Overview
A network groups two or more computers linked to enable resource sharing. Numerous methods may be used to create connections, including satellite communication, cable networks, radio frequency transmission, infrared light-based communication, and conventional telephone lines. LANs and WANs are standard networks. Servers and workstations may operate in a computer network. Servers work continuously to provide services to other computers within a network. The services offered include software hosting, printing, file storage and sharing, faxing, data storage, and messaging, among other options. Workstations have interfaces that facilitate human users’ interaction with the network.
In contrast to servers, workstations necessitate the presence of user interface devices, including a display, keyboard, and mouse. Servers possess more excellent computational capabilities compared to workstations. The arrangement of computers in a network, known as network topology or architecture, refers to the specific manner in which they are interconnected. Nodes refer to network devices such as computers, printers, scanners, routers, and similar components. The primary classifications of network topologies encompass a ring, star, mesh, point-to-point, bus, and tree.
Purpose
A ring network is comprised of interconnected computers arranged in a circular configuration. In this particular topology, data exhibit unidirectional movement—every computer function as a conduit for transmitting signals within the network. The ring topology refers to a local area network (LAN) where the nodes are interconnected in a closed-loop configuration (Disha Experts, 2019). A ring topology is considered an optimal choice in a scenario characterized by dispersed workstations. The degradation of data speed can occur when there is a breakage in the cable infrastructure, which is interconnected with the network. Workstations can be detached in the event of multiple instances of a cable failure within a network.
Scope
The paper aims to offer a thorough review and analysis of the ring network architecture, including its features, benefits, drawbacks, and security issues. The essay starts by defining computer networks and explaining their function while emphasizing the numerous connection options and the services that workstations and servers provide. The discussion then turns to network topologies, particularly the ring topology, characterized as a ring-shaped arrangement of linked computers (Disha Experts, 2019). It is clarified how a ring network’s unidirectional data flow and suitable for a scattered workstation’s function. The possible effects of cable failures on network performance are discussed, highlighting workstations’ detachability in the event of repeated cable failures. The ring topology is briefly compared to various network topologies, including star and mesh, emphasizing their benefits and shortcomings. It highlights how simple it is to identify problems in a mesh network and how well ring topology handles large amounts of data transfer across great distances. Also highlighted is the ring topology’s drawback, which is that the failure of a single computer might impact the whole network.
The topic of the text’s second section is network security in ring topologies. It presents the idea of “defense-in-depth” and highlights the need to implement several security measures. These precautions include firewalls, anti-virus software, biometric passwords or verifications, and anti-spyware (Jang, 2022). The condition of system hardening to guard against data breaches and ongoing monitoring of specific network systems is emphasized throughout the article. The article explains ring network design, its pros and cons, and security mechanisms. It promotes network security and a comprehensive business data and asset protection plan.
Analysis and Synthesis of Ring Topology
The star network exhibits more excellent reliability compared to the ring network. The mesh network topology is considered more advantageous than the ring and star topologies, despite the potential drawback of redundancy that it may encounter. Diagnosing issues within a mesh network is straightforward due to the ease of identifying and locating faulty connections. In this network, every computer functions as a signal amplifier, rendering it a highly suitable topology for efficiently managing substantial data transmission across extensive distances (Jang, 2022). The ring topology’s biggest drawback is that adding or removing a computer affects the whole network. One computer failure may take down the network.
Figure 1: Ring network topology
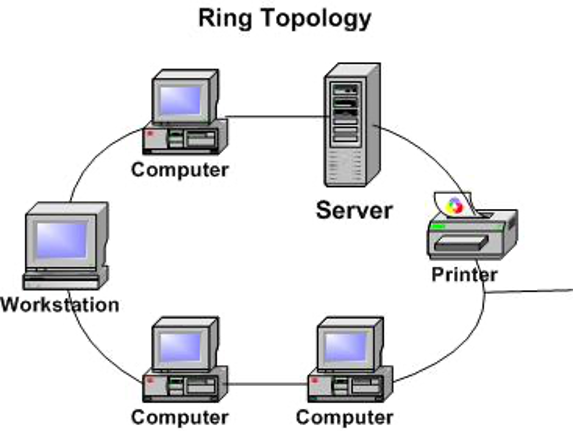
The connections between devices in a ring topology are arranged to establish a circular pathway for data transmission, as depicted in the provided diagram (Figure 1). Two devices link each node. Network nodes send data to their destinations. In most ring networks, data packets are restricted to unidirectional transmission. When a link breaks, this architecture disrupts the whole network. LANs and WANs may use ring topologies (WANs) (Koch, 2018). The selection of RJ-45 or coaxial cable for interconnecting nodes within a ring network is contingent upon the specific network card employed.
