Summary
The organization selected for this project is 3Net Enterprises. The 3Net Enterprise is a global provider of shipboard networking services and ashore data centers. The company also provides other services such as mobile data security. The newly employed Chief Information Officer (CIO) for 3Net Enterprises was expected to implement a data security solution within the company’s transient data centers, which had recently shown signs of vulnerability. Besides the quick data centers, the data security solution was also implemented to secure the afloat units that depend on 3Net Enterprises’ services worldwide. All these facilities depend on 3Net Enterprises for secure internet and data storage and communication services. Some information system security concerns identified with the 3Net Enterprises include the threat of computer viruses or ransomware. Another problem identified with the 3Net Enterprises information system is the threat of being corrupted by external computer devices. The final problem is related to the danger of malware due to several connections. The interest of the newly employed Chief Information Officer (CIO) for 3Net Enterprises was to help the organization’s management to create an information security policy that will ensure that the company’s transient data centers and afloat unit data are safeguarded from the threats of ransomware, malware, and cyberattacks. In this regard, one of the leading solutions to these information system threats identified includes the use of Forescout eyesight hardware that is aimed at helping the 3Net Enterprises to protect its sensitive data by limiting access and enabling the CIO to monitor and mitigate all the risks persistently. The second program used to secure the 3Net Enterprises was Forescout eyeInspect. This program helped the organization achieve the required in-depth visibility for its OT/ICS networks, which allowed the CIO to be timely and effectively manage all the cyber threats.
Implementation Plan
The implementation process was performed in three steps, including conducting an environmental risk assessment. All customers expected the 3Net Enterprises’ CIO to inform them about any security threat or risk they are likely to encounter when procuring the firm’s data security, communication, and mobile data security services. This also applies to any organization’s facility that can be contracted for data security services. In case they are hired, the company IT experts must be called upon regularly to conduct risks and threat assessments to such facilities. Therefore, the 3Net Enterprises’ CIO had to ensure that duty of care, concern and due diligence was taken for employees and customers. It was also the responsibility of the company’s CIO to outline any facility with information security concerns to ensure that clients were not exposed to any risk that might have been avoided. Moreover, such security concerns were also supposed to be discussed during the pre-operation or inspection process by the 3Net Enterprises” IT experts to ensure that all security measures are considered. However, certain areas or locations with particular concerns and serious challenges were given adequate information security services to ensure all loopholes were sealed.
The second step was to purchase the Forescout hardware and servers to protect 3Net’s3Net’s sensitive data and help the firm to monitor and mitigate all the data security risks. The 3Net developed and implemented the Forescout information security measures that enabled it to seal all the security loopholes that could cause all the firm’s data centres and other 3Net Enterprises locations to lose sensitized data such as financial and security data (Christiawan, 2015). Terrorism has become rampant in the contemporary world, and giving terrorists an opportunity to access the organization’s security data is risky for the organization’s survival. In this regard, improving data security was vital for the newly hired CIO. Installing the Forescout hardware and servers helped the 3Net apply the risk management approach due to the size of the firm and the level of information security needed (Christiawan, 2015). The system allowed the organization to consider all elements of data security and measures and prioritized them as one of the most critical forms of Enterprise Risk Management programs for the organization’s benefit. This required shipping the 3Net Enterprises IT Staff to all the ports of call and arranged contracts with the onsite engineering services to install Forescout hardware and servers on all vessels arriving at the desired information system security level. Moreover, the 3Net Enterprises IT Staff also provided adequate training to the Forescout installers concerning the best way to install these devices, which helped the firm enhance its information system security levels.
The final step was configuring the Forescout hardware and servers to ensure they were in learning mode. Moreover, the Runbooks were also created and implemented to provide the administrators with insights regarding the data security risk assessment. The entire process helped the 3Net’s IT team to protect all computers with passwords to limit access. In this regard, no unauthorized person was granted access to any computer unless the company’s CIO or management permitted them. In addition, all the personnel in charge of any computer system switched off the devices upon work closure to avoid unauthorized access.
Moreover, specific security measures of operating systems were used to ensure that only the authorized individuals had access to the 3Net’s computer resources. This kind of information security measure could sense and verify everyone’s identity to limit access. It could also record correctly and keep the memory for a long time, offering authentication. In this way, 3Net’s computer system used strong passwords to limit access by unauthorized persons. The designed information security system also helped 3Net to restrict access to its Wi-Fi and ICT services. Access to 3Net’s Wi-Fi was only limited to the workers and customers. However, these services could also be extended to third parties during certain events and other occasions. Notably, the designed information system security provided the 3Net’s ICT department with an adequate capacity to detect any device that might pose a security threat to the company’s ICT facilities and get rid of them as quickly as possible. Finally, the newly designed information security framework helped 3Net to restrict external access to its ICT resources. The 3Net’s ICT resources and computer systems were encrypted end-to-end to avoid external access. Also, the inbound communication through the company’s website was strongly encrypted to ensure that only people who were authorized by the company management used these resources.
