ABSTRACT
A shortage of fact validation and the inability or unwillingness to provide detailed research findings all adversely influence the results of online concrete proof judicial cases. Concerns have severe ramifications for convicts facing harsh sentences or imprisonment who expect their defense counsel to be well-versed in the facts. The information being improperly investigated, validated, and presented can lead to the conviction of the free from blame and the liability of the criminal. Child pornography is a crime. Case Study focuses on the subjects that seem to be plaguing situation examination and digital suggestion used in these heinous crimes, occupying more of law enforcement’s time, assets, and expertise.
Raising the bar and formalizing digital record examinations in kid pornography has come. Research work demonstrates how systematic analysis and presentation procedures can benefit investigations. Research emphasizes including rigorous validation techniques in cyber forensics tests to reach acceptable standards. The strategies described in Research Study help clarify case management while also maintaining that digital evidence is appropriately evaluated, contextualized, and authenticated.
INTRODUCTION
There is a considerable possibility of prosecutions since the judicial system understands even less about digital technology. The computer forensics industry occasionally takes advantage of this situation, obscuring the situation by focusing on storing, assembling, and displaying digital indications while keeping evidence verified under it or disregarded (Caloyannides, 2003). In the end, adjudicators must analyze the information. They misinterpret mistakes due to failed forensic analysis and presentation and unsuitable validation procedures. In that case, they will be forced to make wrong choices about the accused’s guilt. Regarding the discovery of baby Azaria Chamberlain at Ayres Rock over 30 years ago, coronial investigations, a legal case including disputed forensic data, and a Royal Commission into her terrible death, forensic methodologies in Queensland were fundamentally rethought (Carrick, 2010). In rare cases, digital evidence may fail to meet the stringent standards expected of more advanced forensics systems.
Criminal prosecutions based on digital data are becoming increasingly widespread, and examples in which innocent individuals are judged guilty are not unusual (George, 2004; Lemos, 2008) (George, 2004; Lemos, 2008). With no opposition reaction, defendants are admitting guilt, relying on what seems to be a huge amount of hearsay evidence, primarily digital data. The information may be convincing; the defendant may be financially strapped, the defense counsel may have misinterpreted the results, plea deals may result in reduced penalties, etc. Inability to report admissible data by the prosecution or a claimant, evidence taken out of context and misconstrued, failure to discover substantial proof, system, and software processing problems, and so on can all risk the facts’ credibility (Cohen, 2006; Palmer, 2002) (Cohen, 2006; Palmer, 2002).
The author has been providing professional digital records analysis to criminal defense lawyers in Western Australia since 2008. Computer evidence provided in state and federal law enforcement proceedings was re-examined and validated as part of this process. Thanks to the author’s re-examination and testing of forensic material. Several suspects convinced the jury of their guilt. The chosen Research Study, a child pornography ownership case in Western Australia, shows the common inadequate and incorrect findings found in digital forensics examinations of child pornography matters.
According to the Australian Federal Police, child pornography ownership and smuggling charges are becoming much more widespread in Australia, with a 30 percent increase in convictions for child pornography crimes in 2011 compared to 2010 (2012, Sydney Morning Post). Evaluating evidence to support accusations of criminal intent, including awareness and management of unsuitable material, is required in cases concerning child pornography. It is finding proof that establishes more than just ownership of the items necessitates abilities and experience in presenting evidence to demonstrate the suspects’ intentional acts. In other cases, linking the individual to the offense without sufficient evidence can occur relatively soon.
Officers who perform these critical but time-consuming responsibilities may be under-resourced and overworked with complicated matters, which unskilled analysts and broadcasters exacerbate. Anecdotal data suggests that these cases exist due to political lobbies aiming to eliminate unethical internet behavior through harsh, result-oriented laws. The fundamental difficulty with such a strategy is that it places undue pressure on examiners, putting innocent people at risk.
