Introduction
In today’s interconnected business world, mergers and collaborations are crucial to growth and new prospects (Tzafestas, 2018). When two firms integrate their networks, security, efficiency, and compliance must be addressed. This study analyzes the integration of Company B’s network with Company A’s and proposes a secure network design that integrates the two.
The network settings of both companies will be examined to discover vulnerabilities and weaknesses. Understanding the strengths and weaknesses of each network allows the creation of a new network design that optimizes security, efficiency, cooperation, and operations. This new network design will also migrate some assets to the cloud, taking advantage of its scalability, flexibility, and security.
This paper will also examine the new network diagram components and their significance to the OSI and TCP/IP stack layers to ensure a balanced approach. Cost-effectiveness and project goals will inform each network design decision. Moreover, the paper will seek to link network enhancements to secure network architecture. Linking these principles with regulatory compliance requirements shows how the suggested changes improve security and help the combined firm achieve its legal obligations. As legal frameworks change, proactive actions are needed to comply and protect sensitive data.
This paper will conclude with network security threats, where an examination of how the offered solutions can mitigate risks and strengthen the network will be done. This extensive analysis concludes with a summary of the primary recommendations stressing risk-based decision-making for secure network integration.
Existing Security and network problems
A comprehensive security audit was conducted, and various company vulnerabilities were identified. This section describes the security and network setup, which is crucial in developing a new network architecture for combined businesses. The analysis took into account not only the available resources but also data flows, network services, and user requirements.
The analysis revealed that neither company A nor Company B practiced zero trust security. The zero-trust methodology presupposes the possibility of compromise for any identity that can access resources, whether machine or human (Zhou et al., 2018). The adoption of a zero trust mechanism that puts priority on identity security is very crucial so as to maintain data safety. Teams should put emphasis on identity security as the backbone of the zero-trust approach where they can easily detect, isolate, and prevent compromising identities.
Company A does not have a centralized authentication capability, and that acts as a potential security risk. There are several centralized user databases that can be used by the company to authenticate users across multiple services and platforms (Zhou et al., 2018). Some of these databases include active directory, network information services, and lightweight directory access protocol. The active directory is a database and a set of services that ensure communication between the users and network resources that they want to use (Whitman & Mattord, 2021). This database stores important details about the setup, like who can access certain resources and who is logged in.
After accessing the network infrastructure of company A, several problems were discovered. One of these problems was an insufficient amount of network segmentation. A large network should be segmented into smaller segments to ensure that security measures can be tailored to each segment and the network is easily managed (Whitman & Mattord, 2021). To ensure the highest level of security, during the merge, the network architecture should be modified. The infrastructure of company A does not support any cloud services, which refers to a range of online services which can be accessed instantly from any part of the globe. However, the company is investigating the viability of extending its network to a third-party cloud solution.
Company B has multiple security issues. The company lacks security measures, and that is a major problem which puts the company resources and employees at risk. The company brand and bottom line can be secured from harm through security solutions which actively seek out and neutralize threats (Whitman & Mattord, 2021). Company B lacks a documented security policy that outlines the company strategies for safeguarding digital and physical assets. It is essential for companies to review and revise security policies regularly to ensure that they stay updated on the latest threats, vulnerabilities, and security standards (Zhou et al., 2018). The cybersecurity of company B is in danger because it lacks security policies which are comprehensive. The network infrastructure of the company has a serious problem; this is because the edge router is an ISP router which cannot be controlled or managed by the company (Zhou et al., 2018). In addition to that, the network does not have sufficient segments, which are crucial in establishing a strong security posture and enforcing effective security procedures to protect valuable resources.
Existing vulnerabilities for each company
Several security issues were discovered after a thorough analysis of the network diagrams and vulnerability scans of the two companies. This section discusses the threats, dangers, and consequences of each company network.
