Introduction
Today, technology has absorbed every part of people’s everyday lives worldwide. While individuals use technology to fulfill specific duties, companies are also using technology’s ability to expand and enhance their operations. Even if technology promises efficiency and a better future, Markus (2004, p. 5) believes that underlying issues may disrupt routine procedures. Computer-related crimes such as identity theft, illegal access, virus and malware, and intellectual property theft are examples of such problems.
Addressing these issues frequently necessitates the use of digital forensics. Lutui, R. (2016, p .593); Hart and Christensen (2002, p. 51) define digital forensics as the art of gathering, conserving, identifying, documenting, and interpreting digital evidence. Given the University of Fictitious Learning scenario, the study will explain and comprehend the many types of computer crimes to which IT systems may be exposed and the accompanying economic repercussions, including societal ramifications. The paper will also highlight the fundamental concepts of digital forensic investigations on IT systems. Finally, the study will include recommendations on the best course of action to address any misuse.
Methodology
In this situation, the Digital Forensic Research Conference (DFRWS) investigation approach created by Palmer in 2001 would be applied to allow the analysis to acquire good forensic evidence. The model’s efficacy is informed by six primary stages, which are depicted below.
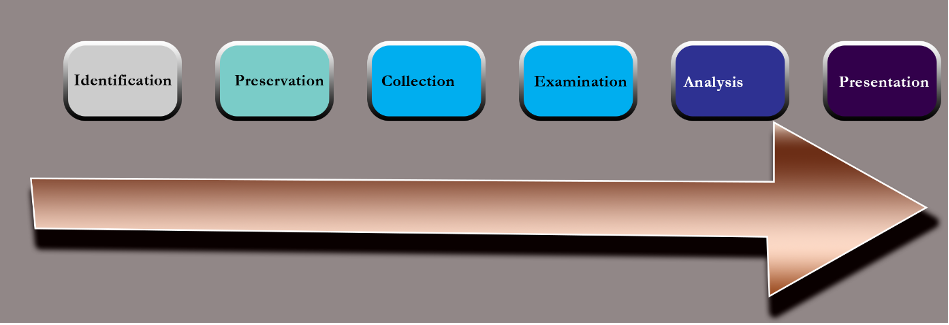
Figure 1: Illustration: Digital Forensic Research Conference (DFRWS) investigative model: adopted by Yusoff et al. (2011)
Identification
Preparation
At this stage, it is critical to evaluate whether law enforcement is required and whether it should extend throughout the inquiry or whether management expects the analyst to produce a report after the investigation (Mabuto, 2013, p. 5). At this point, deciding whether to get formal authorization for the digital forensic inquiry is critical or whether a separate incident response mechanism is in place. Ensuring that suitable protocols are followed in the investigation is essential since improper data management may result in legal ramifications. It is also critical to protect the privacy and confidentiality of consumer data. During this stage, the consultant will also try to figure out the effect of the inquiry on the University of Fictitious Learning’s operations, such as the network downtime duration, loss of revenue, recovery duration, and the loss of sensitive data.
As an independent digital forensic consultant, collecting data about network devices such as routers, hubs, switches, the actual network, computer devices, network topology documentation, firewalls, and servers will also be necessary. Identification of external storage media such as pen drives, flash disks, external hard drives, remote computers, DVDs/CDs, and memory cards.
Preservation
In this inquiry, the preservation phase is critical. The investigation’s preservation phase is vital because it will be utilized to establish the groundwork for providing data integrity. Data change, alteration, and deletion have a significant risk of interfering with the openness of the entire inquiry process. In this situation, some of the primary activities that will be taken to ensure data integrity will involve safeguarding all media and then backing them up `according to the thoughts of (Al-Khateeb, 2019, p.150 ). The necessary tools will also support the network, which will be explored in depth in the following sections. Our method is based on the research of Arshad et al. (2018, p. 346), who mandate that digital forensics be recorded under the needed criteria so that when need be used on legal grounds.
Collection/Acquisition
The primary goal of the collection or acquisition phase is to assist the consultant in collecting, labeling, and acquiring data from questionable devices while preserving data integrity. In this scenario, the consulting recognizes two sorts of data that might be gathered from the investigation site. Volatile and non-volatile data are examples of this sort of data. Volatile data refers to available data while the system is turned on but becomes unavailable when the system is turned off. Caches, registries, and Random Access Memory (RAM) are examples of this data type. The consistent data is referred to as volatile data. This information exists whether or not the computer is turned on. Documents on a hard disk are one example of this data type or any storage device connected to the PC. Because volatile data has a short life cycle, the consulting must utilize the best way to retrieve it (Adat and Gupta, 2018, p. 423; Talesh, 2018, p. 417). The consultant will determine whether to collect the data locally or remotely from the University of Fictitious Learning.
