as inefficiency. Systems for managing EHR data on the blockchain have been suggested as a way to save processing time. EHRs might be compromised, however, since outsourcing firms set up the majority of blockchain systems. Therefore, we provide an EHR administration system based on blockchain that includes proxy re-encryption in this article. Park et al. (2021) suggested an EHR management system built on blockchain that includes PRE. Data integrity is ensured because of the security of the blockchain, which only allows authorized users to get the stored EHRs. Moreover, PRE protects the privacy of encrypted EHRs. Because our technology isolates the proxy server from the blockchain, the blockchain outsourcing firm cannot see the plaintexts of the EHRs even if the system administrator discloses a user’s private key.
According to Moon et al. (2018), the number of security incidents due to ICT outsourcing is always growing. Moon et al. (2018) looked at potential ICT outsourcing security flaws and how they may be fixed by using the appropriate security measures, from which they were able to derive a list of things to check for during security audits of outsourced IT. Moon et al. (2018) created a model to evaluate companies that outsource ICT security management. A company’s role is to analyze the security level of ICT outsourcing using the model and assessment approach and then evaluate each inspection element’s level of security to decide what sort of security measures should be adopted. According to Moon et al. (2018), their research will help businesses now utilizing or considering using ICT outsourcing assess their security level and reduce the risk of security mishaps or that lack industrial confidentiality and critical information.
Akbar et al. (2018) conclude that although there are many advantages to outsourcing software development to countries with lower labour costs. There are also disadvantages, such as communication, coordination, and control difficulties caused by language and cultural barriers between development sites located in different parts of the world. The absence of in-person communication between members of a dispersed development team directly results from their geographic separation. Not only that, but Akbar et al. (2018) note that trust issues in dispersed teams are a direct result of the absence of regular in-person meetings. There was also a lack of development visibility into the product for the foreign teams.
Outsourcing and long-distance data transmission pose substantial challenges to protecting sensitive information in cloud computing. According to Zhang et al. (2018), protecting users’ privacy during data transfers from the network edge to a non-uniformly distributed cloud server is one of the most pressing issues in this emerging field. Bandwidth and resource constraints have reached a limit for the antiquated, centralized cloud computing system due to the growth of IoT devices and the large volume of data produced at the network’s edge. As a result, edge computing, which makes it possible to store and analyze data at the network’s periphery, has the makings of innovative technology. Technology based on cryptography is proposed by Zhang et al. (2018) to address data privacy and security issues. The most common computing models have long struggled with privacy and data security. However, edge computing’s novel characteristics, such as parallel processing, real-time computing, and information perception, have given rise to a variety of new concerns in this area.
Discussion
Service Provider Selection
Selecting a provider that provides the finest services for an organization’s outsourcing activities and is by data security rules and regulations may help it overcome data sharing problems (Tabrizchi & Kuchaki, 2020). Companies often start ITO projects to improve their competitive position in the market. Organizations decide whether or not to launch an ITO program and, if so, which service provider to choose depending on their requirements for IT services, including data storage, cloud computing, and retrieval infrastructure. Customers and service providers alike may benefit from an ITO collaboration. As a result, it would be advantageous for an outsourcing company to outsource its ITO projects to a service provider that can carry them out more efficiently than they could do so internally. Successful ITO projects for an outsourcing business need the development of ITO plans and the selection of a service provider who can aid their implementation (Wang et al., 2018). Outsourcing often involves handing over an organization’s most valuable IT assets to third parties, which may make it more susceptible to service provider failure or opportunism and reduce its long-term adaptability and competitiveness (Pellicelli, 2018). As a result, a company’s IT outsourcing strategy must emphasize the significant risk associated with these techniques, such as losing all corporate IT expertise and exploiting service providers.
A company should be aware of the data it will give, applicable privacy and security legislation, and other requirements before choosing a service provider. For instance, specific categories of personal information in the United States, such as bank account numbers and social security numbers, may result in data breach reporting (Tabrizchi & Kuchaki, 2020). Knowing the outsourcing provider’s nation of origin is crucial so that data may be remotely stored, processed, and transmitted in accordance with their security regulations. Many nations, including the European Union (EU), have unique regulations concerning transferring personal data outside their borders to other nations (Aaronson & Leblond, 2018). Organizations must be aware of the legal requirements for incorporation by adhering to the proper duties for collecting, using, securing, and transferring business data to collaborate with service providers in other nations.
