Introduction
On July 15, 2020, about 130 high-profile Twitter accounts were compromised to promote a Bitcoin scam. The perpetrators gained access to the administrative tools of Twitter to post the Bitcoin scam tweets directly (Anderson and Saleh 2021, p. 7). They seemed to have used social engineering to access Twitter’s administrative tools through Twitter employees. The scam asked people to send Bitcoin currency to a particular cryptocurrency wallet, promising that the money would be doubled and returned as a charity gesture. A few minutes after the initial tweets, over 320 transactions had already been done on one of the wallet addresses provided by the perpetrators, and Bitcoin worth over $110,000 was deposited in the account before Twitter removed the scam messages (Anderson and Saleh 2021, p. 8). The scam compromised accounts of well-known individuals, including and not limited to; Joe Biden, Barack Obama, Bill Gates, Jeff Bezos, Warren Buffet, Michael Bloomberg, and Mayweather Jr. It also affected companies like; Uber, Apple, and Cash App (Wiederhold 2014, p. 131). While 130 accounts were affected by the scam, Twitter believed that only 45 were used to tweet the Bitcoin scam messages, with most of these accounts having at least a million followers. The breach generally raised many questions and concerns in the broader security and public safety of Twitter, as millions of users depend on Twitter not just to tweet publicly but also to communicate privately through the direct message services available on the platform (Anderson and Saleh 2021, p. 7). As such, an attack on the system’s servers raises a threat to Twitter users’ privacy, data security, and safety of their private information. This report, therefore, aims to address the Twitter Bitcoin scam by analyzing the Anatomy of the attack, determining the attackers’ social engineering framework and stages, determining the impact of the attack and recommending approaches that can help minimize the risks of the attack in future.
Anatomy of the Attack
On Wednesday, July 15th 2020, between 20:00 and 22:00, UTC attackers obtained access to Twitter’s internal network and particular employee credentials that gave them access to the organization’s internal support tools (Breda et al., 2017, p. 107). This social engineering attack targeted a small number of Twitter employees, giving them access to about 130 Twitter accounts, ultimately tweeting from 45 of these accounts, accessing the DM inbox of 36 of these accounts and downloading Twitter data of 7 of these accounts. Forensic analysis of the scam depicts that the initial scam messages were posted by the accounts concise one or two-character distinctive names like; “@6” (Debb 2021, p. 582). This was followed by messages on cryptocurrency Twitter accounts at around 20:00 UTC on July 15th, including CoinDesk, Binance and Coinbase. The scam then moved to high profile accounts, with the first scam tweet sent using Elon Musk’s Twitter account at 20:17 UTC (Anderson and Saleh 2021, p. 7). Other accounts compromised in the incidence included well-known persons like; Michael Bloomberg, Jeff Bezos, Bill Gates, Barack Obama, Joe Bidden, Floyd Mayweather, Kanye West and Warren Buffet. Companies such as Cash App, Apple and Uber were also compromised.
The tweets involved in the scam claimed that the sender in charity would repay any Twitter user double the value of Bitcoin they sent to particular wallets as part of the COVID-19 relief effort (Anderson and Saleh 2021, p. 8). The tweets then ensued the sharing of malicious links using many cryptocurrency companies. However, the website that posted the links were taken down by Twitter shortly after the tweets were posted. Although, before this. Over US$110,000 had been deposited on one of the cryptocurrency wallets as 320 transactions had already occurred. Consequently, full message history data from eight accounts that were non-verified were also attained. Security researchers depict concerns that the social engineering technique used to execute this attack could also possibly influence the use of social media in critical online discussions (Debb 2021, p. 583). Security experts also believe that the perpetrators who ran the scam used the “smash and grab” operation as they were aware that the intrusion into the high-profile account would be quickly closed and therefore targeted to scam only a small fraction of the millions of followers that were following these high-profile Twitter accounts. Numerous Bitcoin wallets had been listed at these websites, the first one having received 12 bitcoins from more than 320 transactions valued at over US$118,000 and had approximately US$61,000 removed from it (Gheewala and Patel 2018, p. 80). However, the second account had amounts in only thousands of dollars as Twitter took measures to stop these postings. The compromised accounts repeatedly posted scam messages, even after the messages were deleted. The tweets were sent using the Twitter Web app, and others were sent from IP addresses linked to various countries. The phrases involved in the scam were tweeted over 3000 times in four hours before Twitter took steps to stop the scam (Gheewala and Patel 2018, p. 80). By 21:45, Twitter gave out a statement saying that they were aware of the security issue affecting accounts on Twitter and that they were taking measures to fix it. In an attempt to fix the problem, Twitter disabled given accounts’ ability to tweet or reset their passwords. Three perpetrators were charged for this attack; Nima Fazeli, 22, from Orlando, Florida, Mason Sheppard, 19 from the United Kingdom and the third a Juvenile, their key motive of the attack is to gain money.
