Introduction
Establishing a robust network infrastructure is crucial to guarantee smooth operations in today’s business environment. This paper will examine the primary hardware components used in both Local Area Networks (LAN) and Wide Area Networks (WAN) to clarify their distinct functions and goals. It also thoroughly explains the TCP/IP and Ethernet protocols, highlighting their significance within the framework of the OSI model. The report’s final section examines the four key characteristics of dependable networks—Fault Tolerance, Scalability, Quality of Service (QoS), and Security.
Major Hardware Components in LAN and WAN
In the intricate web of Local Area Networks (LANs), sophisticated hardware components collaborate harmoniously to orchestrate seamless communication and efficient data transfer. Positioned as the network’s nerve center, routers function as astute traffic managers, steering data flows with precision among various devices (Chen et al., 2021). Their role is pivotal, ensuring data reaches its intended destination swiftly and without hitches. Switches, another cornerstone of LAN architecture, serve as intelligent bridges, facilitating communication between devices sharing the same network. Their capability to manage data traffic intelligently contributes significantly to the network’s overall efficiency. Access points emerge as instrumental contributors to network flexibility by extending the capabilities of LANs. These devices empower users with wireless connectivity options, allowing for enhanced mobility within the network. Access points not only amplify the range of network accessibility but also play a crucial role in establishing a dynamic and adaptive network environment. The physical medium that underpins LANs’ entire data transmission process predominantly comprises network cables. Among these, Ethernet cables stand out as the quintessential backbone, weaving the intricate tapestry of information exchange within the confined boundaries of a local network.
Contrastingly, the landscape of Wide Area Networks (WANs) demands a more robust and expansive infrastructure to facilitate effective data transfer across vast geographical expanses. In the WAN arena, modems emerge as indomitable enablers, transforming digital data into analog signals suitable for transmission over the intricate web of telephone lines (Chen et al., 2021). These devices serve as the gateway between digital information and the analog world of traditional communication infrastructure. Multiplexers, another indispensable component of WANs, showcase their prowess by seamlessly combining multiple data streams into a unified flow. This process enhances the efficiency of data transmission over extended distances, where the integrity and coherence of information become paramount. As data traverses lengthy expanses, communication satellites emerge as celestial sentinels, bridging the geographical expanse and ensuring uninterrupted and seamless data transfer. Their role is particularly crucial in scenarios where traditional terrestrial communication infrastructure faces limitations.
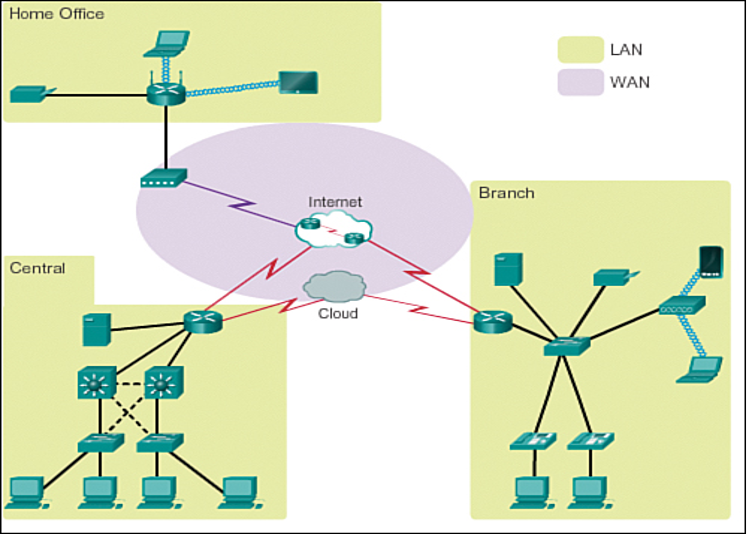
Figure 1: LAN and WAN Hardware Components
Ethernet and TCP/IP Protocols in Networking
Ethernet, controlled by strict IEEE standards, is a key networking component. Ethernet, precisely placed at the Open Systems Interconnection (OSI) design’s Data Link layer, enforces local network data transmission standards (Yu et al., 2019). Ethernet guarantees data interchange reliability and efficiency, offering an excellent basis for device connectivity within a geographically limited region. Ethernet’s broad adoption and adherence to established standards make it essential to contemporary networking.
The Transmission Control Protocol/Internet Protocol (TCP/IP) works with Ethernet to power communication across various networks. This dynamic pair supports end-to-end communication by effortlessly aligning with the OSI model’s Network and Transport layers. The capacity of TCP/IP to break data into packets for transmission and reassemble them at their destination is its core capability (Dwivedi et al., 2023). This guarantees data flow, ensuring smooth communication. The synergy between Ethernet and TCP/IP is beneficial and drives data flow between local networks and Wide Area Networks. Networking protocols form a harmonic union that strengthens LAN communication and crosses WAN geographical distances, symbolizing the synergy needed for contemporary data transport.
