Abstract
The operating system, commonly called the OS, is responsible for managing computer hardware resources. According to Lee et al. (2017), understanding context awareness is crucial for optimizing tasks, task scheduling, and memory management in computer operating systems. In recent years, the emergence of mobile devices such as smartphones and tablets has opened up new opportunities for context-aware computing. These devices are equipped with diverse sensors, making them ideal for leveraging context-aare capabilities. Therefore, the full potential of context-aware computing must be harnessed and implemented in these devices. This paper provides an analysis of context awareness and explains the rationale for optimizing operating system behavior and memory management through the use of context-aware scheduling.
Consequently, the study suggests introducing a context operating system (OS) as evidence of the successful deployment of a context-aware OS on mobile devices (Lee et al., 2017). This implementation involves the integration of context-aware scheduling at the kernel level of the Android operating system, a novel approach that has yet to be previously explored. The findings demonstrate a notable enhancement in the execution of CPU-intensive tasks performed in the background, the optimization of phone memory scheduling, and the reduction in power usage.
Introduction
The skilful application of situational information in message delivery is one of the elements that make human communication so effective. The relevance and comprehension of the intended information are increased when situational information or context is included. This makes the message more vivid and facilitates effective and efficient communication. In human-computer interaction, contextual information has yet to reach its full potential (Elmalaki et al., 2018). Context-aware computing currently needs to catch up to other things like artificial intelligence in robotics, despite attempts by many products to integrate context-aware systems, such as light sensing in mobile phones and tilt sensing for screen rotation. Context-aware computing is attractive because it can change how computer services behave according to situational data (Bai et al., 2019). This suggests that it can improve user interactions with computers while making our lives easier, as computers can predict or adjust to appropriate actions depending on the circumstances.
Numerous scientific ideas, such as ubiquitous and pervasive computing, are the foundation of context-aware computing. The idea of ubiquitous computing emphasizes how computers may be accessed anywhere, at any time, by integrating them into different facets of daily life. Conversely, pervasive computing seeks to reduce the requirement for direct human interaction with traditional computers by integrating computational capabilities into everyday objects (Zhao et al., 2018). The rapid improvements in sensor technologies and automated environmental perception are generating much interest in context-aware computing. The capacity of context to deduce information the user does not expressly offer is fascinating. The use of context-aware computing in the Android operating system is the main focus of this study. In addition to improving memory management, it seeks to increase these devices’ efficacy and efficiency (Zhang et al., 2018).
Computing devices need systems that can answer the fundamental questions of who, where, when, and why and innovative sensors to make it easier for users to learn about their surroundings (Zhao et al., 2018). The primary context is defined in large part by the user environment. Smartphones come with various sensors, such as light, proximity, accelerometer, and GPS, and are known for their sturdy hardware platforms. As a result, new software is required to control these hardware elements, with particular attention to the operating system and how it interacts with the hardware. The OS, often known as the operating system, enables communication between software and hardware. The program shares the hardware resources.
The operating system plays a vital role in retrieving data from these sensors in most applications. The operating system communicates with sensor drivers and then sends the information gathered to the application to obtain context-aware information. It is noteworthy that modern operating systems still need to use this sensor data to guide their choices (Elazhary et al., 2017). This research aims to use memory management and situational information (context) to optimize operating system behavior. In particular, improving process scheduling provides evidence of contextual considerations being optimized and integrated at the operating system (OS) level. This endeavor, which incorporates a low-level optimization in the operating system-level process scheduler, is the first type. This project focuses on Android, an open-source operating system widely available for free on numerous handsets. Furthermore, it should be mentioned that the Linux kernel, the foundation of the Android operating system, is a very robust operating system that can be customized to run on various platforms, such as desktop computers and other embedded devices (Zhang et al., 2018).
Literature Review
This section provides an overview of the fundamental principles of context-aware computing and its current advancements in mobile computers. Additionally, it also explores the concept of context-awareness in mobile operating systems.
Context and context-aware computing
The existing literature has a wide range of interpretations of the concept of context. Notable instances include context switching while multitasking, the provision of context-aware support, and contextual search. However, the explanation offered by Dey and colleagues is widely accepted in the academic world. An “entity” is anything that is of interest. Situational characterization is a word used to describe or evaluate facts regarding the status or condition of an item. An entity is a person, location, or object deemed eligible for permitting communication between a user and an application. This covers both the user and the applications that comprise the interface.
According to Dey (2018), many researchers have proposed distinct conceptualizations of context-aware computing. Nonetheless, Dey and colleagues provide a widely recognized description within the scholarly community. According to the author, contextual information is used by a system to present the user with relevant information or services; the system assesses how relevant the information is depending on the user’s current activities (Dey, 2018). The following paragraph will do a thorough study of prior research on this specific topic. The user’s immediate surroundings typically define the context. Mobile computers are an essential source of contextual information since they are portable and accompany users for extended periods (Cabrera et al., 2019).
Examples of Early Works
Developing an adaptive user interface for personal digital assistants (PDAs) has been a topic of interest in human-computer interaction. This initiative has made significant progress toward achieving context-awareness in mobile computing. Several researchers used two prototypes to present their ideas. According to Sezer et al. (2017), the prototype used a light-sensitive display. Furthermore, the device included a light sensor linked to a palm pilot to familiarize it with the ambient lighting conditions and adjust the backlit display. The second prototype recognized the orientation of the PDA by using two mercury switches (Sezer et al., 2017). In addition, MIThril is acknowledged as a mobile phone endeavor with context-awareness capabilities. This effort was launched in the year 2001. According to Al-Fedaghi (2017), the current project includes numerous sensors, such as a GPS receiver, a three-axis accelerometer, infrared tagging, and microphones.
