Introduction
Technology has enabled efficient communication and transfer of data from various points. Still, the main challenge is making this data transfer secure, considering the tens of millions of people who send information over the internet. The vast number of internet users poses a risk as bad actors who want to steal sensitive information might be present. One way of securing information sent over the internet is cryptography. Cryptography is the science of writing information in secret code that the intended recipient can only decipher (Qadir & Varol, 2019). Modern web applications are more complicated as they process the data in rest and transit, requiring extensive security controls to mitigate the threats that might arise. Some cryptographic techniques cannot match the level of advancements and can be cracked within a reasonable time frame. Cryptographic failures lead to compromised systems and are one of the most critical security risks for organizations and business users. This report will discuss the vulnerabilities of the DES cryptographic algorithm and its replacement by more advanced modern algorithms.
The data encryption standard is a cryptographic algorithm with a known vulnerability. This is classified as symmetric encryption because it uses one key for encryption and decryption (Alenezi et al., 2020). Symmetric encryption can be likened to two people who want to send secrets; they have to encrypt the data and agree on one key that will be used for encrypting and decrypting the confidentiality. When used alone, the data encryption standard is used for confidentiality as it encrypts plaintext data into ciphertext, then it can only be decrypted using the same key. The known vulnerability present in this cryptographic function is its limited number of key sizes. It is a sixty-four-bit key with a relatively small combination that can be decrypted easily, even with a personal computer. The data encryption standard was introduced in the early 1970s by IBM and adopted by the United States government as a widely adopted secure communication standard. It implements the Feistel cipher because it uses the sixteen-round Feistel structure. It has a block size of 64 bits, but the effective key length is 56 bits since the remaining 8 bits are used to check for errors in the ciphertext. DES uses initial and final permutations, a part of the Feistel structure (Rasoolzadeh et al., 2016). The first part involves rearranging the order of bits in the plaintext input and divided into blocks of 64 bits each, and then the initial permutation is carried out. This can be explained as a vault lock that has to be turned in a specific point for it to open,
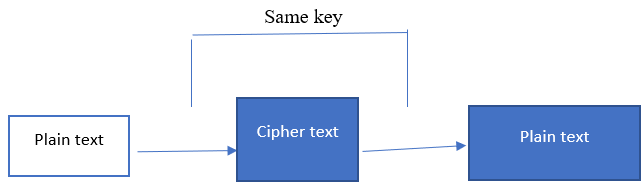
Figure 1 Symmetric encryption
DES Security Issue
DES’s main vulnerability that made it deprecated is its small size of only 56 bits, making it susceptible to brute force attacks. Brute force is a practical way of breaking a cipher by trying every key combination until the right one is found. With the increasing computing power, des becomes easy to crack even using a simple program on a less powerful computer. When DES was introduced, computers had low processing power meaning a brute-force attack would take several years, and the creators knew this. Still, they disregarded it because no computer could crack and decipher it at that time. In 1997, a group of well-known cryptographers sought to perform a brute-force attack on DES, referred to as Cracking the Data encryption standard, and the goal was to decipher a DES-encrypted message.