Review of Other Work
- Security Threats Management for Cyber-Physical System
A Threat Breakdown Structure approach was proposed for dealing with the threats of CPS as recently portrayed by Ogut et al. (2010). Countermeasures were proposed by the threat grid strategy and characterized. Threat esteems presented in a data security management system, and quantitative evaluation was directed for detailed threat appraisal. The quantitative assessment demonstrated that the proposed countermeasures could somewhat reduce the threat. Ogut et al. (2010) looked into the best in class rehearses in cybersecurity threat appraisal of the SCADA systems utilizing point, application space, phases of threat management, threat management ideas, sway estimation, and wellsprings of probabilistic information, evaluation, and instrument support.
Source: Alguliyev et al., 2018.
Despite an extensive number of threat appraisal strategies for SCADA systems, the requirement for a specific design covering all phases of the threat management procedure is absent (Ogut et al., 2010). This enables directors to decide on the present dimension of security and encourages them select security components. Nonetheless, the likelihood added to each harm class would evaluate further the threat related to data systems. Ogut et al. (2010) argue that cyberattacks on organizations’ information systems and data have increased. Therefore, new cybersecurity approaches must reduce such risks and threats (Ogut et al., 2010). One of the industries that experience high incidents of cyberattacks includes healthcare firms because almost 23% of these firms received various cyberattacks during 2015 alone. This means that healthcare data has been a valuable target for cybercriminals. Some of the sensitive information that cybercriminals are interested in such organizations includes patients’ medical history, credit card details, and insurance details. Therefore, for the 3 Net Enterprise to outmaneuver the cybercriminals, the organization had to apply effective IT risk and threats management strategies because these criminals are also sophisticated and more intelligent. Ogut et al. (2010) gave an outline of smart matrix security, including the arrangement of controls, communication, and physical system parts required to provide a specific digital-physical condition. There are different works that Ogut et al. (2010) focus on recognizing computer assaults which change the conduct of the focused-on control systems by understanding the outcomes of the assault for threat evaluation. Ogut et al. (2010) proposed a quantitative threat evaluation display that centers on the CPS running conditions and ascertains threats continuously by utilizing clients’ reactions to threats on specific occasions.
- Digital Security in Smart Grid
Different works focus on the security of the intelligent lattice. Zhou and Zhang (2017) discussed various bundle methodologies for security threat management concerning the intelligent grid. Threat evaluation systems proposed included threat and defenselessness displaying plans which help distinguish and sort threats, examine their effects, and organize them. Zhou and Zhang (2017) reviewed the threat appraisal strategies, enormous difficulties, and controls for different parts of the intelligent lattice, for example, SCADA systems and communication systems, to address the problems confronting savvy network innovations. Nonetheless, intelligent networks require a far-reaching cybersecurity arrangement by supporting partners, researching vulnerabilities and digital threats, and coordinating systems to provide rules for viable threat management. Zhou and Zhang (2017) examined the danger of digital assault on intelligent metering systems by applying strategies and ideas from digital assault situations in a smart matrix system.
Moreover, to adequately combat cybercrime, Zhou and Zhang (2017) believe that an organization must effectively develop remediation actions such as correlating and consolidating every information from the vulnerability scanners to detect any pending risk or threat to the organization’s information systems and data (Zhou and Zhang, 2017). One of the best approaches that the 3 Net Enterprise needs to adopt is the top-down approach to cybersecurity. This is the process where the organization’s senior management is in charge of providing a clear framework for other organizations’ departments on a way they need to respond to any cyber threat or risks in case they occur. In this regard, the 3 Net Enterprise’s leadership team will have to develop excellent frameworks, policies, and cyber risk assessment strategies to effectively combat risks (Zhou and Zhang, 2017). In addition, an organization needs to closely associate with every business stakeholder to ensure that all cyber threats are eliminated.
