The blockchain has approached capacity limits as the number of individuals utilizing Ethereum has risen. As a result, the expense of using the platform has increased, necessitating scaling solutions. Multiple solutions are being investigated, evaluated, and deployed, each with a unique method to achieve comparable aims. The primary goal of scalability is to maximize transactional speed and throughput while maintaining the independence and integrity promised on Ethereum 2.0 vision. Growing demands on Ethereum layer 1 result in delayed operations and untenable gas pricing. Raising the platform’s capability in terms of bandwidth and throughput is critical to Ethereum’s significant and widespread adoption. Although bandwidth and throughput are vital, scaling solutions that support such objectives must be distributed and safe. It is vital to keep the entry barriers for node administrators low to avoid a move toward centralized and unsecured computational capabilities.
One blockchain is the core infrastructure that keeps Ethereum as the transactional champion. The creation of the Bitcoin blockchain eliminated double-expense issues without an administration. Every block is a solid structure for recording a Bitcoin blockchain transfer. Block entries are encrypted and executed. Blocks are encoded and connected utilizing hash algorithms. Merkle tree is a tree that represents the hash of a member at every node. The tool could also maintain trustworthiness if a transaction changes Merkle’s provenance. To prevent centralization difficulties, consensus means that every node involved in the communication has a correct blockchain, and the procedure is the crucial component of verification in the blockchain. Furthermore, Ethereum 2.0 innovation has already been developed, which extends over transferring data. In terms of value transmission, blockchain is faster, simpler, and more secure (Mohammed et al., 2021). Furthermore, Russia has stated that blockchain 2.0 technology is used in automated electoral processes.
Transactions underpin all forms of communication around the globe. The current requirement for individuals is a secure and resilient interaction. Third-party transfers have previously been used as a highly promising strategy; however, they have exhibited unreliability. The distributed manager was established to minimize dependency on intermediaries and address issues like double-spending when money is spent twice. Distributed ledger technologies are an innovation protocol that enables particular network members to securely transmit data without intermediaries and third parties. Distributed ledger technologies could also be characterized as cryptographic algorithms as a clear lead for data manipulation (Mohammed et al., 2021). Ethereum records a transaction in the “block” structured plan. All cubes are secured and connected by the hash protocols.
Ethereum also performs anonymized information exchange among business associates and automatically verifies and records data without using a centralized system or middleman encryption techniques. To date, a variety of blockchain frameworks have shown to be feasible in providing flexible and adaptive solutions for a variety of uses. All systems are featured, including Hyperledger Fabric, Corda, Hyperledger Fabric, Open Link, and Chain Core. Although various blockchain solutions are currently in the pilot stage, there are concerns about the technology’s effectiveness, reliability, and scalability (Dabbagh et al., 2020). As such, this section will primarily focus on previous research and publications on Ethereum scaling.
Ethereum Scaling Technology
First Layer Scaling Solutions
Sharding
The principle of sharding is used in the primary solution proposed in blockchain academia. The core principle underlying sharding is to partition the network into subgroups, known as shards, with each shard operating on a distinct transactional database than the rest of the system. This enables the system to scale with increasing shards, providing excellent throughput and memory effectiveness while possibly jeopardizing security. Similarly, for the blockchain to become secured, all shards must meet the byzantine validator limit, the minimum proportion of bad validators or nodes (Benhaim et al., 2021). In most networks, this limit is 33 percent average validators like Elastico and OmniLedger; any consensual case that exceeds that threshold is intrinsically unstable.
The fundamental concern is that a single shard could be attacked even when the entire network fits well below that limit. For example, when a network with 25% bad nodes are divided evenly into four shards, and over 33% of malevolent nodes eventually wind up in a single shard, the network will become vulnerable to a takeover attack. PoW for committee development and PFT for intra-committee agreement is used in most sharding-based blockchain protocols in academia. In contrast, PoS for committee construction and PFT for intra-committee agreement are used in the minority (Benhaim et al., 2021). Others have their consensus algorithms. As a result, sharding-based blockchain protocols are split into three groups: proof-of-work and PFT, proof-of-stake, and PFT, and sharding-based on alternative consensus methods.
- Sharding-based Proof-of-Work and PFT Elastico
Elastico, the world’s initial sharding-based blockchain technology, is a contender for a public blockchain that deal with byzantine opponents. Elastico partitions the network into numerous committees, each responsible for a different transaction database known as shards. Elastico uses PFT for intra-committee consensus and PoW for committee establishment. With the network density, the number of shards expands roughly exponentially. Elastico can increase throughput to up to 40 tx/s whenever the network hits 1600 nodes. It does, though, have flaws. The first is that malicious nodes can impact the partition of each epoch, such as one sharding round once a day of Elastico (Hafid et al., 2020). Furthermore, the network can only accept up to 25% of faulty nodes and 33% of malicious nodes in each committee.
In throughput and reliability, RapidChain exceeds previous sharding techniques. RapidChain’s cross-shard interactions depend on an inter-committee routing technique of Kademlia’s routing protocol. RapidChain can accept up to 33% of faulty nodes in the system and 50% of malicious nodes for every committee (Hafid et al., 2020). RapidChain also promises a substantially higher throughput, up to 4220 tx/s, once the network reaches 1800 nodes.
