Abstract
Cybersecurity engineering is increasingly being incorporated into enterprises’ information technology frameworks in the modern world. Cybersecurity is a more general term for discovering the flaws and dangers in information systems, whose main objective is to provide cutting-edge fixes for IT-related issues. The paper’s introduction discusses the recognized organization, noon company, about its objectives, plans, and guidelines, as well as its framework for the digital landscape and its services.
The section covering Noon’s asset identification strategy is followed by a thorough review of Noon’s information classification in the report’s main body. This paper goes on to reaffirm the identification of vulnerabilities, threats, and risks to define the potential hazards at Noon company. This is followed by a thorough discussion of the implementation strategy and any further needs thought essential for Noon company security awareness training and awareness raising. In light of this, this paper discusses management strategies for change and configuration. Before concluding, the article evaluates the report’s overall effects and discusses specific contributions relevant to noon company and the more comprehensive cybersecurity engineering framework.
Introduction
Noon Company is an online-based retailer operating primarily in the Middle East. The company’s goal is to give consumers across the region convenient access to the best products, prices, and a great delivery experience. To achieve this goal, Noon Company has developed a comprehensive strategy that combines technology, innovation, customer-centricity, and community-oriented initiatives. The core component of Noon Company’s strategy is to use technology to provide a digital experience that best fits the needs of its customers and promotes a seamless shopping experience. (Noon & Ogbonna, (2021). To this end, the company has invested heavily in digital technologies and created a digital landscape of websites, apps, artificial intelligence (AI), and machine learning (ML). Such investments enable Noon Company to deliver personalized product recommendations and deals, enhanced customer service, real-time updates, and customer support.
Noon Company has also developed several policies and processes to ensure that customer satisfaction and quality remain top priorities. The company’s total return and exchange policies give customers greater certainty in their purchase decisions and allow for an easy, informed, and secure online shopping experience. The company also maintains a customer charter and has established an ethics compliance program to ensure that it complies with applicable laws and industry standards. Moreover, company policies focus on being transparent and responsible in matters related to customer data protection and customer privacy.
Noon Company has developed a framework to ensure data is handled following the highest security and privacy standards. The framework also outlines procedures for customer data storage, customer data de-identification, and customer data access. In addition to better-serving customers, the company is emphasizing community-oriented initiatives. This includes launching programs to support small businesses, entrepreneurs, and charitable causes; teaching digital skills to those seeking them; and collaborating with local universities to increase job opportunities.
Noon Company has a range of services, including logistics, payment processing, and customer service. These services enable customers to enjoy a seamless, end-to-end online shopping experience. Noon Company manages all customer purchase aspects, from order placement to delivery. Overall, Noon Company has established a robust digital infrastructure, developed customer- and community-focused policies and procedures, and has a comprehensive range of services. This combination of technology, policies and services will help Noon Company reach its goal of providing customers with convenient access to the best products and prices.
Main body
Asset identification
An asset identification system is a method by which an organization controls and manages its physical assets by utilizing a unique identifier. This unique identifier can help track and monitor the assets individually. Asset identification aims to ensure that all purchases are correctly accounted for and that their location, maintenance records, and schedules can be quickly accessed.
Noon Company implements a barcode asset identification system as part of its asset management system to identify and locate all its assets. This system allows Noon Company to keep track of the assets, their ownership, and their condition. Barcodes are printed on the physical assets, and the asset management system scans them. (Bitzan, 2020) The details of each purchase are then stored in the design and can be quickly accessed. This asset identification system enables Noon Company to promptly determine the amount, location, ownership, state, and condition of all the assets, making it easier for them to manage assets effectively. This system is often combined with other asset management systems, such as tracking, monitoring, and data analysis, for comprehensive asset management.
Noon Company’s asset management system lets them know immediately what assets have been purchased, assigned, sold, or moved for any purpose, making it effortless to get exact information. The asset identification system can be automated and integrated into Noon Company’s existing financial and accounting systems so that the company can save time and energy in tracking, monitoring, and reporting all the assets.