The researchers used specialized sensors to determine the participants’ position and activity patterns. According to Gu et al. (2020), early research needed to be improved by hardware constraints that limited context awareness applications in mobile devices. Nonetheless, advances in mobile computing, notably the integration of smartphones with context-awareness capabilities, have demonstrated significant promise. The researchers resumed their study of context awareness on mobile devices (Gu et al., 2020). Smartphones provide a concrete physical infrastructure, allowing researchers to concentrate on the software applications that run on these devices.
Context-Aware Mobile Operating Systems
Linsky (2017) has highlighted mobile device operating systems (OS) as a suitable platform for integrating context awareness, emphasizing enhancing energy efficiency within the OS. Two notable instances are CondOS and ErdOS. According to Zhang et al. (2016), context-aware operating systems (OS) can be expanded to encompass additional OS functionalities through CondOS. Examples of essential operating system functions include memory management, input/output control, and scheduling. The following is an evaluation of the two operating systems under consideration.
CondOS
The CondOS operating system draws inspiration from the fundamental principle that context awareness is contingent upon leveraging the existing smartphone platform. In summary, the smartphone possesses all the necessary components to fulfil the requirements for context awareness. Smartphones possess a wide array of sensor hardware components. In addition, they possess the capability to perform the necessary algorithms during the processing of unprocessed sensor data. Multiple writers propose the necessity of centralizing context creation by employing an agent that functions as a central context source for all context queries. According to Trainor (2019), the centralization of context generation leads to decreased power usage compared to individual apps’ autonomous generation of context. The research proposes that the operating system (OS) is the optimal platform for integrating context-aware resource management (Trainor, 2019). The introduction of contextual data units (CDUs) is a novel approach aimed at processing raw data obtained from sensors and seamlessly integrating it into the operating system. Additionally, the study conducted by Khozouie et al. (2017) suggests that a Contextual Data Unit (CDU) offers a significant degree of data abstraction to various applications, such as pedestrian movement and vehicular transportation, by effectively processing the information gathered from sensors.
The authors have enumerated the potential benefits of context-aware operating systems. The items mentioned above encompass:
Memory management involves executing user actions, such as jogging and walking, which might be used to propose a music application’s preloading. Conversely, activities such as operating a vehicle may involve the utilization of a navigational map. In addition, the operating system can monitor the usage patterns of the applications the user utilizes and preload these applications accordingly, resulting in an enhanced end-user experience.
Scheduling: CondOS proposes that the prioritization of processes should be directly influenced by the context in which they operate. The optimal illustration is contingent upon the user’s specific location or situation and their preference. Priority should be given to executing applications that are most likely to be run. The process of scheduling, which involves considering contextual input, facilitates the allocation of an optimal quantity of resources to the most appropriate process.
Input/Output: Contextual data can be adapted to notification mechanisms, auditory alerts, or keyboard font size adjustments as input. The volume of a ringing sound can be modified to be excessively high in a conference or insufficiently low in a party setting. The determination of the suitable ring volume is contingent upon the prevailing background noise level. Furthermore, the font size of the touchscreen keyboard can be adjusted based on the user’s activity, such as walking or sitting.
Security: The security measures implemented are contingent upon the specific site. For example, security measures are less stringent within residential settings. Security measures in public spaces are often stringent to mitigate potential security threats.
Energy management involves integrating up-to-date contextual information on operating systems, which can provide insights into potential future energy opportunities and requirements. In light of this, the operating system possesses the capability to effectively oversee and regulate both applications and resources in order to achieve predetermined energy efficiency objectives. Based on current understanding, it can be stated that CondOS needs to possess a comprehensive implementation. However, the incomplete implementation of FALCON can be utilized for memory management. Pensabe-Rodriguez et al. (2020) propose that FALCON provides an architectural framework for detecting context and executing predictive application launching. Once the context has been processed, FALCON loads the applications into memory and executes the prelaunch routines for each application.
ErdOS
ErdOS is an operating system that emphasizes energy conservation in its design and operation. The procedure above is favourable in the context of mobile systems because of the inherent limitations imposed by battery constraints and the occurrence of energy peaks coming from periods of strong interactions. According to Trainor’s (2019) research, a better method for managing and allocating resources is to consider the context, which entails forecasting resource demands and assigning resources to applications depending on user demands. This strategy is preferred over resource allocation based entirely on algorithms. ErdOS also monitors the status of resources, app resource requirements, and user engagement patterns with those applications. ErdOS also builds a model based on location to assess resource use trends, allowing for predicting future resource demands and calculating and forecasting energy requirements (Khozouie et al., 2017).
The application level illustrates the attainment of context awareness from a scientific standpoint. Contextual information is communicated from the operating system to the applications in order for them to have contextual awareness. Based on previous research, scholars have identified the operating system (OS) as the best site for adding contextual knowledge. Smartphones are regarded as an ideal platform because they provide a solid hardware base supporting context awareness development (Zhang et al., 2018). Our study provides proof of concept by incorporating contextual information at the operating system (OS) level. According to Linsky (2017), an OS has several elements of an operating system. Scheduling, memory management, energy management, security, and other concerns are cited. FALCON and ErdOS have tackled a variety of memory management and energy management issues (Linsky, 2017). The primary goal of this research project is to explore the operating system’s scheduling component.