- Systems, Standards, and Guidelines
There are generally acknowledged threat management models, for example, ISO 31000, that provide rules to threat management exercises which additionally consider threat management a vital piece of the general authoritative procedures, including important arranging and management forms (Alsmadi, 2019). IEC 31010 is further another perceived threat management strategy and design. The NIST system centers on overseeing digital security threats and NERC CIP principles for the recognizable proof and assurance of essential digital resources that help the dependable task of the electric power network. The NIST system is a threat-based methodology for managing digital security threats (Alsmadi, 2019). Primary foundation organizations can utilize the NIST structure close to their current systems to recognize, oversee, and evaluate cybersecurity threats methodically. A specific objective-driven threat management approach Alsmadi (2019) stresses the distinguishing proof of purposes as goals explicit to the organization’s mission. Threats are considered a check to them, with the goal that recognized threats are evaluated dependent on which objectives they contradict. Alsmadi (2019) believes that understanding cybersecurity risk or danger is one of the primary stages in cyber risk assessment and management. In this case, the 3 Net’s information system and data security personnel are needed to classify the organization’s information assets based on their importance (Alsmadi, 2019). For instance, a risk or threat factor attacking a sensitive database like a financial one needs more attention than the risk factor that is only present on a user’s desktop. Therefore, it is always imperative to classify and understand the most critical assets to enable you to give their securities priority. It is always essential to understand all cyber vulnerabilities, risks, and threats because the world of information technology is persistently evolving (Alsmadi, 2019). In this regard, the 3 Net Enterprise’s IT department and, more significantly, its IT experts must get updates about the latest cyber vulnerabilities, risks, and threats to enable the organization to develop excellent cyber defensive mechanisms and create awareness about these latest cyber scams and attacks.
Changes to the Project Environment
- Original Network Environment
The 3 Net Enterprises’ network environment wholly depended on vulnerable three large data centers and smaller sites in the major shipping ports. To make it worse, the firm’s data centers were only secured by weak packet filtering applications, specifically the Access Control Lists, consisting of intrusion detection systems (IDs) AND firewalls. However, this data security system used by the 3 Net Enterprises still put the company under several information security systems and data privacy threats due to its weak vulnerability. Furthermore, despite the extensive threat appraisal strategies laid down by the 3 Net Enterprises for its computer systems, the company still required a specific design to cover all phases of the threat management procedure. In this regard, the 3 Net’s networks were highly vulnerable to information security threats because these systems were significantly insecure due to a lack of solid security and deterministic timings.
Moreover, the 3 Net’s network resources were designed to airgap based on WAN networks and thus lacked visibility. Even though the firm’s information systems ran in critical environments, their security was still challenging because they were prone to software bugs and downtime, which was catastrophic in many cases. This enabled the newly hired CIO to decide on the present security dimension and encouraged the firm’s management to select security components consisting of the Forescout hardware and servers. These network security resources added to each port helped the company further evaluate the threat related to data systems. The shrewd matrix security outline includes the arrangement of controls, communication, and physical system parts required to provide an exact digital-physical condition. There was also a colossal need to recognize the computer assaults, which changed the conduct of the focused-on control systems by understanding the outcomes of the assault for threat evaluation.
- After Network Environment
After implementing the new information security framework, the 3 Net Enterprises extensively enhanced its data privacy and information security. Using the Forescout hardware and servers in the company’s network helped tighten data security and safeguard the firm’s information system’s resources against all cyber threats. The new information system security approach helped the 3 Net to enhance its physical data security and ensure unauthorized access was limited. Moreover, using the Forescout devise enabled the firm to protect its information systems from ransomware threats. The system also helped the company to tighten its cyber security measures. The new data security design helped the 3 Net Enterprises to create a new IT Security Governance strategy that allowed the company to increase data privacy and security efficiency. This ensured the entire firm’s information resources were secured at all times, and both the firm’s workers and clients safely operated at all times without experiencing any data security threat (Dumitru, 2022). In this regard, all 3 Net’s clients and employees could now feel safe and comfortable as they carry on with their usual activities within the firm’s premises.
Furthermore, the new data security framework altered and hardened the 3 Net’s information security systems and protected the company from cyberattacks. This kind of tight data security achieved by the company was also extended to sensitive customer information and office files. Finally, the new data security framework enabled the 3 Net to achieve strong, redundant, robust firewalls and adequate built-in intrusion detection systems for precise packet filtering and stout data security system. This helped the company to provide sufficient security for its computer systems hardware, such as hard drives, flash disks, backup drives, and disks. These resources were tightly protected since they contain sensitive and essential information for the 3 Net Enterprises. Also, the hard drives were given off-site back-ups to ensure that the company still did not lose any data even in case of fire or any other eventuality. Therefore, the 3 Net’s newly hired CIO ensured that the customers’ data were protected from any breach.
