Consensus-Based Policies
Mechanisms of Governance of Comprehensive Policies
The security information policy is the initial defence against highly persistent threats. Policies play a critical function in defining the postures of security and key restrictions on the access granted to Akwaaba Health and wellness centre. This is because there exists no solid replacement for having security information policies that are strong (Henry, 2020). The other issue that is more crucial is the governance framework since the planned eradication and repair defines components that are instrumental when fighting the loss against the assault of advanced threats that have become persistent to Akwaaba Health and wellness centre. Therefore, the two selected variables in this paper are essential in identifying solutions that are long-term in finding a solution to the problems.
Threat and Correlation Management
The threats within Akwaaba Health and wellness centre need to be identified early since the launch of the compromise is usually done with real-time correlation methods. (Henry, 2020) Therefore, this critical concept exploits any form of global information that protects the Akwaaba health and wellness centre environment from more persistent attacks.
Capabilities of Decision-Making Support to Solutions
Akwaaba Health and wellness centre need to determine the origin of the advanced persistent threats (Austin, 2020). This is because the data reports imply that the Akwaba Health and wellness centre is under the target; it is sensible for the institution to remain vigilant and look out for all possible connections within which it is located.
Describe how your solution meets the following.
Cybersecurity automation for Akwaaba Health and wellness centre is improved through automation. To quickly adapt to the scale that keeps developing steadily and the dangers of intricacy, which are also present, associations must adopt risk that compels the design of connection. This is because it guarantees that all the conceivable passage for Akwaaba Health and wellness centre has focused on the critical dangers covered by the institutions’ framework securities (Austin, 2020). However, it is also another function in trying to give access to the assurance that is proactive. Also, this is because it has received confrontation with measures that keep expanding steadily on the dangers associated with the Akwaaba health and wellness centre data. Therefore, they need to ensure that the data continues to develop to guard the Akwaaba Health and wellness centre by aggregating the data in danger.
Using Security that is Highly Advanced and Updated
The concept of relationship logging is extraordinary for the incentives used while trying to identify interruptions to safety. Therefore, further developing the Akwaaba Health and wellness centre framework will enhance the interface’s focus while investigating the crime scene network (Austin, 2020). The procedures of connecting occasions are created to perceive events and offer them a significant meaning on the measures and controls of appoint fitting. Therefore, the process is instrumental in spotlighting the anticipation instead of the reaction. However, there exist multiple occasions of methods of collection that are easily accessible for use in designs of danger relations.
The Security Standard Tools and Environment and Infrastructure play an instrumental role in implementing security tools that are standards within the industry and the environment or infrastructures of Akwaaba Health and wellness centre that are estimated widely with the aid of the techniques and means of the number of the device. The arrangements of the “Network protection Correlation and Automation (CSCA)” are essential in how they are associated and incorporated into the information on digital platforms that is instrumental in developing other emergencies and recognition (Alexander & Wang, 2019). In return, this offers a deceivability that is full to the assault surface of Akwaaba Health and wellness centre while still having the digital assaults foiled before causing any harm to the organization. Therefore, getting to know the type of dangers that are dynamic to Akwaaba Health and wellness centre plays a critical role in creating a centre for digital groups of supervisory which is involved in fortifying the protection of the law by developing further the associated settings of the security which are exceptional.
C.
The collection of evidence for digital analysis and forensics. The processing and interpretation of forensics are the solid processes involved in analyzing and collecting the evidence damning from crime scenes. This involves; the genetic forensic apparatus, solutions and kits that enable the evidence analysis collected when investigating the criminal investigations linked to Akwaaba Health and wellness centre (Ahmed & Roussev, 2022). Also, how the gathered digital evidence is handled is identified as the equipment acquisition with the initial transformation copy (ESI) with the ultimate goal of ensuring that the digital proof is protected. Also, the original identity copy is expected to be protected when engaging in forensics.
Forensics refers to inquiries that are protracted into the causes, course, consequences and perpetrators regarding a violation or an attack towards the standards of Akwaaba Health and wellness centre. During tort proceedings, forensics methods are directly linked to the evidence available for jury hearings (Ahmed & Roussev, 2022). The digital evidence can be acquired from multiple sources within the Akwaaba Health and wellness centre. This includes; sensors of images, cell phones, Flash drives, devices used for storage, Turntables, ISPs and cloud machines that present other vital sources that are more prevalent.