Volatile data
In the case of volatile data, the consultant recommends that the suspect system and the forensic workstation be located on the same LAN. In our scenario, we may utilize the ‘cryptcat’ utility to listen to the Windows NT port server. The practical element of this solution will entail building a trusted toolset in the organization’s Windows NT server’s optical drive, launching the trusted console cmd.exe, and entering the command described below.
cryptcat <ip address> 6543 -k key
Obtaining evidence on the suspicious machine terminal will necessitate the execution of the command given below.
cryptcat -l -p 6543 -k key >> <file name>
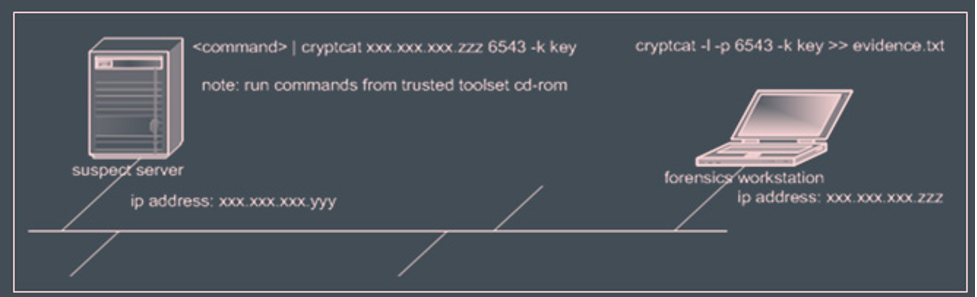
Figure 2; Illustration of the intended volatile data collection configuration
The table below displays the graphical user interface for tools and their related usage and outcomes that may be installed on the suspicious machine workstation.
| Tools | Usage | Outcome |
| Process explorer | It will provide information about running processes, loaded libraries, utilized resources, and so on. | Logged on users, running processes |
| Rootkit Revealer | It will prove essential in detecting kernel mode rootkits and user mode | System date and time, stored in the memory |
| Tcpview | It will be used to display network connections and the associated applications. | Open ports, network connections |
Table 1: volatile data forensic tools, their application, and intended outcomes: adopted from Kao et al. (2018, p. 112)
The consultancy also intends to apply specific Windows-oriented tools to capture volatile data, as shown below.
- HBGray’s F-response- will be helpful for the remote acquisition of physical memory.
- HBGray’s FastDump- useful for the acquisition of physical memory in the local settings
- Ipconfig- will be used to acquire details on the suspect device
- Doskey/history- helpful in collecting command history
- Netusers and qusers- essential for determining logged-in users
- Netfile- vital in identifying services and drivers
The collection of clipboard content in a bid to cover all areas of volatile data will also be used to exhaust this section effectively. There is significant evidence when the suspect machine is in a volatile state, so the consultancy advises that the suspect machine should not be shut down to reach this goal.
Non-volatile data
Following the collection of volatile data, non-volatile data will be collected. The consulting firm will start by copying all the data in the target or suspicious computer. This procedure is also known as forensic imaging. Imaging is critical in this scenario since it will be employed to maintain data integrity. This will be accomplished successfully using the FTK tool. In the case of the University of Fictitious Learning, hard drive cloning will also be utilized. It will be used to create a copy of the complete system. The primary distinction between hard disk cloning and forensic imaging is that forensic imaging can only be performed with the requisite equipment. Still, hard disk cloning may be fulfilled without any forensic tools but a mounted drive. Forensic imaging includes metadata such as hashes and metadata, which is critical in locking all vacant blocks.
Data may be collected through both online and offline tests. Forensic imaging relies heavily on offline forensics. We can use Wireshark or Ethereal tools for online forensic investigation to view live network traffic in our scenario. Non-volatile data collection will get domain controller, firewall, antivirus, and firewall logs during the entire procedure. The consultant will also get the suspect machine’s Web server logs, Windows event logs, database logs, IDS logs, and application logs. Once the team has gathered the digital evidence, it must be documented in the chain of custody log. From the start of the inquiry through the delivery of this investigation report, as specified by Amato et al. (2019, p. 298), the chain of custody log recording will be meant to maintain the integrity of the evidence.
Before the team progresses with the investigation, it will be critical to image the disk bit by bit to access the entire volume and duplicate the original media and the erased contents. After imaging the disk, the consultancy will hash everything to preserve data integrity throughout the investigation. The hash values will be recorded on multiple locations, and we must ensure that no team member alters the data between the time of data collection and the end of the investigation.
Examination
The examination step is another critical component of the digital forensic inquiry. Once the consultancy has successfully collected the appropriate forensic evidence, the data must be examined using various digital forensic investigation techniques (Ademu, 2013, p. 10; McLeod and Dolezel, 2018, p 58). During this portion of the inquiry, the consultancy will investigate the Windows registry, the organizational file system, the database, and the network.
Tools
Access data forensic toolkit (FTK)
The consultant will use this technique to investigate the University of Fictitious Learning’s data breach. FTK is designed to be a comprehensive digital forensic solution or outfit. It will provide us with an aggregate of the necessary tools based on the scenario. FTK will be the solution whether the team intends to break passwords, do email analysis, or discover certain characters in a file. One of the most noticeable features of the utility is that it has an easy-to-use graphic User Interface. FTK is depicted in the diagram below.