The security of Personally Identifiable Information of customers and employees of company A is at risk. This is because sensitive information such as account numbers, phone numbers, and social security numbers might have leaked due to the lack of encryption according to industry standards (Zhou et al., 2018). As a result, various forms of fraud and identity theft may occur. The company should lay down strategies which can help in responding to attacks to reduce these risks. After discovering a compromised machine, the company should remove it from the network immediately, carry out an investigation, and then patch any holes found (Whitman & Mattord, 2021). Proper channels of communication in case of a breach of personally identifiable information should be created and tested in advance. The workers should also be educated on the importance of protecting personal information (Whitman & Mattord, 2021). Intellectual property is another important asset that a company must protect. Knowing the ins and outs of patents, trademarks, copyrights, and trade secret protection is crucial. Personal information is vulnerable to both online and offline attacks. Organizations and their customers are vulnerable to identity theft if adequate protections and regulations are not put in place.
For company B, one of the security flaws is that its software is out of date. The analysis revealed that a number of systems have serious flaws, and that puts the users at risk. To address these security concerns, patches which are software and operating system updates that fix vulnerabilities in a program or product are needed (Zhou et al., 2018). Through that, the loopholes that could be exploited by malicious attackers are closed. When updates are available, vendors make them visible on their websites, and it is therefore essential to ensure that one promptly applies available updates so as to prevent cybercriminals from exploiting these security flaws in their digital devices (Zhou et al., 2018). Attackers might target these vulnerabilities for months or even years after the updates are available. While new vulnerabilities are discovered on a regular basis, keeping software up to date is the best defense against attackers using previously fixed flaws (Zhou et al., 2018). This is the best way to safeguard your computer, phone, and other electronic gadgets.
We have also discovered that company B does not have a comprehensive cyber security policy. A security policy is a document that details the steps that a company takes to safeguard its information technology assets and other valuables (Zhou et al., 2018). Business security needs, technology developments, and growing risks all necessitate periodic reviews and updates to the security policy to keep it relevant and effective (Whitman & Mattord, 2021). Company B should therefore provide its employees with proper education and training to ensure compliance as they transfer their assets and resources to Company A.