Methodology
Numerous researchers have identified mobile device operating systems as appropriate for integrating context awareness. CondOS and ErdOS are examples of operating systems that have achieved context awareness. CondOS extends the concept of a context-aware operating system to include additional operating system functionalities such as scheduling, memory management, and input and output controls (Knappmeyer et al., 2018). While CondOS has yet to be fully deployed, progress has been made by developing FALCON, a memory management system. According to Chakraborty et al. (2018), FALCON is a framework for detecting context and constructing a predictive application launching system. The Launch predictor, which evaluates contextual information to anticipate application launches, is a significant component of FALCON.
The ErdOS prioritizes energy management challenges within the context awareness area. Given the limited energy resources of mobile phones, there is a rising desire for resource management and allocation based on contextual considerations, such as projecting resource and user demands, rather than purely on algorithms (Rjeili et al., 2019). As a result, the ErdOS prioritizes resource status monitoring, assessing application resource requirements, and analyzing user involvement patterns with apps. The ErdOS creates a localized resource usage model in order to forecast resource demand and, as a result, energy consumption.
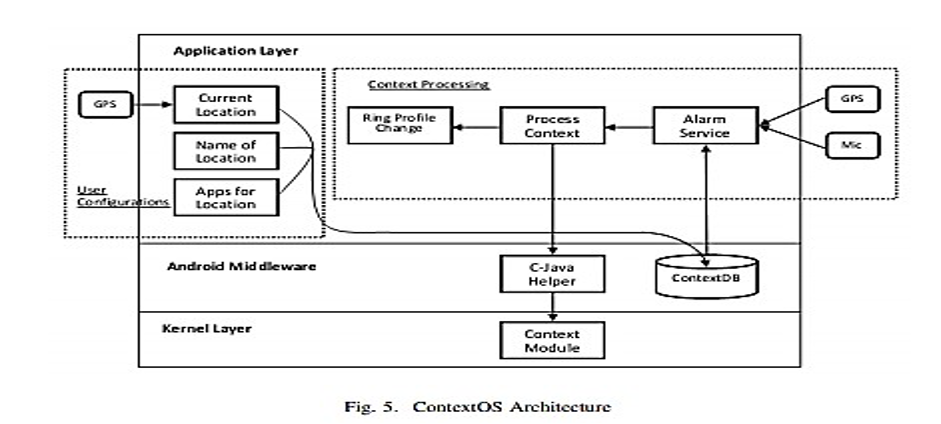
This context-aware operating system (OS) is inspired mainly by ErdOs and CondOS, and it is divided into three levels inside the Android OS framework: the Kernel, Android Middleware, and the Application (Elmalaki et al., 2018). The paper presents an overview of a context-aware system’s key features and operational capabilities within the Android kernel layer. This study’s primary focus is on evaluating process flows, architecture, and essential algorithms within the context of an operating system. Two distinct process flows might be used to construct a context-aware Android operating system. Elmalaki et al. (2018) did a study that examined two separate process flows. The first process flow concerns user configuration, whereas the second concerns the response to context change. The user configuration module is in charge of configuring the system. In most cases, clients go to several sites, necessitating different arrangements. As shown below, the user configuration uses geographical location as a determining element in prescribing the ContextER application.
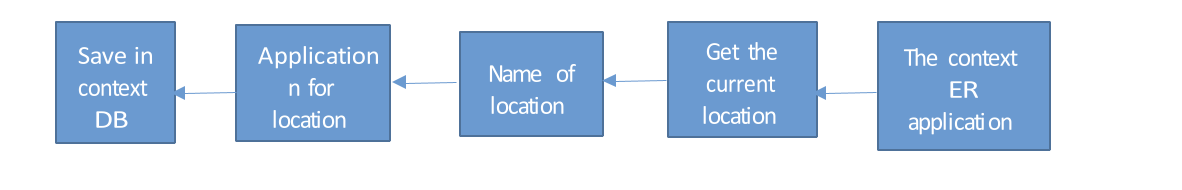
Figure 1: Context change process flow
The OS can respond to a changing context by using the user configuration, which is made possible by reacting to the changing context process. As seen in the following figure:
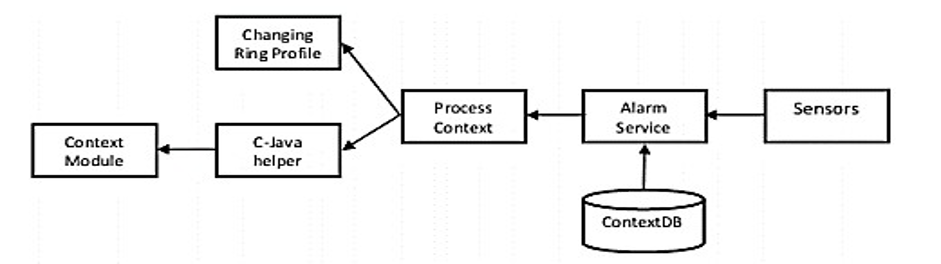
Figure 2: The reaction to the changing context process
The context OS is an altered version of the Android OS based on the above figure. This incorporates new parts at the kernel level into the Android stack. Specifically, the ContextER will serve as the primary entry app in this context OS, allowing users to associate a collection of applications with their location. This app comprises three components: the user-defined location, the location coordinates, and a collection of applications linked to the location, all of which save data in the context database (Wang & Ahmad, 2020). An occasional background-running service accesses this data. This service uses sensors to gather information about the users’ surroundings. Then, it compares it with the most recent data from the context database to determine what needs to be done.