- Sharding-based Proof-of-stake and PFT
The Zilliqa solution significantly increases throughput. The sharding architecture of Zilliqa enables the network to execute interactions simultaneously and obtain superior throughput. Zilliqa is intended to handle a thousand times the amount of data Ethereum does. Nevertheless, this technique has flaws, such as it failing to partition blockchain data storing, as state sharding does; also, Zilliqa’s sharding mechanism is vulnerable to a single-shard takeover attack. Elastico and OmniLedger both promise to have the identical resilience as Zilliqa.
Harmony has been offered as a means to address some of Zilliqa’s flaws, promising to be entirely scalable. Harmony shards validate network communications, transactions, and the blockchain state, similar to Zilliqa. Furthermore, because of its decentralized randomization generation technique, Harmony demonstrated that its sharding mechanism offers strong security (Hafid et al., 2020). Like Zilliqa, Elastico, and OmniLedger, Harmony promises domestic and international resilience.
Ethereum sharding 2.0 is a three-phase sharding-based blockchain framework among the most prominent. The initial is Beacon Chain, which controls all network shards. It also implements consensus criteria, incentives, and sanctions to verifiers and manages verifiers and their values. Shard Chains, the second step, allows for parallel operations. State Execution is the final step, wherein the whole platform’s actions are carried out; it presents the idea of Execution Environments (EEs), which enables a smart contract comparable to Ethereum. To account for cross-shard communications, Ethereum chose the transaction model. Each transaction produces a notice under the receipt model. Such receipts are kept on the beacon chain using decentralized, shared storage, which means they will be visible to other shards but not editable (Zamani et al., 2018). To execute Ethereum sharding 2.0, Ethereum leverages the Casper consensus, a new PoS consensus to substitute the existing PoW consensus.
- Sharding-based on another consensus
Utilizing a unique structure, Logos increased throughput while reducing delay. In terms of technology, Logos employs Axios protocol, a delegated iteration of the ByzCoin-inspired PBFT mechanism, and OmniLedger; the Axios protocol has been tailored to the Logos framework. All accounts on the Logos system have their chain, which keeps records of their operations and performs them simultaneously. The main settlement chain ensures that all nodes are in alignment and that dynamic validation sets are available. Sharding provides an extra level of parallelism to the system, which helps to solve the scalability problem. Operations are validated and authorized by a small group of elected members through a representative system, reducing redundant procedures while maintaining security (Zamani et al., 2018). Additionally, Logos’ distinctive hybrid data framework empowers shards to synchronize on summarized data cheaply and dramatically minimizes the overhead incurred by cross-shard operations; this is the primary advantage of Logos over other sharding-based methods.
Monoxide provides a new asynchronous protocol known as Zones like Shards, which expands the blockchain proportionally to the number of zones without sacrificing or decreasing security or jeopardizing decentralization. Monoxide secures the accuracy of cross-shards or cross-zones operations by utilizing ultimate atomicity. It also offers Chu-ko-nu mining, a revolutionary proof-of-work system that assures functional mining strength in every zone is equal to that of the overall infrastructure, attacking a single zone as tough as an assault on the whole network. Monoxide is the only sharding technique that implements the Nakamoto consensus mechanism with PoW for intra-consensus communication (Hafid et al., 2020). Ultimately, Monoxide asserts to be the only scalable blockchain framework involved in executing entire sharding by dividing or dispersion the workload of all blockchain facets, such as transactional broadcast, mining competitiveness, chain storage, transactional implementation, and state participation.
Second Layer Scaling Solutions
- On-chain Solutions
On-chain solutions are ways for increasing scalability by changing only the components of a blockchain. The Big block is one of the most fundamental instances of on-chain solutions. The block only increases the largest block size, like Bitcoin Unlimited. The benefit of this system is that it has a larger transactional limit and cheaper infrastructure costs than the traditional processes. The negative is that as block sizes grow more prominent, the transmission speed slows, causing forks to occur regularly, enhancing the likelihood of orphan blocks emerging and raising chain maintenance expenses, leading to mining concentration (Kim et al., 2018). Due to such drawbacks, expanding the block size is not an excellent scalability solution.
In Bitcoin’s BIP-114, the Merkelized Abstract Syntax Tree is a binary tree that continuously repeats the process of concatenating two hashes of every block activity, then hashing the two hashed operations again and concatenating them two by one until they are one. The Abstract Syntax Tree is a means of connecting every operation until every system’s dependencies are mapped. Thus, MAST is a mechanism for converting Bitcoin scripting into a Merkle tree. Since it has a binary spanning tree, it expands on a log scale, reducing the size of a block comprising the Bitcoin scripts. Since one branch is concealed, it has more privacy as it fails to understand the other branch’s specific data (Kim et al., 2018). However, since the other branch is not concealed, it fails to provide perfect privacy.
Ethereum uses the sharding approach, commonly employed in distributed databases, to apply to blockchain. As additional blocks are accumulated, the nodes are tasked with storing all block data. Rather than retaining all of the blocks, sharding is a technique wherein nodes are clustered together to form a shard. Each shard processes separate blocks, reducing the load on every node and improving throughput by parallelly handling transactions (Kim et al., 2018). Nevertheless, the data integrity is destroyed once hackers gain complete control over anyone’s shard, a 1% assault.
