Introduction to Cyber Violence
In this particular essay, we will look to discuss policy, by starting, with the definition of cyber violence, the legal framework governing the problem, providing official statistics on the extent of the problem, what are the empirical research findings, and finally offer recommendations on how best to tackle the issue.
Cyber violence can be referred to as the abuse of computer systems or programs to either lead, facilitate or threaten violence can be to an individual or a corporate, resulting in harm; it can be physical, sexual, or on economic aspect inclusive of individuals’ exploitation of circumstances, characteristics or their vulnerabilities (Moral-Arroyo, 2022 pg 1-8). A source from the Council of Europe highlights that often cyberviolence is not taken seriously as it should; the violation starts online but might finally end up offline as it has devasting consequences to the families or friends of the attacked victim, an example, a threat of violence, suicidal incitements, stalking, a solicitation of a child for a sexual purpose can lead a victim self-harming or even an attack from the initial perpetrator. There is a total need to prevent cyberviolence from happening, protect individuals, bring victims justice, and punish those who do it. The vile can occur based on sex, disability, appearance, sexual orientation or race.
Examples of cyber violence are: Cyber-harassment is the broadest form of cyber-violence, involving persistent, repeated conduct that targets a specific person causing severe emotional distress or fear of physical, majorly targeting women and girls. Cybercrime; is the illegal access to confidential personal data, destruction of data, or blocking access to a computer system or data with a severe effect; imagine a fire emergency station with no access to calls. I.C.T. related direct threats, online sexual exploitation, and sexual abuse of children as highlighted in the Lanzarote Convection articles 18 and 23 and Budapest Convection article 9 to stress, sexual abuse, child prostitution, child pornography, soliciting of children for sexual purposes. I.C.T. –related hate crime and ICT-related violations of privacy (Kazan, 2022).
The Cyberthreat Defence Report; The CyberEdge 2021, provided a breath insight into cyber-related security and highlighted that almost 86% of U.K. entire organizations had experienced a cyberattack, which was an increase from the previous year’s study, which stood at 82.3%. Cyber violence is increasing due to evolving technological advancement, and increasing criminal capacity, causing more annoyance to individuals and a nation’s critical infrastructure by undermining its necessary instrumentalities.
The legal framework governing the problem
The U.K. has several legal frameworks about an issue just an example; is the Computer Misuse Act 1990, which highlights the various dimensions of criminal offenses; having access to an individual computer unauthorized, including an illicit copy of software held on any computer; this particular offense comes in hand with a penalty of up to six months imprisonment or a 5000Euros inclusion to this, hobby hacking, and potential penetration testing (Habibi Lashkari, 2022 pg 97-137). The second offense under the act is unauthorized access to either commit or facilitate the commission of further crimes such as fraud and theft, covering more severe cases such as hacking with criminal intent; the punishment for this is up to five years imprisonment with an unlimited fine. The third offense under the act is an unauthorized modification of any computer material, including intentional and unauthorized destruction of software, data, circulation of infected materials online, and unauthorized addition of passwords to data files—the consequences of this, are five-year imprisonment with an unlimited fine. The law acts as the legal defense against hacking, which allows the state to prosecute those found using computers for malicious purposes. The law has, however, been through amendments throughout the years being, in 1998, 2005, and 2008, this being that crimes are changing, technology advancement, not just working for various practitioners such as cyber security, and law enforcement officers, a lack of justified hacking and lacks to provide a scope for a hacking back this being that a particular individual that kind of gains unauthorized access to an attacker system would then find themselves incurring criminal liability.
Latest Statistical representation
The stats from the U.K. cyber security, and Cybercrime statistics in 2022, have noted a huge concern that cybercrime in the U.K. is not going away. The vice continues to be in the mind of individuals and businesses, having dire impacts on the country and the country. Both individuals and companies rely on an internet connection; malicious attackers are taking this advantage. In 2020, the government recently launched a new National Cyber Force to tackle the growing problem. From the stats, currently, more than 85% of the organization in the country have experienced successful attacks between 2020/and 2021; over twelve months, organizations have been affected by ransom attacks involving 71% of these organizations, and entire organizations’ I.T. expenditure accounts for about 11.2%. Cyber Edge highlighted that around 79% of U.K. total respondents are now preferring more technology advancements such as A.I. and machine learning in security products, ransom attacks in the country 39% of them were stopped before they happened, before data was encrypted, following cyber threats sent to organizations, 13% of the entire organizations ended up paying the ransom demanded by these cybercriminals, the cost associated with a ransomware attack in the country stands around 1.96 Million Dollars, due to the extent of the violation, 88% of the total U.K. organization have cyber security insurance, from the entire population around 10% of people have in 2020 opened a phishing link, around 2,300 Covid-19 malicious files have been detected since December 2020, these are just a few of the highlight provided in the report (Janicke, 2022). The country has lost around a 1.3billion Euros related to fraud and cybercrime between the first of January and 31ST July 2021, a published data by the National Fraud Intelligence Bureau.