While Java is used to write Android applications, the kernel layer is implemented using the C programming language. In order to establish communication with the kernel module, the research team utilizes the Java Native Interface (JNI) as a helper component. This interface allows the ContextER application to access and communicate with the kernel module. The operating system will have a context module that facilitates the prioritization of application switching. The IOCTL, an abbreviation for input-output control, serves as the primary auxiliary component facilitating communication between the kernel modules, as stated by Lee et al. (2017). The underlying logic of this project involves configuring the system and initiating its services. Once operational, the system will independently detect the user’s environment, analyze the context, and execute the appropriate actions. To enhance comprehension of the method employed in this project. The content of the study is organized into two main sections: the context module and the context processing method, as discussed by Chakraborty et al. (2018). The algorithm for context processing is responsible for identifying the applications that require modifications to their process identifiers (PIDs) and priorities. The process identifiers (PIDs) are transmitted to the C-java helper component, which transfers data to the kernel module. Table 1 below presents the algorithm for context processing.
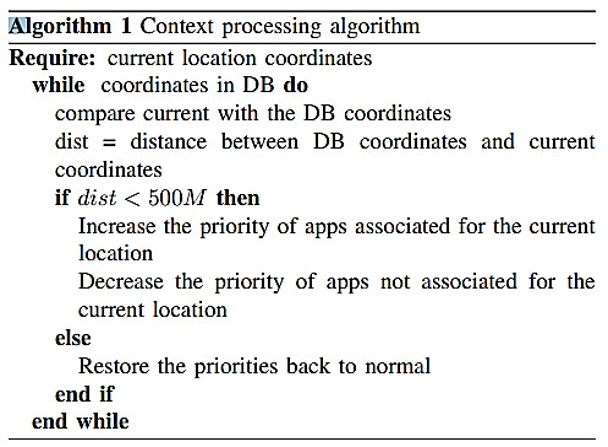
Table 1: Context processing algorithm
The context module is where the priority-changing algorithm takes place. Moreover, it is as table 2 below illustrates.
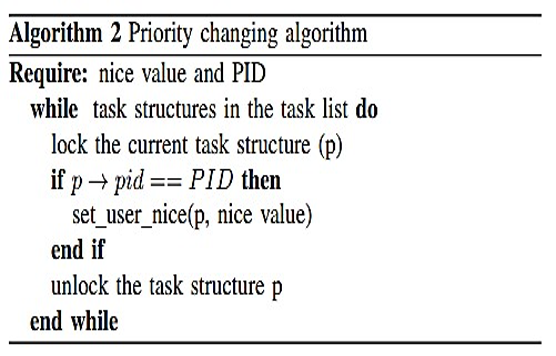
Table 2: Priority changing algorithm
Experiments
This section outlines the experimental stage of the system. The system underwent initial testing in an emulator before being further evaluated on a Samsung Galaxy S smartphone. It was necessary to root the devices to ensure context awareness and efficient memory utilization to facilitate the implementation of this software. The experiment consisted of three stages: scheduler evaluation, memory evaluation, and ring profile evaluation (Lee & Lin, 2019). The initial experiment involved assessing the ring profile changer, wherein various noise levels were examined. The mobile device exhibited the capability to discern between varying degrees of ambient noise and then adjusted its ring profiles correspondingly.
In order to evaluate the scheduler, two applications were executed for 10 minutes each. The CPU time allocated to each application was measured according to their respective priorities. The understanding of test time constraints was acquired from the study conducted by Elazhary et al. (2017), which provides valuable insights into the usage habits of smartphone applications. In summary, the experiment involved utilizing the Facebook (FB) and Gmail (GM) applications, with each app being subjected to a specific usage pattern. In the context of Facebook, we engaged with textual content by reading updates and accessed visual content by downloading ten photographs. Similarly, within the framework of Gmail, we interacted with textual content by reading five emails and participated in exchanging information by sending a single email.
The examination of the scheduler can be classified into four distinct tests. The initial experiment used a favorable parameter of -5 (FB2, GM2), followed by a subsequent trial employing a favorable parameter of -10 (FB2, GM2). A third experiment was then conducted utilizing a favorable parameter of -20 (FB3, GM3). Lastly, the last test was performed with a favorable parameter of -10 but with an intense CPU process running concurrently. After each experiment’s completion, data files, including the recorded CPU time values, were acquired. A minimum of 20 tests were conducted to assess the impact of priority-level modifications.
The primary objective of the experiment was to quantify the CPU time obtained after initiating the test. However, due to the inability of conventional Android tools such as DDMS (Dalvik debug monitor server) and logcat to profile the application externally and the lack of compatibility between the Linux benchmarking suits (e.g., Oprofile, Imbench, and Interbench) and the Linux version operating on the system, CPU time values were documented from the Proc file system (Jeong, 2019). The Proc file stores and manages statistical information for each process. It is executed through the use of shell scripts. According to Lee et al. (2017), the primary shell script terminates the running applications just prior to the commencement of the experiment.
Additionally, it initiates the CPU-intensive operation. In addition, the primary shell script can detect changes in application process IDs (PIDs) that occur due to forced closures or restarts. When such changes occur, the script saves the corresponding time values with the new PID (Ariyapala et al., 2019).