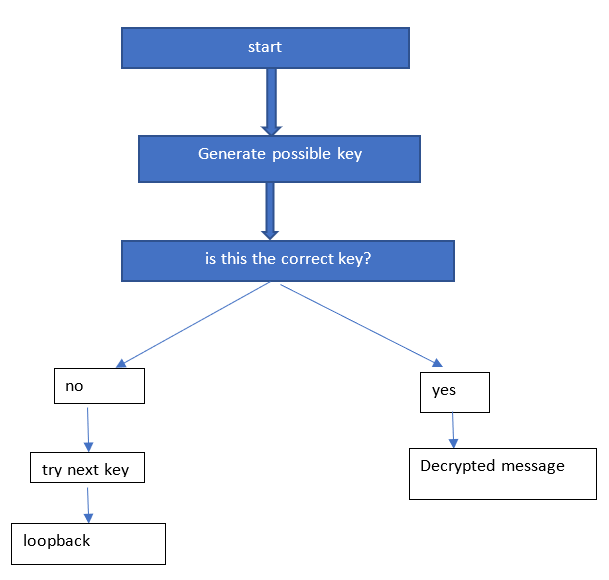
Figure 2. Brute-force attack on DES
DES encryption is like a physical lock with only fifty-six key combinations; when the intruder has the right tools and skills, he can easily break in and access the vault. If the physical key had thousands of combinations, it becomes hard for the attacker to guess as it will take him longer and become impractical. DES also has four out of the 56 keys considered weak keys, which presents a vulnerability to this encryption standard. After the initial parity operations include either all 0s, all 1s, or half of both, these round keys have a similar pattern as the cipher key. Another attack possible on DES is differential cryptanalysis which analyzes the differences in the plaintext and cyphertext (Agate et al., 2020). The resulting differences will then be used to assign probabilities to the possible keys and locate the most probable key. Take, for example, two identical cars on a highway but at different positions that have everything similar except the plates; one could observe the different positions of the cars and deduce differences like the acceleration or speed. DES also potential for a linear cryptanalysis attack, a statistical attack that seeks to find linear approximations; then, the attacker can determine the keys with a high probability of deciphering the data (Bar-On et a, 2019). Another possible attack is meet in a middle attack whose main aim is to reduce the number of brute force permutations. The attacker places random guesses to both the plaintext and ciphertext. Performing a meet-in-the-middle attack is like trying to find someone in a big city, so you divide the search area into two, asking for your friend from the edge to the center, then working the other part from the center to the edge. This reduces the effective key length, making the brute force attack more likely to be successful.
Replacement to DES
Modern cryptographic algorithms are more secure and hard to decipher. One example is the Advanced encryption standard (AES), which was designed to be the predecessor of DES. It is the most widely used symmetric block algorithm due to its proven record of offering confidentiality and integrity. The first difference is that AES is byte-oriented while DES is Bit-oriented. This means that AES ciphers its data in fixed sizes of 16 bytes which is a convention with modern data processing standards (Abdullah, 2017). Modern-generation computers process data in chunks of 8, 16, 32, and 64 bits at a time. This means that the encryption used should process data in chunks of 16 bytes. AES has an advantage as it can achieve a higher level of performance. AES has a key length of 128, 192, or 256 keys, while DES uses a 56-bit key; this means that AES is more secure because it has more possible combinations to be cracked. This can be compared to a modern electronic lock and an old mechanical lock; AES is a current electronic lock that uses advanced algorithms and stronger security features that make it hard to break. On the other hand, DES is a mechanical lock that uses a simple mechanism that attackers can pick. So far, no known crypt-analytical attacks are possible; hence, brute force attack is ineffective against it. DES is vulnerable to brute force attacks, linear crypt analysis attacks, and differential crypt analysis. AES performs encryption faster than DES because of its algorithm efficiency and because it requires fewer system resources and computing power.
Summary
DES presents flaws in that it can no longer be employed in data encryption, rendering it deprecated. The use of DES poses a considerable risk of exposing organizations to cyber-attacks. The current sphere of technology means that advanced computers can perform algorithms much faster, hence the need for advanced cryptography algorithms. Modern cryptography algorithms like AES offer more security in data security because of the advanced algorithms it uses and the increased key size.
References
Abdullah, A. M. (2017). Advanced encryption standard (AES) algorithm to encrypt and decrypt data. Cryptography and Network Security, 16, 1-11.
Agate, V., Concone, F., De Paola, A., Ferraro, P., Re, G. L., & Morana, M. (2023). Bayesian Modeling for Differential Cryptanalysis of Block Ciphers: a DES instance. IEEE Access.
Alenezi, M. N., Alabdulrazzaq, H., & Mohammad, N. Q. (2020). Symmetric encryption algorithms: Review and evaluation study. International Journal of Communication Networks and Information Security, 12(2), 256-272.
Bar-On, A., Dunkelman, O., Keller, N. and Weizman, A., 2019. DLCT: a new tool for differential-linear cryptanalysis. In Advances in Cryptology–EUROCRYPT 2019: 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, May 19–23, 2019, Proceedings, Part I 38 (pp. 313-342). Springer International Publishing.
Qadir, A. M., & Varol, N. (2019, June). A review paper on cryptography. In 2019 7th international symposium on digital forensics and security (ISDFS) (pp. 1-6). IEEE.
Rasoolzadeh, S., Ahmadian, Z., Salmasizadeh, M., & Aref, M. R. (2016). An improved truncated differential cryptanalysis of Klein. Tatra Mountains Mathematical Publications, 67(1), 135–147. doi:10.1515/tmmp-2016-0036
 write
write