Methodology
The waterfall methodology was used and the project was divided into logical segments for a successful rollout. As shown in diagram 2 below, the waterfall methodology consisted of six phases: requirement analysis, system design, implementation (coding), system testing, system deployment, and finally, system maintenance.
- Requirement analysis
The project team conducted an elaborate requirement analysis and documented it in the specification. Then, the team reported the resources, such as the Forescout hardware and servers. These devices were found suitable for protecting the computer system’s resources. The Forescout uses a 2-layer method to manage and save the user’s space and kernel. For example, it usually makes requests to a kernel layer to run the user’s space to access the protected resources of a computer. The Forescout hardware was analyzed and found to be highly feasible when used in the project. However, the constraints or limitations identified during the requirement analysis include inadequate time, budget, and resources. These constraints were identified early enough, and the project team took precautionary measures to ensure the project development and all the processes happened successfully. The project team finally produced the Requirement Understanding Document (RUD) after conducting the analysis and putting considerations.
- System design
The project team designed robust data privacy and information security system using the Forescout hardware and servers. The algorithms used for data encryption were created from a scientific process known as cryptography. This method was used to encrypt data for transmission or storage purposes. In this regard, the algorithms were used to convert data into an abstract form with the help of the Forescout hardware (Alghentawi, 2021). Finally, the personal values and secret keys were introduced to create ineffectual through the casual observer to achieve the desired data security for the 3 Net Enterprises and its clients.
Figure 1: Conceptual Metalmodel Security Domain View
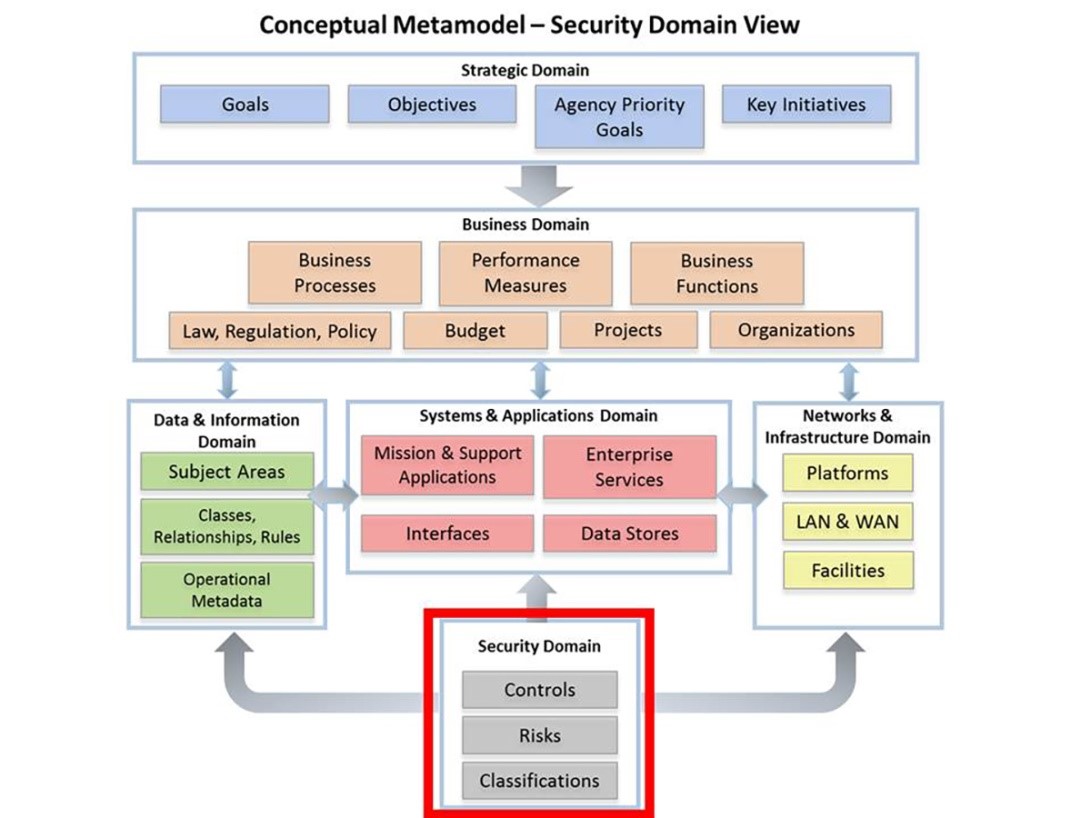
Source: Mwambe and Echizen, 2017)
This process produced two keys: one was given out to 3 Net’s staff, and the other was kept private. In this case, the company’s employees could use their public keys to encrypt their files before sending them. However, encrypted files could not be retrieved unless the person is given the private keys for decryption, referred to as asymmetric encryption, and above was the designed system.
