Ecommerce infrastructure comprises several components that must frequently work together to address severe ecommerce issues. Ecommerce firms, more than any other type of retail business, rely primarily on technology infrastructure. The first and most crucial consideration is an ecommerce platform, since the complete website will be built, serving as a digital shop for consumers. Another critical issue is the sales and marketing parts of an ecommerce enterprise. A firm won’t attract enough clients to the internet business without good promotion. That implies that the firm won’t produce enough sales to turn a profit; this necessitates a significant increase in the sales and marketing infrastructure (Akhmetova. 1).
Major Hardware and Software Components of the Company’s Information Systems Infrastructure.
There are powerful software and hardware pieces that make the infrastructure of every information system of a company’s ecommerce site functioning. It’s worth noting that the software and hardware components of an ecommerce system are essentially identical to those of ecommerce websites. These standards are significant for both large and small organizations since they provide excellent support for virtual transactions and sales conducted through the company’s ecommerce site. In addition, the ecommerce development firm generates revenue for a shopping site. Ecommerce online provides services and items without requiring the actual body to move; as a result, any misplaced criteria might directly influence the firm.
Hardware Components
Network Hub
A network hub is a device that allows numerous computers on a network to connect. The PCs are connected to the network hub through ethernet connections. Hubs typically include four to twelve ethernet connections. These devices best serve small local area networks. According to the OSI reference model, network hubs are Layer 1 devices; they only work at the physical layer rather than as a software program (Aftab, 2).
Routers
Routers are used to connect networks, whereas hubs and switches are used to design networks. For example, if a person working in the brand’s customer care unit has to communicate with the project management unit, the data would be transferred to a switch in the individual’s network, leading to a router. As a result, the router functions as a traffic conductor, forwarding the data packet to the switch for the second network, then routing it to the specific IP address with which one seeks to communicate.
Software Packages
Whether a corporation wants to buy or lease its ecommerce applications, there are two basic software categories to choose from: merchant server software such as EC suites and available packages such as electronic catalogs. A firm can track and manage product inventory and fulfill and send orders with e-commerce software. It allows a company to keep track of sales, market to consumers, give discounts, run a loyalty program, and even start a blog to engage with future customers.
Operative Software Packages
Many companies sell standard functioning software packages, ideal for creating storefronts. Inventory, merchandising, payment preferences, hosting, tax, sales analysis, systems and databases, site layout and design, customer service, shopping, and security are the software packages investigated for specific sites. It should be emphasized that each considers a wide range of parameters. E-catalogs are the virtual equivalent of traditional product catalogs, and the corporation also wants to use them. An e-catalog, like a paper catalog, includes textual descriptions and product photographs, and delivery options. Furthermore, e-catalogs are included in a merchant software package that provides capabilities that make development economical and straightforward (Relas, 3).
There will be merchant server software, including wizards or templates for designing a shop and catalog sites. They, too, are made up of e-shopping carts that assist clients in combining things of interest until they are ready to check out. They also contain web-based order forms that, in many cases, use SSL encryption to ensure a secure transaction. They also include a database for product descriptions, client orders, and price information. They integrate third-party software for tax payments, shipping invoices, and fulfillment and distribution management.
EC Suite
The EC suite is still a merchant server software comprising many EC components and tools to construct EC applications. Users and developers benefit from EC suites because they provide more flexibility, customization, specialization, and integration in aiding back- and front-office functions. Instead of relying on a single database and server, as with less polished merchant server systems, the functionality of specific EC suites is dispersed among several servers and databases.
Hardware Components for the Website Information System Infrastructure
Simple technical ecommerce needs for a website that help with ecommerce operations are sometimes referred to as hardware components. As a result, the website’s size, traffic, and purpose will decide how much server hardware is used. HTML, JavaScript, media files, and PHP make up an ecommerce website, and their storage is frequently located on the webserver. Typically, these inquiries involve what CPU will be used and how much RAM will be used for each task. A question about the disk read, and the writer levels will also be asked. According to the website’s owners, what is the expected number of visits? Again, the rate of increase or percentage must be considered.
Software Components for Ecommerce Company Website Information System Infrastructure
A domain, integrated payment provider, hosting provider, platform, and fronting funds to buy merchandise and packing for delivering the products are all required to start an ecommerce website. Surprisingly, the importance of a content management system (CMS) at this point cannot be overstated. A content management system (CMS) is always needed to generate and maintain digital information. Web and business content management systems are included in this digital content.
Sites like Shopify, WooCommerce, OpenCart, and Magento are examples of content management systems that have worked effectively for ecommerce. Again, there’s what’s known as an API — an API is a simple and seamless way to share data between different programs; this is to say that an API specifies how software components must communicate. Amazon API, WooCommerce API, Magento API, and eBay API are just a handful of the most well-known APIs (Qi, 4).