PROBLEMS OF ANALYSIS AND PRESENTATION
It is a typical occurrence in the digital arena for forensic examiners to neglect or misinterpret evidence, and even worse, to resort to ‘cherrypicking’ when selecting or to exclude evidence to attain a lawful advantage (Berk, 1983: Flush, 2001; Koehler & Thompson, 2006) If abductive logic was used in the case at hand, which is almost certainly was since it is common in such cases, it seems to be being done incorrectly.
Abductive reasoning is inferential reasoning that is most commonly applied in legal proceedings. It is predicated on a collection of acknowledged facts from which the most reasonable response is deduced (Australian Law Dictionary, 2012) (Australian Law Dictionary, 2012). On the other hand, deductive thinking abstracts directly from evidence, while inductive reasoning is based on facts but generalizes only partly beyond it. Abductive reason expands inductive reasoning considerably (Walton, 2004, p. 13) (Walton, 2004, p. 13).
Cases utilizing digital evidence are usually sophisticated, comprising several groupings of linked and unrelated information that make up the rope of truths’ myriad strands of realities. The issue for the auditor is recognizing and selecting information, which demands rigorous, unbiased argumentation. Although they are commonly misunderstood or ignored, every thread is important to the whole. Once the connections have been gathered to examine and test the information, validation is required. The evidence must then be presented in a readily understandable fashion that defines the data, emphasizes its importance and real power, and incorporates potential rebuttal relying on verification and other elements that may doubt the Claim.
CASE STUDY ANALYSIS AND PRESENTATION PROBLEMS
Even though the claimants’ innocence was less accessible than in the Prototype, subjective extrapolations based on a rudimentary understanding of the topic in the Research Study with no attempt to ensure consistent quality and accuracy were also prevalent in other child pornography cases investigated by the author.
The new report from the prosecutorial consultant provided no context for the groups of cataloged proof, their partnerships, or their outcomes concerning the criminal charge. The report lacked sufficient context to assist defense attorneys and defendants in comprehending the relevance of the data. There was no timetable, narrative, or comprehensive discussion of the significance of the displays. The lack of a credible case study design, verification, and a confusing analysis presentation by the prosecuting analyst presented a problem to the defense counsel. Based on the defense expert’s inadequate cross-examination, the prosecutor showed up to misread the digital information.
The prosecution analyst’s hasty application of the facts and assumptions about the authenticity of the evidence demonstrated a disrespect for the defendants’ stated integrity in the matter. The victim’s ownership and sole linkage to the network were critical to the collection and distribution allegations. There was no proof to back up that assertion, and there was no way to establish that other people had access to the files. Based on inductive logic, connections to child pornography websites and disturbing photographs and video files were purportedly employed as prima facie proof of guilt. Whatever criteria stood used to assess the cases’ merits from a prosecutorial standpoint looked subjective, with little consideration given to the possibility of different results.
Exculpatory computer evidence was obtained from operating and carved data, which had earlier been identified but ignored by the trial analyst’s Claim as “being unimportant.” Has either of the verdicts indicated that the defendant was neither the only nor the most notable suspect? Even though the presence of this information was recognized during the court appearance and the prosecution analyst’s cross-examination, it was not preserved or readily shared with the security side. In such cases, it is common for the police to re-examine the material to uncover new damning information and make relevant analysis presentations, which sometimes benefits the prosecution over the accused and opposes the defense strategy. Due to the apparent prosecution’s poor performance, defense analysts are unreasonable.
Others seemed the most probable culprits, even though they had been unlikely to encounter the same accusations as the defendant or be convicted of perjury while testifying. Other witnesses reported that one or both of these individuals were tenants at the defendant’s residence at the offense. Given that the available evidence disputed the views of two key witnesses, the writer stands mystified as to why the defendant was charged and not others Even the prosecution foresaw a deadlock in this case, but the judge has ordered that the procedures be continued and that the jury make the final decision.
The problem seems to be that forensic examiners submit declarations of information selection. Justification of why the samples were selected, on the other hand, Examiners should have knowledge and experience describing importance information related to additional important information.