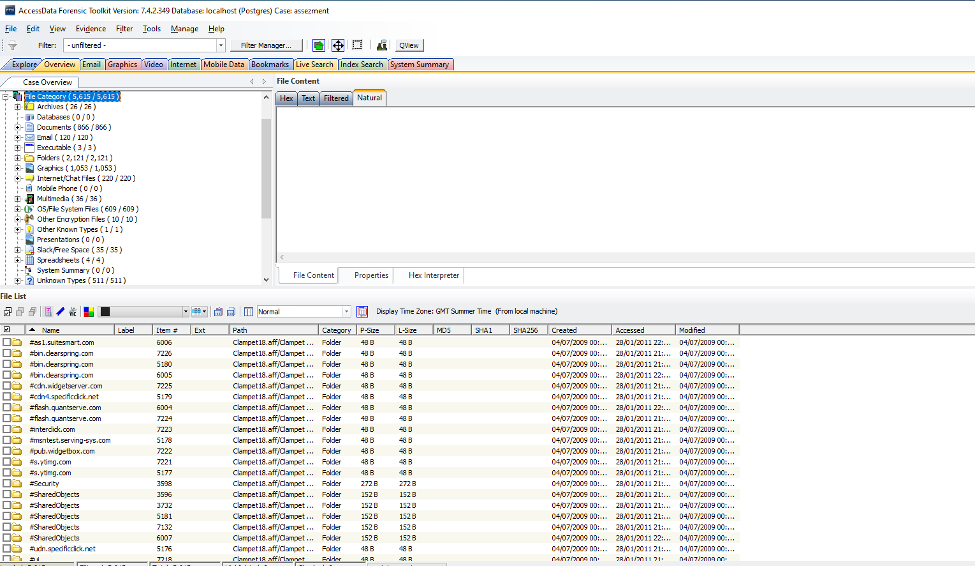
Figure 3: Overview of the FTK
One outstanding characteristic that sets FTK apart from the competition is its performance. The single investigative tool uses a distributed processing approach and multi-core CPUs to deploy parallel organizations. This is good news in our Inquiry
Figure 4: the intuitive GUI of FTK
FTK employs a unique case database. FTK utilizes one primary database for each case, not requiring multiple data set copies. In the case of the University of Fictitious Learning, team members will work more efficiently, preserving valuable resources. The database also enhances stability, distinct from other forensics software that relies on memory. The biggest drawback is that the memory may fail if the capacity exceeds the established parameters; FTK’s database is built on data persistence, which means that data survives even if the memory fails.
FTK will be utilized at the University of Fictitious Learning to assist the consultancy and the team in carving different files depending on formats such as JPEG, HTML,.ZIP, and Ms. Documents. The team will use the tool’s capacity to mirror and produce several formats, such as DD raw, SMART, and EO1. With these ideas, the consultancy can easily track actions through its primary text log file.
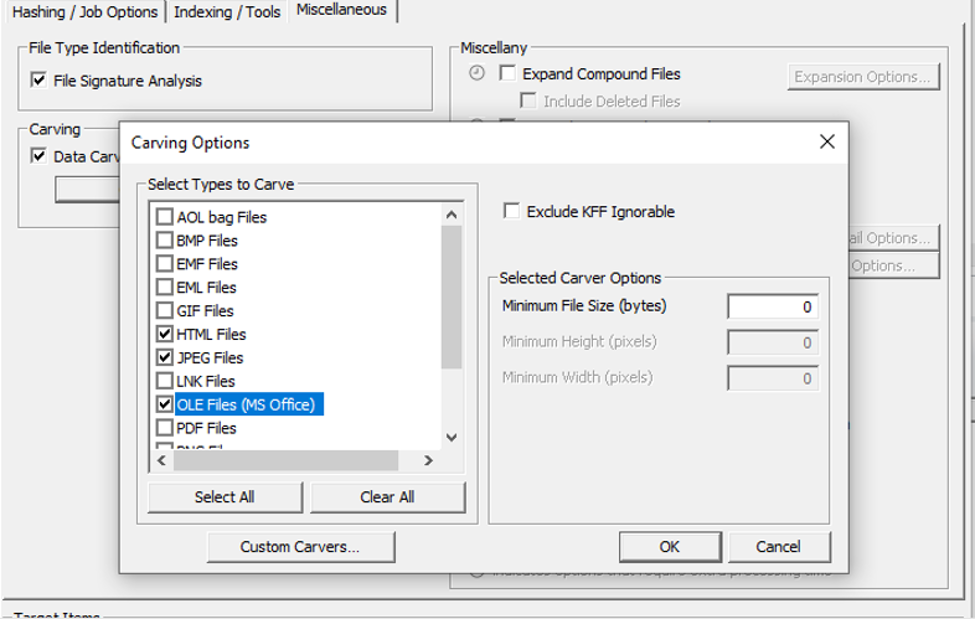
Figure 5: Illustration: access data FTK carving process
When copying original disk drives, it is critical to check file integrity. Creating MD5 and SHA1 hashes, which FTK Imager supports, will be essential in our scenario. The team will also use the program to generate hash reports for future reference. This is necessary to track what has been changed in the suspect machine. After using FTK Imager to create disk drive pictures, the team may use FTK to do more research on the University of Fictitious Learning’s case.