Media representation
The media also has come in to highlight the level of the problem. A good example is the I.T. Governance blog publication by Luke Irwin (Miyamoto, 2020, pg 1-6).
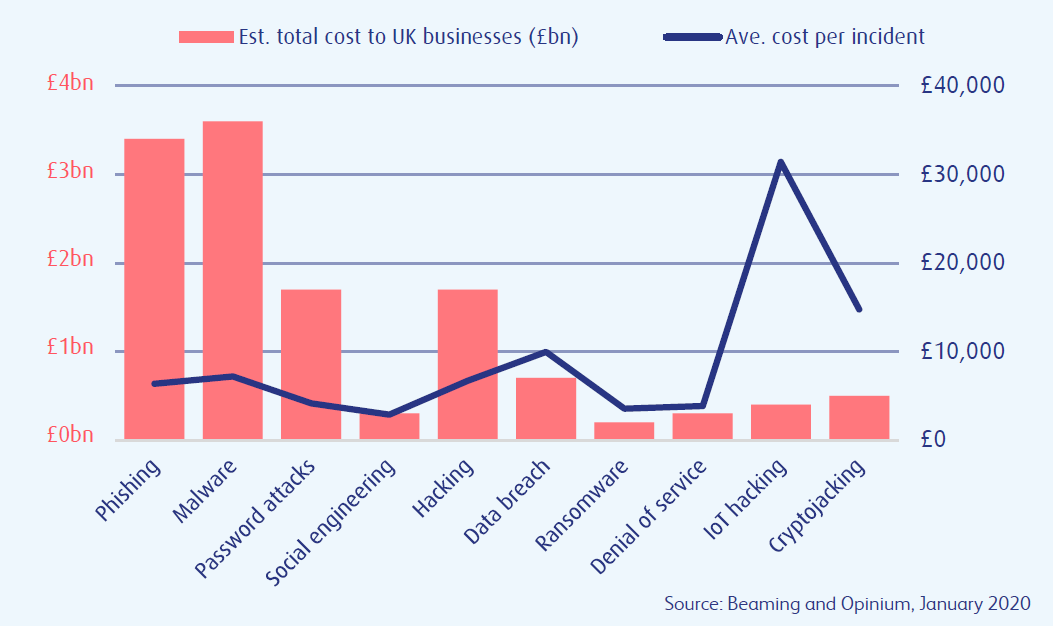
The publication, dated back on 6th July 2020, highlighted that U.K. businesses had severed various forms of cyberattacks against the total cost to U.K. businesses in Billion Euros against the average price per incident. The blog highlighted the effort of Beaming Five years in Cyber Security, where it accounted that U.K. businesses have lost close to 13Billion Euros brought by cybercrimes in 2019; this is not inclusive of asset damage, financial penalties, production loss, which would account for more than 87Bilion Euros. The average cost of the breach had fallen from 26000 Euros per incident back in 2015 to 6000 Euros in 2019. The blog also highlighted that organizations have and are now fighting back against the vice, where it highlights. However, there has been an increase in the last five years; the S.M.E.s and large corporates are improving, identifying the malware as a priority, with close to half of them have taken extra security precautions to handle the threat and highlighting major concerns that only 9% of the organization have a documented of cyber security policy, only 10% have cyber insurance, and only 10% have implemented an intrusion-detected system, put more emphasis on the importance of organization to take up strategies, holistic approach to cyber security rather than identifying specific threats and address them as they affect them.