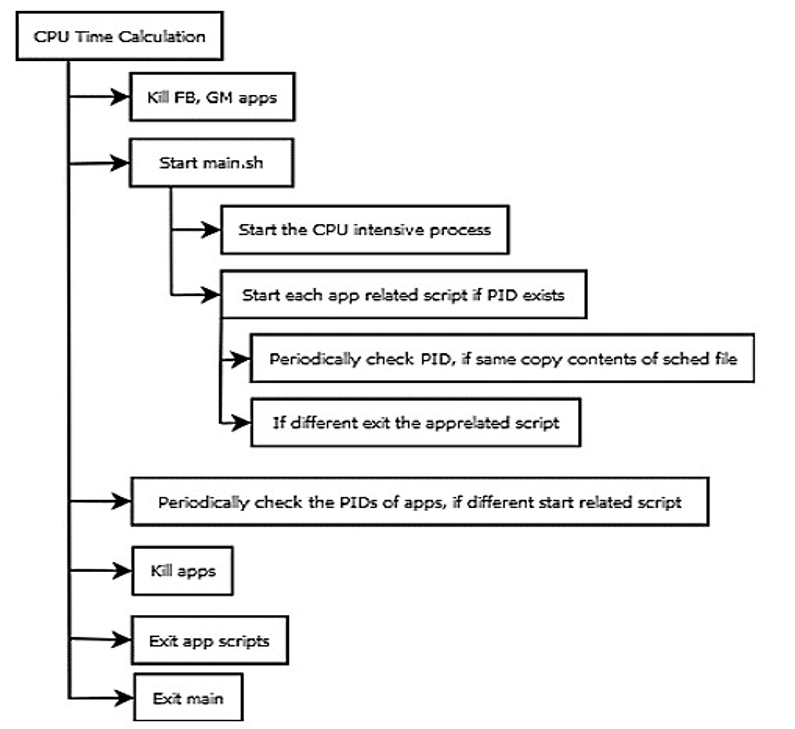
Figure 3: CPU execution time calculation process flow
The experiments were conducted on the Context OS and the Stock Android kernel. The CPU execution times of both operating systems were compared using the Mann-Whitney test, a nonparametric version of the t-test. However, the Mann-Whitney test does not make any assumptions about the distribution of the data. In this experiment, two hypotheses were formulated.
- Two samples can be derived from the same populations.
- Samples obtained from distinct populations are likely to have dissimilar characteristics.
The statistical test, commonly referred to as U, is utilized to assess the significance of data. Specifically, the observed values above the critical value at a predetermined significance level of 0.05 indicate support for rejecting the null hypothesis and favoring the alternative hypothesis. The present study shows that when the P value is less than 0.05, it indicates that the sample data, precisely the run time, originates from distinct populations. Furthermore, there is a substantial influence on the CPU time value due to the alteration of context-aware priority. The summary of these findings is presented in Table 3 below.
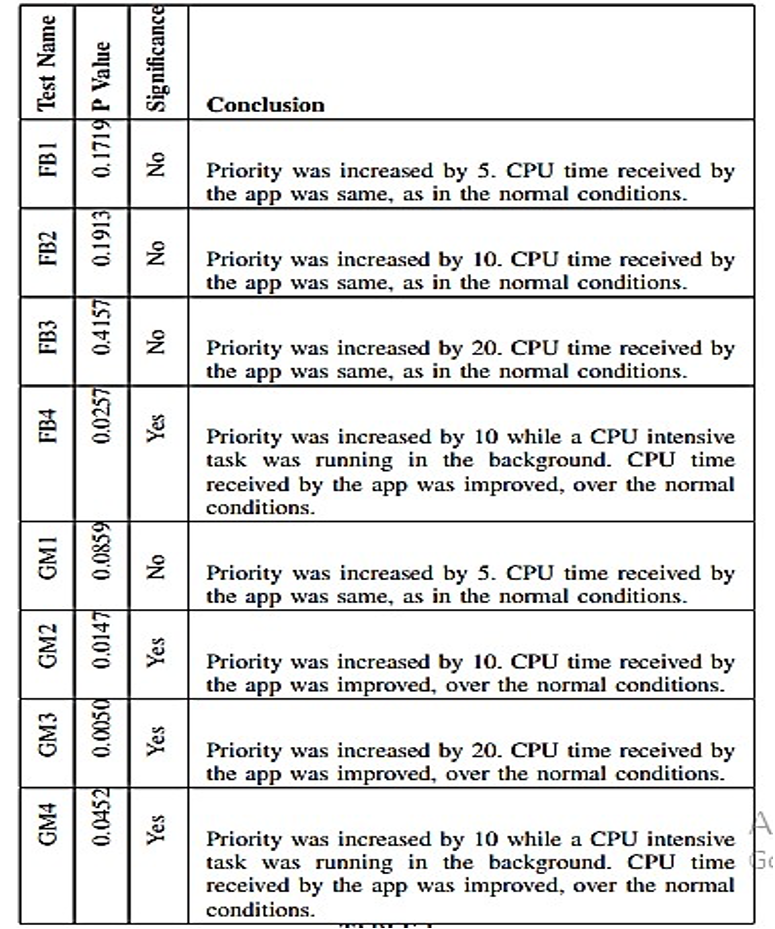
Table 3: Summary of mann-whitney test
The test names, mann-whitney p-value, significance, and conclusion as they relate to the computed p-value are shown in Table 3 above. In test FB4, for example, the first sample value was obtained by executing the FB application in a CPU background processing mode that was quite intensive. The second sample was acquired after raising the priority to 10 and performing extensive CPU background processing. The application’s CPU time value significantly improved due to a priority increase, as indicated by the p-value of 0.0257, which is less than 0.05.
Discussion
Despite being based on the Linux 2.6 kernel, the Android kernel exhibits particular distinctions from the mainline Linux kernel. Variations may be observed in components such as Ashmem, Binder Mechanism, and The Power Manager (Zhang et al., 2018). Nevertheless, this distinction does not impact the scheduler in any kind. In addition, the Android operating system employs two mechanisms to effectively control CPU time allocation: priority levels and C groups. The priority levels in the Android operating system are denoted by the excellent value, which spans from +19 to -20 (Schlegel et al., 2018). Notably, these values exhibit an inverse relationship with priority since lower excellent values are allocated more CPU time than higher nice values. The default lovely value for all user interface threads is set at 0, while an excellent value of 10 is designated for background processes. (Mongia & Madisetti, 2020).