OPH
After finding the suspect device, we will use this program to break passwords on the target system files. SAM and other file formats are included in this example. OphCrack is a free password-cracking application for Windows that uses rainbow tables. Although it also works on Linux and Mac systems, it is the most popular Windows password-cracking application. It is capable of deciphering NTLM and LM hashes. Free rainbow tables are also available for cracking Windows XP, Vista, and 7. The fact that this tool’s performance is predicated on a time-memory trade-off fuels our team’s determination to use it. This implies that it quickly recovers 99.9% of alphanumeric passwords.
Passwords may be recovered from various file formats, including Excel, Zip., and Quicken; OPH will be deployed on a single machine. To support multiple file formats, modules will be utilized. Every module is designed to use the attacks that are best suited to the file type for which it was intended.
Each task gets preference based on the difficulty of the encryption technique used by the software that generated the encrypted file. As jobs, several files can be added. Jobs containing specific types of files will be prioritized based on the collection phase chosen since simpler encryption algorithms process data more rapidly. In this case, retrieved passwords will be kept in a field known as a Golden Dictionary and shown with their corresponding assignment. Because files from the same source likely have the same password, passwords successfully retrieved from files with less sophisticated encryption will be applied to files with more complex encryption.
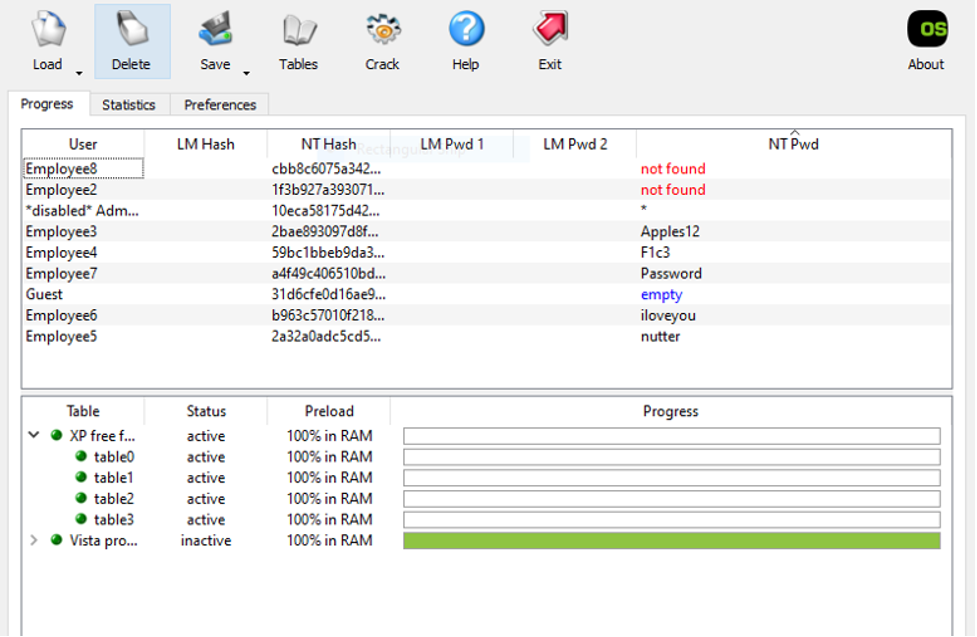
Figure 6; Illustration: OPH cracker in action
PRTK
The firm also intends to employ PRTK to crack passwords on files and SAM. The password recovery toolkit, or PRTK, is a collection of FTK tools that allows forensics to decode and break encrypted data in various ways. At the University of Fictitious Learning, one of the ways to recover passwords will be the inherent lexicon, a collection of phrases related to a specific forensics case. In addition, the team will use the dictionary as a lookup reference to compare the hash value of the actual password to the hash of a word in the dictionary. The team will also use PRTK’s auto-generated Golden Dictionary, which has a list of passwords that have been successfully recovered. In addition to pre-existing dictionaries, PRTK will allow the team to create and export new ones. Because the forensics is aware that many people use passwords based on personal information such as their son’s name, their wife’s date of birth, their husband’s mother’s name, and so on, the consultant will employ PRTK’s Biographical dictionary. This is a one-of-a-kind dictionary built on biographical data of the person of interest to go forward. Name, address, city, state, and other facts can be entered into this lexicon to help the team develop a more successful assault profile.