POSSIBLE SOLUTIONS TO THE CASE STUDY’S ANALYSIS AND PRESENTATION ISSUES
According to Saunders, Toulmin’s technique, based on his The Design of Logic and Reasoning (1958) theory, has been used to generate arguments at different phases of the dispute. It succeeds for the constitutional case because of its precision, flexibility, and effectiveness (1994, p. 169). Toulmin (1958, p. 7) was concerned that acceptable arguments be founded on solid evidence and supported by concrete evidence. The model contains the components of inference and uncertainty in judicial reasoning and judgment and lawyers’ dependence on precedent and legislative authority (Saunders, 1994, p. 169). It incorporates a rebuttal aspect within the explanation, anticipating lawyer rejection of counterpoints. The forensics expert must go through the same procedure.
Official logic principles clashed with standard argumentation techniques for analyzing and analyzing public speech. When creating reasonableness criteria in court cases, lawyers utilized it to grasp the restrictions. There were six items to consider, as detailed below:
Data (object) –consists of evidence, truths, and information. It provides the argument’s foundation.
Warrant- establishes the rational relationship or logical procedure between the Facts and the Claim. The Accusation is the starting point for a rationale and expresses the arguer’s conclusion based on the Warrant’s Information.
Claim- is the point of an argument and represents the conclusion advocated by the arguer based on the Data linked to the Warrant.
Backing- is the material that supports and clarifies the Warrant’s reasoning Backing improves the credibility of an idea.
Qualifier- represents an argument’s validity, strength, and appropriateness.
Reservation (Rebuttal)- is an exception to the arguer’s Claim since arguments are not always genuine.
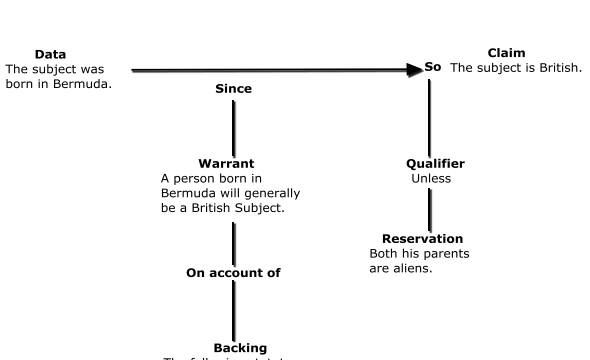
Fig1. Toulmin’s Model of Argumentation (Toulmin, 1958, p.105)
According to the Research Study, no consideration has been given to the possibility that relevant to the case information might exist. The data might not be correct, so no verification was done. Toulmin’s concept allows for creating templates that guarantee a more thorough and thorough data analysis. When Toulmin’s methodology remains used in the Research Study, the disorder is replaced by a detailed, complete, and systematic view of the aspects of the charge leveled against the accused.
VALIDATION PROBLEMS
Validity or accuracy in the case of cyber operations is defined by Sippl & Sippl (1980, p. 608) as a proportionate assessment of the achievement of being accurate, effective, and efficient, and data validity is described as a metric of validity. Such inspection linkages and evaluations must rely on tests and analytics to examine the database’s dependability, verify data, and determine the integrity of the evidence (Sippl & Sippl, 1980, p. 140).
While abstract law nears portrayal as it is regarded for usage in the ruling, it satisfies the requirements of the credibility and rightness of legal opinion that integrates conceptualization of the actual incident documented by dialect for the trial. At the same time, digital forensics is more useful to esoteric law advances depiction as it is displayed for implementation in the ruling is more relevant to forensic data (Azuelos-Atias, 2007.
VALIDATION ISSUES IN THE CASE STUDY
The prosecuting analyst found inferred ties between all of the exhibits in the Research Study. Still, she didn’t express the connection incomplete, meaningful words and didn’t present any proof of proved verification. These difficulties appear to be a recurring theme in the author’s previous child pornography research.
