Executive Summary
Threat modeling is an important fete in the cybersecurity profession. It helps in identifying potential threats by anticipating security attacks in a given system or system by allowing analysts to visualize the system from an attacker’s perspective. Therefore, the analysts can identify potential entry points that adversaries can use in attacking a system. Data flow approaches provide a suitable way to model threats by showing data flow into, within, and out of a given system. The recent attack on the Queensland University of Technology’s information system highlights the impact of cyber security incidents on organizations. This report delves deep into modeling the threats in the QUT information systems by first developing a context diagram and a level zero Data Flow Diagram (DFD) of the institution. The DFD is then used to discover the threats and vulnerabilities in the institution’s information systems. Lastly, the report categorises the discovered threats and vulnerabilities based on the STRIDE methodology.
Introduction
According to Sion et al. (2020), secure systems are those whose assumptions can be made explicit and can be examined in systematic processes. Threat modeling is one of these processes, and it helps security analysts to reason about the security of a given system and identify threats. Through threat modeling, a system is looked at from the adversary’s perspective for the anticipation of security attacks, and the modeling dwells on the premise that adversaries cannot attack a given system without having the capability to supply it with data or interact with it. Modeling helps document the entry points in the system as the starting point for identifying the system’s vulnerabilities. Such data flow approaches as Data Flow Diagrams (DFDs) help track the adversary’s entry points and identify the assets that can be compromised (Sion et al., 2018). Threat modeling is particularly done after a system has been attacked or in a risk assessment of a given system. Queensland University of Technology (QUT) is a good example of an organization whose information systems have been attacked and the integrity of their data has been compromised. In assessing the severity of this attack, it is necessary to have a threat analysis or model of this organization. This report provides a threat analysis of the QUT information systems. It covers system analysis using context diagrams and DFDs, a discovery of the potential threats, and outputs a list of threats following the STRIDE methodology.
Data Flow Diagrams
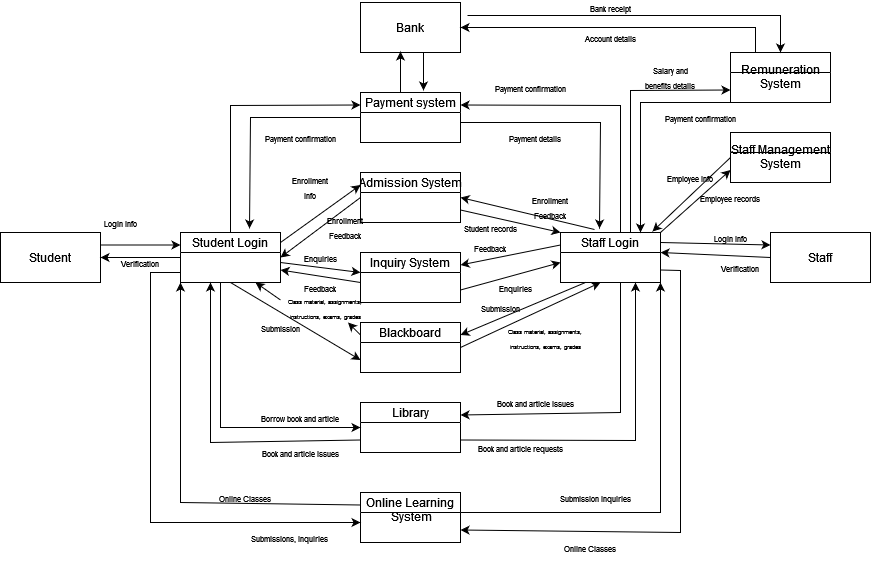
Figure 1: Context Diagram of the QUTA Information Systems
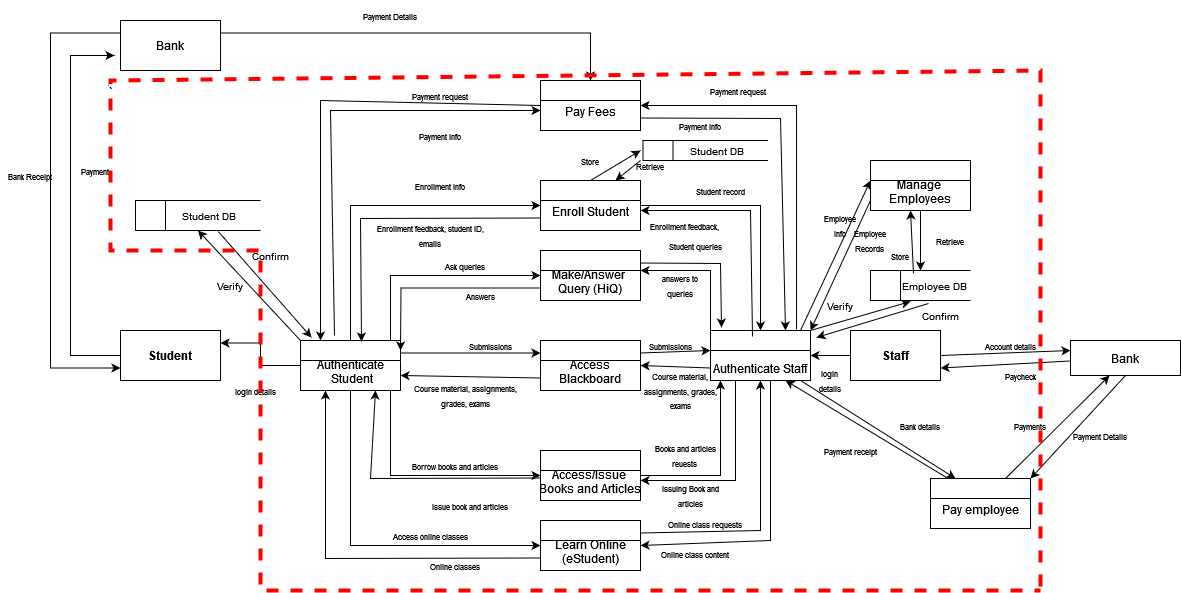
Figure 2: Data Flow Diagram (DFD) Showing Flow of Data in QUTA Information Systems
As an organization, QUTA leverages the power of information technology in conducting various tasks, as demonstrated in Figures 1 and 2 above. However, these technologies can be targeted, as evidenced by the QUT case, to compromise the integrity, confidentiality, and availability of the various business-related asses and data demonstrated in the two diagrams. The context diagram in Figure 1 shows the high-level overlay of QUTA’s information systems, while the DFD in Figure 2 delves deep into the