Major hardware and software components Amazon’s information systems infrastructure
Amazon’s information systems infrastructure is a complex hardware and software network that supports the company’s e-commerce operations. Its infrastructure includes a wide range of systems, such as databases, servers, network equipment, and software applications, that are designed to work together seamlessly to ensure the smooth operation of the company’s online platform. The infrastructure is designed to support the high volume of daily data and transactions the company handles. Additionally, it is to be scalable, flexible, and highly available to meet the demands of the company’s rapidly growing customer base. Amazon’s information systems infrastructure is critical to the company’s ability to provide customers with an efficient and reliable shopping experience.
Hardware components of Amazon’s infrastructure
The foundation of Amazon’s information systems infrastructure is a vast network of servers and data centres. These servers are built with high-performance, multi-core processors and large amounts of RAM and storage. To handle the large traffic volume and ensure high availability, Amazon employs load balancers and caching servers (Jindal et al.,2021). Backup servers and disaster recovery systems are also implemented to ensure data security.
Amazon’s information systems infrastructure relies heavily on a robust and reliable network infrastructure. It includes a combination of wired and wireless networks and a variety of networking devices such as routers, switches, and firewalls. These devices are used to route and secure data traffic between the various components of the infrastructure (Jindal et al.,2021). Amazon uses multiple networking protocols like TCP/IP, HTTPS, and VPNs to ensure secure and fast data transfer.
Also, Amazon’s information systems infrastructure heavily uses cloud computing services, such as Amazon Web Services (AWS). It allows the company to scale its resources up or down as needed and to only pay for the resources it uses. Additionally, it will enable the company to store and process data in different regions worldwide, providing faster customer access times (Jindal et al.,2021). This cloud infrastructure is built on a distributed architecture, allowing fault tolerance and high availability.
Amazon’s information systems infrastructure utilizes several databases to store and manage data. These include relational databases, such as MySQL, and NoSQL databases, such as MongoDB and Cassandra. These databases store customer information, product information, and transaction data. Amazon also uses big data technologies like Hadoop and Spark for large-scale data management and processing.
Amazon’s information systems infrastructure also includes a search engine that allows customers to quickly and easily find products on the website. This search engine is likely on a technology such as Elasticsearch, designed to handle large amounts of data and provide fast search results (Jindal et al.,2021). Amazon uses machine learning algorithms to analyze user behaviour and search patterns to provide personalized search results.
Amazon’s information systems infrastructure includes a Content Delivery Network (CDN) to ensure customers can access the website quickly and smoothly. A CDN stores copies of content on servers located in different geographic locations, allowing customers to access the content from the closest to them (Jindal et al.,2021). It also reduces the load on the primary servers and improves overall performance.
Amazon’s information systems infrastructure includes a variety of security measures to protect customer data and prevent unauthorized access. These measures include firewalls, intrusion detection, and prevention systems, and encryption technologies. Additionally, Amazon has implemented various policies and procedures to ensure compliance with security regulations. It includes regular security audits and penetration testing to identify and fix vulnerabilities.
Software components of Amazon’s infrastructure
Amazon’s information systems infrastructure relies heavily on various software applications to support its operations. These include e-commerce platforms, such as Magento or Shopify, customer relationship management systems, enterprise resource planning systems, and analytics and business intelligence tools. These software systems manage and analyze customer data, manage inventory, process transactions, and support marketing and sales efforts (Aljamal, El-Mousa & Jubair, 2019). Amazon also uses various workflow management and automation tools to help with business-process automation.
Artificial Intelligence and Machine learning: Amazon’s information systems infrastructure also includes various AI and ML technologies to provide customers with a personalized and seamless shopping experience. It includes recommendation engines, chatbots, and natural language processing (NLP) systems (Aljamal, El-Mousa & Jubair, 2019). These technologies also help automate various tasks such as pricing optimization, inventory management, and fraud detection.
Amazon’s hardware and software from a size, scale, type, and interoperability standards perspective
Amazon’s e-commerce company is a vast and complex system that requires high scalability, flexibility, and availability. By using a mix of proprietary and open-source systems and implementing industry-standard protocols and technologies, Amazon ensures that its methods can communicate and work together seamlessly, providing a seamless experience to its customers.