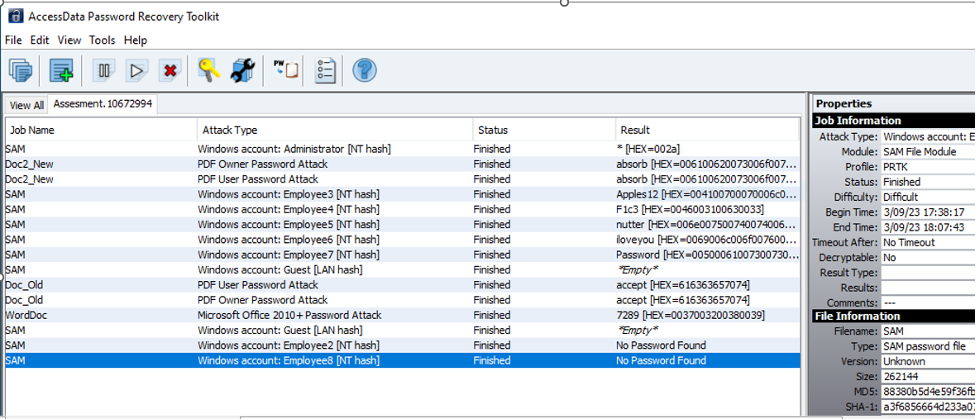
Figure 7: the Illustration of the PRTK tool in action
Registry viewer
After identifying the employee’s information, the PRTK tool will assist the team with cracking the password. The Masker program will also mask any sensitive data contained inside the files. This will be used in conjunction with the registry viewer. The technology will be paired with FTK access data to enhance our understanding of specific data categories, particularly DAT. This sort of information will assist us in determining their work history, last website access, MRU information, and printer access. A registry is classified as a log file since it contains data forensics may access. This is accomplished using the related key-value Lastwrite time, saved as a FILETIME and regarded as the last time the file was updated. The team will review some of the processes outlined in the rest of the article to assess the University of Fictitious Learning’s registry and ensure that problems are resolved internally and externally to maintain data integrity and safeguard the organization’s reputation.
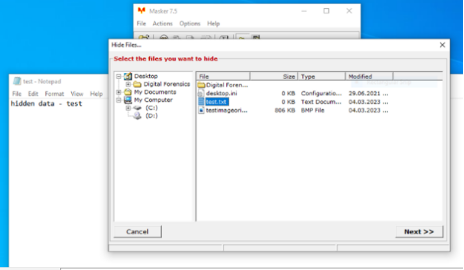
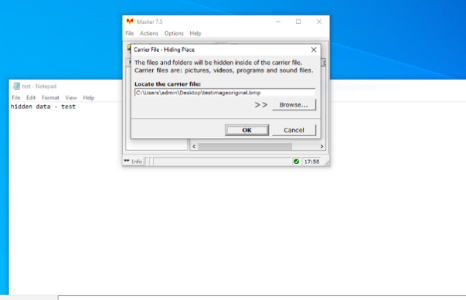
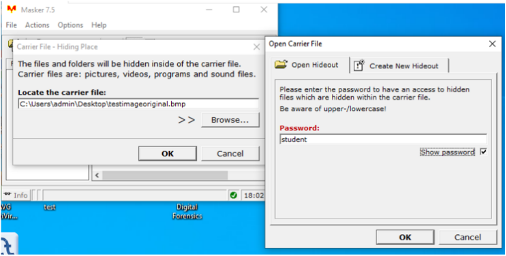
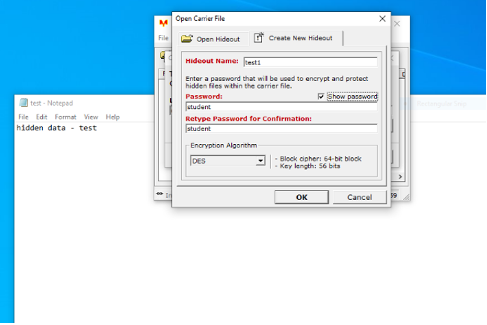
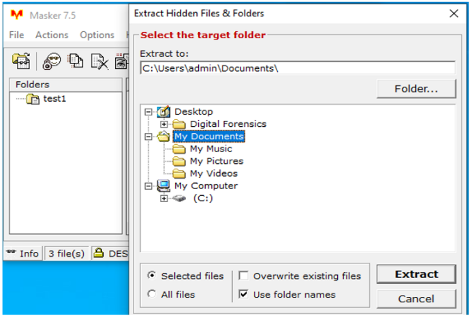
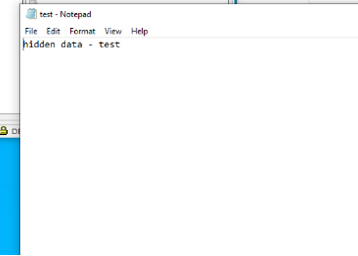
Figure 7: the masker tool in action
“Windows registry” refers to a database order mostly linked with Windows CE, Windows NT, Windows 2000, and Windows 98. It is a reference point for user applications or hardware settings during program or process execution. The typical Windows registry structure is separated into “Hives,” as seen below.
HKEY_CURRENT_USER- harbors the current details of a user logged into the organization system.