Noon Company can also provide each asset with unique identifiers such as serial numbers and product SKUs. This way, they can enhance and optimize their asset management to ensure that all the assets are appropriately identified, tracked, and monitored. The asset identification system can allow Noon Company to quickly find assets and provide comprehensive reports, which can help maximize asset utilization, improve asset security and compliance, and help the company reduce the cost of asset management.
Information classification
Information classification is the process of grouping information into usable and logical categories. The purpose of information classification is to ensure that only the right people have access to the correct data, which helps to protect the information’s confidentiality, integrity, and availability. (Jbair et al., 2022) There are typically four types of information classifications –public, internal, confidential, and restricted.
Information classification process
First step: Entering assets into an inventory.
When entering assets into an inventory, it is essential to be accurate and have good record-keeping practices. The process begins by obtaining an accurate list of assets to be logged into the inventory. This can be obtained by physically counting the assets or reviewing records. The next step is to enter the assets into the stock. This can be done manually or via computer, depending on the inventory system used. When entering purchases, including all details, such as serial numbers, descriptions, and locations.
Additionally, ensure the status of each asset is noted, whether it is in use, pending disposal, or missing. Once all purchases have been entered, the inventory should be reconciled at least once a year to account for any new additions or removals from the list. Good record-keeping and change documentation are essential for keeping the inventory up-to-date and accurate.
Second step: classification
Senior management should offer crucial instructions regarding the organization’s ISO 27001 risk assessment findings. For instance, extremely high degrees of confidentiality is required for data assets exposed to significant dangers. As a result, the information classification for the noon company is established as follows:
Confidential Lever
Personal Level is an essential type of information classification used by Noon company. This type of classification is used to identify and protect personal information at the highest level of sensitivity. This includes information restricted to certain people and never shared with the public or anyone outside the organization. (Alshaikh, 2020) The most common types of data classified as confidential include proprietary information, trade secrets, company strategies, personal communications, employee records, customer and supplier contact information, financial records, and other susceptible information.
Noon’s confidential-level security measures and access restrictions protect these information assets from unauthorized use, access, or disclosure. The company’s employees must identify confidential information and the security measures necessary for its protection. These security measures must include encryption, logging, monitoring, and auditing for internal and external access and data leakage prevention. Access to confidential information should also be limited to only authorized personnel necessary for the company’s daily operations.
Restricted Level
The local Level is a type of information classification in Noon Company that restricts access to sensitive information and resources. It ensures that only authorized individuals have access to critical documents and data. This classification level allows the company to protect its valuable knowledge, ensuring that the data is not misused or accessed without permission. Access to documents with local-level classification is limited to management-level administrators and the personnel required to protect the integrity and confidentiality of the data. Access is provided to only those who need it to fulfill their roles, and strict protocols are followed to ensure that only authorized individuals can access the data. By controlling access and restricting access to critical information, Noon Company can provide its data that remains secure.
Internal Level
Internal Level is a type of information classification used by Noon Company to limit access to sensitive information. This system helps ensure that only authorized personnel have access to certain data types. The internal Level divides information into four categories depending on the sensitivity of the report: restricted, confidential, sensitive, and public. The local Level is assigned to data with the highest sensitivity and is only accessible by certain high-level personnel. The “confidential” Level is set to data with significant importance to the organization and is only shared with those who need it. The sensitive Level is less stringent and is usually given to company-related confidential information that can be shared with employees in certain positions. Finally, the public Level contains less critical information that can be shared with the public or authorized personnel. Noon Company’s internal Level helps maintain the security and privacy of internal data.
Public Level
Public Level is a type of information classification within Noon that enables employees and companies to decide which information should be communicated with the outside world. This classification level is essential as it helps maintain sensitive data security, privacy, and integrity. Public-level classification means the information is made available to the public, including government agencies and other interested parties. Publicizing the material on platforms used by the general public, such as websites, news releases, blogs, and adverts, could achieve this. Company policies, project updates, news, and personnel promotions are a few examples of information that might be categorized as public. Public-level classification is essential to ensure company secrets are kept secure and other entities can see only what the company wants them to see.
Third step: Labelling
Labeling is a fundamental information classification process in Noon Company. This is because classification is needed to organize information. Labeling also makes it easier and faster to search for information. Labels increase the data’s order, visibility, and understanding and facilitate communication between stakeholders. Labeling can also allow users to quickly access more complex types of data, such as large datasets. All of these advantages make labeling an invaluable classification process for Noon Company.