Confidentiality implementation. The management of threats and confidentiality are identified as a hybrid of host levels of organization and hubs on data streams over the general organization objective. For Akwaaba Health and wellness centre IIG, the hubs involved in the host are uniform. At the same time, their connections attend shift according to verification, types of query on DNS and streams of networks (Stapleton, 2021). The selected occasions, therefore, hold a significant amount of data regarding the organization’s exercises. Also, the IIG edge components that are multidimensional are taken additionally in addition to catching the data that is equally intelligent. It is therefore proposed that a clever edge entails using a GNN that is improved in using the critical instrument of consideration in consolidating ultimately the highlight of the edge involved in portraying IIG “NIST.”
D
To ensure that the harmful activities are identified among the unusual and typical endpoint of the actions of Akwaaba Health and wellness centre, it is urgent to undertake the settings. The information which is collected across the endpoints of the association offers security circumstances that are more specific while empowering the Akwaaba Health and wellness centre associations in sorting out the malevolent hints which are easily dispersed across multiple endpoints in uncovering the Akwaaba Health and wellness centre digital assault (Perols & Murthy, 2020). Also, putting into consideration that endpoints provide an entry point that is more typical in trying to execute a more horizontal development, the information of the endpoint is, therefore, able to have assaults uncovered in a youthful stage, and before causing any harm, it dramatically reduces the break expenses.
E
Ideally, multiple security systems are involved in providing random and various warnings. More often majority are wrong and lack context. Therefore, the Akwaaba Health and wellness centre security personnel need to conduct a manual investigation to ensure that the alerts generated by the solution are alerted (Stuart et al., 2021). This is linked to the fact that prolonged procedures play an instrumental role in preventing security experts who get to the basics of the fundamental concern of whether cyberattacks exist. Therefore, it is necessary to speed up critical responses and detection. At the same time, the breach breadth and cost are significantly reduced, as the systems used will ensure that the investigations are automated while trying to validate the process.
F
The “post-implementation “for Akwaaba Health and wellness centre goes through its primary stages. The first step is identifying the threat since it has created eight strategies for identifying multiple procedures for advancing various APT. The approval and commitment of the selected techniques use traffic that is more genuine in making a significant commitment to the assortment of the flow and ebb exploration (Mallick et al., 2023). The second step is connection alert, through which a structure of the relationships has a great intention of interfacing with the primary yields of where the strategies are located. It also entails the Akwaaba Health and wellness centre’s plans of recognizing the interconnected alarms that align with the APT solitary situation. The third step is the expectation of the attack in which a forecast module based on AI has been proposed, mainly dependent on the system yield of the Akwaaba health and wellness centre relationship (Mallick et al., 2023). Therefore, it also needs to be fully utilized by the security groups of Akwaaba Health and wellness centre to decide on the possibility of early caution in fostering a general assault on APT. The management of threats and correlations is subject to tentative assessments in which the introduced framework can foresee APT within the initial strides in making a precision forecast of 84.8%.
G
According to this methodology, scientists have succeeded in designing a structure that can detect the malware of APT. This tends to have a general focus for the framework at the initial infiltration phase towards the network. Through the structure, the open source creates a “Security Information and Event Management (SIEM)”, which is ideally utilized in recognizing the practice that is recommended on “Distributed Denial of Service (DDOS).” The accomplishment is achieved by investigating the Akwaaba Health and wellness centre files and the communication processes (MacGregor & Haasbeek, 2021). The identified research easily rotates around the capacity ideas of having to snare into identifying the malware that has a zero-day. The Ambush instrument is used as it is an open-source that avoidance the framework of intrusion “HIPS.” The framework proposed for Akwaaba Health and wellness centre can notice all the calls of the function, which has to work with the framework in distinguishing the solid conduct of any eminent behaviour that is evil in promoting the reliable discovery of the malware multi-day.
While investigating the Akwaaba health and wellness centre technique, it is proposed that it is essential to deal with an assault that is multi-day in distinguishing how the OS is utilized. This is because the hooking is required to demonstrate security investigators that have become helpful to the Akwaaba Health and wellness centre investigators to ensure that APT is recognized. Also, apart from the dramatic structure that has been propped, it is equally essential to utilize the DOS recognition assault on services of the system, which may fail to work on the APT malware (MacGregor & Haasbeek, 2021). This is because it is identified as a digital hoodlum on the skills incorporated in muddling intra-calls at work. Also, it is easier for the structure to sometimes yield positive alerts that are bogus on every call capacity, which is being looked into by the open source, which is based on the avoidance of the framework of interruption “HIPS.”