Stages of the Attack
| Stages of the Twitter Scam Attack | |
| Attackers used the phone spear phishing attack on a small number of Twitter’s employees. | |
| Successful attack made attackers to gain access to Twitter’s internal network and employee credentials | |
| Attackers used the employee’s credentials to access Twitter’s internal systems and gain information about the organization’s processes. | |
| Attackers targeted additional employees with access to Twitter Account and Support tools | |
| Attackers used credentials of these employees to access the Twitter Support tools. | |
| Hackers gained access to 130 Twitter Accounts ultimately tweeting from 45 accounts, accessing the DM inbox of 36 accounts and downloading Twitter Data of 7 accounts | |
| Attackers used the “smash & grab” operation targeting a small fraction of millions of followers of the high-profile accounts. | |
| Hackers were able to get more than US$110,000 deposited on their cryptocurrency wallets as 320 transactions occurred from the attack. | |
| Within a span of 4 hours after the attack, Twitter was able to take measures to stop the scam and halt the Bitcoin operations. | |
The attackers used the social engineering scheme to cause the attack. In this context, social engineering can be regarded as intentionally manipulating people into performing particular actions and disclosing confidential information (Debb 2021, p. 582). From the Twitter attack, the attackers followed the social engineering framework to execute the attack.
Social Engineering Framework
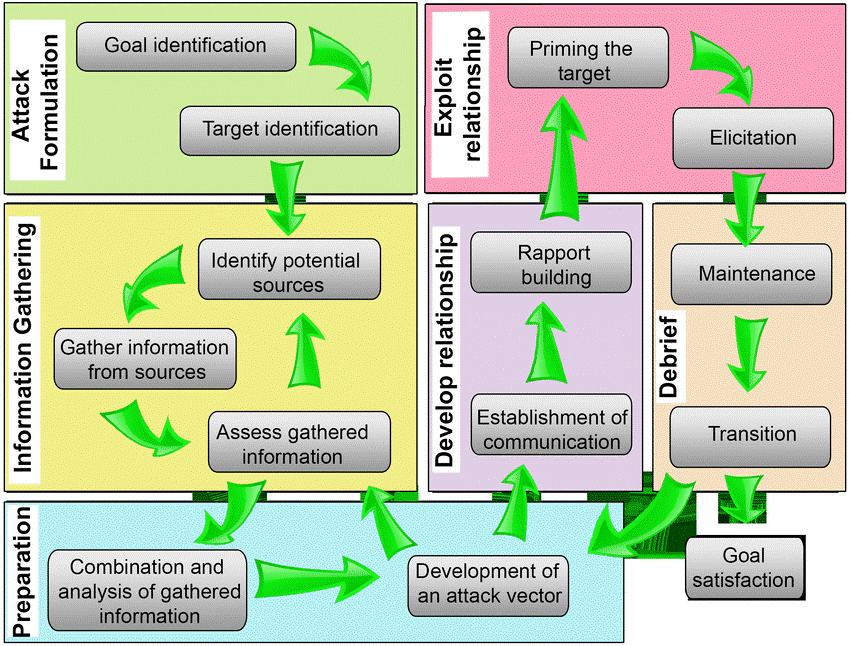
https://www.researchgate.net/figure/Social-Engineering-Attack-Framework_fig7_335884231
From the Twitter Scam attack, it is evident that the attackers followed the social engineering framework steps: attack formulation, information gathering, preparation of the attack, exploit relationship, developed a relationship, debriefed, and later satisfied their goal (Indrajit 2017, p.7).
- Attack formulation
The attackers identified their goal as gaining money (Mann 2017, p. 10). After recognizing this goal, the attackers identified their target as Twitter users who would fall into the scam of having their money doubled from the Bitcoin operations.
