PART 1
PART 2
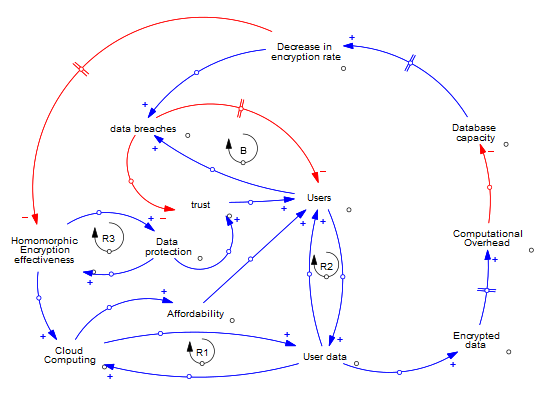
Diagram Discussion
My causal loop diagram aims to illustrate the application of Homomorphic Encryption (HE) in Cloud computing technology. “In cloud computing, fully homomorphic encryption is commonly touted as the holy grail of cloud security” (Gentry, 2009). The existence of periodic modifications with HE allows us to be aware of the limitations that still occur with every new modification. “With the wide application of cloud computing, the security of cloud platform has become one of the core issues of cloud computing, which restricts the development of cloud computing. Homomorphic encryption can directly process cipher text data, effectively ensuring the security of cloud user data” (Min Zhao, E. 2019). Therefore, my causal loop diagram (CLD) indicates variables that represent factors associated with CC and FHE.
The variables in my system are required to comprehend the functions of HE and its benefits and drawbacks. The balancing loop between users and data breaches is an important feedback loop. The very essence of HE is to be able to protect its users’ data through encryption methods, and data breaches undermine this goal. This feedback loop serves as the primary regulator of the system, cancelling the effect of the reinforcing loop and bringing it to equilibrium. The affordability of CC affects users, making more people interested in using it.
Another essential dynamic to consider is the unilateral directional flow between users’ data and the decreased encryption rate. Encrypted data bulked over time from the availability of more users’ data leads to computational overhead, which is the combination of excess or indirect computations; in this dynamic, each variable influences the other and hence indicates unilateral influence. One of HE’s significant limitations is computational overhead; this affects the encryption rate’s effectiveness and makes data more susceptible to attack. This unilateral flow allows us to see the negative consequence of implementing HE into this system.
Other relevant feedback loops would be R1, R2 and R3. They emphasize the exponential growth/increase from one to the other, which establishes a negative HE property leading to data breaches. They can also be positive reinforcing loops that help to indicate virtuous acts because CC and HE create storage capacity for users and offers data protection, respectively. They also indicate signs of proportionality, where if one were to go down, so would the other.
Users will be the primary stakeholders in my system because many other variables, such as data breaches and trust in the system, influence them. Users in my system are susceptible to the significant benefits and drawbacks my system provides. Remoulding cloud servers in cloud computers to increase the number of databases available will be a way of intervening to create desired change. As a result, user data is not stored in a single location, resulting in computational overhead. This improves the ethical outcomes for users because it is a way to manage the existing limitations, thus eliminating or managing data breaches and allowing users to trust this encryption method. My CLD spans the last five years because FHE was incorporated with CC. Because previous versions of HE could not perform specific tasks, the period is critical.
My diagram shows substantial delays between database capacity and a decreased encryption rate. These delays harm my system because they can quickly go unnoticed, making it hard for skilled labour to assess the issues and propose solutions. They also take time to impact the system negatively. An intervention intended to improve the system may be incorporating the optimum population theory, which is instead of allowing the maximum number of users to make use of a database that all require their data to be secured with HE, we allocate specific numbers of users that can be on a database at a particular time. The result of this is regulating data flow and minimizing overhead.
An archetype behaviour that is observed in this system is the tragedy of the commons. HE identifies as a commons because it is used by many and satisfies the criteria of being a commons because it has finitude, where there is a maximum level of consumption(usage) of this technology before its availability is maximized. It is also the source because users have their data secured. In my causal loop diagram, we observe that increasing the number of users over time can lead to computational overhead, which decreases HE’s effectiveness in time. This is where the tragedy exists. Therefore, it is necessary to implement strategies to maintain this commons by privatizing or regulating it.
Leverage points in the system are the existence of feedback loops, where the reinforcing loops cause an exponential increase in the use of the system and lead to a negative property. It is regulated by the balancing loop, where the number of users decreases due to more data breaches. All of which are vital components of my system.