Forth step: Handling
Noon Company classifies its information by establishing protocols and procedures to ensure data security and reliability. This includes clearly defining access levels and password protection for confidential information, setting up data encryption and other secure infrastructure, and creating guidelines for handling and sharing the data. This safeguards customer data and helps the company protect its intellectual property. Additionally, periodic reviews and audits of the protections in place can detect and address any security issues and ensure the continued safekeeping of Noon’s valuable information.
Risk assessment
The Noon Company has identified the following assets as necessary for its business operations:
- Network infrastructure includes routers, switches, access points, and other IT components that support employers and customers.
- Software applications include custom and third-party applications used to track customer data and manage operations.
- Customer data includes customer records, financial transactions, and other business-critical information.
- SaaS services: Noon Company uses numerous SaaS services, such as web hosting and cloud storage, to support customers and business operations.
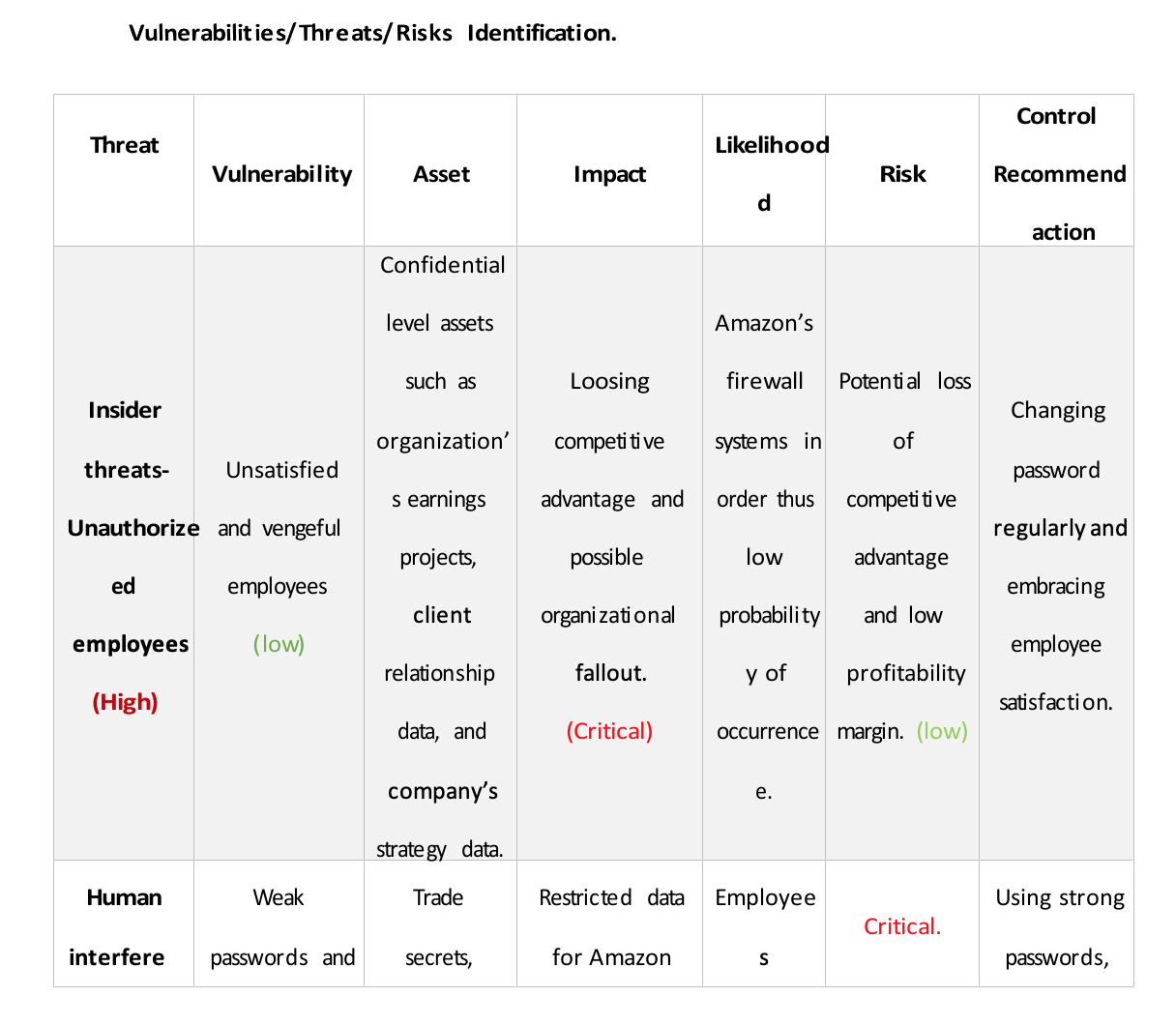
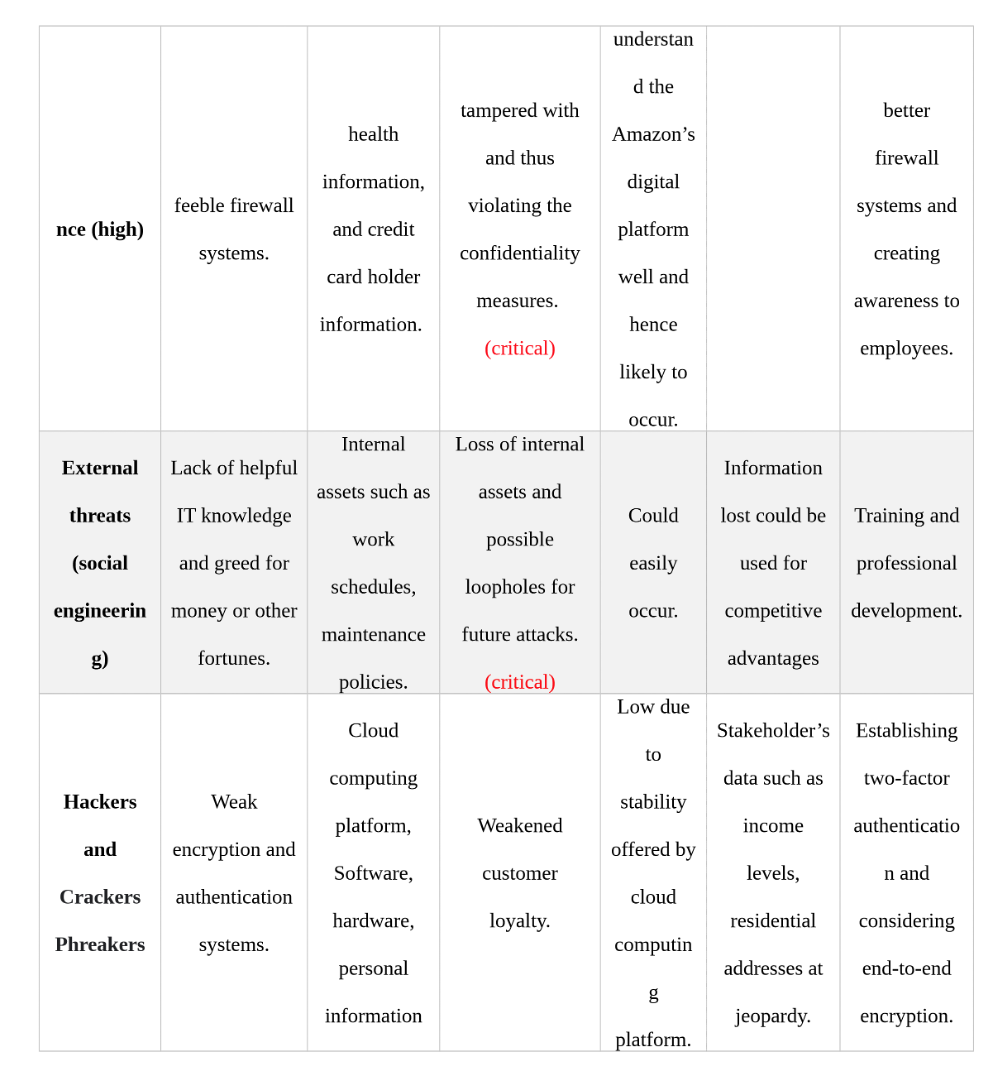
Risk 1: Network infrastructure threats:
- Denial of Service (DoS) attacks: A DoS attack can occur when malicious actors send numerous requests to a network to overwhelm the resources and deny legitimate users access. Impact: A DoS attack can be significant, disrupting normal business operations and resulting in lost revenue. Likelihood: The likelihood of a DoS attack is moderate, as malicious actors often seek to target more extensive networks.