Furthermore, it has been observed that all the background tasks are consolidated under a singular container, known as C groups, in order to enforce a limitation on their CPU consumption, ensuring that they do not exceed 10% (Hu et al., 2019). This implies that even if all background applications are initiated, none of these processors can exceed a utilization rate of more than 10% of the total CPU time. This ensures that the foreground application consistently receives an adequate allocation of CPU time.
I am examining the inherent characteristics of the Android operating system. The context-aware Android operating system does not impact application priority. Regardless of the increased importance in the context of OS, foreground applications are consistently assigned high priority (Wang & Ahmad, 2020). Nevertheless, including a core future in Context OS has resulted in a noteworthy enhancement of the CPU time allocated to intense CPU tasks running in the background. Numerous studies have indicated that the enhanced functionality of mobile phone devices has resulted in a significant proportion of these devices remaining unused (Zhao et al., 2018). The use of context-aware priority change can prove advantageous in optimizing the utilization of this gadget. When the phone is identified as idle and attached to a charger, it is possible to provide a higher priority to the cloud computing process, in contrast to instances when the phone is occupied and not charging.
Implementation
This section provides an overview of the primary implementation details of ContextOS. The current implementation is available in two distinct forms: a kernel module and a userspace application. Rjeili et al. (2019) assert that the kernel module represents a recent inclusion within the Android operating system. The project implementation relies on two Android sources: the goldfish kernel, utilized in the accumulator, and the GT-I9000 kernel, employed in the Samsung Galaxy S. The following is a concise elucidation of a userspace application.
The Context App consists of a configuration user interface (UI) and a service that runs periodically. Curum and Khedo (2019) assert that the user interface (UI) effectively manages the coordinates of a specific location, facilitates the assignment of names to corresponding sites for convenient utilization, and enables the association of a preferred set of applications with the location. In addition, the system can initiate and terminate the service (Curum & Khedo, 2019). Using the Java programming language and Android-specific concepts, such as list views and custom adapters, is prevalent in implementing user interfaces (UIs). Location data can be accessed by utilizing location managers provided by the framework. According to Elazhary (2017), the limitation of GPS functionality in indoor environments creates an opportunity to utilize network location technology. The data obtained from the user interface is stored in an SQLite database.
The implementation of a periodically running database is facilitated through the utilization of an Android service. The service’s primary function is to detect and analyze the surrounding environment and execute appropriate actions based on the configurations stored in the database. Frequently, periodically monitored location values become desynchronized from the stored values of the user. In this particular scenario, we must ascertain whether the user is situated within a predetermined geographical area. Hence, it is appropriate to designate a circular area with a radius of 500 metres surrounding the predetermined location. The calculation of the spatial separation between two geographical points entails the utilization of the Android function, as denoted by the equation “Dist. between (startLat, startLon, endLat, endLong, results).”
According to Zhang et al. (2018), startlat and startLon represent the geographical coordinates of a predetermined location. In contrast, “endlat” and “endLon” represent the present geographical coordinates. The distance measured in metres, stored in the variable “results,” has been computed. The steps outlined in the initial algorithm are executed based on the obtained results. Determining the Process ID (PID) associated with a specific process entails the utilization of the RunningAppProcessInfo.pid variable, which is inherently linked to each running process. The measurement of background noise level is accomplished by utilizing an integrated microphone. As stated by Natarajasivan and Govindarajan (2016), the Media Recorder API facilitates the implementation of the MediaRecorder function. The function gets Amplitude () is utilized to accurately measure the maximum Amplitude that is detected through the utilization of a microphone. The provided equation was utilized to compute the decibel measurement based on the Amplitude.
akespowerDb = 20*log10(amplitude/referenceAmp)
An average value is used for the Amplitude, with ten samples spaced out over 200 ms. The determined decibel level changed the band profile. The entire ring profile is picked, or the vibration mode is chosen if the computed decibel total reaches 70 dB.
C-java Helper
This component uses C to communicate with the kernel module (Curum & Khedo, 2019). JNI was added to facilitate communication between the C-java Helper and the ContextER application. Using the Android Native Development Kit (NDK), the C-Java helper was implemented and compiled into a loadable dynamic library. The program must load this library at runtime, and JNI function calls will be used to call the library’s methods. This component mostly uses IOCTL calls-to-call methods within the kernel module (Elazhary, 2017).
Context Module
The primary objective of the Context Module, as identified by Curum and Khedo (2019) in their research, is to modify the prioritization of apps. These roles are performed through the utilization of the set_user_excellent () function. The arguments about this function encompass the process task structure and the distinct value transmitted to the module by the C-Java Helper component. Identifying the associated process’s structure places significant focus on the task list. The process identification (PID) must be utilized during this exercise. Despite the simultaneous emergence of challenges during the process of iterating the task list, the implementation of a concurrency mechanism establishes control. Once the module has been finalized, it must be compiled with the appropriate kernel source. When utilizing the module within the emulator, it is necessary to compile it against the goldfish Kernel. This is particularly relevant when the target device is the Samsung GT-I9000 with its respective kernel. The procedure above occurs due to the inclusion of supplementary code into the kernel during runtime using a loadable kernel module. This module must be compatible with the operating kernel (Rjeili et al., 2019).
Issues and Challenges
The utilization of ContextOS in conjunction with smartphones has demonstrated a multitude of technological improvements in the domain of context awareness. Nevertheless, several unresolved matters and obstacles still require attention and resolution.