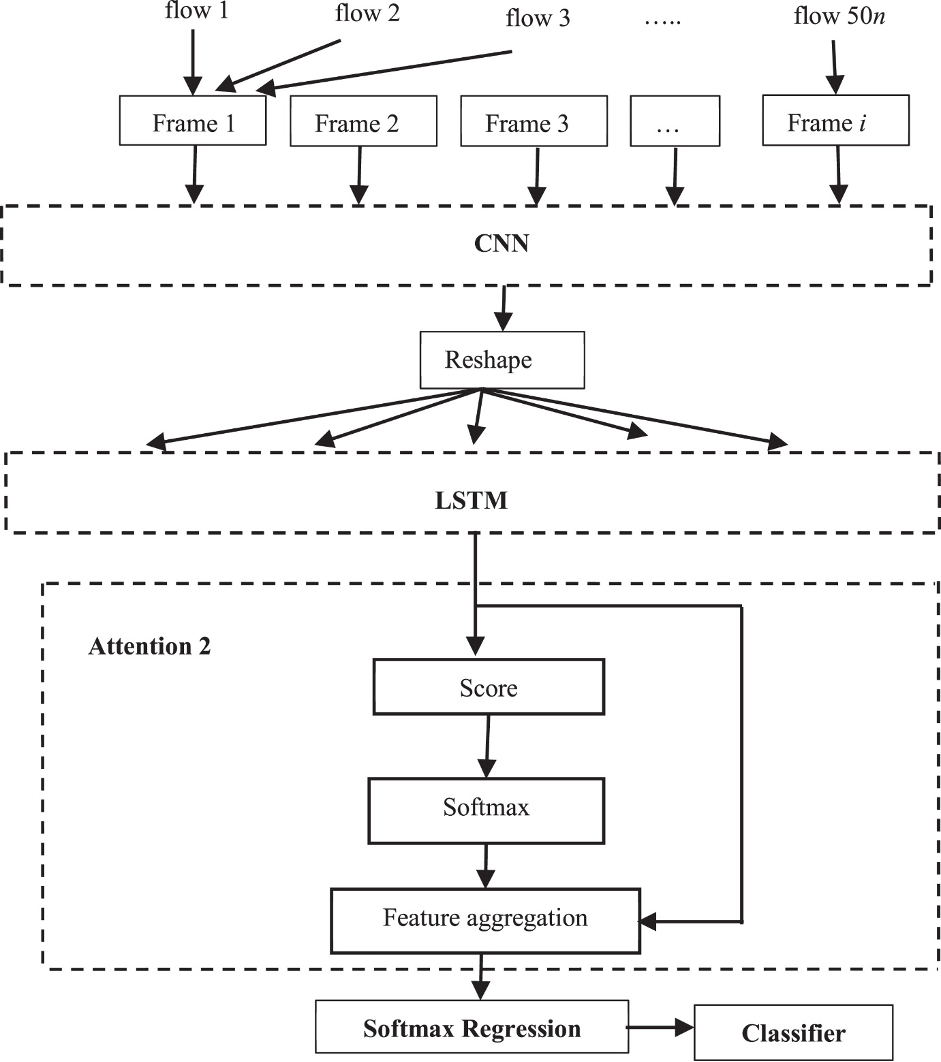
APT Attack Flow: (Rothwell & Kinsey, 2019)
H
Access Control
Putting into place access controlled to the Akwaaba Health and wellness centre information is instrumental in protecting the availability and integrity of confidential information. Unauthorized users have limited access from having to use, retrieve, and modify the data using restricted access (Shires, 2022). The threats, risks and vulnerabilities that Akwaaba Health and wellness centre identified can define control measures.
Authentication
Authentication involves providing the user’s identity before they access the Akwaaba Health and wellness centre system. This is the second step in the control process of gratin in access. Therefore, it is easier for the user to be authenticated with the following three techniques (Shires, 2022). The approach in which the user is aware such as passwords, phrases and code passes. What the user possesses, such as ATM cards, smart cards and tokens. Finally, the user needs to use what they are interested in, such as fingerprints, scanning their voices, and scanning their retina.
Authorization
Normally it is to the advantage of the client’s entrance on what they can do or not within the Akwaaba Health and wellness centre security framework or application. In this third stage of controlled access, for example, the approval may confine to one client more information in which advantages are seen while other clients can view, change and approve reports (Lanza, 2022). Therefore, approval needs to be identified on the essential access advantage in which clients must perform their functions. For example, the Akwaaba Health and wellness centre doctors will be able to put in more requests and access patients’ data more persistently than a volunteer or solitary unit of nursing who work within the data section that needs the approval to access the data for patients.