- Off-chain Solutions
Off-chain computing (state-channel solution) improves scalability by handling operations beyond the network. It keeps the main-chain state and implements the last state computed in another stream. Bitcoin’s Lightning Network is a prime illustration of an off-chain solution. The Lightning Network was created to answer problems such as the ones below. Although Bitcoin allows for micropayments, it is impractical to complete the service charge and wait for the operation to join the block. The Lightning network method begins with the individuals who would use the payment method to establish the channel. At this point, a coin is placed in the multi-sig signature that operations share beforehand, preventing one person from arbitrarily escaping with the coin (Pawar et al., 2020). An on-chain operation that incurs a main-chain service charge is opening the channel. Following the opening of a channel, any actions in the channel are off-chain activities, meaning they are not recorded in the main chain, and there is no cost and a short queue length. When a channel is terminated, its final state is reported and sent to the Main-chain, and it is also an on-chain transaction. If users A and B retain a channel, and B and C retain a channel, then A and C can link, improving scalability. This strategy has the benefit of lowering processing fees and waiting times while also easing the load on the main chain (Pawar et al., 2020). Nevertheless, minors’ revenues decline as the service charge evaporates, and their ecosystems may shift.
- Child-chain
The parent-child framework of the child-chain system conducts operations in the child-chain and stores the outcomes in the parent-chain. Plasma, an instance of a child chain, may be observed in Ethereum. It is possible to represent this as Blockchain in Blockchain. Plasma may iteratively produce a Plasma network with a parent-child infrastructure that handles operations on the child system and turns all operations in the single Merkle root hash, then written to the parent chain. It is comparable to the off-chain approach at the start of the procedure. After establishing the child-chain in the Plasma network that becomes a parent-chain, it invests the coin through the smart contract and acquires the tokens for usage in the child-chain (Poon & Buterin, 2017). The former child-chain functions like a traditional blockchain and all activities are archived as a Merkle root hash in the parent-chain system.
When a scam happens anywhere on the plasma chain, the compromised node is lengthier to remove the unit than the token’s owner, allowing the token’s operator to relocate the token to any parent plasma system. In contrast, the compromised node loses the deposit. Anybody can contribute to block validation because it is accomplished through fraudulent proof equipped with smart contracts. Since just the child-Merkle chain’s root hash is transported to the parent chain, and the parent chain can be computed by dividing the child chain by functionality, this technique is substantially lighter. However, verifying the child chain is costly since it must stay abreast if all parent chains are trustworthy (Poon & Buterin, 2017). Furthermore, after converting all operations on the child-chain to Merkle hashes, it should be checked that the parent-chain, iteratively to the root, is valid, which is inconvenient.
- Inter-chain
The inter-chain approach is a mechanism of allowing interactions across different blockchains. The inter-chain strategy aims to combine blockchains, just as autonomous ethernet in the initial periods was connected into one network, the Internet (Lee, 2018). The Inter-chain technique is quite comparable to the side-chain strategy; thus, it is the foundational technique for executing the side-chain.
Atomic-swap is an instance of an inter-chain technique. The goal of this method is to transfer assets across multiple blockchains. Assuming that Lightcoin user A and Bitcoin user B wants to trade 20 LTC and 1 BTC. B creates a transfer that enables A to take 1 BTC through the digital certificate and a quantity n that only A understands, or that restores the coin to B once a specific amount of time has passed. B then generates a public key for the n quantity and distributes it around the system. Upon receipt of information, user A creates a process that enables them to take 20 LTC utilizing user B’s digital certificate, or that restores the currency to A after a specified time which is less than the time B specifies; for instance, A can limit the expiry to 1 day if B specifies two days. At this stage, a possesses the public key for n; thus, they can complete the operation without realizing what n is. When B effectively obtains 20 LTC, A gains knowledge of n, allowing A to grab 1 BTC. Since if A’s expiry time is more significant than B’s, B takes 20 LTCs right before the end of their expiry, and the coin returned to B before they take 1 BTC, A’s expiry time will decrease. This method benefits by combining many blockchains and transferring resources across them (Lee, 2018). The drawback is that these blockchains should employ the same PoW technique, which is a hash-competing methodology, and that when one of the parties is sluggish, the transaction cannot be finished when the expiry date is approaching. Table 1 below summarizes Ethereum scaling technologies, including their respective effectiveness and drawbacks.
| Ethereum Scaling Technology | Solution | Effectiveness | Flaws |
| First Layer Solutions | Elastico |
|
|
| OmniLedger |
|
|
|
| RapidChain |
|
|
|
| Zilliqa |
|
|
|
| Harmony |
|
|
|
| Logos |
|
|
|
| Monoxide |
|
|
|
| Second Layer Solutions | On-chain Solutions |
|
|
|
|
||
| Off-chain Solutions
Child-chain |
|
|
|
| Inter-chain |
|
|
Solutions Utilizing the Ethereum Consensus Algorithm can Offer the best Solution
Proof-of-Work Consensus
While several blockchain systems use different PoW processes, the principles of the PoW consensus algorithm illustrate Bitcoin’s blockchain topology and PoW technique. The block header and transactions contained within every block in the Bitcoin blockchain make up the block. A block header entails a past block header’s hash value, Merkle root operations, and a nonce element. The Merkle root highlights the operations in the existing block, and the primary hash function ensures that the network is not changeable after a block is added to the blockchain (Portmann, 2018). The nonce element holds an integer number that modifies the block header’s hash value without affecting other elements. Figure 1 below demonstrates a hash unit.
