Introduction
With the Internet of Things (IoT) in practically every aspect of modern life, the growth of linked devices brings potential and concerns. First, its unmatched efficiency and usability transform domestic and industrial equipment. However, it exposes many cybersecurity vulnerabilities that threaten vital infrastructures and privacy. Both sides point to IoT device security problems that hackers might exploit to steal sensitive data, threaten national security, and cause massive economic damage. The previously submitted Researched Argument Essay explains these complications. The article described how IoT devices in essential areas like healthcare, finance, and utilities have expanded hackers’ target area. The examination revealed vulnerabilities caused by poor security, underlining the need for a new Internet of Things security strategy—the Research Project Proposal also detailed ways to address these issues (Ahmad et al. 16). The proposed exploratory project used blockchain and AI to improve stakeholder awareness of cybersecurity issues and generate new safeguards.
Based on these core findings, this study will propose a complete IoT cybersecurity strategy. Better authentication, encryption, regulatory compliance, and user education form a holistic security system that can adapt to new threats. This proposal needed careful research of all relevant sources. At least five reliable sources, such as expert analyses, review papers, and recent empirical studies, were evaluated to verify that the suggestions were based on current research and industry standards. This technique also uses new sources to overcome the challenges of delivering security changes. These sources were used to create a meticulous implementation approach to handle present and future IoT cybersecurity issues, considering technology’s rapid progress and cyber threats. IoT devices need better cybersecurity than ever. As the research progresses, it will provide extensive recommendations for defending the physical and digital worlds against IoT ecosystem dangers. In this increasingly interconnected world, we struggle for our way of life and technology security.
Recommended Solution
Given the growing number of vulnerabilities in the IoT ecosystem, a comprehensive approach is needed to improve security. This comprehensive plan uses blockchain and AI, promotes cybersecurity awareness among IoT value chain stakeholders, and creates new security frameworks. The plan aims to strengthen defenses against threats and set the stage for future successes.
Development of New Security Frameworks
Development and implementation of IoT-specific security frameworks underpin the suggested solution. These frameworks should protect IoT devices and platforms with secure device authentication, data encryption, and network security. Standardized security protocols help IoT networks withstand new cyber threats by speeding up security updates and improving interoperability.
Adoption of AI and Blockchain Technologies
Blockchain and AI could transform IoT security. AI-powered systems may analyze massive amounts of information for trends and outliers to discover and prevent emerging cyber threats. Blockchain technology can also prevent man-in-the-middle attacks and verify data during device-to-device transfers by creating an immutable record (Ghiasi et al. 108975). These technologies will improve IoT security frameworks’ ability to survive complex attacks.
Initiation of a Cybersecurity Culture
Long-term IoT ecosystem security requires a strong cybersecurity culture. By teaching developers, consumers, and administrators about security best practices, we seek to promote a security-first approach throughout the IoT device and system lifetime. Regular awareness campaigns, workshops, and training are essential to teach stakeholders about security threats and measures.
Implementation Steps
To adopt recommended security measures, follow these steps:
Develop novel security procedures and solutions with top academic institutions, think tanks, and corporations. The key goals of this research and development phase are scalable, energy-efficient, and IoT infrastructure-compatible solutions.
Full training should be accessible to developers, manufacturers, and end-users. This training should address secure coding, device setting, and security maintenance. These actions should help IoT ecosystem members improve their security.
Partner with cybersecurity firms to use their experience and resources. By working together, we can share cyber threat expertise and accelerate the adoption of cutting-edge security solutions (Lee 157).
Structure and Participants
Several parties must work together to achieve the security enhancement plan:
Cybersecurity researchers will study blockchain and AI and design new security methods.
IoT device manufacturers should ensure their products meet industry standards and feature the latest security methods.
Software engineers will actively create new security solutions and use secure coding.
Patching, configuration changes, and following best practices dramatically improve IoT device security (Ma 8000).
Internet of Things (IoT) security has three phases: initial R&D, deployment (integrating these solutions into IoT devices and systems), and maintenance (training, monitoring, and updates to respond to new security threats). The implementation will follow these three steps.
Summary analysis chart
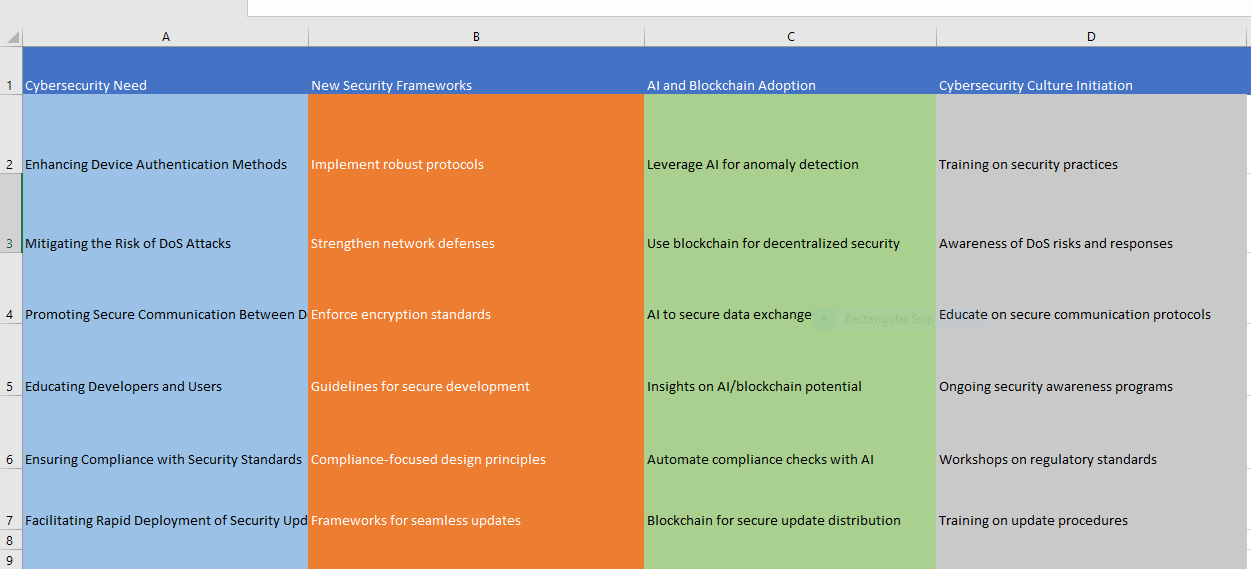
Implementation
Time Frame and Sequence
Initial Research and Development Phase (Months 1-6): This age sees academic and research institutes working on AI and blockchain security frameworks. Finding partners, funding, and starting research initiatives are all part of the process.