PART 3
Application of Virtue Ethics.
Homomorphic encryption
Homomorphic encryption (HE) has proven to be an effective encryption method because of its mode of encryption that distinguishes it from standard encryption methods. However, despite this significant benefit, HE has also been observed to possess some drawbacks, which diminishes its effectiveness with its users. Recognizing that eudaimonia comes from a Greek word, which means happiness, Aristotle explains that happiness is more satisfying than satisfaction and that one must possess virtues (Van Zyl, 2019).
The main advantage of HE, which is to provide maximum data protection for its users, has a positive impact because we observe that through this means, individuals, organizations, and so on have the safety of their confidential data guaranteed due to the thorough processes that are involved in bringing this encryption method to fruition. After close observation over the years, we recognize the success of HE over other encryption methods. On the other hand, the main disadvantage of HE, which is the existence of limitations despite its modifications over time, concerns its users. This reduces users’ trust in this encryption method, calling its effectiveness into question. After observing its evolution over time, users may need more convincing that HE is the safest and most effective way to encrypt confidential data.
Perseverance
Perseverance is persistence in doing something despite difficulties or delays in achievement. It is a virtue helpful to engineers and computer scientists when making decisions based on HE, because it requires one to be resilient in their actions and working in the engineering field, one must be perseverant in their course of actions to produce the best result. Considering the rigorous activities engineers and computer scientists engage in, it is necessary to have this virtue when dealing with projects with a wide human and environmental impact. It is common to encounter challenges when working on a project like the implementation of HE; therefore, it is necessary to be aware that this task calls upon one’s optimism, effectiveness, and resilience.
Pertinacity/intransigence is an excess of perseverance, which is pursuing a goal/objective even when it is no longer worthwhile or becomes self-destructive. A lack of perseverance could be caused by laziness, which is a disinclination to act or exert oneself despite having the ability to act or exert oneself. Perseverance is the middle ground between these two extremes because we practice it while being aware of the ongoing effort required, the need for rest and rejuvenation, and when it is necessary to propose trying alternative methods to achieve the same goal.
Connecting the Two and Explaining How it Leads to Eudaimonia (The Universal Good or Human Flourishing)
Homomorphic encryption (HE) requires perseverance because it is necessary to develop the system’s capabilities and trust in users. HE has been worked upon for many years with limitations with every modification, yet people still consider it the safest way to secure private data. Engineers and computer scientists must incorporate this virtue prudently in their years of research and technology modifications as we observe the impact HE has on its users. The perseverance to create a system that functions optimally reflects the Aristotelian view of ethics by implications of practical wisdom and efficacy (Van Zyl, 2019). This virtuous decision dramatically impacts the eudaemonia of the users because it is necessary to consider what influences our technology has on human beings.
References
Ko, R., Choo, K. (2015). The cloud security ecosystems. Singress. https://doi.org/10.1016/B978-0-12-801595-7.09989-4
Little, S. (2021, May 18). The vices of perseverance. https://www.irunfar.com/the-vices-of-perseverance.
Min Zhao, E., Yang, G. (2019). Homomorphic encryption technology for cloud computing. Procedia computer science Vol. 154 p. 73-83. https://doi.org/10.1016/j.procs.2019.06.012
Yahoo! (n.d.). Perseverance+definition. Yahoo! Retrieved November 13, 2021, from https://search.yahoo.com/search;_ylt=A0geJaQ.JohhgUgA4BhXNyoA;_ylc=X1MDMjc2NjY3OQRfcgMyBGZyA21jYWZlZQRmcjIDc2EtZ3Atc2VhcmNoBGdwcmlkA1ZNWlptYmhNVE95TmZJMHRNbWg0MUEEbl9yc2x0AzAEbl9zdWdnAzEwBG9yaWdpbgNzZWFyY2gueWFob28uY29tBHBvcwMyBHBxc3RyA3BlcnNldmUEcHFzdHJsAzcEcXN0cmwDMjMEcXVlcnkDcGVyc2V2ZXJhbmNlJTIwZGVmaW5pdGlvbgR0X3N0bXADMTYzNjMxMjk0OAR1c2VfY2FzZQM-?p=perseverance%2Bdefinition&fr2=sa-gp-search&fr=mcafee&type=E211US1451G0.
Zyl, V. (2019). Virtue ethics a contemporary introduction. Routledge, Taylor & Francis Group.
 write
write