In today’s corporate world, information technology (IT) plays an essential part as the basis of the company’s activities. As organizations depend more on networked infrastructure, the threat of IT compromises has become a serious perturbation. The paper examines the multidimensional structure of technological IT intrusions in a conventional company setting. Envisioning an ever-changing digital corporate environment depicts a scenario in which data flows fluidly across divisions, consumers, and partners. Nevertheless, such interconnection exposes weaknesses that attackers might prey on, risking the confidentiality, integrity, and availability of critical data. The article intends to provide enterprises with knowledge for fortifying their technological frontiers in the midst of developing cyber-attacks by analyzing breach kinds, emphasizing their relevance, and suggesting creative defence measures. IT security is more than an option; it is a must for long-term corporate prosperity in today’s linked and digitalized planet.
A Digital Business Environment
Creating a strong digital corporate setting entails imagining an ever-changing ecosystem in which data moves effortlessly through divisions, consumers, and partners. The situation is distinguished by a cloud-based architecture, networked gadgets, and a wide range of apps that enable effective functioning and interaction. Nevertheless, although interconnection increases output, it also offers weaknesses that attackers might abuse. Resolving such weaknesses is critical to ensure the safe operation of the digital ecosystem. The section will go into the complexities of a comparable ecosystem, outlining possible vulnerabilities that might be exploited in various forms of IT intrusions.
Types of Digital IT Breaches
Phishing Attacks
Phishing assaults are a persistent and subtle danger to the digital corporate environment. Phishing methods, characterized as deceptive efforts to gain confidential data including credentials or billing addresses, depend on individuals’ vulnerability to social engineering (Jena, 2023).
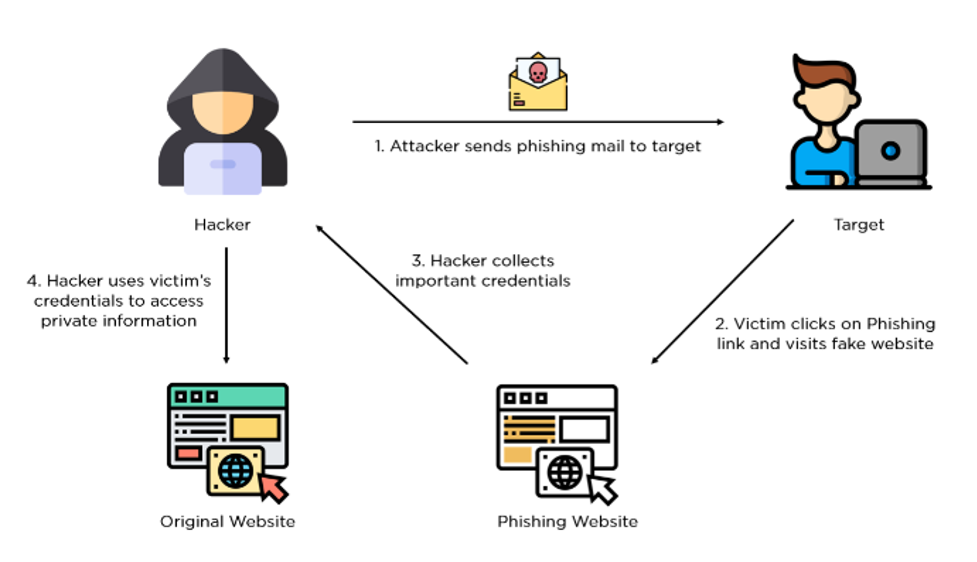
Figure 1: Flow chart of phishing attack (Jena, 2023)
Figure 1 is a flow chart of the phishing attack process. Personnel, the primary layer of security, are frequently pursued by misleading emails or texts mimicking reputable companies. The susceptibility rests in the human factor, thus vigilance and training are essential. In minimizing the danger of becoming vulnerable to phishing attempts, businesses should engage in extensive staff orientation initiatives, set up powerful spam filtering mechanisms, and implement multi-factor verification (Jena, 2023). Companies may dramatically minimize the risk of successful phishing attacks by strengthening their human shield and preventing confidential data from getting into unauthorized people.
Malware Attacks
Malware attacks are a danger to the security of a computerized corporate setting. Malware is characterized as malicious programs that aim to interfere, harm, or obtain illegal control over computing devices by exploiting peripheral loopholes and obsolete programs. The risk grows as fraudsters adapt their approaches. Safeguarding from malware necessitates an anticipatory strategy, which includes frequent software upgrades that fix weaknesses, the use of strong antivirus products, and the installation of end users’ security methods (TechTarget, 2024).