In the Testing Ground, the defense scientist claimed that the accused created technology that deleted browser cookies and recorded cache documents promptly, claiming that this was done to mask child pornography browsing. Instead of any relevant statistics that could have been acceptable if they had been available, the analysts’ expert judgment was used to make the broad assumption that software developers use anti-forensics software. It was all speculation. It was way outside professional opinion, and the prosecution never explored the defendant’s explanation. The subsequent scientific analysis demonstrated that the application was linked to a browser not downloaded on his machine; the Claim’s integrity was never investigated before it was presented to the jury. If the defense hadn’t questioned the jury, they would probably have accepted the rationale at face value. In its place of existence allowed to persuade the jury unfairly, this material should have remained examined and eliminated as illegal in the absences of the jury contingent on the outcome of a dispute between the administration analyst besides the minority consultant.
Child pornography surfing activity can be confirmed using search data, records, browser caches, and the user’s viewing and holding habits. Despite the accused’s explanations during his incarceration and subsequent interview, no attempt remained to link his browsing patterns to the machine’s alleged users. A simple validity check would have shown admissible data, increasing the likelihood that others were accessing and copying unlawful data without permission. To unswerving the truth, the verification technique comprises reconstructing browser activity and verifying and assessing every file.
POTENTIAL SOLUTION TO THE VALIDATION ISSUES IN THE CASE STUDY
Additional evidence, often referred to as hearsay evidence, can only be used in court when specific protocols remain (Anderson & Twinning, 1991). Suppose corporate documents, particularly digital records, are retained in the context of ordinary company activities. There is evidence that reasonable precautions remained undertaken to assure the records’ authenticity and accuracy. In that case, they are relevant to the case as exceptions to the ordinary hearsay rule (Chaikin, 2006).
When circumstantial evidence cannot be proven, Western Australian law gives suspected people the benefit of the doubt, just like other nations. Updated photos found over data cutting of local disks. For example, they will be declared useless during a hearing if they cannot remain validated by other indications (SOWA versus Sabourne, 2010); as a result, information and records demonstrate identification may be considered a vital part of the verification system.
In forensics, evaluating evidentiary weight needs a validation check and analysis of the acceptance and trustworthiness of digital information, followed by verification of confirmation Corroboration implies showing the presence of objective evidence to verify the display and its connection with the previous exhibit. Sufficient facts were legally obtained; believable information stood acquired in a meaningful, accurate, and consistent way with validated data, and supporting evidence remained achieved by demonstrating the presence of actual evidence to verify the screen and its ability to connect to the prior display.
Checking entails thoroughly inspecting and gaging every piece of evidence, as well as the connection between supporting exhibits, to determine their evidential weights:
Testing an exhibit to determine the integrity of the information, metadata, and relationships with other displays are known as verifying. The period of removal of the Internet browser, for example, was obtained from the Recycling center, contrasted to the defendant’s alibi, matched with the laptop clock, and then validated against other actions to complete the verification procedure in the Research Work.
Experiments established research data or credible statistics are used to assess the validity of display relationships.
The defendant was accused of purposefully uninstalling the browser to hide illegal browsing behavior in the Research case. Matching the time of the browser’s erasure (later proven to be deletion) with the defendant’s location demonstrated that the defendant was not around and could not have been involved, according to an alibi. There is no need for more testing because the evidence is irrelevant and must be dismissed.
The figure below depicts the admissibility checking of the major exhibit, which includes plausibility testing to establish the evidence’s relevancy, accuracy, and coherence (unambiguity) For example, deciding whether the updates are relevant to other Web users; checking for complexities in timestamps that are vague as to whether they were modified or significantly altered of this other methodology; identifying the exactness of period stamps to establish whether the documents are pertinent to the matter.