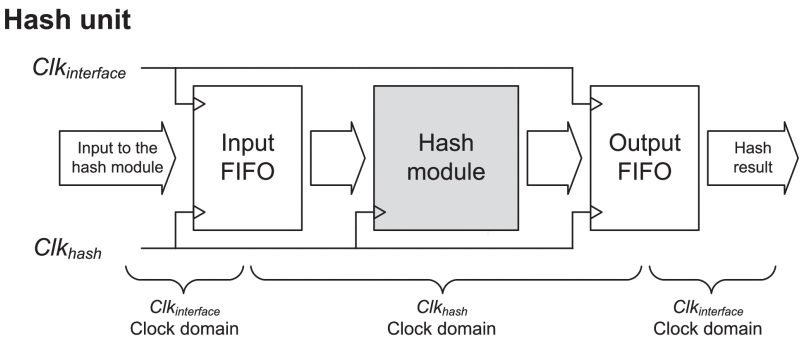
Figure 1: Hash Unit
Source: https://www.sciencedirect.com/topics/computer-science/one-way-hash-function
The hash function of the block header in the Bitcoin consensus mechanism must be less than a specific threshold, which is defined by the complexity level. The system adjusts the complexity level continuously based on the platform’s pooled hash rate. Bitcoin’s hashing is double SHA-256, which employs the SHA-2 hashing algorithm twice on the block header. Obtaining a nonce quantity that enables the hash function to match the criterion is the essence of the mining procedure. Since the hashing is not injective, the only way to locate a legitimate block is to perform brute-force searching involving several PoW calculations with varying nonce integers (Portmann, 2018). The likelihood of discovering a block with a nonce number that fulfills the criteria is proportionate to the dedicated processing capacity because the hash function’s result is spread evenly.
The largest blockchain branching is chosen as the legitimate chain by every node in the blockchain system. When an adversary wishes to fabricate a phony blockchain, it must provide the network with a more extensive blockchain than the legitimate one. Constructing a counterfeit blockchain necessitates more PoW calculations than the total processing capacity of the miners presently involved. The PoW consensus protocol’s integrity is based on the assumption that there is no monetary motivation to take over the bulk of computational resources and waste electric power attacking the blockchain (Portmann, 2018). On the other hand, ASIC solutions for blockchain miners pose a danger to this assumption. Figure 1 below indicates the complexity grows as the number of miners increases on an Ethereum platform over 24 hours.
The PoW calculation necessitates a large amount of computational power; however, it is confined to various computations’ most common hash functions. An ASIC-based infrastructure can give unequaled functionality and energy effectiveness for the specific computational activity than a general-purpose computational platform, including a CPU or GPU. An ASIC-based Bitcoin mining infrastructure, for instance, can execute 13 trillion PoW operations every second and requires 1310 W of power, while a GPU-based miner console with NVIDIA GeForce GTX 1080 could only execute 1.5 billion PoW calculations every second while utilizing 250 W of electricity. Producing an ASIC necessitates a significant investment; however, most of the costs are non-recurring engineering (NRE) costs discounted as total output grows. As the Bitcoin network expands, more ASIC-based mine console is deployed, and the financial boost of mining is no longer viable except if miners utilize ASIC-based mining equipment (Cho, 2018). To minimize the same outcomes as Bitcoin mining, various ASIC-resistant PoW techniques have been devised. The following are the most common varieties of ASIC-resistant PoW methodologies.
- PoW with multiple hashes
Unlike Bitcoin’s PoW technique, which utilizes only one hashing algorithm, this family of PoW methods utilizes many hashing algorithms to generate the block’s legitimate state. Such hashing methods are utilized in a specific order to the block’s header (Ashik et al., 2020). Every block’s hash algorithm sequencing would either be fixed or continuously generated. X11, X14, X17, X11EVO, X16S, X16R, Quark, and TimeTravel are just a few examples of multi-hash PoW techniques. Figure 2 below illustrates hash functionalities within a fixed chain.
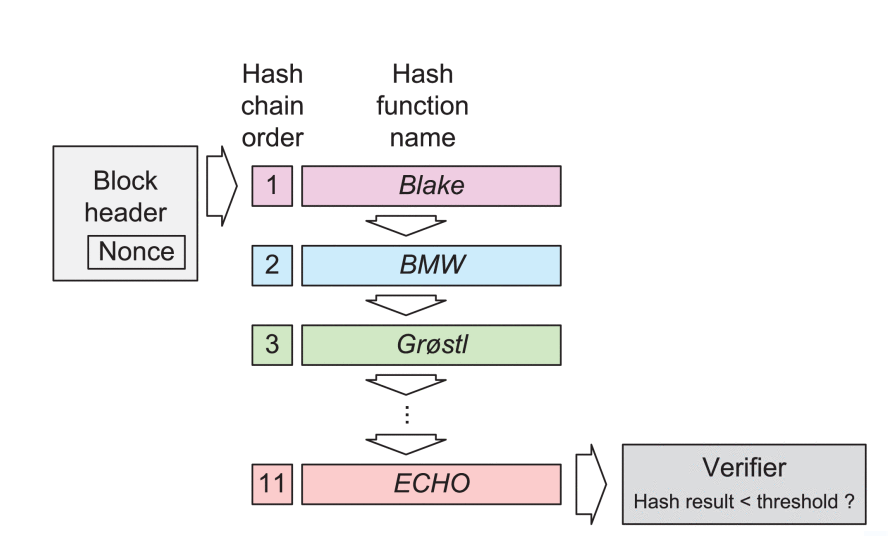
Figure 2: hash functionalities within the fixed chain
Source: https://www.sciencedirect.com/topics/computer-science/one-way-hash-function
- Memory-intensive PoW
While ASICs have significantly more algorithm efficiency than general-purpose operating systems, they are limited by external data throughput, just like general-purpose operating systems. Memory-hard PoW algorithms, such as Ethereum’s Ethash, Scrypt, and CryptNight, prioritize this feature to provide ASIC resilience. A memory-intensive PoW algorithm requires retrieving random data from a large dataset. The full dataset is large enough that creating an ASIC capable of storing the entire dataset in on-chip memory is complex. For instance, Ethash’s DAG dataset is several gigabytes in size and growing. The site of the information that must be retrieved for every PoW computation with a unique nonce is decided during the computing; therefore, prefetching the necessary data or grouping multiple nonces that reference the same region of the dataset is not possible (Cho, 2018). As a result, the applicable hash rate would be constrained by the system’s accessible off-chip data throughput.