- Unsecured network: An unsecured network can make it easy for malicious actors to gain unauthorized access and disrupt business operations. Impact: The impact of an unsecured network is high, as it can allow malicious actors to exfiltrate customer data and disrupt normal operations. Likelihood: Unsecured networks are relatively common, making the likelihood of this threat moderate.
Vulnerabilities:
- Weak passwords can be easily guessed or brute-forced, making it easy for malicious actors to gain access. Impact: The impact of weak passwords is significant, as they allow easy access to customer and business data. Likelihood: The likelihood of this vulnerability is moderate, as weak passwords remain a common form of security.
- Insecure protocols can be exploited, allowing malicious actors to access networks and exfiltrate data. The impact of insecure protocols is high, as malicious actors can access valuable customer and business data. The likelihood of this vulnerability is moderate, as many networks still need to be fully secured against known vulnerabilities.
Risk 2: Software applications Threats:
- Malware infections: Malicious actors can infect systems with malware, allowing them to steal customer data, disrupt operations, and gain control of systems. Impact: The impact of a malware infection is high, as malicious actors can access private customer data and disrupt operations. The likelihood of malware infections is moderate to high, depending on the security measures in place.
- Unpatched applications: Unpatched applications can make it easy for malicious actors to exploit known vulnerabilities. Impact: The impact of unpatched applications is high, as malicious actors can gain access to business data and disrupt operations. The likelihood of this threat is moderate to high, as unpatched applications are relatively common.
Vulnerabilities:
- Unsupported applications: Unsupported applications can be vulnerable to known exploits, making it easy for malicious actors to gain access. Impact: The impact of unsupported applications is high, as malicious actors can easily access vital customer data. Likelihood: Unsupported applications are typical in many organizations, making the likelihood of this vulnerability moderate.
- Poor coding practices: Poor coding practices can leave applications vulnerable to known exploits and make them easy targets for malicious actors. Impact: Poor coding practices are high, as they can allow malicious actors to gain access to business data and disrupt operations. The likelihood of this vulnerability is moderate, as poor coding practices are often the result of human error.
Guidelines for implementing security training and awareness program
- Establish program objectives that are in line with the overall security goals set for the organization.
- Identify required stakeholders and involve them in designing the program.
- Design and develop appropriate training materials and content that address the organization’s security needs and the skills and knowledge of all personnel.
- Provide employees with specific scenarios and examples appropriate to their job roles and responsibilities.
- Make the training interactive and use hands-on methods to engage the learners.
- Provide feedback and support to participants to help them apply learned concepts in the workplace.
- Monitor the progress and performance of the training program to identify areas that need attention or improvement.
- Measure the effectiveness of the training by using relevant metrics and evaluate the program’s efficacy.
- Keep the program updated with current security best practices and trends.
- Reinforce security awareness messages and updates regularly.
Management of maintenance, change, and configuration
Change and configuration management is a process within the noon company that arranges, records, and monitors all changes that occur within the organization. By identifying the architecture of IT assets, the process of change and configuration management help to diagnose and repair configuration issues while providing an audit trail of all changes.
At noon company, the change and configuration management process begins with logging and categorizing all changes made to the environment. An authorized change management system is also implemented to ensure all changes are approved and recorded. The change and configuration management process ensure that standardized procedures and processes are followed to carry out different organizational tasks. Furthermore, the process is also used to monitor and track all changes in the environment, ensuring that the entire system complies with the company’s policies and rules.
Moreover, the change and configuration management process help the noon company identify, document, and classify application and system components and related versions. These components and arrangements can be viewed, examined, and tracked at any time. The midday company also ensures that policy-based access rights are enforced to provide data and information security.
