Introduction
Today, technology permeates every element of people’s everyday lives all around the globe. While companies are using the power of technology to expand and enhance their operations, people too require technology to fulfill customized duties. Despite the efficiency and better future that technology offers, Markus (2004, p. 5) believes that underlying issues may impair regular operations. Computer-related crimes including identity theft, illegal access, malware, and intellectual property theft are examples of such difficulties.
Digital forensics are commonly used to address these issues. Digital forensics is the art of gathering, preserving, recognizing, recording, and evaluating digital evidence, according to Hart and Christensen (2002, p. 51). In light of the Ghita Financial Services situation, the paper will explain and comprehend the many types of computer crimes to which IT systems may be subject, as well as the ensuing economic effects, including societal repercussions. The paper will also provide light on the key ideas behind digital forensic analyses of IT systems. Finally, the report will include suggestions for the best course of action to take in order to address suspected misuse.
Methodology
To enable the analysis to obtain reliable forensic evidence, Palmer’s investigative model from the 2001 Digital Forensic Research Conference (DFRWS) will be employed in this instance. The success of the concept is influenced by seven key phases, which are shown below.
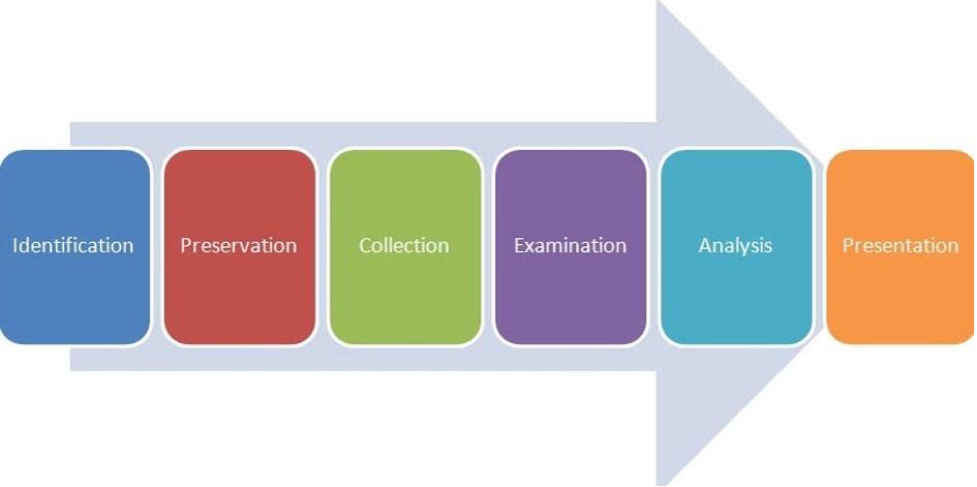
Figure 1: Illustration: Digital Forensic Research Conference (DFRWS) investigative model: adopted by Yusoff et al. (2011)
Identification
Preparation
It will be crucial at this stage to decide if law enforcement is required and whether it should pursue the case all the way, or whether Mr. Vladimir, the CEO, just wants the analyst to provide a report at the conclusion of the inquiry. Choosing whether to get written approval for the digital forensic inquiry or if a separate incident response mechanism is in place will be crucial at this point. It is crucial to ensure that the necessary steps are taken throughout the inquiry since illegal data management might result in legal ramifications. At this point, it is also crucial to guarantee the security and privacy of the consumer data. The consultant will also try to ascertain how the investigation has affected Ghita’s operations, including how long the network was down, how much money was lost, how long it took to restore, and how much sensitive data was lost.
It will also be crucial for you to gather information on the servers, routers, hubs, switches, computers, network topology documents, firewalls, and other network equipment as an independent digital forensic consultant. recognizing external storage devices such memory cards, flash drives, external hard drives, remote PCs, and DVDs/CDs. The preparation in the acquisition stage also includes imaging the hard drives of the target devices and hashing them using the required tools.