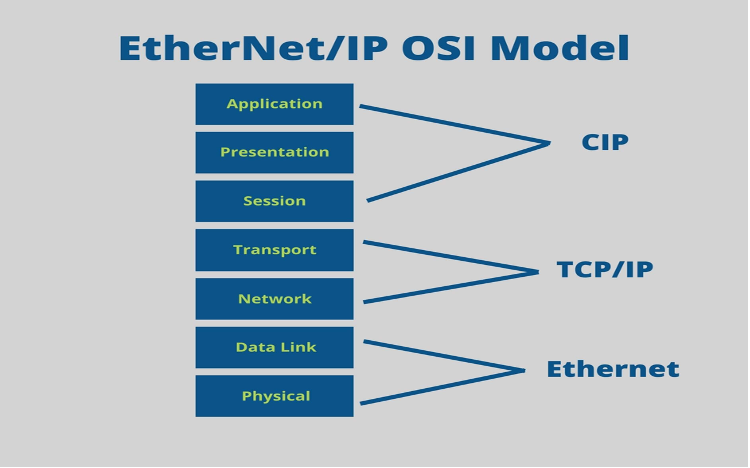
Figure 2: OSI Model and Protocol Interaction
Characteristics of Reliable Networks
Fault Tolerance
Fault tolerance is an essential pillar that guarantees a network’s continuous operation despite unexpected challenges. Networks can smoothly switch to backup systems in the case of hardware or software failures by incorporating redundancy into essential components like servers and routers (Lan, 2023). By reducing downtime and averting any interruptions, this redundancy serves as a safety net, ensuring a steady and continuous user experience. For example, in a fault-tolerant network design, in an instance that a main server fails, the backup server takes over without any noticeable disruption to end users, guaranteeing uninterrupted operations.
Scalability
A critical feature that guarantees a network’s long-term survival in the ever-changing digital environment is scalability. This feature captures how well the network can adapt to the growing demands of more data traffic and user needs without compromising performance. Adding extra servers to the network infrastructure, updating technology to withstand increased demands, or putting complex load-balancing techniques in place are ways to achieve scalability (Adday et al., 2022). Scalability is shown by cloud-based infrastructure, which smoothly allocates more resources to meet demand spikes and maintains optimum performance.
Quality of Service (QoS)
Quality of Service is critical in effective network management, guaranteeing that specific performance requirements are met for diverse data types. Prioritizing traffic is the linchpin of QoS, enabling time-sensitive data like video conferencing to take precedence over less time-critical information (Lan, 2023). QoS mechanisms act as traffic directors, ensuring optimal network performance by allocating resources judiciously. For instance, in a network employing QoS, a video conference will receive higher priority, ensuring minimal latency and a smooth, high-quality communication experience, while background data transfers may experience controlled bandwidth allocation.
Security
Network security is an essential safeguard against illegal access, data breaches, and the constant danger of cyberattacks, particularly in the digital age. A secure network is built on firewalls, strong access restrictions, and encryption (Adday et al., 2022). Maintaining the confidentiality and integrity of sensitive data requires regular security assessments and upgrades to keep up with the always-changing threat environment. Financial institutions provide a practical example of strong network security in operation. Here, the network is protected from possible breaches through encrypted communication channels, strict access rules, and ongoing monitoring, which also protects client data and financial transactions.
Conclusion
The cornerstone for building a strong network design is a thorough grasp of Ethernet and TCP/IP protocols and LAN and WAN hardware components. Further strengthening the groundwork for dependable network deployment is examining critical features like Fault Tolerance, Scalability, Quality of Service, and Security. This extensive understanding guarantees a strategic approach to satisfy the client’s demands and effectively negotiate the complexities of network installation, making it a prospective project lead within the networking department of UC Computing Services.
References
Adday, G. H., Subramaniam, S. K., Zukarnain, Z. A., & Samian, N. (2022). Fault Tolerance Structures in Wireless Sensor Networks (WSNs): Survey, Classification, and Future Directions. Sensors, 22(16), 6041.
Chen, A., Law, J., & Aibin, M. (2021, December). A survey on traffic prediction techniques using artificial intelligence for communication networks. In Telecom (Vol. 2, No. 4, pp. 518-535). MDPI.
Dwivedi, A., Tiwari, P., & Pandey, S. (2023). Transmission Control Protocol/Internet Protocol: Security Issues & Solution. International Journal of Scientific Research in Modern Science and Technology, 2(2), 01-08.
Lan, Z. (2023). A Comprehensive Review of Fault-Tolerant Routing Mechanisms for the Internet of Things. International Journal of Advanced Computer Science and Applications, 14(7).
Yu, W., Wang, Y., & Song, L. (2019). A two-stage intrusion detection system for industrial control networks based on ethernet/IP. Electronics, 8(12), 1545.
 write
write