- Information gathering
The attackers used their social engineering skills and knowledge on phone sphere phishing attacks to access Twitter’s internal systems and get information about the organization’s processes (Indrajit 2017, p.7). The attackers identified potential sources like Twitter’s employees with access to Twitter’s accounts and support tools (Indrajit 2017, p.8). They then gathered information from sources by using their credentials to access Twitter support tools, and with this, they were able to gain access to high-profile Twitter accounts.
- Preparation
It is difficult to determine the time taken by these three individuals to gain Twitter insider tools, combine and analyze the information obtained about the organization’s internal system and processes and develop an attack strategy (Junger et al., 2017, p. 77).
- Develop Relationship
For the Twitter Scam attack, the attackers seemed to have developed a relationship with Twitter employees, with access to the company’s internal systems and support tools. After building rapport with this staff, they established communication with them to get ways of lodging the attack vector they had created for the organization (Indrajit 2017,p.6).
- Exploit Relationships
After establishing a good relationship with the staff in charge of the company’s support tools, the attackers lodged the phone spear-phishing attack using the staff’s devices.
- Debrief
Hackers gained access to 130 Twitter Accounts, ultimately tweeting from 45 accounts, accessing the DM inbox of 36 accounts and Downloading Twitter Data of 7 accounts (Junger et al., 2017, p. 77).
- Goal Satisfaction
Hackers could get more than US$110,000 deposited on their cryptocurrency wallets as 320 transactions occurred from the attack.
To execute the Twitter Bitcoin Scam, the attackers used the psychological tactic of emotional manipulation to attack the victims. Emotional manipulation happens when a manipulative individual employs exploitative and dishonest strategies to control and victimize the victim (Conteh and Royer 2016, p.10). In this case, the perpetrators told their target audience, Twitter users, to send Bitcoin currency to a particular cryptocurrency wallet, promising that the money would be doubled and returned as a charity gesture (Conteh and Royer 2016, p.10). The psychological manipulation was on the doubling of the money. The majority of the Twitter users with bitcoins fell for this as they took part in the transactions with the hope that they would get twice as much as they had invested, not knowing that this was merely a scam.
Impact Analysis
Through the social engineering techniques, the Twitter Bitcoin Scammers were able to target 130 Twitter accounts, ultimately tweeting from 45 of these accounts, accessing 36 DM inbox of these accounts and downloading the Twitter Data of 7 of these accounts. These made them see some private information of Twitter users (Couce-Vieira et al., 2020, p. 358). For instance, the attackers were able to view personal information in the accounts taken over during the attack, including the phone numbers and email addresses of the Twitter users, which are displayed on the company’s internal support tools (Zhongming et al., 2020, p. 8). Additional information to risks of data security, the safety of the private information of the Twitter users and a threat on what these Twitter users were discussing on their DMs were also viewed by the hackers (Couce-Vieira et al., 2020, p. 359). This resulted in the privacy of Twitter users. The scammers exploited human vulnerabilities by misleading some of the organization’s employees to gain access to the organization’s internal systems.
Risk Data
| Related Threats/Vulnerabilities | Main Risks of the Twitter Bitcoin Scam | Impacts of the Twitter Bitcoin Scam |
| Human Vulnerabilities | Cryptocurrency Organizations | Data Insecurity |
| High-profile Twitter accounts | The intrusion of the user’s private information | |
| Twitter users following the high-profile accounts | Lack of Safety of the user’s information |
Overall, the Twitter Bitcoin Scam significantly impacted both the data systems and victims (Witman and Mackelprang 2022, p. 2). The victims’ intrusion of their private information and data puts them at risk of having some of their confidential information leaked to the unintended audience. External corruption of the user’s data would expose the victims to reputational harm, brand erosion and trust degradation (Witman and Mackelprang 2022, p. 2). Apart from that, other victims of the attack, the Twitter users, also suffered a financial consequence as some of them ended up losing their bitcoins through the scam. Besides, the Scam also affected Twitter Company, as it made people question the organization’s security systems following the attack. It also made the data security of the company questionable.
Moreover, with the data breach that Twitter faced, the company was at risk of being sued by the people whose information was exposed and asked to pay for credit monitoring for the consumers whose information had been exposed (Murko and Vrhovec 2019, p.5). In addition, the company also incurred costs such as reinforcing the loopholes of the data breach. Consequently, the company also lost some of its clients severely affected by the scam.