HKEY_LOCAL_MACHINE- houses details about drives and hardware
HKEY_CLASSES_ROOT- This registry aims to ensure that programs are executed as required.
HKEY_CURRENT_CONFIG- holds data regarding the existing configuration
HKEY_USE_holds all information of users on a specific system
We all know that the Windows registry contains both volatile and non-volatile information. This means that the team must be familiar with each consequence, functioning of hives, data, keys, and values to produce an accurate forensic report.
Autostart Location is the registry place where apps frequently execute without user interaction. Because it has previously been scheduled to run automatically or when the user executes particular instructions, this feature may target the University of Fictitious Learning to run continually while the computer is turned on without uninterrupted user cooperation. HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsNTCurrentVersionImage File Execution Option, for example, is a Windows registry where an attacker may utilize a key to redirect an application’s original copy to its trojan copy. The University of Fictitious Learning might be the target of this assault, which involves turning the customer’s payment page into an illicit website. In our scenario, it is preferable to investigate the bootstrapping location to determine whether the University of Fictitious Learning problem results from user activity, malware, or an attacker in the organization. To address the issue of auto tracking, the team will use SysInternals.com’s AutoRuns tools, which can provide a list of autorun locations.
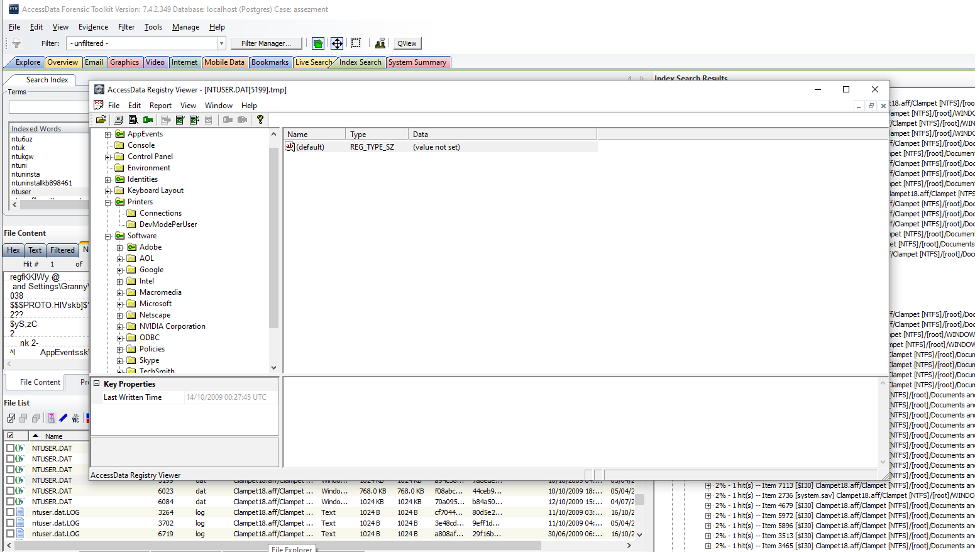
Figure 8: Illustration: Access Data’s registry viewer
UserAssist- – It is found under the hives HKEY_CURRENT_USERSoftwareMcirosoftWindowsCurrentVersionExplorerUserAssist. It retains encrypted records of every item, program. So, a user has visited the system, which contains two sets of keys that commonly resemble generically unique IDs. This characteristic will be used to the consultancy’s benefit by the team. According to Karie et al. (2019, p. 62), if an investigator obtains access to the encrypted record, which is no longer conclusive, it may reveal some user behavior that caused the malware to be activated by an application or other activity, which is very important in this case.
USB removable Storage- The HKEY_LOCAL_MACHINESystemControlSet00xEnumUSBSTOR entry in the computer registry holds information about all connected devices. See the diagram below.
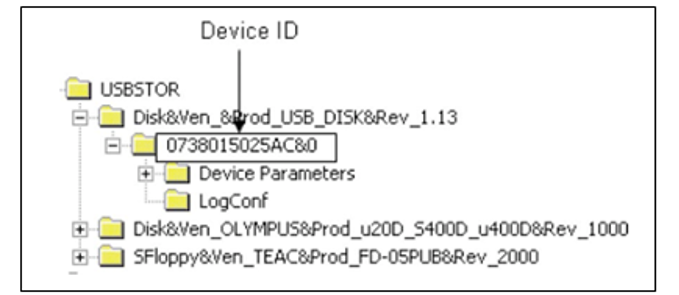
Figure 9: Illustration of a USB thumb drive IDs
In our scenario, the hives of the mounted disk will provide a hint when the investigator checks the device ID material kept at the registry to establish which device was mounted,d on the University of Fictitious Learning organization. By carefully scrutinizing each value key, the team can detect detachable USB storage devices and map them to the parent prefix.