The organization should do an information security assessment before selecting a vendor or service provider to ensure it satisfies the bare minimum criteria set out by privacy and security law (Hintze, 2018). Personal data, subject to more limitations than business data, may be especially vulnerable, but an information security assessment can help an outsourcing firm identify the greatest risks and vulnerabilities. The outsourced company should develop or revise its information security strategy once the information security assessment is finished to address any compliance issues and data protection threats. Selecting and using third parties with access to regulated data is a crucial aspect of any information security policy, and it should be recorded as such. Checklists, evaluation tools, on-site inspections, and interviews with key security specialists might all be a component of the approach for selecting a third-party provider as part of the information security plan. In order to correctly manage and safeguard firm data with third-party suppliers, an information security strategy must be constantly applied.
Request for Proposal (RFP) and Service Level Agreement (SLA) are two governance agreements that companies must prepare before an outsourcing company can begin selecting service providers from whom it will get its ITO services (Bhatti et al., 2021). Based on the goals of the outsourcing business and the SLA that details what services will be given by the vendors, the RFP is released to the interested service providers. A company that outsources its work to others can use either a single-stage or a multi-stage ITO strategy. When an outsourcing deal is finalized, the client company hands over control of its IT assets like servers and workstations to the outsourcing vendor and manages the vendor in accordance with the terms of the contract and any agreed-upon ITO initiatives. If desired, an outsourcing firm may also create a strategy for handling the aftermath of contract termination.
Cultural and Language Barriers
The greatest challenges businesses have when outsourcing services are linguistic and cultural boundaries, which may lead to coordination issues that can be complicated (Lin, 2020). IT outsourcing success is primarily determined by the contractual connection between the outsourced company and the service provider. This is true whether outsourcing occurs in eastern or western culture. The outsourcing company must trust that its data will remain secure after being handed to the supplier. As a result, reliability and continued dedication to the IT outsourcing initiative’s stated objectives are essential qualities in a reliable outsourcing partnership (Wang et al., 2020).
Numerous studies have shown that a positive client-provider connection is just as important as high-quality service when it comes to the effectiveness of outsourcing. While some outsourcing businesses say that a partnership’s success depends heavily on the two parties’ same values and beliefs, others stress the need to have buy-in from upper management. The success of any outsourcing partnership depends on both parties having a thorough and accurate grasp of the other’s needs, which can only be achieved if the outsourced firm provides detailed instructions for the provider to follow (Wang et al., 2020). By keeping their attention on the agreements outlined in the outsourcing contracts, both parties will be able to reap the benefits of the outsourced project. At the beginning of the outsourcing partnership, the outsourced company must identify the structures, forms, and communication channels between its internal team and supplier. Investment in strengthening outsourcing partnerships is key to the success of the IT outsourcing project (Wang et al., 2018).
Contract Agreements
By effectively leveraging the contract arrangements with the service provider, a company may avoid the problems associated with data sharing during outsourcing. When a company works with a service provider to outsource its data, they do so in order to manage or store it more efficiently than it could internally (Hintze, 2018). This is known as a data outsourcing contract. The construction of reasonable and suitable security measures that safeguard regulated data is guaranteed by a contract agreement, which the supplier must adhere to. Effective management and execution of an outsourced contract may make for a successful outsourcing relationship (Pankowska, 2019). The outsourced project, however, might collapse if the contract is improperly written. Any outsourcing project’s setup is thought to include contract management as a critical component. Most contracts contain the privacy and data protection requirements businesses must meet to operate legally in a given nation. Contracts that respect these standards may help to advance data protection.
A contract agreement enables an internal team to keep an eye on the methods used during the original selection process and to have periodic meetings to assess if any adjustments are required because of new security concerns or regulatory requirements. The success or failure of the outsourcing agreement is most strongly influenced by the outsourcing contract, which establishes the requirements that the service provider must meet (Hintze, 2018). The performance metrics and many service level agreements (SLA) that include financial penalties to encourage the provider to fulfil goals are often highlighted in outsourcing contracts. Outsourcing companies may protect themselves from being stuck in a bad deal by including a clause allowing them to terminate the contract if the service they were promised does not provide (Pankowska, 2019). The success of an IT outsourcing project may be ensured by first establishing a contract agreement, which will reduce the opportunity for opportunistic conduct. Service-level agreements with the outsourcing partners based on mutual trust and commitment may also help a contract arrangement succeed.