Other than the scam’s impact on the victims, it also negatively impacted the organization’s data systems. Unauthorized access to the organization’s systems ended up damaging the system, software and data stored in the system due to unprofessional way of access into these systems (Murko and Vrhovec 2019, p.6). Interruptions of these systems made the organization work on ways of reinforcing any loophole, including the human vulnerabilities that may result in future attacks of the company’s data system.
The Twitter Bitcoin Scam also had psychological and physical impacts on the victims. Psychologically, the Twitter Bitcoin Scam made victims feel out of control of the situation, making them experience feelings of anxiety and become demoralized. These psychological impacts ensuing a cyber-crime can range from mild to severe attacks resulting in symptoms of panic attacks, anxiety, depression, posttraumatic stress and suicide (Navarro 2019, p. 7). Apart from the psychological effects, the victims of the Twitter Bitcoin Scam are bound to experience physical impacts such as the increase in weight and obesity due to emotional eating.
Recommended Approach and Conclusion
From my investigation of the Twitter Bitcoin Scam, the main risks identified are those pertaining to data insecurity, intrusion of people’s personal information and lack of safety of the user’s information (Payne et al., 2021, p. 135). This may result in reputational harm, brand erosion, and degradation of trust if the information obtained by the perpetrators in the high-profiled Twitter accounts contains sensitive data. However, to address such risks and prevent future occurrence of a similar incidence, Twitter should consider using the humanistic psychological theory-based approach to help prevent re-occurrence of the issue in future. The humanistic approach suggests that effective interactions and human relationships are vital pillars of success in an organization (Perols and Murthy 2021, p. 76). Being that the Twitter Bitcoin Scammers used human vulnerabilities to conduct a phone sphere phishing attack and gain access to the internal system of the organization and attain information about the company’s operation processes, it is vital to use the humanistic approach to make staff aware of how crucial it is to work together with the organization to fight cybercrimes. The humanistic approach is rooted in empathy and encouragement (Purswell 2019, p. 357). In this case, the humanistic approach will help Twitter feel empathetic to staff used to help the attackers lodge the attack on the organization.
On the other hand, the humanistic approach would also encourage their staff to take serious responsibility for keeping the company’s information safe. Through the humanistic approach, Twitter will share precautionary steps with their staff to help them understand ways of protecting their organization from cyber-attacks (Yurtseven et al.,2021, p. 385). This would include teaching them ways of spotting suspicious emails, abiding by policies that guard sensitive business information, maintaining company physical security, and keeping their personal devices away from essential software containing the company’s critical data. Besides, through the humanistic approach, it would be easy for Twitter to teach its staff how to protect the company’s private information and not disclose it to anyone unless necessary (Purswell 2019, p. 358). Moreover, the organization can also use this approach to urge staff to verify their source of information if asked to input sensitive data on their website.
Apart from the humanistic approach, the other approach which can be used by Twitter to reduce the risk of re-occurrence of the issue and to create change is the cognitive approach. The cognitive approach is a type of theory-based psychological approach that is used in business to help staff understand the entrepreneurial behavior that they ought to depict while doing business, the steps that they ought to follow if they are to attain any success in business and ways that they can work and protect their business from attacks that may result to business failure (Sumner and Yuan 2019, p. 75). In this context, the cognitive approach can be used by Twitter to help create change and minimize risks of future cyber-attacks. To effectively use the approach, Twitter will tap on the learning aspect of the cognitive approach (Vrij et al., 2017, p. 16). When applied in business, the learning aspect in the cognitive approach would help an organization expand its staff knowledge to gain new expertise and skills. To facilitate this approach, a business will encourage staff to learn steadily by giving them tools that would help them facilitate learning.
With the cognitive approach, Twitter can learn ways of reinforcing cyber security in their organizations. This is through making them aware of ways of; controlling unauthorized access to company data, setting a password policy and enforcing it, ensuring the security of mobile devices and making them knowledgeable of ways that they can avoid becoming victims of a phishing email (Vrij et al., 2017, p. 15).