I
Data security strategy is identified as the primary line of offering protection on the highest level of data perseverance. The approach is involved in deciding on the association’s entrance on the limitations on access and the act of security. There exists no trade for security strategies with solid data. The other more cortical issue is the administration system used in the Akwaaba Health and wellness centre (Schulz, 2019). It needs to have an arranged destruction fix on the parts that are fundamental in battling against any form of misfortune from the highest relentless levels of dangerous attacks.
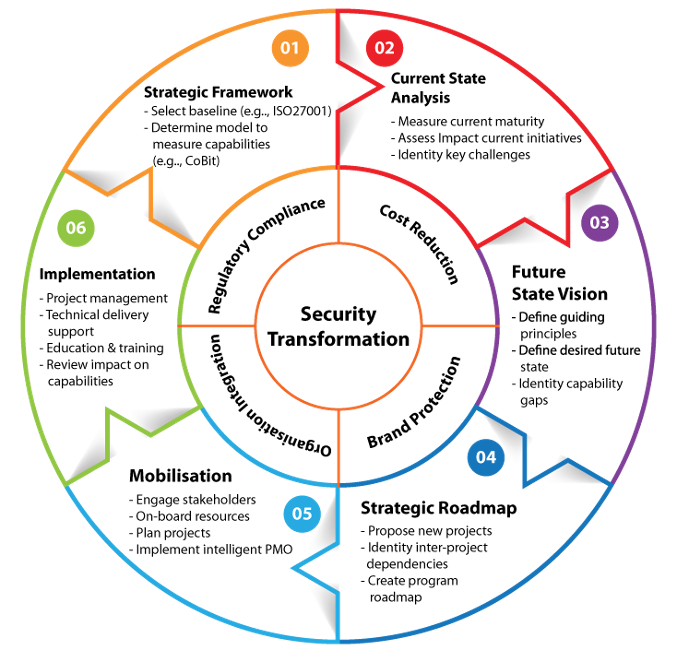
Security Policy Strategy: (McGiffen, 2022)
J: References
Ahmed, I., & Roussev, V. (2022). Analysis of Cloud Digital evidence. Security, Privacy, and Digital Forensics in the Cloud, 301–319. https://doi.org/10.1002/9781119053385.ch15
Alexander, C. A., & Wang, L. (2019). Cybersecurity, information assurance, and big data based on Blockchain. 2019 SoutheastCon. https://doi.org/10.1109/southeastcon42311.2019.9020582
Austin, G. (2020). Twelve dilemmas of reform in cyber security education. Cyber Security Education, 208–221. https://doi.org/10.4324/9780367822576-13
Henry, A. P. (2020). Mastering the Cyber Security Skills Crisis. Cyber Security Education, 29–54. https://doi.org/10.4324/9780367822576-2
Lanza, C. (2022). Semantic tools for cybersecurity. Semantic Control for the Cybersecurity Domain, 105–126. https://doi.org/10.1201/9781003281450-5
McGiffen, M. (2022). Encryption in transit using Transport Layer Security. Pro Encryption in SQL Server 2022, 259–268. https://doi.org/10.1007/978-1-4842-8664-7_18
MacGregor, A., & Haasbeek, J. (2021). Automation of SPCC plan preparation, implementation, and maintenance. Proceedings of the Water Environment Federation, 2006(13), 103–110. https://doi.org/10.2175/193864706783710857
Mallick, A., Bag, S., & Aich, P. (2023). The changing role of Human Resource Management in the new normal: A post-pandemic paradigm change. Human Resource Management in a Post-Epidemic Global Environment, 1–15. https://doi.org/10.1201/9781003314844-1
Perols, R., & Murthy, U. S. (2020). The impact of cybersecurity risk management examinations and cybersecurity incidents on investor perceptions. SSRN Electronic Journal. https://doi.org/10.2139/ssrn.3112872
Rothwell, W. “B., & Kinsey, D. (2019). Linux Essentials for Cybersecurity. Pearson Education, Inc.
Schulz, G. (2019). Data Infrastructure Availability, data protection, security, and strategy. Data Infrastructure Management, 87–122. https://doi.org/10.1201/9780429264955-6
Shires, J. (2022). Information controls. The Politics of Cybersecurity in the Middle East, 155–200. https://doi.org/10.1093/oso/9780197619964.003.0006
Stapleton, J. J. (2021). Security without obscurity. https://doi.org/10.1201/b16885
Stuart, H., Arboleda-Flórez, J., & Sartorius, N. (2021). Paradigm 3: Stigma reduction requires well-developed plans. Oxford Medicine Online. https://doi.org/10.1093/med/9780199797639.003.0004
 write
write