The matter of user profiling posed significant challenges. Individuals who utilize cell phones exhibit varying usage habits with respect to these devices. Comprehending this pattern is a challenging endeavor. However, once the pattern has been detected, it allows for providing personalized services to the user. De Matos et al. (2017) argue that utilizing the machine learning framework is the most effective approach for addressing these challenges. One example of an often-utilized framework on Android devices is the WEKA machine learning workbench (De Matos et al., 2017).
Moreover, facilitating smartphone users’ transition from mere gaming engagement and communication with acquaintances and relatives to educational pursuits will constructively contribute to addressing this issue (Bibri, 2018). Educators or mentors should actively promote using educational tools like the MApp to enhance students’ proficiency in targeted learning objectives. This facilitates the users in developing a more comprehensive comprehension of the integration of user profiling.
Furthermore, in order to enhance the contextual understanding, a limited number of two sensors were employed. The two sensors encompassed in the system are the Global Positioning System (GPS) and the microphone (MIC). Incorporating several sensors into the ContextOS posed a significant challenge due to its potential to enhance the refinement of user context. According to a study by López-Iturri et al. (2017), additional sensors possess diverse technological capabilities that enhance the provision of a more efficient context. Restricting the quantity of sensors hinders the speed of the process or impairs the ability of ContextOS to deliver optimal outcomes.
Moreover, the users of the sensors have access to a restricted amount of information. The individual can acquire knowledge and comprehension about a limited number of sensors. However, they need more technical expertise to engage with additional sensors that may be introduced subsequently effectively. A prominent illustration can be seen in the security field, where the pervasive issue of precisely recognizing location is prevalent. According to Tran et al. (2017), only two sensors need to provide more precision for discerning the user’s focus in situations where many places of potential interest require attention. The deployment of two sensors in circumstances where geographical data systems are necessary to give precise and comprehensive information for accurate suggestions also impacts security (Tran et al., 2017).
Additionally, the research has discovered the limitation of solely focusing on the scheduling system. The absence of crucial systems such as security, energy, and memory management inside the ContextOS is noteworthy. Yue et al. (2016) argue that preventing these difficulties can be achieved by integrating rigorous and extensive research on alternative systems to diversify. In addition, integrating additional systems into ContextOS can yield improved solutions for addressing scheduling systems (de Matos et al., 2017). According to López-Iturri et al. (2017), planning timely recommendations for systems is crucial to maintain their relevance. When the system depends on transmitting contextual data to remote servers to generate recommendations, locations characterized by limited network access may encounter delays in delivering those recommendations.
Ultimately, the incorporation of context awareness into mobile phones was impeded by the presence of hardware restrictions. This issue prompted academics to allocate significant resources in terms of time and funding to explore potential enhancements for integrating context awareness into mobile computing (Bibri, 2018). The difficulties above are straightforward and readily manageable.
However, allocating ample resources and acquiring technical expertise are crucial in effectively addressing these challenges. The issue of ContextOS is intricate and necessitates the employment of seasoned individuals in many organizations and governmental sectors, particularly in areas like security that rely on this system. The responsibilities of individuals in this position involve addressing and managing various issues and obstacles that may develop to ensure the organisation’s efficient operation.
Conclusion
This project aims to demonstrate the motivation behind optimizing the operating system’s behaviour based on the context information. In addition, it demonstrates a behavior that has never been seen before implementing context-aware scheduling at the Android Kernel level. When compared to when context awareness was implemented at the application level, the result was that there was a significant improvement in the scheduling of the context when it was implemented at the OS level. In addition, context-aware scheduling has significantly improved when a CPU-intensive job is operating in the background. This is in addition to the fact that there has been a slight increase in the amount of overhead in terms of power consumption, and the phone’s memory management has been optimized.
References
Al-Fedaghi, S. (2017). Context-aware software systems: toward a diagrammatic modelling foundation. Journal of Theoretical and Applied Information Technology, 95(4), 936.
Ariyapala, K., Conti, M., & Keppitiyagama, C. (2019, August). Contextos: A context-aware operating system for mobile devices. In 2013 IEEE International Conference on Green Computing and Communications and IEEE Internet of Things and IEEE Cyber, Physical and Social Computing (pp. 976-984). IEEE.
Bai, G., Gu, L., Feng, T., Guo, Y., & Chen, X. (2019, September). Context-aware usage control for Android, in International Conference on Security and Privacy in Communication Systems (pp. 326–343). Springer, Berlin, Heidelberg.
Bibri, S. E. (2018). Big Data Analytics and Context-Aware Computing: Characteristics, Commonalities, Differences, Applications, and Challenges. In Smart Sustainable Cities of the Future (pp. 481–533). Springer, Cham.
Cabrera, O., Franch, X., & Marco, J. (2019). 3LConOnt: a three-level ontology for context modelling in context-aware computing. Software & Systems Modeling, 18(2), 1345-1378.
Chakraborty, S., Raghavan, K. R., Johnson, M. P., & Srivastava, M. B. (2018, February). A framework for context-aware privacy of sensor data on mobile systems. In Proceedings of the 14th Workshop on Mobile Computing Systems and Applications (pp. 1–6).
Chakraborty, S., Shen, C., Raghavan, K. R., Shoukry, Y., Millar, M., & Srivastava, M. (2018). Ip Shield: a framework for enforcing context-aware privacy. In 11th {USENIX} Symposium on Networked Systems Design and Implementation ({NSDI} 14) (pp. 143156).
Curum, B., & Khedo, K. (2019). AMBLE: A Context-Aware Mobile Learning Framework. EAI Endorsed Transactions on Context-Aware Systems and Applications, 6(19).
de Matos, E., Amaral, L. A., & Hessel, F. (2017). Context-aware systems: technologies and challenges in the Internet of Everything environments. In Beyond the Internet of Things (pp. 1-25). Springer, Cham.