Company B’s network also lacks adequate hardware and networking level security measures. The company uses the ISP router as the edge router, which does not provide the company with the protection it needs. This creates a complex security management problem because it allows remote users to access the network in a variety of ways (Whitman & Mattord, 2021). Furthermore, Company B uses a wide variety of server and desktop/laptop operating systems, which complicates the task of patching and monitoring for cybersecurity vulnerabilities (Whitman & Mattord, 2021). The risk grows in proportion to the number of different software and hardware configurations in use. The corporation can lower its risk of lawsuits, strengthen its systems’ defenses, and reduce its vulnerability to attacks by instituting centralized management, patching, and monitoring processes.
Network topology diagram, merged network
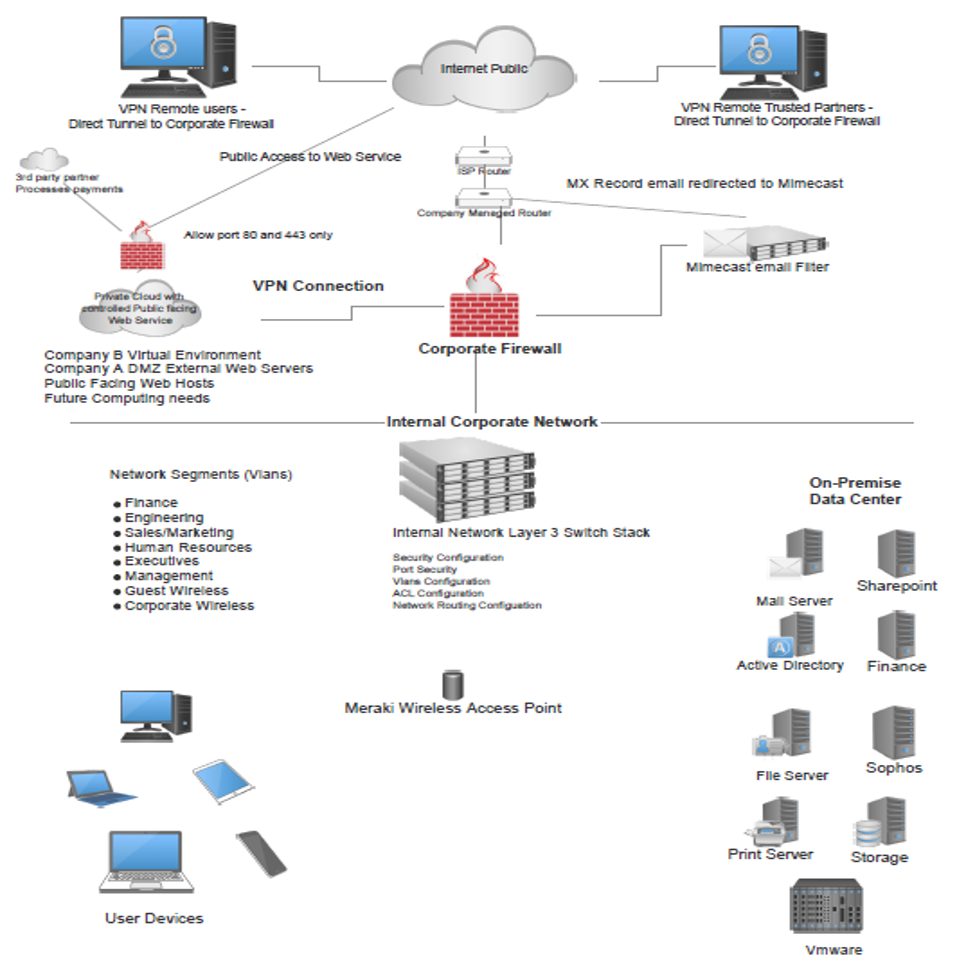
Diagram 1: Network topology diagram,merged network Source: own source
Network layer – OSI model and TCP/IP protocol stack
There are several differences between the OSI and TCP/IP models. One of the major differences is that the OSI model divides various functions into separate layers, while the TCP/IP combines some of these functions into one layer (Stack Overflow, 2016). This is clearly evident in the network access and application layers of the TCP/IP model, which includes several layers that are distinct in the OSI model.
It can be more challenging to diagnose problems and enhance performance in the event where TCP/IP model is used compared to when an OSI model is used; this is because the OSI model gives the opportunity of checking a particular layer like the application, session, and presentation layers to identify the root of data-related issues (Stack Overflow, 2016). Both models are logical and are built with layers making their architectures similar.
| Layer | TCP/ IP Model | Layer | OSI Model |
| 4 | 7 | Application | |
| Application | 6 | Presentation | |
| 5 | Session | ||
| 3 | Transport | 4 | Transport |
| 2 | Internet | 3 | Network |
| Network Access | 2 | Data Link | |
| 1 | 1 | Physical | |
Table 1: OSI model and TCP/IP protocol stack
At layer three of the OSI model, a router is used to inspect the IP and IPX of incoming data packets (Stack Overflow, 2016). At layer 2 of the OSI model, a switch, which is a networking device, redirects packets based on their MAC addresses to their destination ports. A layer 2 switch performs only switching, whereas a layer 3 switch is a specialized hardware that routes packets using IP addresses (Stack Overflow, 2016). In layer 7, there is a new generation firewall that has the ability to inspect layer 7 HTTP traffic and identify the applications which are in use (Stack Overflow, 2016). This layer is also referred to as the application layer, and it is commonly targeted by attacks that circumvent the security measures laid down at layers three and four.