Service Provider Optimizations and Performances
A service provider may assist a business overcome data sharing obstacles by providing the most optimized versions of their goods. This allows the business to focus on providing its customers with the best possible service performance. Businesses that choose to outsource often do so to improve the effectiveness of their operations; hence, service providers need to possess the optimal optimizations and give the highest performance levels for their clients. A disadvantage of a company looking to outsource its services is choosing an unqualified service provider to handle the outsourced tasks. Neglecting to carry out a contract agreement may have unforeseen detrimental effects on the success of the outsourcing operation.
Pay-for-performance contracts are outcome-oriented contracting that may be used to decide a contractor’s compensation, the length of their contract, or even the possibility of future work with the organization (Elkomy et al., 2019). When a business hires an outside firm to handle its information technology needs, it often has a number of goals in mind and draws up contracts outlining the criteria to use in evaluating the service provider’s performance, as well as any bonuses or fines that could be levied. Developers at service providers may improve their firm’s capacity to offer business services by defining integration issues that may arise when clients outsource data. Outsourcing firms might benefit from service providers that make the most of their potential for growth via training and new ideas. Providers of services need to stay ahead of the competition by keeping up with emerging outsourcing trends like cloud computing, data management, and application integration.
The outsourcing company and the service provider may receive and share data in a dyadic process (Wang et al., 2018). There must be solutions for problems with data transmission if the outsourced project is to succeed. When a company outsources its data management, the service provider must outline any data transfer concerns before allocating resources. Developers working on behalf of service providers should design and deploy systems that make it easy for their customers to share their data, thereby reducing the opportunity for opportunism. Initiating a lasting outsourcing connection with its partners is facilitated by the optimizations implemented by the service provider. Hintze (2018) argues that having a data processor rather than a data storer as a third-party provider is preferable for most businesses since it gives them more say over the data’s use and protection. If an employee has reason to believe that their employer should not learn specific details about them then it may be in their best interest to use a product provided by a third party acting as the data controller.
Service provider developers must set up systems that allow ongoing monitoring of the surrounding environment and network integration. Managers’ decision-making abilities and the range of available alternatives benefit significantly from the accessibility to real-time data made possible by scanning (Hintze, 2018). Decision-makers may grasp existing and anticipated changes in their external surroundings by using efficient environmental scanning software. A service provider may also look into management activity to discover what is going on in an organization’s environment and what patterns are emerging. Service providers may be informed of any changes in the client environment once the scanning is complete, allowing developers to update their resources and fix any problems that may have arisen. When outsourcing data, the correct precautions should be taken since both businesses depend on the initiative’s success. The long-term success of the outsourcing relationship is ensured when service providers optimize their offerings and give outstanding performances that align with the outsourcing endeavours’ interdependent objectives.
Conclusion
Organizations are outsourcing their data for various reasons, including using the knowledge and experience of the service provider. However, outsourcing data may result in several problems, such as integration difficulties, unwanted access, and stolen data. The successful implementation of the outsourced project and the outsourcing partnership depend on the data exchange. In order to secure data effectively while outsourcing, it is crucial that both the customer and service provider use the optimal security measures. Organizations that make the most of their data capabilities see greater returns on their outsourcing investments due to things like better vendor selection, more efficient relationship management, more fruitful contract drafting, less disruption during transitions, and a more strategic fit between the service provider’s expertise and the company’s goals. Better product and service performance assessments may be made by the service provider and sent to the customer for decisions due to using correct data methodologies. The success of outsourcing depends on the client and the supplier being able to effectively share information since this will lead to better service for the end users.