The importance of database design cannot be overstated. Indeed, interactive databases are more suited for ecommerce transactions than document-based databases. Database middleware, application server middleware, web middleware, transaction processing middleware, web middleware, and message-based middleware are among the middleware from which this ongoing ecommerce development will be designed.
As previously stated, the company’s ecommerce website will be subjected to web analytics. As it turns out, web analytics has been discovered to help businesses attract more visitors and improve client retention for both services and commodities. Google Analytics, Clicky, Chartbeat, and Woopra are the most excellent tools for analyzing online traffic on the site. Another point to consider is the text analytics component; text analytics is sometimes confused with text data mining, which is approximately equivalent to text analytics. Text analytics is demonstrated to display the drawing of critical textual messages. QDA miner, WordStat, and SimStat are the most satisfactory solutions that have been explored for the site’s text analytics capabilities. In ecommerce, analytics for ecommerce helps to analyze clients’ purchasing habits against the backdrop of market trends.
Potential Security Vulnerabilities and a Security Design
Many criminals follow the money wherever it flows without question; this does not rule out the internet and, in particular, ecommerce. As a result, ecommerce business owners should prioritize the security of their websites. The possible security vulnerabilities that lure the company’s ecommerce website and the security design to nip the nasty trend in the bud will be examined in this section. Online security is critical to online trading since cybersecurity flaws can result in cash loss, data loss, and the loss of a company’s complete operation. It’s not only about securing corporation data in e-commerce; it’s also about protecting customer data. Client personal information may be lost due to breaches of internet security systems. (Paintal, 5).
Security Vulnerabilities
Financial Scams
Hackers conduct unsanctioned trades and cover their tracks, causing firms to lose money. Once again, fraudsters file false returns or refunds to steal money from the firm. While e-commerce is straightforward, people are becoming more aware of the dangers posed by online fraudsters. Merchants who manage online shopping websites must take precautions to ensure that their sites are safe from internet hackers and fraud.
Spamming
Emails are an excellent tool for promoting sales, but they are also one of the most common ways for spam to spread. Including viral links incorporating blog comments or contact forms, on the other hand, is an open invitation for internet spammers to do damage to the firm. They usually send the messages into the inboxes and then respond. Spam also jeopardizes the web site’s security and slows it down.
Phishing
Criminals that pose as genuine firms and send emails to clients to deceive them into providing critical information are one of the most prevalent dangers to ecommerce security. Phishing schemes include sending emails to clients or organizations with bogus statements such as “you should do this action.” This strategy only works if the company’s clients keep working and provide the intruder access to their login information or other personal information that they may exploit.
Brute Force Attacks
By referring to an online store management panel. It cracks the password using all possible combinations utilizing apps that link to its website.
Bots
Bots, such as those that search the internet and help you rank your website in search engine results pages, may be recognizable to you from your favorite books. On the other hand, Dedicated bots search websites for pricing and information on new products. Criminals utilize this information to limit sales and income by changing the cost of your online company or obtaining the best-selling products in shopping carts.
DDoS Attacks
DDoS attacks clog up internet services with traffic from various sources, rendering them unreachable. The attack targeted various essential services, ranging from banks to e-commerce sites, making it impossible to obtain vital information. While the DDoS assault isn’t a massive catastrophe, it can be disastrous for the company’s mainline. They can potentially impact network performance, resulting in a poor end-user experience. Worse, such attacks are occasionally utilized as a preventative tactic.
SQL Injections
Hackers employ SQL injection to obtain unauthorized access to one of a company’s most important assets: a website that enables its website. In most circumstances, website failures allow the attacker to enter instructions into the program while processing the data. SQL injection attacks have the potential to be extremely harmful since they will enable an attacker to bypass website authentication measures and steal personal information about workers, customers, assets, partners, suppliers, and other crucial data. If the attacker cannot extend the typical user’s permissions to the controller, he may launch more attacks or put the entire system at risk.
Trojan Horses
A trojan horse in business is an advertising offer made by a company designed to attract potential customers by offering them cash or something of value in exchange for acceptance. Still, after approval, the buyer is forced to spend a much more significant amount of money, either by being signed into a lengthy contract with a problematic exit or by having money drawn in some other method. The consumer may be subjected to adverse repercussions such as overspending, enormous amounts of debt, or identity theft. Trojan Horses may have been installed on systems by customers and administrators. It is one of the most dangerous networks security dangers since attackers may utilize these apps to steal confidential information from their computers quickly.