- Implementation (coding)
The source codes were written, developed, and assigned according to the project requirements. The project team created physical design specifications for the data security into the working codes and used them for designing the data security system. Moreover, the project developed the Forescout hardware system in small fragments called units and integrated them into the more extensive procedure. Each unit was then tested to ensure it functioned properly.
Diagram 2: Waterfall Methodology Stages
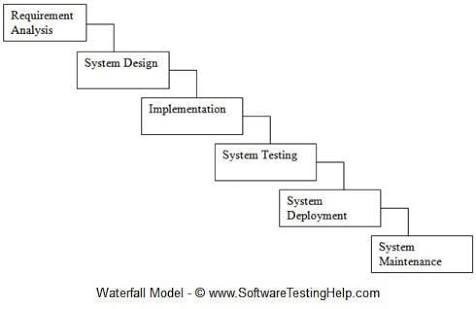
Source: Fagarasan et al. 2021.
- System testing
After completing the coding process, the testing team checked for all possible errors and defects. This was done by automatically running the cases and allowing the codes through each test case to determine their functionality levels. The main aim of system testing was to ensure the designed data security system met all the system requirements. The project team then got the opportunity to fix all the identified errors and defects and ensure the developed system meets all the quality assurance standards.
- System deployment
The data security system was finally deployed on the 3 Net Enterprises’ live environments and to the company’s client servers. The main aim of system deployment was to analyze and test the performance of the designed data security system, and the project realized the procedure was complete and ready for use by the client.
- System maintenance
The project provided constant support and maintenance to the data security system designed and guaranteed the system was functioning smoothly. The CIO assigned the 3 Net’s IT staff the responsibility to maintain the system and ensure it serves its purpose constantly.
Project Goals and Objectives
The main objective and goal of this project were to :
- To review Ashore Data Centers and document current capabilities and constraints.
- Review vessels to determine infrastructure inconsistencies between platforms
- Review network segmentation to account for VLANS with Access Control Lists (ACLs)
- Install Forescout appliances, and deploy agent-based endpoints (SecureConnector)
- Schedule training with third-party vendors for global administrators to become competent and confident in administering this new solution.
The project team reviewed the Ashore Data Centers and documented the current capabilities and constraints by providing a standardized Installation Design Plan (IDP) for ashore and afloat environments to minimize cost and complexity. In addition, the team coordinated all the networked systems and enhanced resource management and allocation efficiency. Secondly, the project team reviewed vessels to determine infrastructure inconsistencies between platforms to improve data privacy by protecting the data and information exchanged between 3Net Enterprises and its clients. The team also achieved this objective by reinforcing the network’s wireless security against infiltration and protecting the 3Net Enterprises from internal carelessness, data theft, virus penetration, and cyber threats. Third, the project team also reviewed the network segmentation to account for VLANS with Access Control Lists (ACLs) by developing a network map based on the OSI model to graphically depict Routing, Distribution, and Access Layers and installing hardware in 3Net Enterprise’s Data Centers and on required vessels. The fourth objective was installing the Forescout appliances and deploying the agent-based endpoints (SecureConnector), which was achieved by configuring the network learning within Forescout to begin capturing data and establish normal operating behaviors. The final objective was to schedule training with a third-party vendor for global administrators to become competent and confident in administering this new solution. Finally, it enabled the protective mode to begin securing endpoint connections, applications, and services.
Project Timeline
| Milestone or deliverable | Planned Duration (hours or days) | Actual Duration | Actual Start Date | Actual End Date |
| Review Ashore Data Centers and document current capabilities and constraints. | 2 Days | 4 days | July 1st | July 4th |
| Review vessels to determine infrastructure inconsistencies between platforms | 2 Days | 4 days | July 5th | July 9th |
| Review network segmentation to account for VLANS with Access Control Lists (ACLs). | 2 Days | 4 days | July 10th | July 14th |
| Install Forescout appliances and deploy agent-based endpoints (SecureConnector) | 10 Days | 15 days | July 15th | July 25th |
| Schedule training with a third-party vendor for global administrators to become competent and confident in administering this new solution. | 15 Days | 20 days | July 26th | August 15th |
The projected duration for the first deliverable was two days, but the actual durations moved to 4 days. Similarly, in the second and third deliverables, the projected duration was two days, but the actual durations moved to 4 days. Finally, the situation was similar in the fourth deliverable because the projected duration was ten days. Still, the actual duration moved to 15 days, whereas the situation was similar in the fifth deliverable, where the duration was moved to 20 days from 15 days. The adjusted durations include management risks, delayed funding, and a lack of good communication between the project team and stakeholders. Lack of proper communication made it impossible for the 3 Net Enterprises Communication team to release funds in good time to enable the project team to deliver the project deliverable as planned.