A wireless link in an AP simply means a wireless device. The AP is found on the second layer of OSI, which is the data link layer. The AP acts as a bridge connecting a standard wireless network to a wireless device or as a router transmitting data to another access point (Stack Overflow, 2016). The HTTP protocol for web servers operates at the application by allowing communication between web servers and clients. At the transport layer, there is encryption of VPN tunnels. The VPNs establish a secure and private network connection over public networks like the Internet (Stack Overflow, 2016). VPN ensure that the data transmitted is remains confidential and protected from unauthorized access (Stack Overflow, 2016). The File Transfer Protocol is located in the application layer of the TCP/IP Internet protocol suite, which is the same layer as other protocols like Hypertext Transfer Protocol (HTTP) and Post Office Protocol (POP).
More on OSI model
| Application | Human-Computer interaction |
| Presentation | Ensures data is in a usable format, encryption |
| Session | Maintains connection, controlling ports and sessions |
| Transport | Transmit data using transmission control protocol and user datagram protocol |
| Network | Decide physical path, routing |
| Datalink | Defines the format of data on network |
| Physical | Transmits raw bit stream over the physical medium |
Table 2: OSI model
Merged network: adding, deleting, or repurposing network components
Strategic decisions must be made to ensure that the merge between the two companies works securely and efficiently. All the resources will be moved to networks of company A, which will benefit from a cloud partnership for highly secure hosting. Both companies will use the cloud, making it easier for users and networks to work together. The Active Directory system of Company A will lay the groundwork for Zero Trust principles and provide a central location for all users and resources. Group rules will be set up to handle password rules and send patches to hosts (Radosavovic et al., 2020). The new cloud partnership will have direct secure network connections, with an ACL implemented to ensure only required ports and protocols are open between the networks. A VPN tunnel will be implemented between the cloud and the on-premise network. Once a person logs into the network and proves who they are, they will be able to use systems and storage in the cloud (Radosavovic et al., 2020). The ability of the cloud environment to scale will make the procurement of a new system quick and secure.
As the merging process continues, it is essential to note that the systems and data of company B will be moved to the new cloud service but not the on-premise network. The DMZ program of company A will also be migrated to the cloud, and that will offer cost and budgetary benefits. Most of the new hardware and web services will be moved to the new cloud, and that will help in cutting capital expenditures. The recurring expense of operating in the cloud is easily projected. However, the capital expenditure of purchasing on-premise hardware typically depreciates for three years and operates at a low power and cooling operation after that point. In the end, this move to the cloud will give both companies involved in the merger a safe and effective solution.
If need be, the systems will be changed. Mimecast services will be relocated to a network of company A and all incoming emails will be filtered through it. Through that, spam and unwanted emails from unsolicited sources will be addressed (Radosavovic et al., 2020). The network performance management will also be improved if this service is placed outside the internal network. The Cisco umbrella DNS security network will be implemented to make sure that all policies are followed, and sensitive data is kept safe (Tzafestas, 2018). The code42 data-centric security tool will also be implemented to automate and speed up processes for responding to data risk incidents.
Similarly, the Sophos endpoint detection response application will be installed on all hosts to keep an eye on security threats and have a place to store information about threat levels (Tzafestas 2018). Multi-factor authentication and zero trust for the workforce will be used to control access. This will make sure that only allowed users and secure devices can access the application (Whitman & Mattord, 2021). One trust data privacy or data lifecycle management solution will be used to help in data governance and privacy to ensure that data is proactively managed as it enters the company.
The two companies use multiple operating systems allowing the user to choose the one that best suits them, but that also becomes a burden to the IT team because it must keep all systems up to date because failing to do so puts the company at risk. The risk can be mitigated by upgrading the operating system at the server end and at the user device and managing them with an in-house security application that can provide real-time monitoring and audit reporting (Radosavovic et al., 2020). Unused hardware from both companies will be disposed of safely with proper documentation of the procedure.