From a size and scale perspective, Amazon’s e-commerce company would likely use a distributed architecture for its hardware and software systems. It would include a large number of servers for database storage, as well as multiple proxy servers for load balancing and to improve performance. Network equipment would also distribute and highly available, focusing on redundancy and failover capabilities. In terms of type, Amazon would likely use a mix of both proprietary and open-source systems (Williamson et al.,2022). For example, they might use a proprietary database management system like Oracle or SQL Server for their primary data storage. However, they might use open-source tools like Hadoop and Spark for big data processing and analytics. Additionally, Amazon would use services from their AWS (Amazon Web Services) for most of their services.
Interoperability standards would be a key consideration in the design of Amazon’s systems. The company would likely implement industry-standard protocols and technologies, such as HTTP, HTTPS, and TCP/IP, to ensure that its systems can communicate and work together seamlessly (Duda et al.,2022). Additionally, Amazon would likely use APIs (Application Programming Interfaces) to allow external systems to interact with its platform and provide access to data and functionality. The company would also use web services such as SOAP and REST to provide interoperability between different systems.
For Content Management, Amazon would likely use a Content Management System (CMS) that allows them to manage and organize their digital content. Depending on their specific requirements and needs, it could be a combination of proprietary and open-source systems. They would also use tools like AWS’s CloudFront for their CDN (Content Delivery Network) for faster customer content delivery (Palmatier & Martin, 2019). All these systems would be orchestrated and monitored by robust system management and monitoring tools like AWS CloudWatch, AWS Elastic Beanstalk, and Kubernetes to ensure the systems are up, running, and healthy.
| Factors | Hardware | Software |
| Size and Scale | Distributed Architecture | Distributed Architecture |
| Type | Proprietary database management system | Open-source tools |
| Inter-operability standards | Standard protocols and technologies and APIs | Standard protocols and technologies and APIs |
| Content Management | Proprietary and open-source systems | Proprietary and open-source systems |
Potential security vulnerabilities and a security design for Amazon e-commerce company
Security is critical for any e-commerce company, and Amazon is no exception. The company handles sensitive information, including customer personal and financial data and sensitive business information. As such, the company must take the necessary steps to protect this information from unauthorized access, misuse, or theft. Security is a complex and ever-evolving field, and Amazon needs to stay up-to-date with the latest threats and vulnerabilities (Ehikioya & Guillemot,2020). By implementing a comprehensive security program and a robust incident response plan, they can help protect their customers’ information and ensure the security and integrity of their systems.
One potential security vulnerability for Amazon is the risk of data breaches. It can occur when an attacker gains unauthorized access to the company’s databases and steals sensitive information. To mitigate this risk, Amazon must implement robust access controls and authentication mechanisms to ensure that only authorized individuals can access the company’s databases. Additionally, they could use encryption to protect data in transit and at rest, making it more difficult for attackers to access or read the stolen data (Ehikioya & Guillemot,2020). Another potential vulnerability is the risk of Distributed Denial of Service (DDoS) attacks. DDoS attacks occur when an attacker floods a website with traffic, causing it to become unavailable to legitimate users. To protect against this attack, Amazon could implement a DDoS protection service, such as Cloudflare, that can detect and block malicious traffic.
Another security vulnerability that Amazon could face is attacks on its web application. These attacks target the application’s vulnerabilities, such as SQL injection, cross-site scripting, and cross-site request forgery (Luo & Choi,2022). To mitigate this risk, Amazon must ensure that its web applications are designed with security in mind and regularly tested for vulnerabilities. Additionally, they could use web application firewalls (WAFs) to protect their web applications from common attacks.
A security design for Amazon would include implementing a comprehensive security program that provides regular security assessments and penetration testing to identify and address vulnerabilities. They would also implement a robust incident response plan to quickly and effectively respond to security incidents. Amazon would also have a dedicated security team responsible for monitoring the network and systems for unusual activity and researching and staying up-to-date on the latest security threats and vulnerabilities (Luo & Choi,2022). In addition, Amazon would also ensure compliance with industry standards and regulations such as Payment Card Industry Data Security Standard (PCI DSS), General Data Protection Regulation (GDPR), and Health Insurance Portability and Accountability Act (HIPAA) to protect their customer’s data.