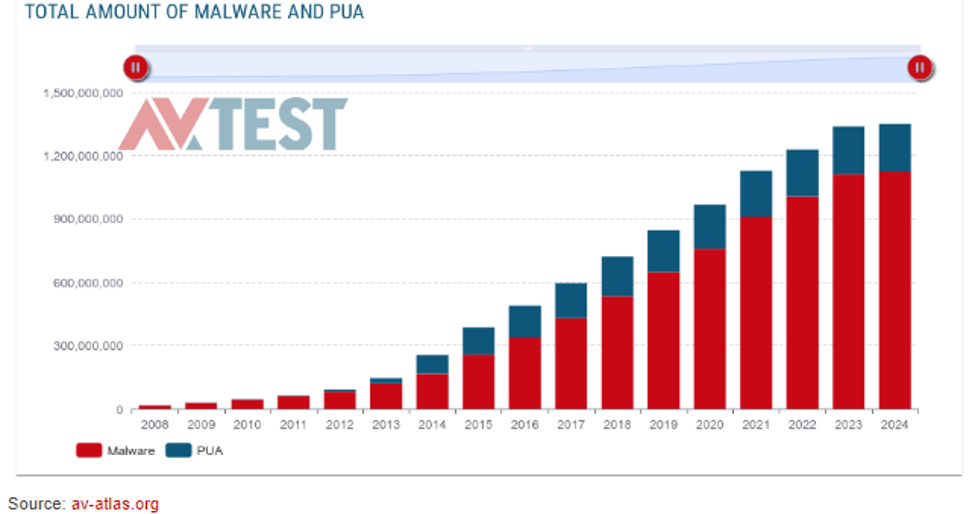
Figure 2: Graph of the Total Amount of Malware and PUA over the Years (AV-TEST, 2024)
Figure 2 shows how malware attacks have been rising over the years. By tackling such weaknesses, businesses may build an effective barrier against the constantly growing range of malware attacks, protecting their computer systems and sensitive information from unwanted entry or alteration.
Insider Threats
Internal threats, caused by malevolent intentions or unintended behaviors, are a distinct and sometimes overlooked danger in the digital company world. The risk originates from weak accessibility restrictions and oversight measures, which enable workers or spies to take advantage of their privileged status. Companies must create strict accessibility policies to restrict exposure to confidential data depending on their position. Furthermore, continual tracking by modern security technologies may reveal aberrant activity, offering early warning signs of possible internal threats. Engaging in extensive employee education initiatives to enhance secure data knowledge and promote a responsible attitude can help reduce the likelihood of insider attacks (TechTarget, 2024). By mitigating such weaknesses, businesses can strengthen their security against internal intrusions.
Denial of Service (DoS) attacks
Denial of Service (DoS) assaults have substantial impacts on the availability and operation of internet-based company networks. Such assaults entail overloading an infrastructure or network and making it unreachable to authorized consumers. Vulnerabilities stem from the absence of a strong networking architecture that can overcome such attacks. To minimize the danger of DoS assaults, companies should install preventative technologies such as intrusion detection systems, firewalls, and information distribution systems. Firewalls serve as the primary layer of protection, screening incoming traffic, whereas intrusion prevention technologies identify and counteract hostile activity in real-time. Utilizing content delivery networks assists deliver and handle traffic effectively, decreasing the consequences of DoS assaults and providing continuous accessibility to internet-based operations (TechTarget, 2024).
Importance of Protecting Vulnerabilities
Data Confidentiality
Data confidentiality is an essential element in the world of online companies, protecting private data from unwelcome disclosure. Compromise of data confidentiality can have adverse implications, namely monetary harm and negative publicity. In a world of technology where large volumes of private information travel across systems, maintaining the secrets of business content is crucial. For safeguarding confidential information, businesses must establish secure encryption mechanisms, access restrictions, and safe transmission technologies (Hashemi-Pour & Chai, 2023). Setting priorities for keeping information confidential protects organizations from regulatory and fiscal ramifications to maintain the confidence of customers and other partners in a world wherein data integrity is an unavoidable component of effective functioning.
Operational Integrity
Operational integrity is the foundation for long-term corporate performance, and compromises can have serious implications. Breach-related delays can lead to lost revenue, reputational harm, and a drop in consumer confidence. Sustaining organizational integrity in an internet-based corporate context requires protecting networks against cyber-attacks that might disrupt the smooth flow of daily activities. Businesses must have robust safety protocols, undertake frequent risk evaluations, and guarantee the robustness of vital technology (Hashemi-Pour & Chai, 2023). Operational integrity helps organizations reduce the likelihood of interruptions and improve their capacity to adjust and grow in an ever-changing digital world, encouraging sustainability and endurance.