Unanticipated Requirements
Some unanticipated requirements during the project implementation include disaster recovery and cyberthreat detection plans. First, it came out that the designed data security system needed a disaster recovery plan. In addition, it usually requires a quantitative threat evaluation display that centers on the CPS running conditions and ascertains threats continuously utilizing clients’ reactions to threats on specific occasions. In this regard, the NIST system was identified as one of the most suitable methodologies for security threat management. The NIST system is a threat-based methodology for managing digital security threats. Therefore, the 3 Net Enterprises could utilize the NIST structure close to its current systems to recognize, oversee, and evaluate cybersecurity threats methodically. A specific objective-driven threat management approach stresses the distinguishing proof of objectives as goals explicit to its mission. Secondly, the need to develop a cyberthreat detection plan also came up such a mechanism could help the 3 Net Enterprises detect cyber threats, with the goal that recognized hazards are evaluated depending on which objectives they contradict. As with any other system, security had to be incorporated from the planning stage and throughout the life cycle. Therefore, the project team realized that allocating security only to what appeared to be critical to the company would mean neglecting other potential attack vectors. However, this could be taken care of through network segmentation. This was where an IRP was vital for protecting the 3 Net Enterprises’ data against future attacks.
Conclusions
By implementing Forescout at 3Net Enterprises, this project reduced expense and complexity and offered a uniform Installation Design Plan (IDP) for both on- and off-shore situations. It also resolved any environmental issues related to power, space, or air conditioning. The project also illustrated the Routing, Distribution, and Access Layers graphically and created a network map based on the OSI model, thus harmonizing the networked processes with existing standards. Furthermore, by installing hardware in 3Net Enterprise’s Data Centers and on required vessels, the project enforced role-based access to the network and eliminated sharing of sensitive devices. Forescout’s network learning was also set up so it could start collecting data and establishing typical operating patterns. Lastly, 3Net Enterprises started protecting endpoint connections, applications, and services, by enabling the network protective mode. The measurable metrics for this project include the level of preparedness, unidentified devices on the internal networks, intrusion attempts, insecurity incidents, and mean time