Dey, A. K. (2018). Context-Aware Computing. In Ubiquitous computing fundamentals (pp. 335–366). Chapman and Hall/CRC.
Elazhary, H. (2017). Context-aware mobile application task offloading to the cloud. Context,
Elazhary, H., Althubyani, A., Ahmed, L., Alharbi, B. A., Alzahrani, N., & Almutairi, R. (2017). Context management for supporting context-aware Android applications development. International Journal of Interactive Mobile Technologies (iJIM), 11(4), 186–201.
Elazhary, H., Althubyani, A., Ahmed, L., Alharbi, B. A., Alzahrani, N., & Almutairi, R. (2017). Context management for supporting context-aware Android applications development. International Journal of Interactive Mobile Technologies (iJIM), 11(4), 186–201.
Elmalaki, S., Wanner, L., & Srivastava, M. (2018, September). Caredroid: Adaptation framework for Android context-aware applications. In Proceedings of the 21st Annual International Conference on Mobile Computing and Networking (pp. 386-399).
Gu, T., Wang, X. H., Pung, H. K., & Zhang, D. Q. (2020). An ontology-based context model in intelligent environments. arXiv preprint arXiv:2003.05055.
Hu, D. H., Dong, F., & Wang, C. L. (2019, May). A semantic context management framework on a mobile device. In 2019 International Conference on Embedded Software and Systems (pp. 331-338). IEEE.
Jeong, E. (2019). Context-aware Background Application Scheduling in Interactive Mobile Systems.
Khozouie, N., Fotouhi-Ghazvini, F., & Minaei-Bidgoli, B. (2017, November). Developing a context-aware mobile patient monitoring framework with an ontology-based approach. In 2017 IEEE 4th International Conference on Smart Instrumentation, Measurement and Application (ICSIMA) (pp. 1-5). IEEE.
Knappmeyer, M., Kiani, S. L., Frà, C., Moltchanov, B., & Baker, N. (2018, May). Contextual: A lightweight context representation and context management schema. In IEEE 5th International Symposium on Wireless Pervasive Computing 2018 (pp. 367-372). IEEE.
Lee, J., & Lin, K. J. (2019, July). A context management framework for real-time SOA. In 2010 8th IEEE International Conference on Industrial Informatics (pp. 559–564). IEEE.
Lee, J., Lee, K., Jeong, E., Jo, J., & Shroff, N. B. (2017, September). Context-aware application scheduling in mobile systems: What will users do and not do next? In Proceedings of the 2017 ACM International Joint Conference on Pervasive and Ubiquitous Computing (pp. 1235–1246).
Linsky, J. B. (2017). US Patent No. 9,648,490. Washington, DC: US Patent and Trademark Office.
López-Iturri, P., Aguirre, E., Azpilicueta, L., Astrain, J. J., Villandangos, J., & Falcone, F. (2017). Challenges in wireless system integration as enablers for indoor context-aware environments. Sensors, 17(7), 1616.
Mongia, B. S., & Madisetti, V. K. (2020). Reliable real-time applications on Android OS. IEEE Electrical and Computer Engineering Electrical and Computer Engineering.
Natarajasivan, D., & Govindarajan, M. (2016, August). Location-based context-aware user interface recommendation system. In Proceedings of the International Conference on Informatics and Analytics (pp. 1-6).
Pensabe-Rodriguez, A., Lopez-Dominguez, E., Hernandez-Velazquez, Y., Dominguez-Isidro, S., & de la Calleja, J. (2020). Context-Aware Mobile Learning System: Usability Assessment Based on a Field Study. Telematics and Informatics, 101346.
Rjeili, J. A., Freedman, J. L., & Momchilov, G. (2019). US Patent Application No. 16/269,726.
Schlegel, R., Zhang, K., Zhou, X. Y., Intwala, M., Kapadia, A., & Wang, X. (2018, February). Soundcomber: A Stealthy and Context-Aware Sound Trojan for Smartphones. In NDSS (Vol. 11, pp. 17-33).
Sezer, O. B., Dogdu, E., & Ozbayoglu, A. M. (2017). Context-aware computing, learning, and big data in the internet of things: a survey. IEEE Internet of Things Journal, 5(1), 1-27.
Trainor, J. (2019). US Patent Application No. 15/799,155.
Tran, T. X., Hajisami, A., Pandey, P., & Pompili, D. (2017). Collaborative mobile edge computing in 5G networks: new paradigms, scenarios, and challenges. IEEE Communications Magazine, 55(4), 54-61.
Wang, A. I., & Ahmad, Q. K. (2020, November). Camf-context-aware machine learning framework for Android. In Proceedings of the International Conference on Software Engineering and Applications (SEA, 2010), CA, USA.
Yue, S., Yue, S., & Smith, R. (2016). A survey of testing context-aware software: Challenges and resolution. In Proceedings of the International Conference on Software Engineering Research and Practice (SERP) (p. 102). The Steering Committee of The World Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp).
Zhang, M., Duan, Y., Yin, H., & Zhao, Z. (2018, November). Semantics-aware android malware classification using weighted contextual API dependency graphs. In Proceedings of the 2014 ACM SIGSAC conference on computer and communications security (pp. 1105–1116).
Zhao, X., Guo, Y., Feng, Q., & Chen, X. (2018, March). A system context-aware approach for battery lifetime prediction in smartphones. In Proceedings of the 2011 ACM Symposium on Applied Computing (pp. 641–646).
 write
write