Nature and Effectiveness of policy
There have been several policies take-up by the U.K. government in response to cyber violence to tackle the matter. Just an example, in 2016, the government set aside 860 Million Euros to set up the National Cyber Security Programme, the program being a five-year plan underpinned by £1.9 billion to make the U.K. more secure and resilient against cyber threats (H.S.M. 2019 pg 103-128). The project had objectives such as, defend looking to improve the country’s response to various incidents, increasing citizens’ knowledge of cyber threats, deterring; making the country a hard target for criminal attacks, develop; that being an innovation in building upon cyber security talents, and expertise that will help to the U.K. against future threats. The National Cyber Security Centre (NCSC) set up the program, which has had significant efforts to combat cybercrimes; in 2020, it responded to close to over 700 cyber incidents and has helped close to 1200 organizations handle cyber attacks the same way year. NCSC has set up the suspicious Email Reporting Services that enables the public to report any suspicious emails to a government address; in its first months, it received more than 2.3 million reports and took down over 22000 malicious URLs 9300 malicious web links. The center has built a cyber-talent aiming to encourage diversity in cyber security through CyberFirst, an initiative for students between the ages of 11 to 19 seeking to develop the next generation of cyber professionals, including bursaries and free courses, competition to encourage female talent through The CyberFirst Girls Competition. The center is looking to bring more room for improvement by helping in an indication of what more can be done; it also looks to have an ongoing commitment through public and private partnerships; yes, there might be something missing, but there can be significant attempts done to impact on the difference.
Journal publications
Several publications in terms of journals have been written, as academic writer looks to discuss more the topic, it has been there ever since, it’s not leaving us soon, gaining interest to talk more about it and how it can be handled, an example is the journal publication of Egyptian Journal of Forensic Sciences published on 10th February 2020, that look on cyber violence patterns on online surveys of females in Egypt a violation on bases of sex an emerging worldwide problem having a great impact on individuals and the society at large (Ali, 2020, pg 1-7). The journal tried to assess the situation of cyber violence against women among the Egyptian population; by sampling a total of 356 women by giving them questionnaires distributed through social media applications, it established that a total of 41% of women had had an experience in the previous year, with 45.3% of them have reported it multiple times of exposure, where the offenders remain unknown. Taking various forms; 41.20% received images with sexual images, 26.40% received insults through emails, 25.7% received humiliating or offensive comments, 21.6% received violent photos of demeaning women, and 20.3% received infected files through their emails. The attacks had severe impacts on the victims; 76.9% were affected psychologically by anger, worry, or fear, 13.6% were affected socially, 4.1% were exposed to physical harm, and 2.0% were affected by financial reporting losses.
Conclusions and recommendations
From the discussion, cyber violence is itself causing more harm, be it to individuals or corporate; just highlighting the discussion of the U.K. as a country, the impact it has had, further on the written journal on cyber violation on women shows that it is not a single country affair rather than a global issues. In my recommendation, I would suggest there need to be comprehensivity through a public-private partnership with both governments and privates corporates, discussion on international security forums, the governments should look to amend existing laws to stiffen up on the punishments allowing more comprehensivity, individuals should look to use stronger passwords, corporates should try using more firewalls that will block any unknown site connections, update the anti-spyware software, individuals should be more careful on what information they provide in the social media platforms, only look to download applications from trusted sources, companies should look to encrypt their data while purchasing online ensure you have enabled privacy settings and always ask for help from the rightful person.
Bibliography
Suárez-Relinque, C. and del Moral-Arroyo, 2022. Child-to-parent cyber violence: what is the next step?Journal of family violence, pp.1-8.
Kazan, 2022. Cyber Bullying and Violence Literacy in the Context of Digitalization. In Research Anthology on Combating Cyber-Aggression and Online Negativity (pp. 496-519). I.G.I. Global.
Lukings, M. and Habibi Lashkari, 2022. Global Relevance. In Understanding Cybersecurity Law and Digital Privacy (pp. 97-136). Springer, Cham.
Ferrag, M.A., Friha, O., Hamouda, D., Maglaras, L. and Janicke, 2022. Edge-IIoTset: A New Comprehensive Realistic Cyber Security Dataset of IoT and IIoT Applications for Centralized and Federated Learning. IEEE Access.
Taeihagh, A. and Lim, H.S.M. 2019. They govern autonomous vehicles: emerging responses for safety, liability, privacy, cybersecurity, and industry risks. Transport Reviews, 39(1), pp.103-128.
Hassan, F.M., Khalifa, F.N., El Desouky, E.D., Salem, M.R. and Ali, 2020. Cyber violence pattern and related factors: an online survey of females in Egypt. Egyptian Journal of forensic sciences, 10(1), pp.1-7.
Miyamoto, 2020, January. I.T. Governance under COVID-19 Era. In 2022 5th International Conference on Computers in Management and Business (ICCMB) (pp. 1-6).
 write
write