response. However, the metrics that showed considerable success include intrusion attempts, insecurity incidents, and indicated time response. In this regard, implementing the project’s immediate and potential effects include a reduced number of intrusion attempts, data insecurity incidents, and faster mean time for cyberattack response. Therefore, the 3 Net Enterprises experienced a significant reduction in intrusion attempts, data insecurity incidences, and mean time to detect such intrusions.
Project Deliverables
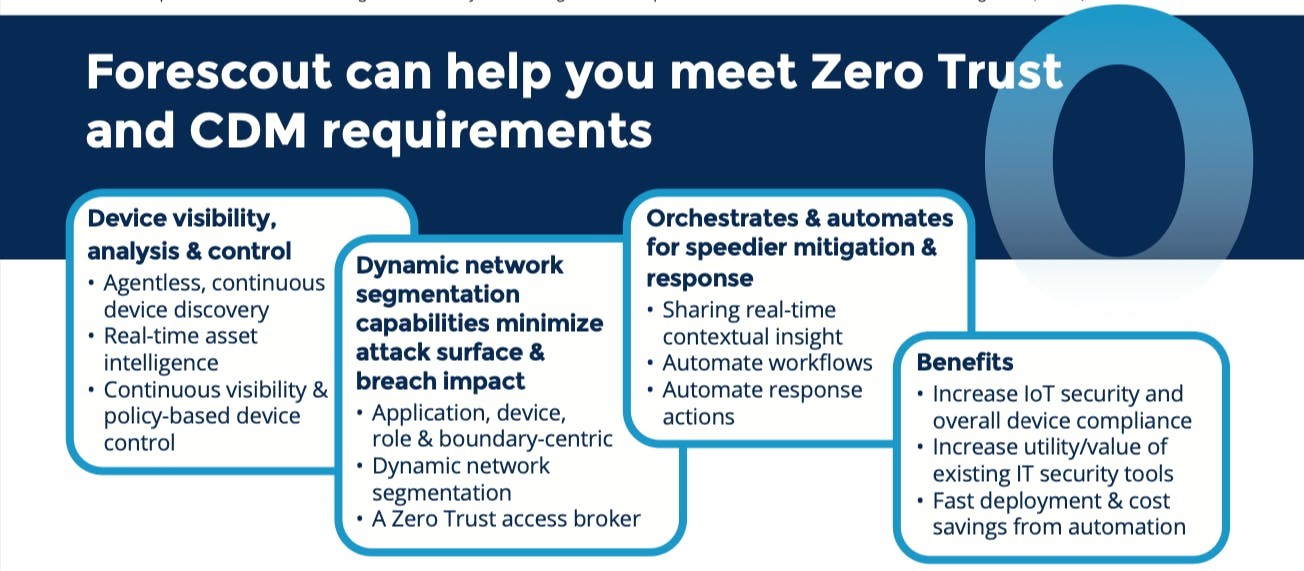
In appendix A, a foundation for zero trust is explored in detail and its components that help organizations achieve tight data security. One of the main components of the foundation for zero trust is workflow automation, which entails cybersecurity asset management, asset compliance, and network segmentation. The second component is security orchestration which entails risk compliance and network access control. A combination of the foundation for zero trust and Forescout hardware is essential in preventing a compromised information security system from being attacked by computer viruses or malicious programs. This is done by allowing either user-to-app or app-to-app) connections, also known as a one-to-one connection. Therefore, a data security system is invisible to the internet when it has zero trust, and no cyberattacker can discover such a computer system.
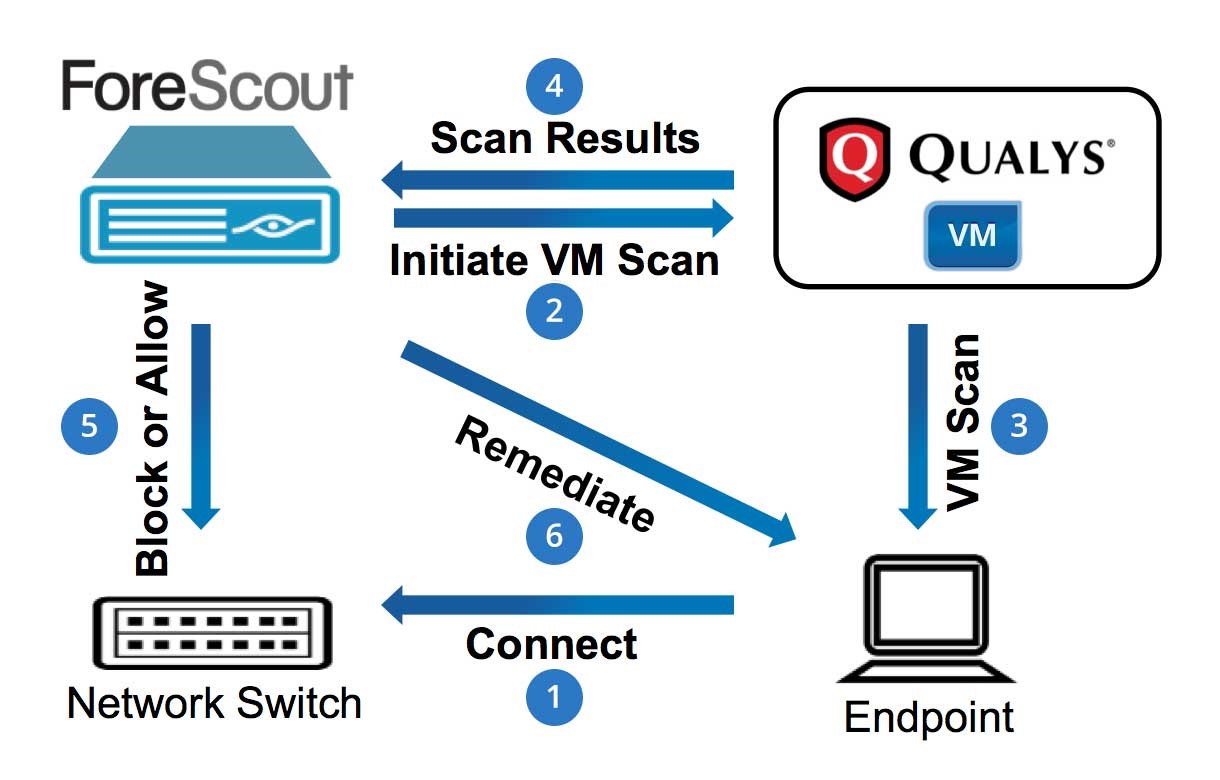
Furthermore, as observed in appendix B, the forescourt security system demonstrates a sample data security system with several components. Some elements of a forescout security system include the network switch, VM scan, endpoints, and connect. The system operates like a complete circuit in an electric parallel connection where each component works interdependently. Depending on the risk levels, the network switches can either allow or block information processed in the forecourt hardware from proceeding to the following process. Also, the information reaching the endpoint is scanned at the VM scan for safety. Finally, the scan results are displayed, and the threat is neutralized before it attacks the computer system. Finally, Appendix C illustrates the role played by the forescout hardware in the foundation for zero trust and CDM requirements. Some of the functions outlined in the system include devise visibility, analysis and control, dynamic network segmentation, threat mitigation, and the system’s benefits. Some of the benefits explored include increasing the IoT security and the devise compliance of the entire system. Finally, continuous visibility and policy-based devise control are also indicated as one of the most critical aspects of the forecourt hardware security system.