In conclusion, as bitcoins’ popularity rises, so has there been an increase in social engineering crimes such as phishing. These scammers tend to use deceit and psychological manipulation to control the key information relating to the user accounts. These scams, similar to the Twitter Bitcoin scam, tend to condition victims to think that they are dealing with trusted groups such as a well-known business, government agency, or celebrity. These scammers use various techniques to gain the trust of a potential victim to reveal vital information or send money to the digital wallet of the scammer. In the Twitter Bitcoin Scam, Scammers used Twitter accounts of high profile individuals after gaining access to their Twitter platforms using the social engineering skills and knowledge of phone spear-phishing attacks to gain access into Twitter’s internal support systems. The attack made Twitter’s data security and safety of users’ information on the platform questionable. With the negative impact that emanated from the attack, the organization should however work on preventing this attack in the future, through training its staff to protect the organization from cybersecurity attacks.
References
Anderson, C. and Saleh, T., 2021. Investigating cyber-attacks using domain and DNS data. Network Security, 2021(3), pp.6-8.
Breda, F., Barbosa, H. and Morais, T., 2017, March. Social engineering and cyber security. In International Technology, Education and Development Conference (Vol. 3, No. 3, pp. 106-108).
Couce-Vieira, A., Insua, D.R. and Kosgodagan, A., 2020. Assessing and forecasting cybersecurity impacts. Decision Analysis, 17(4), pp.356-374.
Conteh, N.Y. and Royer, M.D., 2016. The rise in cybercrime and the dynamics of exploiting the human vulnerability factor. International Journal of Computer (IJC), 20(1), pp.1-12.
Debb, S.M., 2021. Keeping the Human in the Loop: Awareness and Recognition of Cybersecurity Within Cyberpsychology. Cyberpsychology, Behavior, and Social Networking, 24(9), pp.581-583.
Gheewala, S. and Patel, R., 2018, February. Machine learning based Twitter Spam account detection: a review. In 2018 Second International Conference on Computing Methodologies and Communication (ICCMC) (pp. 79-84). IEEE.
Indrajit, R.E., 2017. Social engineering framework: Understanding the deception approach to human element of security. International Journal of Computer Science Issues (IJCSI), 14(2), p.8.
Junger, M., Montoya, L. and Overink, F.J., 2017. Priming and warnings are not effective to prevent social engineering attacks. Computers in human behavior, 66, pp.75-87.
Mann, I., 2017. Hacking the human: social engineering techniques and security countermeasures. Routledge.
Murko, A. and Vrhovec, S.L., 2019, November. Bitcoin adoption: Scams and anonymity may not matter but trust into Bitcoin security does. In Proceedings of the Third Central European Cybersecurity Conference (pp. 1-6).
Navarro, R.R., 2019. Preventative fraud measures for cryptocurrency exchanges: mitigating the risk of cryptocurrency scams (Doctoral dissertation, Utica College).
Payne, B.K., He, W., Wang, C., Wittkower, D.E. and Wu, H., 2021. Cybersecurity, technology, and society: Developing an interdisciplinary, open, general education cybersecurity course. Journal of Information Systems Education, 32(2), pp.134-149.
Perols, R.R. and Murthy, U.S., 2021. The Impact of Cybersecurity Risk Management Examinations and Cybersecurity Incidents on Investor Perceptions and Decisions. Auditing: A Journal of Practice & Theory, 40(1), pp.73-89.
Purswell, K.E., 2019. Humanistic Learning Theory in Counselor Education. Professional Counselor, 9(4), pp.358-368.
Sumner, A. and Yuan, X., 2019, April. Mitigating phishing attacks: an overview. In Proceedings of the 2019 ACM Southeast Conference (pp. 72-77).
Vrij, A., Fisher, R.P. and Blank, H., 2017. A cognitive approach to lie detection: A meta‐analysis. Legal and Criminological Psychology, 22(1), pp.1-21.
Wiederhold, B.K., 2014. The role of psychology in enhancing cybersecurity. Cyberpsychology, Behavior, and Social Networking, 17(3), pp.131-132.
Witman, P.D. and Mackelprang, S., 2022. The 2020 Twitter Hack–So Many Lessons to Be Learned. Journal of Cybersecurity Education, Research and Practice, 2021(2), p.2.
Yurtseven, İ., Bagriyanik, S. and Ayvaz, S., 2021, September. A Review of Spam Detection in Social Media. In 2021 6th International Conference on Computer Science and Engineering (UBMK) (pp. 383-388). IEEE.
Zhongming, Z., Linong, L., Xiaona, Y., Wangqiang, Z. and Wei, L., 2020. Insider Threat at Twitter Is a Risk to Everyone.
 write
write