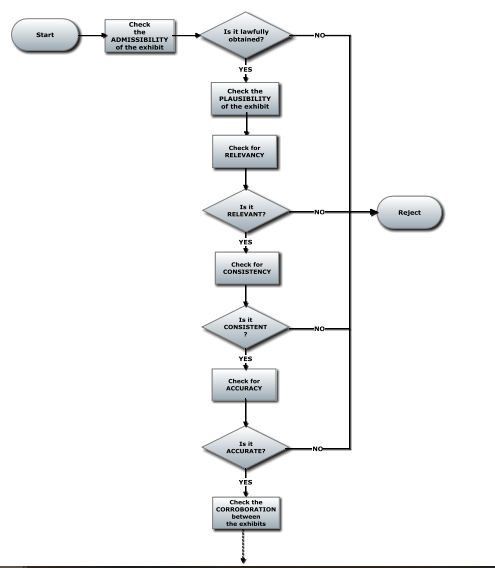
Fig2 Examination the significance, accuracy, and uniformity during the plausibility stage
The procedure was then put through its paces in the verification process. The verifying display and the relationship between the primary and supportive exhibits were examined and verified. Relevance validating to see if a canceled file was comparable to a document; observance having checked to see if a redacted file remained related to a composition shown in a software log or other files with the same name. Precision checking to show a link between web surfing and severe other user occurrences are all examples of how it can be used to confirm between screens.
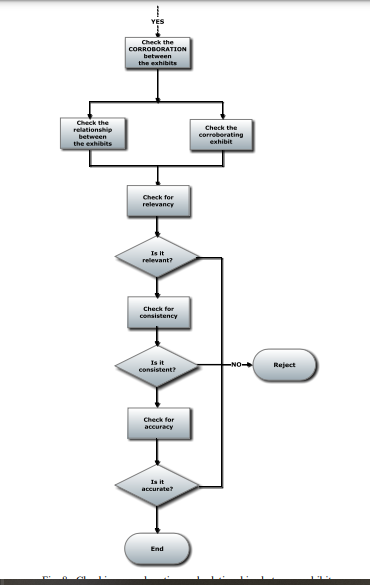
Fig3 Examining exhibit linkages and corroboration
The method can then be used to measure the weight of every piece of evidence and the total weight of legal evidence. The procedure ensures that all relevant material is reviewed and presented with increased transparency in child pornography trials and other digital scientific proof matters. Significant validation concerns are less likely to be overlooked or trivialized due to the process. Although this Research Study does not address the challenges of incorporating and evaluating outcomes that influence the truth’s validity, it does provide the instruments to assess the strength of each display and evidence thread in the scenario.
CONCLUSION
Minimal logical reasoning is found in the Research Study, exacerbated by the poor presentation of fundamental facts, which remains further harmed by insufficient digital information verification. Regardless of whether they are guilty, everybody in court must seek full and accurate information. It’s logical to assume that extensive methods were utilized to assess the evidence’s accuracy and completeness and that the results are accurate and reflect what it claims to support. The case should ideally proceed using the best available research evidence, confirming that it is, to a reasonable accuracy, what it appears to be.
Validation entails a thorough evaluation of the evidence’s legality, validity, and verification. Via well-argumentation models like Toulmin’s model to provide evidence that has been well validated has a lot to recommend. Complete and accurate validation of electronic evidence presented openly is vital, and it considerably aids both the forensic expert and the judicial officer. It ensures that the information assessment is subjected to objective inspection and inspection; it holds the inspector responsible and fosters detailed and thorough data for high grade. Most importantly, it pursues reality without prejudice, which is a hallmark of forensic science.
The author approved Toulmin’s model and validation techniques in research events and has already seen enhanced case administration and contact with legal practitioners. More research into fine-tuning verification to service a variety of case situations looks to be required.
Bibliography
Ajoy, P. B. “Effectiveness of Criminal Law in Tackling Cybercrime: A Critical Analysis.” Sch Int J Law Crime Justice 5, no. 2 (2022): 74-79.
Belshaw, Scott, and Brooke Nodeland. “Digital evidence experts in the law enforcement community: understanding the use of forensics examiners by police agencies.” Security Journal (2021): 1-15.
Belshaw, Scott, and Brooke Nodeland. “Digital evidence experts in the law enforcement community: understanding the use of forensics examiners by police agencies.” Security Journal (2021): 1-15.
Horsman, Graeme. “Defining principles for preserving privacy in digital forensic examinations.” Forensic Science International: Digital Investigation 40 (2022): 301350.
Stoykova, Radina. “Digital evidence: Unaddressed threats to fairness and the presumption of innocence.” Computer Law & Security Review 42 (2021): 105575.
 write
write