Encryption is a security measure that entails the utilization of cryptographic services at the transport layer of a network. The utilization of layers facilitates the process of routing and establishing connections with endpoints. IPS allows network data encryption. Nodes connect networks physically. Nodes need an IP address to be recognized by other network devices. The implementation of node security occurs at the endpoint during data transmission or at the point of distribution (Warner, 2019). Nodes must be constructed to recognize, analyze, and transmit data in a network.
Defense-in-depth involves strategically implementing many security measures to protect an institution’s data. The defense mechanism is fortified by implementing a sophisticated and intricate system. Ring networks may be secured using numerous countermeasures. These countermeasures include firewalls, anti-virus software, biometric verifications or passwords, and anti-spyware. System hardening prevents data breaches best. The process entails mitigating the risk of a potential attack by implementing measures such as revoking excessive permissions and deactivating superfluous services.
A defense-in-depth strategy is a comprehensive approach that effectively safeguards the security of a ring network. The network is secured through system hardening and continuous monitoring of each system. The preservation of information and assets within a company is of utmost importance, thus making network security a vital consideration (J. Michael Stewart & Kinsey, 2020). The primary objective of information security is to guarantee the preservation of availability, authentication, confidentiality, and integrity. Maintaining confidentiality is crucial in safeguarding against unauthorized individuals’ ability to duplicate, reproduce, or intercept sensitive information. Maintaining integrity is of utmost importance in guaranteeing that a company possesses a sense of trust in the precision of its data.
The concept of information security encompasses not only the implementation of protective measures but also the ability of organizations to retrieve data effectively. This is because the effectiveness of security measures is rendered futile if accessing necessary information for operational purposes becomes problematic. Authentication is an essential component that facilitates the establishment of secure information transmission within a network. The features encompassed within the realm of information security contain physical security, personnel management, the establishment and enforcement of procedures and policies, the creation of secure applications, and the fortification and surveillance of networks (Disha Experts, 2019). Information security encompasses a set of protocols and guidelines designed to safeguard information against potential threats from natural disasters, unforeseen incidents, and human errors. The policies and procedures should prioritize resolving diverse concerns, including data integrity, controls for all media, backup protocols, configuration controls, disaster recovery measures, and contingency planning.
Establishing a network facilitates effective communication and information exchange among computers and peripheral devices. Additional components augment a network’s efficiency, encompassing routers, hubs, cables, and switches (Disha Experts, 2019). The ring network possesses numerous advantages. Implementing a unidirectional data flow system decreases the likelihood of packet collisions. The management of the connection between the workstation does not necessitate the presence of a network server. The transmission of data between workstations takes place at elevated rates. The addition of extra workstations has a minimal impact on the performance of the network. The network possesses various limitations. If a single workstation experiences a shutdown, it significantly affects the entire network (Chapple & Seidl, 2020). The star topology is generally characterized by slower data transmission rates than other network topologies, as data must traverse through each node within the network. The ring topology is typically more cost-effective and simpler to implement than alternative network configurations.
Conclusion
The ring network architecture, with its linked nodes creating a circular channel for data transmission, provides a distinctive configuration for computer networks. The ring topology has benefited, such as adequate data transmission speeds and the capacity to manage massive volumes of data transfer across considerable distances, despite possible downsides, including the possibility of the whole network being disrupted by the loss of a single computer. The “defense-in-depth” strategy, which involves adopting several security measures, including firewalls, antivirus software, biometric verifications, and system hardening, is essential for network security. The necessity of data security and ongoing monitoring is highlighted by the need to preserve assets and information inside a corporation. Despite its drawbacks, the ring topology is still a feasible and affordable option for networks, providing dependable data transfer and scalability. Businesses should prioritize network security and thorough data protection to guarantee the accessibility, authentication, confidentiality, and integrity of information.
References
Chapple, M., & Seidl, D. (2020). CISSP Official (ISC)2 Practice Tests. John Wiley & Sons.
Disha Experts. (2019). Guide to LIC Assistant Prelim & Main Exam 2019 with 3 Online Tests. Disha Publications.
- Michael Stewart, & Kinsey, D. (2020). Network Security, Firewalls, and VPNs. Jones & Bartlett Learning.
Jang, M. H. (2022). Mastering Fedora Core 5. Wiley.
Kaur, G., Kaur, L., & Kaur, R. (2021). Elements and Digitization of Computer. Educreation Publishing.
Koch, C. (2018). Introduction to Information Technology. Scientific e-Resources.
Warner, S. (2019). Topological Rings. Elsevier.
 write
write