Memory-hard algorithms currently have better ASIC resilience than Bitcoin’s SHA256d. Nevertheless, ASIC solutions that address such memory-intensive PoW techniques, like the Antminer E3 for Ethash and Antminer L3+ for Scrypt, are finally introduced to the market (Cho, 2018). Furthermore, future transistor innovations like 3D stacking could help memory-intensive PoW systems overcome performance bottlenecks. Memory-hard PoW methods’ ASIC resilience must be verified with advancing technology as they become more accessible to low-cost ASIC platforms.
- Programmatic PoW
Memory-hard PoW methods’ ASIC resilience must be verified with advancing technology as they become more accessible to low-cost ASIC platforms. The diversity of calculations is one of the emerging strategies for ASIC-resistant PoW techniques. A significant reservoir of arithmetic operations or randomly created software, for instance, could be used in the process. Building customized hardware components to address each conceivable computational activity would be unfeasible. This form of PoW algorithm has yet to be implemented in a functional blockchain platform, although it is currently intensively explored (Ashik et al., 2020). Nevertheless, customized hardware with a vast array of small but effective programmable circuits can still be built to improve computation efficiency beyond general-purpose computational systems.
Different consensus protocols for blockchain systems have been developed, albeit not as prevalent as PoS. Practical Byzantine Fault Tolerance (PBFT) is a replica following the consensus technique involving recognized entities that can accept up to 33% of the participants failing Byzantinely. Proof-of-Human-Work necessitates human engagement by demanding the resolution of a puzzle as proof of work. Comparable to CAPTCHA, the challenge is designed to be user-friendly but inadequate for machines. A particular consensus algorithm, such as Proof-of-Useful-Effort, attempts to link PoW computations with productive work (Ashik et al., 2020). Primecoin’s consensus algorithm, for instance, is predicated on a computational that finds a prime number sequence.
How Understanding Use Cases of Ethereum Scaling help in Identifying Future Trends
Ethereum was created in 2015 to serve as a distributed global supercomputer. Ethereum, the world’s second-largest blockchain infrastructure, has been plagued by scalability concerns for the past few years. The non-scalability of the proof-of-work consensus protocol means that blockchains implementing it can only handle single-digit operations throughput. As a result, the system is currently transitioning to proof-of-stake, an alternate consensus process that appears to alleviate the Ethereum platform’s difficulties potentially. Most decentralized applications could run on the blockchain thanks to its consensus method, comparable to a cloud deployment but with additional safety features, independence, and reliability. This quickly became known as the ‘ICO mania,’ Several people started establishing coins on the Ethereum blockchain for no other reason than to receive money from investors. This resulted in many new subscribers and operations on the blockchain, which can handle 15 operations per second.
The infrastructure became overburdened, and the expense of using it soared. This fee, referred to as ‘gas,’ is a price incurred in Ether to the participants who handle transaction processing. Because all operations must be broadcasted to the system for all blocks, and the most secured node has all the blockchain’s information, scalability difficulties are inherent in such a consensus protocol (Hargrave & Karnoupakis, 2020). This provides a situation wherein operation throughput cannot be directly scaled without expanding the number of different blocks, resulting in centralization due to inaccessibility.
Miners, who execute network operations, take the gas charge straight from each operation, making them the critical decision authorities for the typical gas price. A transfer with a more excellent gas price will be approved quicker, while a smaller gas price will be approved slowly due to miners prioritizing greater yields. Operations start to back up in the memory pool; awaiting operations reside. Miners prioritize operations with higher gas prices, and the minimum gas price for verifying a transfer rises as a result. As the network grows more crowded, the platform’s gas charge rises to obscene levels, exacerbating the problem. The CryptoKitties dApp’s viral success demonstrated this (Hargrave & Karnoupakis, 2020). CryptoKitties was gaming on the Ethereum blockchain, enabling customers to obtain and sell tokenized digital experience cats. It exploded almost instantly, delivering many operations to the chain’s memory cache. CryptoKitties drove almost all of the network’s transactional queries, which increased from 622,000 to nearly 1.07 million. As a result, gas costs began to rise gradually before skyrocketing due to high network usage.