Security Design
Active Protection
This danger necessitates highly effective network security measures, such as the DoS security service, because e-commerce enterprises are continually under assault and can be attacked at any time, regardless of their significant security precautions. The concept is straightforward: all incoming traffic is analyzed and monitored, and requests for fake targeted visits are forbidden. DDoS assaults will not be able to set up the site or negatively influence its performance because of this security.
Switch to HTTPS
A corporation that employs HTTP protocols may be vulnerable to security risks. They were moving to HTTPS, which displays a green indicator with the phrase “secure” next to the URL in the client computer. The data submitted by users, as well as their mobile users, is protected by HTTPS protocols. Because HTTP protocols are no longer extremely safe, many current browsers display a warning that the site does not appear secure, and the user should not proceed. Some browsers will restrict the user from visiting the webpage if this is not done. If a firm employs HTTPS, Google will give it a better ranking.
Secure the Servers and Admin Panels
Most e-commerce platforms have ridiculous default passwords. The organization is at risk of being looted if the network administrator does not change. Strong passwords and usernames should be used by the firm, which should be updated regularly. If an anonymous IP attempts to sign in, network administrators may forward you and notify the panel. These specific activities have the potential to improve the firm’s safety significantly.
Antivirus and Anti-Malware Software
Hackers can use stolen credit card information to place orders from anywhere in the world. An antivirus or anti-fraud tool might help deal with this severe ecommerce problem. They utilize sophisticated algorithms to detect fraudulent transactions and prompt consumers to take relevant action. They assign a fraud risk score to aid business owners in determining whether or not marketing is genuine.
Using Firewalls
Another excellent piece of ecommerce advice is to utilize low-cost yet powerful firewall software and plugins. They protect your site from hostile networks and regulate traffic entering and leaving it. Because it possesses selective permeability, only trustworthy traffic is permitted.
Secure the Website with SSL Certificates
Certificates for the Secure Sockets Layer (SSL) are files that associate a key with transactions across several network channels. These certificates are connected to credit card information and transactions to react to typical questions. SSL certificates encrypt data in transit to prevent third parties from intercepting it. The user’s data is encrypted before it is sent to the server. SSL certificates are required if you wish to conduct any business on an ecommerce site. They ensure that all of your transactions are secure. It also provides the firm with a certificate of ownership, ensuring that it cannot be used as a phishing site.
Backup Data
Data loss is not uncommon as a result of hardware failure or cyber-attacks. And if a company does not back up its data regularly, it risks losing it permanently. Even if someone forgets to do it manually, the business should automatically use an automated backup solution to back up all data. The responsible parties might go one step further and replicate the backup to ensure a backup plan in case the original backup is lost. Cloudways, a managed ecommerce web hosting service that generates backups automatically, is another option.
Educate Clients
Some security breaches are caused by the client rather than the company. They might be using weak passwords or sending sensitive information to phishing sites, where hackers could steal it. Customers may assist businesses in addressing these ecommerce security challenges by becoming more educated. Employees may be required to use strong passwords, and the company’s regulations may explain how phishing works. Strong passwords contain a complicated combination of characters, symbols, and numbers, virtually impossible to guess or brute-force. The two-factor authentication approach can be used if the company’s passwords are weak; alternatively, if the user’s information is sensitive and exposed to hackers.
Use Multi-Layer Security
A variety of security techniques may be employed to improve an ecommerce company’s security. I’ll employ the more widely used Content Delivery Network, or CDN, to defend the site from DDoS assaults and malicious traffic. Machine learning is used to discriminate between destructive and non-violent speech. I can also use two-factor authentication to provide an extra layer of security. Two-factor authentication necessitates the use of a standard login and password, as well as an additional code sent to the user’s phone number through email or SMS.