References
Alghentawi, M. (2021). Evaluation of IoT: Challenges and Risks on Communication Systems. Journal of Millimeterwave Communication, Optimization and Modelling, 1(2), 37-43. file:///C:/Users/Edward/Downloads/5-Evaluation+of+IoT+Challenges+and+Risks+on+Communication+Systems-Alghentawi%20(1).pdf
Alguliyev, R., Imamverdiyev, Y., & Sukhostat, L. (2018). Cyber-physical systems and their security issues. Computers in Industry, 100, 212-223. https://doi.org/10.1016/j.compind.2018.04.017
Alsmadi, I. (2019). Cyber Security Management. The NICE Cyber Security System,243-251. doi:10.1007/978-3-030-02360-7_10
Christiawan, E. (2015). The Importance of Information Security Management in Small Medium Enterprises. https://www.researchgate.net/profile/Evan-Christiawan/publication/330846544_The_Importance_of_Information_Security_Management_in_Small_Medium_Enterprises/links/605fecf692851cd8ce6fbf52/The-Importance-of-Information-Security-Management-in-Small-Medium-Enterprises.pdf
DUMITRU, I. A. (2022, April). Zero Trust Security. In International Conference on Cybersecurity and Cybercrime (Vol. 9, pp. 99-104). https://proceedings.cybercon.ro/index.php/ic3/article/view/2022-13/93
Fagarasan, C., Popa, O., Pisla, A., & Cristea, C. (2021, August). Agile, waterfall and iterative approach in information technology projects. In IOP Conference Series: Materials Science and Engineering (Vol. 1169, No. 1, p. 012025). IOP Publishing. https://iopscience.iop.org/article/10.1088/1757-899X/1169/1/012025/pdf
Mwambe, O. O., & Echizen, I. (2017). Security modeling tool for information systems: Security Oriented Malicious Activity Diagrams Meta Model Validation. MIS Review, 59. http://misreview.mis.nccu.edu.tw/pdf/volume/2212/2212-04-full.pdf
Öğüt, H., Raghunathan, S., & Menon, N. (2010). Cyber Security Threat Management: Public Policy Implications of Correlated Threat, Imperfect Ability to Prove Loss, and Observability of Self-Protection. Threat Analysis,31(3), 497-512. doi:10.1111/j.1539-6924.2010.01478.x
Zhou, Z., & Zhang, Q. (2017). Fault Tree Analysis Based on Dynamic Uncertain Causality Graph. Volume 4: Nuclear Safety, Security, Non-Proliferation and Cyber Security; Threat Management. doi:10.1115/icone25-66296
Appendix A: Foundation for Zero Trust
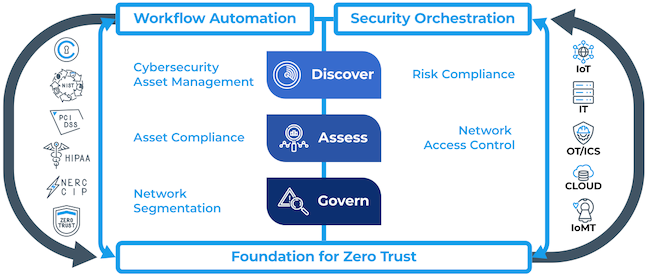
Appendix B: Forescout Security System
Appendix C: Role Of Forescout Hardware In The Foundation For Zero Trust
 write
write