This is simply one of Ethereum’s creators’ predicted concerns, as restricted scalability was one of the first challenges issued on the network. Nevertheless, the system has only increased in size, and upgrading an infrastructure still extensively used daily is tough. Furthermore, unlike a centralized infrastructure, Ethereum cannot be ‘paused’ for improvements. This has complicated the scalability challenge, mainly because it updates the consensus protocol at the center of the world computer. Among other things, the key suggested change is a switch to a proof-of-stake consensus protocol.
On the other hand, proof-of-work depends on the sheer computational capacity to guarantee that all parties agree. Although it is being used to safeguard the network, computational power is lost. Proof-of-stake is based on more core rules of operation. The consensus protocol focuses heavily on finding and removing problematic participants from the process (Alfandi, Otoum & Jararweh, 2020). This is known as Byzantine Fault Tolerance, and it is a crucial aspect of keeping the blockchain up and operating.
Proof-of-stake tries to minimize the number of negative individuals by requiring them to put their money where their mouth is. Verifying nodes must stake, or deposit, a particular amount of Ether in a shared ledger, the size of which affects the intensity of the participant’s decision on the blockchain. Such validators are then given the authority to suggest block editions, with consensus obtained after a round of polling to verify that all participants on the system have access to the same shared history. This is more effective in terms of the amount of electricity consumed and the platform’s economy (Alfandi, Otoum & Jararweh, 2020). Because new currencies do not need to be created regularly to incentivize miners, the platform can use a deflationary rather than an inflationary paradigm.
Furthermore, transactional throughput can be boosted because participants are only needed to replicate the state of operations on the network, not the complete chain. Proof-of-stake networks are more scalable long-term viable, and more resilient to 51 percent of attacks (Coladangelo & Sattath, 2020). Nevertheless, Ethereum’s execution appears to be a long way off, at least for now.
The most incredible Ethereum solutions have emerged as the remedies to the Ethereum network’s scalability and high trading costs. In reality, scalability is a desirable prerequisite for securing a blockchain platform’s broad acceptance. Furthermore, decreased trading fees may inspire more people to use the Ethereum network. By permitting off-chain processing, solutions give the best solution for the growing demand on the Ethereum platform. The many Ethereum solutions presented can potentially alter the blockchain environment positively. Solutions are the following substantial hit guarantee that blockchain platforms are used efficiently (Coladangelo & Sattath, 2020). On the other hand, it is worth noting that several Ethereum solutions are still in the early stages of development or evaluation. As a result, full-fledged solutions could take some time to dominate the Ethereum environment.
Scalability Trilemma and its Solutions
The ability of blockchain technology to accommodate high operational throughput and expansion is referred to as scalability. This shows that the role of a scalable blockchain will not degrade as use cases proliferate and the acceptance of blockchain technology increases. Scalability is a term used to describe blockchains that perform poorly as usage grows. According to the blockchain trilemma, increased scalability is feasible, yet security, decentralization, or both would suffer as a result. Scalability is the only option for blockchain platforms to contend with traditional, centralized systems, which currently have considerably greater network settlement speeds and functionality (Altarawneh et al., 2020). Whereas several blockchain systems have achieved decentralization and security, the world’s foremost decentralized platforms have a big issue in establishing scale.
The scalability trilemma is well-known in the blockchain world, having been initially defined by Vitalik Buterin, the coinventor of Ethereum. According to Vitalik, trade-offs across three crucial qualities: decentralization, scalability, and security are unavoidable. Decentralization is at the heart of Ethereum; security is a must-have feature, while scalability is the most incredible difficulty. The scalability trilemma argues that one can have only two of either decentralization, scalability, or security; for example, one can only choose one of the triangle’s sides; consequently, trade-offs are almost unavoidable. The main difficulty is achieving scalability, security, and decentralization simultaneously (Altarawneh et al., 2020). In the research, sharding, Directed Acyclic Graph, and Lightning Network have all been presented to answer the scalability problem.
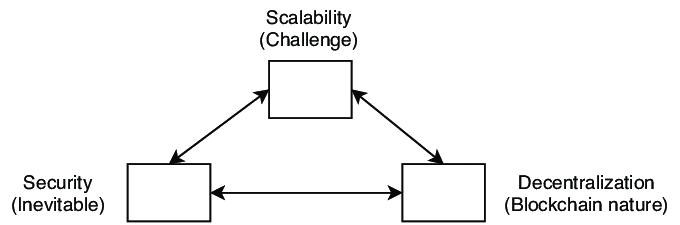
Figure 3: The scalability trilemma
Source: https://ieeexplore.ieee.org/abstract/document/9133427
Scalability, security, and decentralization are three traits that all distributed platforms should strive towards. To be scalable, a decentralized platform should expand as the network develops without incurring high storage capacity, even as the number of active nodes and transactions expands. A decentralized method is reliable if it is fair, predictable, and accessible even in adversity. Lastly, to be fully decentralized, a distributed platform should meet two elements of decentralization. Firstly, it must be made up of a large set of discrete nodes and be capable of handling a large number of them going down simultaneously. Secondly, such nodes should not be controlled by a limited group of people or groups (Altarawneh et al., 2020). Even though decentralized platforms are often constructed with such properties in mind, it is a binary choice. As a result, any consensus algorithm prioritizes two of the three features.