information system. It shows the data flow in the information systems, with the students, staff, and the bank being the main actors. From it, the areas where adversaries can use as the weak points can be well understood. Also, it indicates the threat boundary, shown by the dotted red line, which shows the trusted actors, processes, and elements in the QUTA information systems and differentiates them from those that cannot be trusted. In the case of QUTA, the actors, elements, and processes that cannot be trusted are enclosed inside the red dotted line, while trustable actors and processes that can be trusted are outside the boundary. As indicated in the DFD, the students and the bank can be trusted in QUTA’s information system. These two actors have little control over the different processes and data, unlike the staff, who can easily access data from all the data stores and have control of the processes.
Threat Discovery
As indicated, the threat boundary indicates the areas in QUTA information systems that are most likely to be the entry point for adversaries while trying to instigate cybersecurity incidents in the systems. Therefore, it shows areas of vulnerability and threats to the system. After the cyber incident that took place in QUTA, where ransomware rendered some of the systems unavailable, and there was data theft, a deep analysis of the system was conducted for the identification of the vulnerabilities and threats on QUTA systems. Given that the staff were identified as the main actors, mainly the IT staff and system administrators, directly involved with the systems, an interview was conducted, and they were asked the following questions.
- At what point did the data breach take place?
- How was the data breach identified?
- Who discovered the breach?
- What information systems were affected?
- What information has been stolen or compromised?
From the interviews, the staff indicated that they became aware of a ransomware attack on December 22, 2022, when the printers within the QUTA began to print ransom notes until they ran out of printing papers. The ransom indicated that critical data in data stores had been copied and encrypted, and it could be published online unless a modest royalty was paid. The immediate action was to shut down all the IT systems, and the staff noted that the notes were the only means they used to identify the breach. However, a deep analysis of the system was done, and it was identified that the personal information of some students and staff was stolen from an internal storage drive. This information was from current and former staff and students, and it included such information as bank details, home addresses, and other information. The breach affected selected systems, including Blackboard, ‘eStudent’ (an e-learning platform), Digital Workspace, and HiQ Website. Also, the attack affected network drive folders, including the ‘U Drive,’ the university’s entire printing network, and access to information systems via VPN using Cisco AnyConnect was disabled. From these interviews, a number of potential threats and vulnerabilities in QUTA information systems can be identified, as shown in Table 1 below. The table also indicates what needs to be done for each of these vulnerabilities or threats.