Deployment Phase (Months 7-12): This phase integrates security protocols from the research and development phase into Internet of Things systems and devices. Training users and developers, partnering with cybersecurity businesses, and releasing security fixes and frameworks are vital (Sarker 300).
Maintenance and Evaluation Phase (Months 13-18): In the last phase, I will monitor security measures, train personnel, and collect feedback. This phase is crucial for assessing strategy effectiveness and making modifications.
Measurement of Effectiveness
To assess solution efficacy, we will utilize quantitative and qualitative metrics:
Incident response time: Cyber incident response time is how quickly issues are recognized and remedied.
Incident frequency: Reports of attacks or security breaches are decreasing. Compliance by Users:
More users and developers adopt security best practices.
System uptime: Internet of Things systems’ increased availability suggests they can endure DDoS attacks. To further understand the practical issues and security measures from the user’s perspective, we will consult stakeholders, including software developers, end-users, and IoT device manufacturers.
Plan Revision
A continual feedback loop will allow the plan to adapt to new input and difficulties. This procedure has these steps:
Key stakeholders meet every three months to review the strategy, discuss issues, and make improvements.
We regularly conduct comprehensive security audits to eradicate emerging cyber dangers from the IoT ecosystem (Sonnad et al. 56).
Distributing surveys to stakeholders lets us gather thorough input from developers, manufacturers, and users on security measures’ usability, efficacy, and areas for improvement.
By iteratively modifying our cybersecurity strategy, we can stay current and adapt to the changing IoT ecosystem.
Persuasive Concluding Argument
Cyber threats are constantly changing, making IoT device protection more vital. These technologies have simplified and streamlined our personal and professional lives and revealed substantial security vulnerabilities. These vulnerabilities threaten sensitive financial data, individual identities, and our nation’s vital public services infrastructure. Our comprehensive IoT ecosystem protection strategy combats these widespread dangers. Our recommendations were based on research and industry norms. Their comprehensive strategy includes creating a pervasive cybersecurity culture, robust security frameworks, and new AI and blockchain applications. This cybersecurity strategy can adapt to existing and future threats.
Many practical benefits can be accomplished with this method. Increasing device authentication can significantly reduce illegal access. Protecting essential IoT services from denial-of-service attacks maintains their availability and reliability. Data integrity and confidentiality are enhanced by encouraging devices to communicate securely. Educating developers, users, and administrators on best practices strengthens the ecosystem and promotes proactive cybersecurity. Our suggestions match the company’s goals and needs precisely. Improved IoT cybersecurity can protect us from current threats and help IoT technology remain stable and reliable. This crucial sector is ready for additional growth and development.
Our ideas are backed by extensive study. Repeated studies show that cybersecurity knowledge lowers risk, that AI and blockchain offer novel ways to identify and prevent cyberattacks, and that comprehensive security frameworks function. The results prove our strategy’s credibility and capacity to address the organization’s cybersecurity needs. Finally, we must implement our entire cybersecurity plan to protect Internet of Things technologies. These suggestions will strengthen digital infrastructure and offer new perspectives on issues. We hope the funding organization approves. We must protect our interconnected world now to ensure a great future.
Work Cited
Ahmad, Waqas, et al. “Cyber security in iot-based cloud computing: A comprehensive survey.” Electronics 11.1 (2021): 16. https://www.mdpi.com/2079-9292/11/1/16
Ghiasi, Mohammad, et al. “A comprehensive review of cyber-attacks and defense mechanisms for improving security in smart grid energy systems: Past, present and future.” Electric Power Systems Research 215 (2023): 108975. https://www.sciencedirect.com/science/article/abs/pii/S0378779622010240
Lee, In. “Internet of Things (IoT) cybersecurity: Literature review and IoT cyber risk management.” Future Internet 12.9 (2020): 157. https://www.mdpi.com/1999-5903/12/9/157
Ma, Chen. “Smart city and cyber-security; technologies used, leading challenges and future recommendations.” Energy Reports 7 (2021): 7999–8012. https://www.sciencedirect.com/science/article/pii/S2352484721007265
Sarker, Iqbal H., et al. “Internet of things (iot) security intelligence: a comprehensive overview, machine learning solutions and research directions.” Mobile Networks and Applications 28.1 (2023): 296–312. https://link.springer.com/article/10.1007/s11036-022-01937-3
Sonnad, Shashidhar, et al. “The integration of connectivity and system integrity approaches using internet of things (IoT) for enhancing network security.” 2022 5th International Conference on Contemporary Computing and Informatics (IC3I). IEEE, 2022. 56 https://ieeexplore.ieee.org/abstract/document/10072475
 write
write