References
Aaronson, S. A., & Leblond, P. (2018). Another digital divide: The rise of data realms and its implications for the WTO. Journal of International Economic Law, 21(2), 245-272. https://sci-hub.hkvisa.net/10.1093/jiel/jgy019
Akbar, M. A., Shafiq, M., Kamal, T., Riaz, M. T., & Shad, M. K. (2019). An empirical study investigation of task allocation process barriers in the context of offshore software development outsourcing: An organization size based analysis. International Journal of Computing and Digital Systems, 8(04), 343-350. https://journal.uob.edu.bh/bitstream/handle/123456789/3557/paper%203.pdf?sequence=4
Almutairi, M., & Riddle, S. (2018). A framework for managing security risks of outsourced IT projects. Proceedings of the 2018 International Conference on Software Engineering and Information Management – ICSIM2018. https://sci-hub.hkvisa.net/10.1145/3178461.3178476
Bhatti, B. M., Mubarak, S., & Nagalingam, S. (2021). Information security implications of using NLP in IT outsourcing: A diffusion of innovation theory perspective. Automated Software Engineering, 28(2). https://link.springer.com/article/10.1007/s10515-021-00286-x
El Arass, M., & Souissi, N. (2018). Data lifecycle: from big data to SmartData. In 2018 IEEE 5th international congress on information science and technology (CiSt), 80-87 https://www.researchgate.net/profile/Mohammed-El-Arass/publication/330027037_Data_Lifecycle_From_Big_Data_to_SmartData/links/5c4edca3299bf12be3e922cb/Data-Lifecycle-From-Big-Data-to-SmartData.pdf
Elias Malope, M., & Naidoo, R. (2020). Knowledge sharing challenges in subsidiary-to-subsidiary IT infrastructure outsourcing. Conference of the South African Institute of Computer Scientists and Information Technologists 2020. https://sci-hub.hkvisa.net/10.1145/3410886.3410908
Elkomy, S., Cookson, G., & Jones, S. (2019). Cheap and dirty: the effect of contracting out cleaning on efficiency and effectiveness. Public Administration Review, 79(2), 193-202. https://onlinelibrary.wiley.com/doi/pdf/10.1111/puar.13031
Gurung, A., & Prater, E. (2017). A research framework for the impact of cultural differences on IT outsourcing. In Global sourcing of services: strategies, issues and challenges. https://mds.marshall.edu/cgi/viewcontent.cgi?article=1004&context=mis_faculty
Hintze, M. (2018). Data controllers, data processors, and the growing use of connected products in the enterprise: Managing risks, understanding benefits, and complying with the GDPR. SSRN Electronic Journal. https://sci-hub.hkvisa.net/10.2139/ssrn.3192721
Lin, N. (2020). Designing global sourcing strategy for cost savings and innovation: A configurational approach. Management International Review, 60(5), 723-753. https://link.springer.com/article/10.1007/s11575-020-00428-5
Moon, J., Lee, C., Park, S., Kim, Y., & Chang, H. (2018). Mathematical model-based security management framework for future ICT outsourcing project. Discrete Applied Mathematics, 241, 67-77. https://sci-hub.hkvisa.net/10.1016/j.dam.2016.03.013
Pankowska, M. (2019). Information technology outsourcing chain: Literature review and implications for development of distributed coordination. Sustainability, 11(5), 1460. https://sci-hub.hkvisa.net/10.3390/su11051460
Park, Y. H., Kim, Y., Lee, S. O., & Ko, K. (2021). Secure Outsourced Blockchain-Based Medical Data Sharing System Using Proxy Re-Encryption. Applied Sciences, 11(20), 9422. https://www.mdpi.com/2076-3417/11/20/9422/pdf?version=1634090611
Pellicelli, M. (2018). Gaining flexibility and innovation through offshore outsourcing. Sustainability, 10(5), 1672. https://sci-hub.hkvisa.net/10.3390/su10051672
Statistica. (2019, April 30). Global market spend on outsourcing and shared services 2018. Statista. https://www.statista.com/statistics/1071929/global-market-spend-outsourcing-shared-services/
Tabrizchi, H., & Kuchaki Rafsanjani, M. (2020). A survey on security challenges in cloud computing: Issues, threats, and solutions. The Journal of Supercomputing, 76(12), 9493-9532. https://facultyweb.kennesaw.edu/lli13/alg/6823/lm11/Cloud%20security%20survey.pdf
Wang, J. J., Sasanipoor, N., & Wang, M. M. (2018). How PMBOK standard and partnership quality influence IT outsourcing success: An investigation of the mediated moderation effects. Journal of Global Information Technology Management, 21(4), 282-300. https://sci-hub.hkvisa.net/10.1080/1097198X.2018.1536597
Wang, M. W., Tan, C. L., & Wahid, N. A. (2020). Service Quality, Facilities Management Practices and Outsourcing Service Provider Capabilities: A Critical Review and Conceptual Framework for Facilities Management Companies. Global Business & Management Research, 12(2). http://www.gbmrjournal.com/pdf/v12n2/V12N2-5.pdf
Wang, Y., Liu, Y., & Canel, C. (2018). Process coordination, project attributes and project performance in offshore-outsourced service projects. International Journal of Project Management, 36(7), 980-991. https://sci-hub.hkvisa.net/10.1016/j.ijproman.2018.02.005
Zhang, J., Chen, B., Zhao, Y., Cheng, X., & Hu, F. (2018). Data security and privacy-preserving in edge computing paradigm: Survey and open issues. IEEE access, 6, 18209-18237. https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=8327600
 write
write