The change and configuration management process helps the noon company to efficiently and accurately identify and document system configurations while ensuring that all changes made in the environment are adequately tracked and recorded. The process also ensures that the company’s policy and rules are enforced, promoting security and compliance within the organization.
Individual contribution
- The knowledge available in the modern world, characterized by technical progress and globalization, is expanding.
- Cybercriminals are coming up with increasingly complex strategies to use in their attacks.
- Cloud computing is gaining traction in the current era, where the Covid-19 pandemic has converted the majority of physical organizations’ practices to virtual platforms.
- Cloud computing is gaining traction in the present era, where the Covid-19 global epidemic has converted the majority of physical organizations’ practices to virtual platforms.
- Predictably, all businesses will eventually shift their IT infrastructure to cloud computing platforms.
According to the prepared consulting document that was specific to the noon Company, I have discovered that:
Noon Company is an established and growing enterprise specializing in eCommerce solutions for businesses in the retail industry. The company offers a wide range of services, including web design and development, custom app development, and hosting, in addition to professional consulting and support. Noon Company has a proven track record in the industry due to its customer-focused approach. The team of professionals at Noon Company is highly experienced in customer engagement and delivering customer-centric solutions. Many factors make Noon Company an excellent choice for businesses seeking reliable eCommerce solutions. The company’s customer-driven approach ensures satisfaction and a hassle-free experience for businesses, while their professional expertise guarantees efficient service. The Noon Company team also offers customized solutions to meet customer needs. They know various platforms and technologies, allowing them to develop bespoke solutions.
Noon Company’s experienced IT support team provides ongoing help and guidance throughout the customer journey. This ensures customers have all the assistance they need when using their eCommerce solutions. In conclusion, Noon Company is a reliable and reputable enterprise in the eCommerce solutions industry. With their customer-centric attitude, efficient services, and personalized solutions, they are an excellent choice for businesses seeking effective eCommerce solutions.
Conclusion
The Noon Company’s commitment to providing comprehensive and innovative solutions for cybersecurity for its customers has been commendable. Through their unique approach, they have committed to ensuring their clients’ systems are as secure as possible. From proactive solutions such as encryption and authentication solutions to reactive strategies such as network monitoring and response plan development, Noon Company strives to ensure that its clients are secure and protected from security threats. What makes Noon Company unique is its dedication to providing more than just cybersecurity services (Aldawood & Skinner, 2019). They also offer their customers a wide range of consulting, training, and support services. This package has proved invaluable to those looking to arm themselves with the latest advancements in security practices. Combining these services and a culture of customer education has allowed Noon Company to help its clients understand the risks they face and develop the appropriate defensive measures to protect their data and systems. No cybersecurity plan is complete without an evaluation of the solutions being implemented.
Noon Company provides its customers with both intrusive and non-intrusive penetration testing that helps them identify and address any vulnerabilities or threats that may be present on their networks. This makes them stand out against its competitors and enables them to deliver unmatched solutions for its clients. Overall, the Noon Company has provided its customers with an unbeatable cybersecurity solution that keeps their data safe and secure from attackers. The specific measures taken by the company to ensure their customer’s systems are secure have meant that customers could rest easy knowing their data and systems are safe. Their in-depth consultation and support services have provided their clients with the knowledge they need to build an effective security strategy and ensure their systems stay ahead of the curve.
References
Alshaikh, M. (2020). Developing cybersecurity culture to influence employee behavior: A practice perspective. Computers & Security, 98, 102003.
Aldawood, H., & Skinner, G. (2019). Reviewing cyber security social engineering training and awareness programs—Pitfalls and ongoing issues. Future Internet, 11(3), 73.
Bitzan, J. L. (2020). I am determining Critical Information Asset Identification, Classification, and Valuation (Doctoral dissertation, Capella University).
Jbair, M., Ahmad, B., Maple, C., & Harrison, R. (2022). Threat modeling for industrial cyber-physical systems in the era of intelligent manufacturing. Computers in Industry, 137, 103611.
Noon, M., & Ogbonna, E. (2021). Controlling management to deliver diversity and inclusion: Prospects and limits. Human Resource Management Journal, 31(3), 619-638.
 write
write