System Availability
System availability is critical to the dependability of online amenities, and compromises may result in profound effects. Denial of Service (DoS) assaults, for example, can make networks unavailable, compromising the availability of essential functions for customers and partners. In a hyper-connected contemporary corporate world, ensuring continuous system uptime is critical. In fortitude to resist and neutralize DoS assaults, businesses must build strong defenses such as firewalls, anti-intrusion systems, and data distribution routers (Hashemi-Pour & Chai, 2023). Setting priorities for system performance allows organizations to provide a consistent consumer experience, increase consumer happiness, and strengthen their online systems against interruptions that might jeopardize service dependability and undermine investor confidence.
Creative Strategies for Minimizing Vulnerabilities
Behavioral Analytics
Employing behavioral analytics is a preemptive method for recognizing and minimizing possible insider risks in the digital corporate world. The novel technique entails constant tracking and evaluating user activity tendencies to discover abnormalities indicating fraudulent intent. Businesses may build standards for regular user conduct and detect anomalies quickly by utilizing modern technologies and data mining. Behavioral monitoring not only improves the identification of threat actors but also gives vital information about system safety (Berjawi et al., 2023). The technique enables firms to react quickly to suspected actions, lowering the chance of internal breaches while strengthening their entire cybersecurity position.
Blockchain Technology
Embracing Blockchain technology is a game-changing technique for improving the safety and integrity of internet-based company dealings and information. Blockchain provides a unique method to prevent illegal changes. Blockchain infrastructure protects important data by establishing an open and irrevocable transaction record. Such a strategy is needed in situations when the manipulation of data poses a considerable danger. Incorporating Blockchain into internet-based company settings builds confidence since each transaction is digitally registered and verified (Taherdoost & Madanchian, 2023). Such an autonomous model allows enterprises to reduce the danger of data tampering, resulting in a more safe and reliable digital environment.
AI-Powered Threat Detection
Deploying AI-Powered Warning Systems is a breakthrough technique for reinforcing digital corporate settings against increasing cyber-attacks. Companies may use machine learning and AI systems to examine big data instantaneously, discovering trends and anomalies that indicate possible intrusions. Such a proactive strategy improves monitoring capacity, enabling quick reactions to developing threats. AI-powered alerting streamlines detecting threats and adapts to the changing threat environment (IBM, 2023). Such technologies continually adapt to emerging information and evolve, equipping enterprises with durable protection against complex cyber threats and assuring continued protection of digital assets.
Conclusion
The digital age necessitates a planned and diligent strategy for navigating the complicated world of IT intrusions. Comprehending the risks in a digital company setting is critical for designing successful tactics to prevent different forms of intrusions. As organizations become more reliant on linked systems, preserving technological innovation is no longer an option; it is a need for long-term sustainability. Businesses may strengthen their digital horizons by resolving each of the weaknesses identified in this document and employing inventive tactics. Incorporating cutting-edge innovations such as Blockchain and AI-powered warning systems, along with a dedication to staff awareness and strong access controls, allows firms to effectively regulate and minimize the risks from a wide range of cyber-attacks. In an ever-changing digital context, firms that emphasize cybersecurity arise not simply as data defensive players, but also as builders of a robust safe digital economy.
References
AV-TEST. (2024). Malware statistics & trends report: AV-TEST. AV. https://www.av-test.org/en/statistics/malware/
Berjawi, O., Attar, A. E., Chbib, F., Khatoun, R., & Fahs, W. (2023). Cyberattack detection through behavior analysis of internet traffic. Procedia Computer Science, 224, 52–59. https://doi.org/10.1016/j.procs.2023.09.010
Hashemi-Pour, C., & Chai, W. (2023, December 21). What is the CIA triad?: Definition from TechTarget. WhatIs. https://www.techtarget.com/whatis/definition/Confidentiality-integrity-and-availability-CIA
IBM. (2023). IBM announces new AI-powered threat detection and response services. IBM Newsroom. https://newsroom.ibm.com/2023-10-05-IBM-Announces-New-AI-Powered-Threat-Detection-and-Response-Services
Jena, B. K. (2023, September 15). What is phishing attack in Cyber Security – Complete Guide. Simplilearn.com. https://www.simplilearn.com/tutorials/cryptography-tutorial/what-is-phishing-attack
Taherdoost, H., & Madanchian, M. (2023, March 21). Blockchain-based new business models: A systematic review. MDPI. https://doi.org/10.3390/electronics12061479
TechTarget. (2024, January 29). Top 10 types of information security threats for IT teams: TechTarget. Security. https://www.techtarget.com/searchsecurity/feature/Top-10-types-of-information-security-threats-for-IT-teams
 write
write