Preservation
In this inquiry method, the preservation step is crucial. The investigation’s preservation phase is very important since it will be utilized to provide the foundation for delivering data integrity. Data deletion, modification, and alteration operations have a significant likelihood of obstructing the openness of the whole inquiry process. Securing all media and backing them up are two crucial steps that will be taken in this situation to ensure data integrity. The right tools, which will be covered in depth in the sections that follow, will also be used to support the network. Our strategy is based on the research by Arshad et al. (2018, p. 346), which mandates that digital forensics be recorded in accordance with the necessary criteria so that they may be used as evidence when necessary.
Collection/Acquisition
The primary objective of the data collection or acquisition phase is to assist the consultant in gathering, labeling, and acquiring data from the questionable devices while ensuring data integrity. In our situation, the consultant is aware that the investigation scene might provide two important data kinds. Volatile and non-volatile data fall within this category. Data that is accessible while the system is turned on but unavailable when it is turned off is referred to as volatile data. Caches, the registry, and Random Access Memory (RAM) all include this data. Consistent data are referred to as the volatile data. This is the information that is present whether or not the computer is turned on. Documents on the hard drive or any other storage device connected to the computer are examples of this data. The consultant must utilize the optimum method to extract volatile data due to its limited shelf life. The consultant will choose whether to collect the data locally for Ghita or remotely.
Volatile data
The consultant suggests that the suspect computer or the forensic workstation must be in the same LAN when dealing with volatile data. The ‘cryptcat’ program in this instance is capable of listening to the Windows NT port server. The practical use of this strategy is setting up a trusted toolset on the organization’s Windows NT server’s optical drive and using the trusted console cmd.exe to issue the command below.
cryptcat <ip address> 6543 -k key
Capturing data on the suspect machine workstation will require us to deploy the command shown below
cryptcat -l -p 6543 -k key >> <file name>
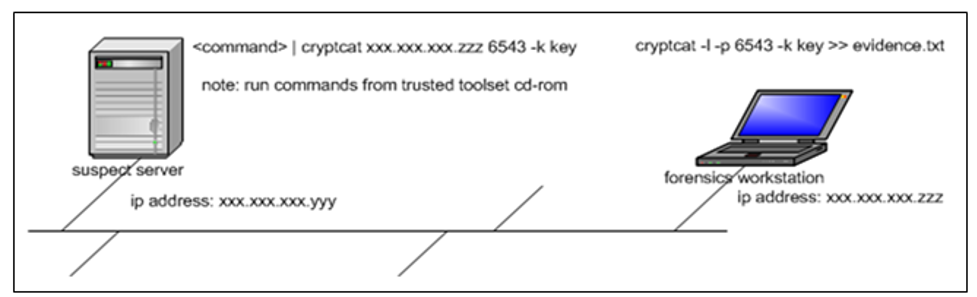
Figure 2; Illustration of the intended volatile data collection configuration
The table below shows the GUI interface tools and their associated usage and outcome that can be deployed in the suspect machine workstation.
| Tools | Usage | Outcome |
| Process explorer | It will provide information about running processes, loaded libraries, utilized resources, etc. | Logged on users, running processes |
| Rootkit Revealer | It will prove critical in detecting kernel mode rootkits and user mode | System date and time, stored in the memory |
| Tcpview | It will be used to display network connections and the associated applications. | Open ports, network connections |
Table 1: volatile data forensic tools, their application, and intended outcomes: adopted from Kao et al. (2018, p. 112)
The consultancy also intends to apply certain Windows-oriented tools to capture volatile data, as shown below.
- HBGray’s F-response- will be helpful for the remote acquisition of physical memory.
- HBGray’s FastDump- useful for the acquisition of physical memory in the local settings
- Ipconfig- will be used to acquire details on the suspect device
- Doskey/history- helpful in collecting command history
- Netusers and qusers- essential for determining logged-in users
- Netfile- essential for identifying services and drivers
The collection of clipboard content to cover all areas of volatile data will also be used to exhaust this section effectively. There is significant evidence when the suspect machine is in a volatile state, so the consultancy advises that the suspect machine should not be shut down to reach this goal.