Secure network design principles
The new network redesign is set up based on two key ideas, which are network segmentation and access control. Network segmentation involves the division of the network into smaller sub-networks to allow each segment to have its own security rules and services (Whitman & Mattord, 2021). This is achieved through the use of virtual local area networks (VLANs), with multiple VLANs being created for users. Access control lists are then set up to limit where on the network these people can go (Whitman & Mattord, 2021). The VLANs can be monitored to detect any sign of malicious activity.
Active Directory is one of the most important principles of a secure design. This directory service is offered by Microsoft. The active directory runs on a Windows server and allows the administrators to control who can access the network resources and the rights they have (Whitman & Mattord, 2021). The directory is normally a database and a set of services connecting the users to the tools that they need to do their work (Whitman & Mattord, 2021). The directory contains important information about the users and computers as well as who is allowed to use certain tools. Through group policy (GPO) which is a hierarchical system, network managers can set up specific settings for users and computers (Whitman & Mattord, 2021). GPO is a good security tool that can be used to enforce strict password policies and manage user accounts according to company policy.
Regulatory compliance requirements
Several rules have been put in place to safeguard consumers and investors from unfair practices. Company A is a financial institution, while company B is a smaller enterprise in the same industry that deals with customer payments. When the two entities are combined, they will be subject to the same regulations (Ben, 2022). Companies must perform annual audits of their financial statements so as to comply with the Sarbanes-Oxley Act of 2002 (SOX) (Nick, 2023). This audit determines how accurate the procedures used in preparing these financial statements are (Nick, 2023). Our networks, systems, and security procedures must all be up to SOX standards for us to be in compliance. The network will be designed bearing in mind the regulatory compliances which exist. The payment card industry data security standards (PCI DSS) have come up with policies and procedures to secure cardholder data and guarantee the security of credit, prepaid, and debit card transactions (Ben, 2022). To ensure compliance with this standard, the company will implement security controls in its design.
Importance of regulatory requirements to the merged company
Intellectual property (IP) assets can greatly impact purchases. It is essential to find out whether the constituents have any patents, copyrights, or trademarks (Wolters Kluwer, n.d.). Tricky situations like not being allowed to use a voluntary assumed name in every state can be avoided through the identification of all moving pieces in advance (Wolters Kluwer, n.d.). Knowing when and how to transfer and assign these assets can help guarantee that the deal proceeds smoothly and on time.
How the proposed merged network topology diagram meets the regulatory requirement
The new merged network topology depicts strategic network connections with secure encryption tunnels utilizing third-party payment services partnership. This relationship helps us comply with credit card regulatory requirements (Nick, 2023). It will shift more responsibility and liability over to our partner. We can leverage our partner’s expertise in protecting customer data and adhering to restrict PCI DSS standards. There is expense to these services, but it is offset by the fact that they will take on more of the liability in case of a breach. A third-party payment is when a third-party service provider processes payments for two parties. Examples of third-party payment services include PayPal, Stripe, Apple Pay, Google Pay, and Venmo. Similarly, by bringing company B’s understanding of security policies and migrating resources and users to a newly designed network of company A, the network regulatory requirements can be met.
Emerging threats appliable to the merged organizations
Potential network security risks of implementing the topology
Deploying a network architecture may raise security issues which are exacerbated during the migration phase (Zhou et al., 2018). The IT team may therefore encounter difficulties and may require additional resources to maintain functionality, accessibility, and security. The migrated and newly deployed network infrastructure must be tested thoroughly to ensure that they are up to date with the latest patch level (Zhou et al., 2018). An exhaustive testing procedure should be developed to ensure that all the systems are functioning at the desired security level prior to the go-live phase.
Potential performance impacts on the merged network after implementation of the proposed design
To increase network security, certain ports, protocols, and services are only allowed, while others which are unauthorized are restricted (Radosavovic et al., 2020). This measure helps in reducing potential security threats. We have defined the standard ports, protocols, and services required to provide our customers with an operational and secure infrastructure. We will have the capability of proactively monitoring and responding to any malicious network traffic. These ports and protocols, together with IP addresses, will be utilized to build an Access Control List (ACL) on the corporate switch stack (Radosavovic et al., 2020). Through the restriction of unauthorized ports and protocols, malicious activities will be eliminated, and network traffic will be reduced; this will not only improve security but also network performance (Radosavovic et al., 2020). Users will only be allowed to access the systems that they need to perform their tasks.