According to Carroll (2008, p.), KEY_LOCAL_MACHINESoftwaremicrosoftWZCSVCParametersThe interface key is the spot where the investigator may locate the SSIDs of wireless networks that are utilized on a PC. When an investigator navigates to the fundamental values, he will discover subkeys that serve as unique identifiers. When the team accesses these subkeys, they can access ActiveSettings, displaying each wifi SSID as a binary data type. SSID is shown in plain written format. Although IP address and other network information can be found under HKEY_LOCAL_MACHINESystemCurrentControlSetServicesTCPIPInterfacesGUID, if a user’s IP address appears to be found under the said Windows registry, team members can use this information to tie the user of the suspect machine to a specific timeframe within University of Fictitious Learning Organizational Setting.
Malware analysis
According to Vance (2016, p. 184) and Tri (2018, p. 11), 99% of vulnerability incidents result in data breaches for a few days, and 85% of these situations take several weeks to investigate. Analysts will agree that this is a significant issue since it stifles organizational progress.
We collectively recognize that the basic notion when executing a malware analysis is that specific components of a Windows PC are anticipated to include facts regarding the virus’s installation and use and that organizations may overlook this fact at times. The legal at the University of Fictitious Learning will comprise an audit of record hash values, signature errors, compressed files, collision logs, System Restore points, and the pagefile. A thorough examination of the event logs and file systems is necessary to determine when the virus first appeared on the system. The team will also examine the registry for changes made in relation to the threat’s installation time and unexpected entries, such as those in Autostart sections. The firm may utilize keyword searches to hunt for malware traces and link to other similar servers. The typical attack channels will be identified, such as Web browser history, unauthorized logins, and email attachments.
The team acknowledges that an inquiry should be performed based on the following parameters:
- Restoration Points
- User accounts review
- File System Examination
- Keyword Search
- Examination of prefetch
- Reviewing Auto-start
- Inspecting executables
- Reviewing Installed Programs
- Reviewing Scheduled Jobs
- Examining Logs
- Searching for recognized malware
- Examining the registry
Before the consultant can begin the investigation, the team is required to establish the malware analysis procedure as a preparatory environment using technologies such as Norton Ghost and VMware. VMware is a virtual-based malware analysis environment, whereas Norton Ghost is a specialized malware analysis environment.
Steganography: Openpuff
It is feasible in various media such as photos, audio, video, text, etc. The most common kind of steganography is image steganography. In our situation, the team will try to use the two primary types: spatial domain and transform domain. The spatial domain is the most popular approach, comprising LSB, MSB, and both LSB-MSB steganography. The Lsb is the most frequent and straightforward approach. The primary focus is on the LSB method steganography tool, which is based on the OpenPuff steganography program. The steganography picture from the OpenPuff tool will be compared on several criteria to choose the best output collection rather than the best format. The counter steganalysis tool will evaluate pixel and bit value changes. PSNR estimation tool will also be employed in the calculation of the PSNR.
In most cases, the consultation team will need that the picture steganography be compared based on resilience, visual distortion, and other factors to maintain it secure from assaults and mistreatment. The file size, which includes input and output size, hiding and extraction time, and so on, will be compared for picture quality and changes in all three formats: BMP, PNG, and JPEG.
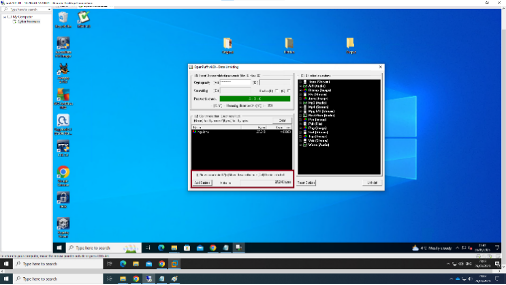
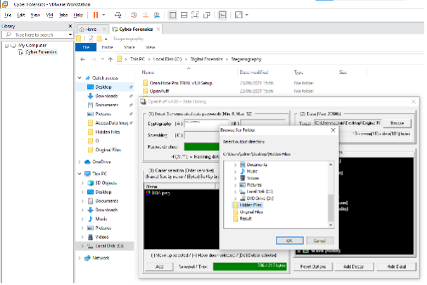
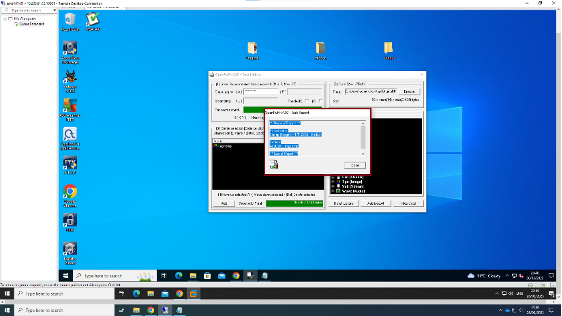
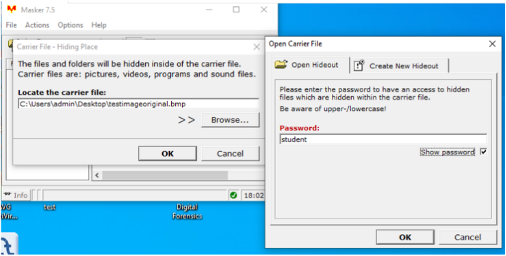
Figure 10: Openpuff tool in action
Capabilities & Limitations
This section offers an appreciation of what tools can and cannot achieve in practice.
| Tool | Capabilities | Limitation |
| FTK | · The single investigative tool adopts a distributed processing approach and utilizes multi-core CPUs to deploy parallel organizations.