Even though the blockchain trilemma offers significant barriers to adoption, new solutions are emerging to reconcile network security, decentralization, and scalability. Whereas the CAP hypothesis has remained true for over 40 years, the adoption of Layers 1 and 2 technologies and the development of Proof of Stake in the blockchain is on the verge of moving the norm toward distributed, secure, and scalable decentralized platforms. Layer 1 pertains to blockchain technologies such as Bitcoin, Litecoin, and Ethereum in the decentralized environment (Hafid et al., 2020). Several research or use methodologies aim to solve the blockchain trilemma and directly enhance scalability.
- Consensus Protocol Enhancement
Proof of Work is the consensus method on central blockchain systems like Bitcoin. Proof of Work is safe, but it takes a long time. Bitcoin, for instance, receives only seven TPS. That’s why most blockchain systems, including Ethereum’s update to Ethereum 2.0, use the Proof-of-Stake consensus method. Rather than requiring miners to run cryptographic algorithms with extensive processing capabilities, the PoS consensus mechanism decides validation status based on a stake in the system (Hafid et al., 2020). This is expected to significantly increase the Ethereum platform’s throughput while boosting decentralization and ensuring security.
- Nested blockchain
Layer 2 refers to a platform or system that uses fundamental blockchain technology to improve scalability and efficiency. Bitcoin, for example, is a Layer-1 protocol, while the Lightning Network is a Layer-2 solution for speeding up Bitcoin transactions. A nested blockchain is a distributed network system that operates on an interconnected web of subsidiary networks and uses the primary blockchain to specify settings. There are several blockchain levels on the primary chain, each with a parent-child relationship. The parent chain delegated work to the kid chains, who completed it and returned it to the parent. The underlying core blockchain does not participate in network services until resolving disputes arise. Above Layer-1 Ethereum, a stacked blockchain network, such as the OMG Plasma project, is used to support faster and more efficient processes (Hafid et al., 2020). This method of workload allocation reduces the processing burden on the main-chain, resulting in tenfold increased scalability.
- Sidechains
A side-chain is a functional chain that runs alongside the blockchain and is employed in massive bulk operations. Side-chains have their consensus method, which could be adjusted for performance and scalability. A practical token is frequently utilized regarding the data transfer mechanism across the side and main networks. The main chain’s principal role is to maintain general integrity and resolve conflicts. Side-chains differ from state channels in several ways. To begin with, side-chain operations are not private among users; instead, they are published openly on the blockchain (Altarawneh et al., 2020). Furthermore, security issues in side chains have no impact on the main-chain or other side chains. A side-chain requires a significant amount of time and effort to construct.
- State channels
A state channel improves total operational bandwidth by facilitating two-way interaction among a blockchain and off-chain functional pathways via various approaches. To authenticate a transmission over a state channel, the user does not need to be involved right away. Instead, it is a network-adjacent tool protected via a multi-signature or smart contract technique. The ultimate state of the channel and all its intrinsic transformations like Ethereum’s Raiden Network and Bitcoin Lightning are posted to the underlying blockchain whenever an operation or batch of operations is completed on a state channel (Altarawneh et al., 2020). State channels surrender partial independence for better scalability in the trilemma dilemma.
Conclusion
The growing range of applicants and clients on Ethereum is causing the infrastructure to become overburdened. The Ethereum platform’s capability is restricted. As a result, the cost of accessing the platform rises sharply as more individuals compete for the right to submit operations to the Ethereum platform. The key scalability goals for the Ethereum platform are fast processing speeds and higher transactional throughputs. Equally, scaling solutions should not jeopardize the Ethereum platform’s integrity or decentralization. On the layer one blockchain, Ethereum also faces issues about excessive gas expenses and delayed operations. For now, Ethereum has two unique alternatives for solving scalability, excessive transaction fees, and transaction settling latencies in the form of sharding and layer two solutions. As a result, Ethereum scaling solutions are essential tools for tackling network performance issues. Several scalability options for Ethereum are being researched, tested, and implemented, with various methodologies for attaining scalability.
References
Abraham, I., Malkhi, D., Nayak, K., Ren, L., & Spiegelman, A. (2016). Solida: A blockchain protocol based on reconfigurable byzantine consensus. arXiv preprint arXiv:1612.02916.
Alfandi, O., Otoum, S., & Jararweh, Y. (2020, April). Blockchain solution for iot-based critical infrastructures: Byzantine fault tolerance. In NOMS 2020-2020 IEEE/IFIP Network Operations and Management Symposium (pp. 1-4). IEEE.
Altarawneh, A., Herschberg, T., Medury, S., Kandah, F., & Skjellum, A. (2020). Buterin’s scalability trilemma viewed through a state-change-based classification for common consensus algorithms. 2020 10th Annual Computing and Communication Workshop and Conference (CCWC). https://doi.org/10.1109/ccwc47524.2020.9031204
Ashik, M. H., Shahriar Maswood, M. M., Alharbi, A. G., & Medhi, D. (2020). FPoW: An ASIC-resistant proof-of-Work for blockchain applications. 2020 IEEE Region 10 Symposium (TENSYMP). https://doi.org/10.1109/tensymp50017.2020.9230915
Benhaim, A., Hemenway Falk, B., & Tsoukalas, G. (2021). Scaling blockchains: Can elected committees help? SSRN Electronic Journal. https://doi.org/10.2139/ssrn.3914471
Blom, F., & Farahmand, H. (2018). On the scalability of blockchain-supported local energy markets. 2018 International Conference on Smart Energy Systems and Technologies (SEST). https://doi.org/10.1109/sest.2018.8495882
Cho, H. (2018). ASIC-resistance of multi-hash proof-of-Work mechanisms for blockchain consensus protocols. IEEE Access, 6, 66210-66222. https://doi.org/10.1109/access.2018.2878895
Coladangelo, A., & Sattath, O. (2020). A quantum money solution to the blockchain scalability problem. Quantum, 4, 297.