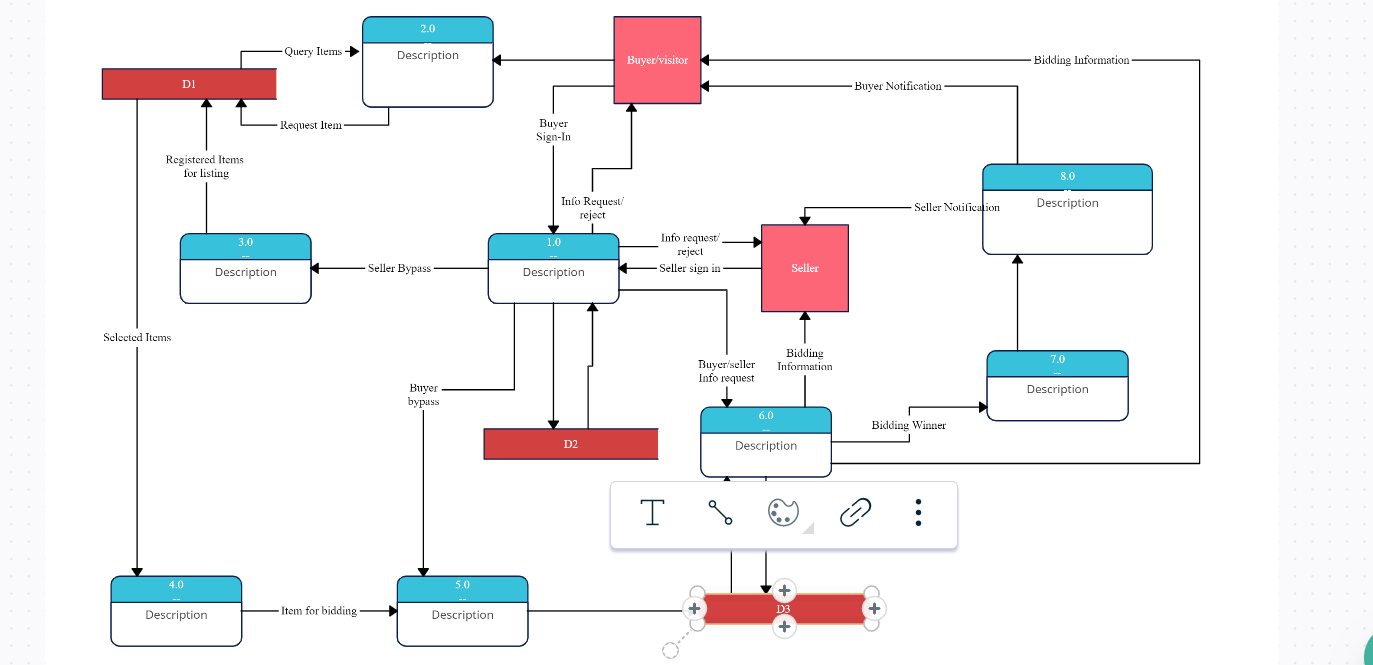
Data Flow Diagram
Sources
- Zaures Akhmetova, Z., Baimukhanbetova, E., Belgozhakyzy, M., Alikbaeva, A., & Tulebaeva, N. (2020). The development of e-commerce infrastructure in current conditions. In E3S Web of Conferences(Vol. 159, p. 04028). EDP Sciences. https://www.e3s-conferences.org/articles/e3sconf/abs/2020/19/e3sconf_btses2020_04028/e3sconf_btses2020_04028.html
- Omer Aftab, M. O., Ahmad, U., Khalid, S., Saud, A., Hassan, A., & Farooq, M. S. (2021, November). Sentiment Analysis of Customer for Ecommerce by Applying AI. In 2021 International Conference on Innovative Computing (ICIC)(pp. 1-7). IEEE. https://ieeexplore.ieee.org/abstract/document/9693026
- Kristina Relas, K. (2019). Redefining Consultation Packages for the Ecommerce Service Offering: In a Digital Marketing Software as a Service Company. https://www.theseus.fi/handle/10024/172780
- Qing Qi, Q., & Cao, J. (2020, October). Investigating the Evolution of Web API Cooperative Communities in the Mashup Ecosystem. In 2020 IEEE International Conference on Web Services (ICWS)(pp. 413-417). IEEE. https://ieeexplore.ieee.org/abstract/document/9284108
- Simran Paintal, S. (2021). ECOMMERCE AND ONLINE SECURITY. International Journal of Management (IJM), 12(1). https://d1wqtxts1xzle7.cloudfront.net/66098771/IJM_12_01_058-with-cover-page-v2.pdf?Expires=1644681569&Signature=UPzo~NRrvnxUfdMIRr~mOX9JiP1~lngZ7X1DKha0RsR09Fo-PYdEb-ETx7h1ODUeQrkABBgZOj-vsQrfBM4x~B1HkUO~kRXPvp8JQFABk3VC4cSUbKVMzkXTmMVcxW4WagjVSzzOw0YvgL7RKDFW9mJoXD6~e0QpOIYibk9TnSGkZCr0sNOHqRyaaVLO21IqD8IAA0qttST-RDFJIEe5sW71HrRRp2t-eBpFIeHzkFLS~ofhPznCTt-APDy14EzvPV~JL0Xbg2H~MNaqj8O95Kg8Q~Xf2ROVTbh7CWgRQ1lImHKYJ0BwVSsftvEL7jHgotnu9kI1vFq6YwLGXXdGog__&Key-Pair-Id=APKAJLOHF5GGSLRBV4ZA
 write
write