· Exploits one central database for each case and does not require multiple data set copies. This implies that team members will work more efficiently, preserving valuable resources. · The database also enhances stability, distinct from other forensics software that relies on memory. |
· Even though FTK’s database is built on data persistence, which means that data survives even if the memory fails, the principal drawback is that the memory may fail if the capacity exceeds the established parameters. |
| OPH | · OphCrack is a free password-cracking application for Windows
· This tool’s performance is predicated on a time-memory trade-off · This implies that it quickly recovers 99.9% of alphanumeric passwords. · |
· Its application and adoption are widely suited for Windows applications and users. |
| Openpuff | · Openpuff is a free tool for hiding confidential data
· Powerful- powerful open-source steganography tool that supports a widespread series of carrier formats such as .JPG, MP3 |
· The tool’s effectiveness is marred by its interface, which has steep learning curves. |
| PRTK | · PRTK’s Biographical dictionary is a one-of-a-kind dictionary built on the biographical data of the person of interest to go forward.
· Name, address, city, state, and other facts can be entered into this lexicon to help the team develop a more successful assault profile. |
The tool is based on educated guesses on certain occasions. |
| · |
Table 2: Capabilities & Limitations of the digital forensic tools
Conclusion
The case of the University of Fictitious Learning has uncovered some of the more complex underlying issues of digital forensics. The comprehensive and intricate inquiry offered insight into the timeline and implications of the organizational breach. The investigation has underlined the need for a robust security system to protect sensitive customer information from unwanted access. The report also emphasizes the need for organizations to respond promptly to security breaches to maintain their reputation.
References
Adat, V. and Gupta, B.B., 2018. Security in Internet of Things: issues, challenges, taxonomy, and architecture. Telecommunication Systems, 67, pp.423-441.
Ademu, I.O., 2013. A Comprehensive Digital Forensic Investigation Model and Guidelines for Establishing Admissible Digital Evidence (Doctoral dissertation, University of East London).
Al-Khateeb, H., Epiphaniou, G. and Daly, H., 2019. Blockchain for modern digital forensics: The chain-of-custody as a distributed ledger. Blockchain and Clinical Trial: Securing Patient Data, pp.149-168.
Amato, F., Cozzolino, G., Moscato, V. and Moscato, F., 2019. Analyse digital forensic evidence through a semantic-based methodology and NLP techniques. Future Generation Computer Systems, 98, pp.297-307.
Arshad, H., Jantan, A.B. and Abiodun, O.I., 2018. Digital forensics: review of issues in scientific validation of digital evidence. Journal of Information Processing Systems, 14(2), pp.346-376.
Carroll, O. L., Brannon, S. K., & Song, T. 2008. Computer forensics: Digital forensic analysis methodology. US Att’ys Bull., 56, 1.
Hart, S.L. and Christensen, C.M., 2002. The great leap: Driving innovation from the base of the pyramid. MIT Sloan management review, 44(1), p.51.
Kao, D.Y., Chao, Y.T., Tsai, F. and Huang, C.Y., 2018, November. Digital evidence analytics applied in cybercrime investigations. In 2018 IEEE Conference on Application, Information and Network Security (AINS) (pp. 111-116). IEEE.
Karie, N.M., Kebande, V.R. and Venter, H.S., 2019. Diverging deep learning cognitive computing techniques into cyber forensics. Forensic Science International: Synergy, 1, pp.61-67.
Lutui, R., 2016. A multidisciplinary digital forensic investigation process model. Business Horizons, 59(6), pp.593-604.
Mabuto, E.K., 2013. Finding digital forensic evidence when graphic design applications are used for document counterfeiting (Doctoral dissertation, University of Pretoria).
Markus, M.L., 2004. Technochange management: using IT to drive organizational change. Journal of Information Technology, 19(1), pp.4-20.
McLeod, A. and Dolezel, D., 2018. Cyber-analytics: Modeling factors associated with healthcare data breaches. Decision Support Systems, 108, pp.57-68.
Talesh, S.A., 2018. Data breach, privacy, and cyber insurance: How insurance companies act as “compliance managers” for businesses. Law & Social Inquiry, 43(2), pp.417-440.
Tri, M. K., Riadi, I., & Prayudi, Y. 2018. Forensics acquisition and analysis method of imo messenger. International Journal of Computer Applications, 179(47), 9-14.
Vincze, E. A. 2016. Challenges in digital forensics. Police Practice and Research, 17(2), 183-194.
Yusoff, Y., Ismail, R. and Hassan, Z., 2011. Common phases of computer forensics investigation models. International Journal of Computer Science & Information Technology, 3(3), pp.17-31.
 write
write