Dabbagh, M., Kakavand, M., Tahir, M., & Amphawan, A. (2020). Performance analysis of blockchain platforms: Empirical evaluation of Hyperledger fabric and Ethereum. 2020 IEEE 2nd International Conference on Artificial Intelligence in Engineering and Technology (IICAIET). https://doi.org/10.1109/iicaiet49801.2020.9257811
Hafid, A., Hafid, A. S., & Samih, M. (2020). Scaling blockchains: A comprehensive survey. IEEE Access, 8, 125244-125262. https://doi.org/10.1109/access.2020.3007251
Hargrave, J., & Karnoupakis, E. (2020). Blockchain Success Stories. O’Reilly Media.
Hu, Y., Manzoor, A., Ekparinya, P., Liyanage, M., Thilakarathna, K., Jourjon, G., & Seneviratne, A. (2019). A delay-tolerant payment scheme based on the Ethereum blockchain. IEEE Access, 7, 33159-33172. https://doi.org/10.1109/access.2019.2903271
Kim, S., Kwon, Y., & Cho, S. (2018). A survey of scalability solutions on blockchain. 2018 International Conference on Information and Communication Technology Convergence (ICTC). https://doi.org/10.1109/ictc.2018.8539529
Kuzlu, M., Pipattanasomporn, M., Gurses, L., & Rahman, S. (2019). Performance analysis of a Hyperledger fabric blockchain framework: Throughput, latency and scalability. 2019 IEEE International Conference on Blockchain (Blockchain). https://doi.org/10.1109/blockchain.2019.00003
Lee, J. (2018). Komodo: An Advanced Blockchain Technology, Focused on Freedom. Komodo Platform, Komodo, 12.
Lee, W. (2019). Creating your own private Ethereum test network. Beginning Ethereum Smart Contracts Programming, 71-91. https://doi.org/10.1007/978-1-4842-5086-0_4
Luu, L., Narayanan, V., Zheng, C., Baweja, K., Gilbert, S., & Saxena, P. (2016). A secure Sharding protocol for open blockchains. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. https://doi.org/10.1145/2976749.2978389
Miller, A., Xia, Y., Croman, K., Shi, E., & Song, D. (2016). The honey badger of BFT protocols. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. https://doi.org/10.1145/2976749.2978399
Mohammed, A. H., Abdulateef, A. A., & Abdulateef, I. A. (2021). Hyperledger, Ethereum and blockchain technology: A short overview. 2021 3rd International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA). https://doi.org/10.1109/hora52670.2021.9461294
Pawar, M. K., Patil, P., & Hiremath, P. S. (2020). A study on blockchain scalability. Advances in Intelligent Systems and Computing, 307-316. https://doi.org/10.1007/978-981-15-8289-9_29
Pongnumkul, S., Siripanpornchana, C., & Thajchayapong, S. (2017). Performance analysis of private blockchain platforms in varying workloads. 2017 26th International Conference on Computer Communication and Networks (ICCCN). https://doi.org/10.1109/icccn.2017.8038517
Poon, J., & Buterin, V. (2017). Plasma: Scalable autonomous smart contracts. White paper, 1-47.
Poon, J., & Dryja, T. (2016). The bitcoin lightning network: Scalable off-chain instant payments.
Portmann, E. (2018). Rezension „Blockchain: Blueprint for a new Economy“. HMD Praxis der Wirtschaftsinformatik, 55(6), 1362-1364. https://doi.org/10.1365/s40702-018-00468-4
Schäffer, M., Di Angelo, M., & Salzer, G. (2019). Performance and scalability of private Ethereum blockchains. Business Process Management: Blockchain and Central and Eastern Europe Forum, 103-118. https://doi.org/10.1007/978-3-030-30429-4_8
Xin, W., Zhang, T., Hu, C., Tang, C., Liu, C., & Chen, Z. (2017). On scaling and accelerating decentralized private blockchains. 2017 IEEE 3rd International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing, (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS). https://doi.org/10.1109/bigdatasecurity.2017.25
Yang, F., Zhou, W., Wu, Q., Long, R., Xiong, N. N., & Zhou, M. (2019). Delegated proof of stake with downgrade: A secure and efficient blockchain consensus algorithm with downgrade mechanism. IEEE Access, 7, 118541-118555. https://doi.org/10.1109/access.2019.2935149
Zamani, M., Movahedi, M., & Raykova, M. (2018). RapidChain. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. https://doi.org/10.1145/3243734.3243853
Zheng, Z., Xie, S., Dai, H., Chen, X., & Wang, H. (2017). An overview of blockchain technology: Architecture, consensus, and future trends. 2017 IEEE International Congress on Big Data (BigData Congress). https://doi.org/10.1109/bigdatacongress.2017.85
 write
write