Table 1: Identified/Discovered Threats and Vulnerabilities in QUTA Information Systems
| ID | Threat/Vulnerability | Mitigation Measures |
| 1. | Ransomware attack | Have an updated antivirus installed into its systems, have a backup of all data, install network defense systems, have email protection, and institute heightened control over the systems. |
| 2. | VPN insecurities | Limit access to its systems via VPN, prevent DNS, IPv6, and WebRTC leaks, have a kill switch and a network lock, and secure its remote access networks. |
| 3. | Wi-Fi protocol insecurities | Have heightened firewall and intrusion detection systems across its Wi-Fi networks. |
| 4. | Phishing attack | Train its staff on identifying suspicious emails and links. |
| 5. | Insider attacks | Have strong access control, multifactor authentication, and data protection measures. |
| 6. | DoS | Institute network segmentation, IP blocking, traffic rate limiting, and balancing network traffic loads |
| 7. | USB attack | Install updated antivirus and have a strong policy on the use of USB devices in the workplace. |
| 8. | Cross-site scripting (XSS) | Validating input data |
| 9. | SQL injection | Validating input data |
| 10. | Employee awareness | Educate employees on cybersecurity. |
Among the identified threats and vulnerabilities, the following appear to be the most serious, and that need immediate attention.
- Ransomware attack: By definition, a ransomware attack is a malware attack where an attacker locks and encrypts his or her victim’s data and then demands a ransom for the data to be unlocked or decrypted (Brewer, 2016). This is the exact thing that raised the cyber security incident at QUT, and the attacker could have taken advantage of a person, system, network, or software vulnerability to infect the university’s computers and printers with malware. This type of attack works by infecting computers, devices, or networks using a link or installing a file, application, or program that carries malicious code that is designed to covertly download and install ransomware (Brewer, 2016). It can happen through phishing emails, email attachments, social media, malvertising, or self-propagation using networks or USB drives. In preventing this type of attack, such organizations as QUTA need to put such measures as having updated antivirus installed on computers and having a secure backup of all data. Also, they need to install network defense systems, including firewalls and intrusion detection systems, have email protection, and institute heightened control over their systems’ security.
- Phishing attack: Phishing attack is a common threat, especially in educational institutions, and they involve the attacker sending fraudulent emails, texts, calls, or websites that trick the victims into downloading malware, sharing sensitive data, or carrying out other actions that expose them (Alkhalil et al., 2021). QUTA is at a high risk of phishing attacks due to the high number of individuals interacting with its systems and the sensitive data in the systems. This type of attack often leads to ransomware attacks and data breaches in corporations. The attack can be prevented by training staff and students on how to identify phishing emails, calls, and messages, installing antiviruses on computers, installing spam filters, and multifactor authentication of system users.
- Wi-Fi protocol insecurity: At QUTA, there is a high risk of the Wi-Fi being used as an entry point by malicious actors. This was evidenced by the attack on printers, which mainly work through a Wi-Fi connection. Attacks on Wi-Fi protocols include DoS, spoofing, or hijacking sessions where attackers can gain access to secure data and communication. The vulnerability can be addressed by having advanced firewall security and intrusion detection measures across all Wi-Fi networks.
STRIDE Categorization
Table 2: STRIDE categorization of the discovered threats and vulnerabilities
| ID | Threat/Vulnerability | Threat Category |
| 1. | Ransomware attack | Tampering |
| 2. | VPN insecurities | Tampering |
| 3. | Wi-Fi protocol insecurities | Tampering |
| 4. | Phishing attack | Spoofing |
| 5. | Insider attacks | Information disclosure |
| 6. | DoS | Denial of services |
| 7. | USB attack | Tampering |
| 8. | Cross-site scripting (XSS) | Tampering |
| 9. | SQL injection | Tampering |
| 10. | Employee awareness |
Conclusion
Threat modeling is important for the identification of threats and vulnerabilities in a given system. This report documents threat modeling in QUTA by first presenting a detailed context diagram and level zero DFD on the processes, actors, and elements in QUTA’s information systems. These diagrams are then used to discover threats and vulnerabilities in the systems, as documented in Table 1. Also, in Table 1, the report highlights the mitigation measures that can be put in place to prevent threats and vulnerabilities. Lastly, the report categorizes the discovered threats and vulnerabilities based on the STRIDE categorization method, as documented in Table 2.
References
Sion, L., Yskout, K., Van Landuyt, D., van Den Berghe, A., & Joosen, W. (2020, June). Security threat modeling: Are data flow diagrams enough? In Proceedings of the IEEE/ACM 42nd International Conference on Software Engineering Workshops (pp. 254-257).
Sion, L., Yskout, K., Van Landuyt, D., & Joosen, W. (2018, April). Solution-aware data flow diagrams for security threat modeling, in Proceedings of the 33rd Annual ACM Symposium on Applied Computing (pp. 1425-1432).
Alkhalil, Z., Hewage, C., Nawaf, L., & Khan, I. (2021). Phishing attacks: A recent comprehensive study and a new anatomy. Frontiers in Computer Science, 3, 563060.
Brewer, R. (2016). Ransomware attacks: detection, prevention and cure. Network Security, 2016(9), 5–9.
 write
write