Data flow diagram for Amazon
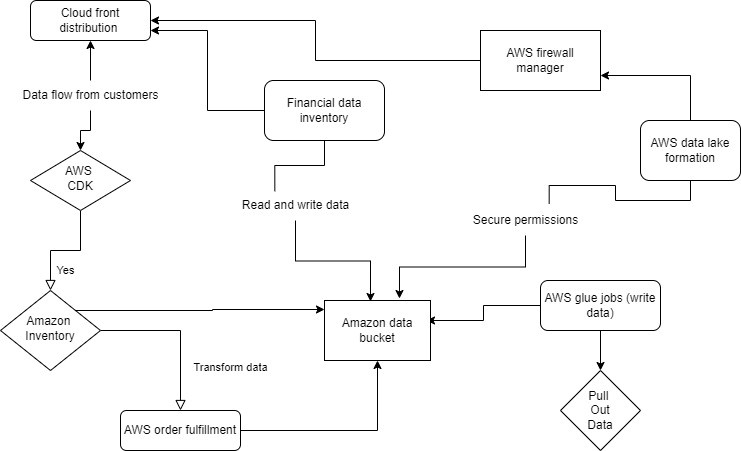
Cloud front distribution
Customer data flows from customers to Amazon’s systems when they purchase on the website or mobile app or interact with customer service.
Suppliers’ data flows from suppliers to Amazon’s systems when they send inventory information or update product details.
Processes before data transmission
- Data validation: This process ensures that all incoming data is accurate and complete.
- Inventory management: This process manages the flow of products in and out of Amazon’s warehouses.
- Order fulfilment: This process handles picking, packing, and delivering the product to the customer.
- Financial reporting: This process handles the financial data of Amazon’s business, like revenue and profit.
AWS data lake for data storage
Customer database: Represented by a symbol of a computer disk, this data store holds information about all of Amazon’s customers, including their purchase history and contact information.
Product database: Represented by a symbol of a computer disk, this data store holds information about all of Amazon’s products, including their descriptions, prices, and inventory levels.
Order database: Represented by a symbol of a computer disk, this data store holds information about all of Amazon’s orders, including their status and shipping information.
Data flow
Data flow from customers to data validation: Represented by a line with an arrow pointing from the customer symbol to the data validation symbol, this flow represents the data that customers provide when they make a purchase or interact with customer service.
Data flow from data validation to inventory management: Represented by a line with an arrow pointing from the data validation symbol to the inventory management symbol, this flow represents the data that has been validated and can be used to update inventory levels.
Data flow from inventory management to order fulfilment: Represented by a line with an arrow pointing from the inventory management symbol to the order fulfilment symbol, this flow represents the data used to pick, pack, and ship products to customers.
Data flow from financial reporting to financial database: Represented by a line with an arrow pointing from the financial reporting symbol to the financial database symbol, this flow represents the economic data used to generate financial reports.
References
Aljamal, R., El-Mousa, A., & Jubair, F. (2019, April). A user perspective overview of the top infrastructure as a service and high-performance computing cloud service providers. In 2019 IEEE Jordan International Joint Conference on Electrical Engineering and Information Technology (JEEIT) (pp. 244-249). IEEE. https://ieeexplore.ieee.org/abstract/document/8717453
Duda, O., Kunanets, N., Matsiuk, O., & Pasichnyk, V. (2022). Cloud-based IT Infrastructure for “Smart City” Projects. In Dependable IoT for Human and Industry (pp. 389-409). River Publishers. https://www.taylorfrancis.com/chapters/edit/10.1201/9781003337843-23/cloud-based-infrastructure-smart-city-projects-oleksii-duda-nataliia-kunanets-oleksandr-matsiuk-volodymyr-pasichnyk
Ehikioya, S. A., & Guillemot, E. (2020). A critical assessment of the design issues in e‐commerce systems development. Engineering Reports, 2(4), e12154. https://onlinelibrary.wiley.com/doi/full/10.1002/eng2.12155
Jindal, R. P., Gauri, D. K., Li, W., & Ma, Y. (2021). The omnichannel battle between Amazon and Walmart: Is the focus on delivery the best strategy? Journal of Business Research, 122, 270–280. https://doi.org/10.1016/j.jbusres.2020.08.053
Luo, S., & Choi, T. M. (2022). E‐commerce supply chains with considerations of cyber‐security: Should governments play a role? Production and Operations Management, 31(5), 2107-2126. https://onlinelibrary.wiley.com/doi/abs/10.1111/poms.13666
Palmatier, R. W., & Martin, K. D. (2019). Understanding and valuing customer data. The Intelligent Marketer’s Guide to Data Privacy, 133–151. https://doi.org/10.1007/978-3-030-03724-6_7
Williamson, B., Gulson, K. N., Perrotta, C., & Witzenberger, K. (2022). Amazon and the new global connective architectures of education governance. Harvard Educational Review, 92(2), 231-256. https://meridian.allenpress.com/her/article-abstract/92/2/231/483738/Amazon-and-the-New-Global-Connective-Architectures
 write
write