Non-volatile data
The next step will be to obtain non-volatile data after gathering volatile data. The first step taken by the consultant will be to transfer all of the data onto the target or suspicious computer. The term “forensic imaging” is another name for this procedure. Because it will be utilized to maintain data integrity, imaging is quite important in this situation. This will be done successfully using the FTK tool. Ghita’s lawsuit will also include the use of hard disk cloning. The system as a whole will be duplicated using it. The main distinction between forensic imaging and hard disk cloning is that forensic imaging can only be completed with the required equipment, but hard disk cloning can be completed with nothing more than a mounted drive. To lock all vacant blocks, forensic imaging, which includes information like hashes and metadata, is essential.
Data gathering is possible during both online and offline tests. Forensic imaging requires offline forensics. In our situation, we may turn to Wireshark or Ethereal tools for online forensic investigation to see live network traffic. Domain controller logs, firewall logs, antivirus logs, and firewall logs will all be collected under non-volatile data collection. The consultant will also get the suspicious machine’s Web server logs, Windows event logs, database logs, IDS logs, and application logs. It will be crucial to enter all digital evidence into the chain of custody log as soon as the team obtains it. The chain of custody log documentation will be created from the beginning of the inquiry until this report is presented with the intention of protecting the integrity of the evidence, as instructed by Amato et al. (2019, p. 298).
It will be important to image the disk piece by piece, access the full volume, and reproduce the original media and the deleted data before the team moves further with the inquiry. The consultant will hash everything after imaging the disk in order to maintain data integrity during the examination. We must ensure that no team member modifies the data between the time of data collection and the conclusion of the digital forensic inquiry since the hash values will be recorded on many different sites. The majority of the tools that will be used in this situation will have read-only access to the media. Ghita’s servers, hard disks, and external storage will all be the target.
Conclusion
Some of the intricate underpinnings of digital forensics have been made apparent by the Ghita case. The extensive and involved inquiry clarified the timing and importance of the organizational breach. The investigation has brought to light the need of having a strong security system in place to protect sensitive customer data from unwanted access. In order to maintain their reputation, businesses must react promptly to security breaches, according to the report.
References
Amato, F., Cozzolino, G., Moscato, V. and Moscato, F., 2019. Analyse digital forensic evidence through a semantic-based methodology and NLP techniques. Future Generation Computer Systems, 98, pp.297-307.
Arshad, H., Jantan, A.B. and Abiodun, O.I., 2018. Digital forensics: review of issues in scientific validation of digital evidence. Journal of Information Processing Systems, 14(2), pp.346-376.
Carroll, O. L., Brannon, S. K., & Song, T. 2008. Computer forensics: Digital forensic analysis methodology. US Att’ys Bull., 56, 1.
Hart, S.L. and Christensen, C.M., 2002. The great leap: Driving Innovation from the base of the pyramid. MIT Sloan management review, 44(1), p.51.
Kao, D.Y., Chao, Y.T., Tsai, F. and Huang, C.Y., 2018, November. Digital evidence analytics applied in cybercrime investigations. In 2018 IEEE Conference on Application, Information and Network Security (AINS) (pp. 111-116). IEEE.
Karie, N.M., Kebande, V.R. and Venter, H.S., 2019. Diverging deep learning cognitive computing techniques into cyber forensics. Forensic Science International: Synergy, 1, pp.61-67.
Markus, M.L., 2004. Technochange management: using IT to drive organizational change. Journal of Information Technology, 19(1), pp.4-20.
Tri, M. K., Riadi, I., & Prayudi, Y. 2018. Forensics acquisition and analysis method of imo messenger. International Journal of Computer Applications, 179(47), 9-14.
Vincze, E. A. 2016. Challenges in digital forensics. Police Practice and Research, 17(2), 183-194.
Yusoff, Y., Ismail, R. and Hassan, Z., 2011. Common phases of computer forensics investigation models. International Journal of Computer Science & Information Technology, 3(3), pp.17-31.
 write
write