How to manage the identified potential security risks
A detailed testing plan will be created, and every system that is to be added to the network will have to go through the testing phase (Whitman & Mattord, 2021). To comply with security standards, we will adhere to the security standards, perform testing to ensure the systems operate at their most current patch level, and ensure that privileged user accounts are tightly enforced and monitored. Zero trust principles will also be implemented to secure resources.
Recommendations summary
The merging of the two companies will involve the decommissioning of the company network, and users and data will be moved to company A. Where applicable, hardware and services will be repurposed to company A infrastructure. Before the transfer, company A network will be built up so as to provide a safe and functional working environment. A cloud partnership will also be sought to accommodate web services and storage (Whitman & Mattord, 2021). Furthermore, a third-party processing payment service will be used to handle credit card payment liabilities because both companies currently process credit cards in-house and store personally identifiable information on-premise and that poses a possible security threat. Because of the cooperation with a third-party provider, the business will transfer the risk to a specialist group while at the same time capitalizing on the knowledge and experience of the provider to achieve PCI compliance. The cost-benefit of this activity reveals how essential it is as the company takes on less risk and offloads payment services to a partner.
Investing in cloud partnership costs will help the business scale and ensure redundancy in the infrastructure. Through redundancy, the company will be able to operate at a high level of efficiency, ensuring data and services are constantly accessible (Whitman & Mattord, 2021). Cloud services offer greater flexibility, security, and reliability compared to on-premise networks; this is majorly because cloud services are hosted remotely (Zhou et al., 2018). Cloud computing eliminates the need of maintaining and updating systems hence freeing up time, money, and resources so that concentration can be put on the core strategies of the business. Through high-speed and secure connection, data and services can be transferred easily and without interruptions between the cloud solution and the on-premise networks (Zhou et al., 2018). The cybersecurity team will collaborate closely with the IT team in making decisions on budget and in allocating resources between the cloud solutions and on-premise software as per the requirement. After the appropriate network has been set up, it will provide infrastructure which is secure, adaptable, and scalable (Zhou et al., 2018). This infrastructure will allow the company to provide the best quality services to the clients. The network will be streamlined so as to ensure that it operates under minimal maintenance and optimized costs.
References
Ben Cole, (2022). Regulatory compliance: TechTarget. In which layer is HTTP in the OSI model?http2 – In which layer is HTTP in the OSI model? – Stack Overflow
Nick, Sorenson (2023). SOX Audit: 8 Steps to a Successful Audit. https://pathlock.com/learn/sox-audit-8-steps-to-a-successful-audit/
Radosavovic, I., Kosaraju, R. P., Girshick, R., He, K., & Dollár, P. (2020). Designing network design spaces. In Proceedings of the IEEE/CVF conference on computer vision and pattern recognition (pp. 10428-10436).
Stack Overflow, (2016). In which layer is HTTP in the OSI model?
Tzafestas, S. G. (2018). Ethics and law in the Internet of things world. Smart cities, 1(1), 98-120.
Whitman, M. E., & Mattord, H. J. (2021). Principles of information security. Cengage learning.
Wolters Kluwer (nd). ma-transactions-8-essential-compliance-requirements. https://www.wolterskluwer.com/en/expert-insights/ma-transactions-8-essential-compliance-requirements)
Zhou, W., Jia, Y., Peng, A., Zhang, Y., & Liu, P. (2018). The effect of iot new features on security and privacy: New threats, existing solutions, and challenges yet to be solved. IEEE Internet of things Journal, 6(2), 1606-1616.
 write
write