ABSTRACT
The digital forensics field has evolved over the years to allow proper examination of evidence to help determine what the accused might have done in the past. Despite the field’s emergence in the 1990s, it did not help much until the advancement of modern technology, which is changing the area rapidly. The application of blockchain technology in digital forensics has improved the provenance of digital evidence in cases. Block-enabled framework for the Internet of Things offers digital forensics with good immutability, authenticity, and traceability. The artificial Intelligence blockchain framework has made digital forensics more efficient. Two-level blockchain chain system has also proved efficient in managing digital crime evidence. Besides digital forensics, blockchain technology has improved in threat hunting, as shown in machine and deep learning, whereby the accuracy in detecting existing and new vulnerabilities has improved.
Keywords: Blockchain, Internet of Things, Artificial intelligence, machine learning, Deep learning, Escort, Ethereum
Introduction
Blockchain, among other new technologies, is highly applied in digital forensics and threat hunting. Blockchain technology can enable a comprehensive view of actions or transactions back to originations, making it an essential tool in forensics. Digital evidence is critical in cybercrime investigation by linking persons to the committed crime. Thus, it’s vital for investigating agencies to guarantee authenticity, integrity, and auditability of digital evidence during investigations or as the case proceeds in courts. Digital forensics is most common in the court of law, whereby the storage of criminal evidence is highly needed.
According to Ryu et al. (2019), digital forensics is a branch of scientific forensics used in identifying, processing, and analyzing data that is stored electronically. The goal of digital forensics is to preserve any evidence in original form through investigations by identifying and validating the information in digital form. The identification step includes finding evidence and noting where it is stored. The preservation step incorporates isolation, securing, and preserving the data. The analysis step includes reconstructing data fragmentation and drawing conclusions based on the evidence (Ryu et al., 2019). The next step is documentation, whereby all data records are created to recreate the crime scene. The last stage is presentation, whereby a summary and conclusion are made. This report shows how blockchain is leveraged for forensic applications to bring integrity and tamper proof in a digital forensic chain of custody. The report also focuses on blockchain technology applications in threat hunting.
Blockchain and Digital Forensics
The advancement in technology through the use of smartphones, the internet, and social media connects people and has a significant contribution to the daily life of individuals. However, cybercrime has become a global threat and needs technological solutions. Although there are laws to combat a crime, digital forensics is incorporated to determine what, who, where, and why questions about the crime committed (Ulybyshev et al., 2018). Emerging technologies such as the Internet of Things (IoT), social networks, and the fifth generation of communication (5G) have become part of modern life (Li et al., 2019). The technologies are making life easier, fun, and easier to have information at your fingertips. Due to the nature of the IoT environment, forensic investigation and digital evidence are needed to identify and mitigate criminal activities within the system.
Blockchain-based IoT forensic framework is critical for forensic investigation in the IoT environment. The framework provides full data provenance architecture and assurance in evaluating all the operations (Lone et al., 2018). The system can also provide security availability and privacy, traceability, and transparency. The framework popularly known as the IoT Forensic Chain (IoTFC) is valued in digital forensics. IoTFC is critical for the comprehensive view of the evidence items. The decentralized ledger system provides a comprehensive view of the evidence items and can show links and sources. Decentralization is critical in many investigation scenarios where many evidence activities and sources are needed. According to Li et al. (2019), blockchain within the IoT chain framework provides distributed trust to all the individuals in the investigation process.
Attaining continuous integrity in digital forensic remains challenging in the investigation processes. Data breaches have increased in the IoT systems due to the unstable evidence systems whereby critical information is compromised or lost. Managing the integrity of such evidence requires the blockchain-based IoT forensic framework. Cryptographic hash functions such as SHA 256 are commonly used in forensic imaging but are insufficient. Due to the nature of cyber activities, there is a need for continuous integrity checks that should be achieved through the IoTCF (Li et al., 2019). The blockchain framework is also critical for providing a tamperproof environment that ensures that the evidence collected is secured. The evidence items within the blockchain are also shared with all the participants. The chained evidence items in the blockchain cannot the tampered with in the system. The nature of blockchain technology is also significant in the provision of immutability and auditability, which are critical components in the forensic chain of evidence.
The other aspects of blockchain application in IoT systems are attaining traceability and full provenance. Although traceability offered by blockchain has attracted some criticism by being regarded as an encryption solution and potential privacy issue, blockchain application in IoT is more comprehensive. The IoTCF can monitor anomalies and provide effective traceability from scene to court and along all the chains to restrict the access of all the provided information (Li et al., 2019). Generally, IoTCF improves the existing digital forensics in three aspects: reducing examination costs and resources, establishing connections with third parties, and improving the profitability of the process. The figure below is block enabled forensic network in the Internet of Things showing evidence management from collection to prosecution through IoTCF.
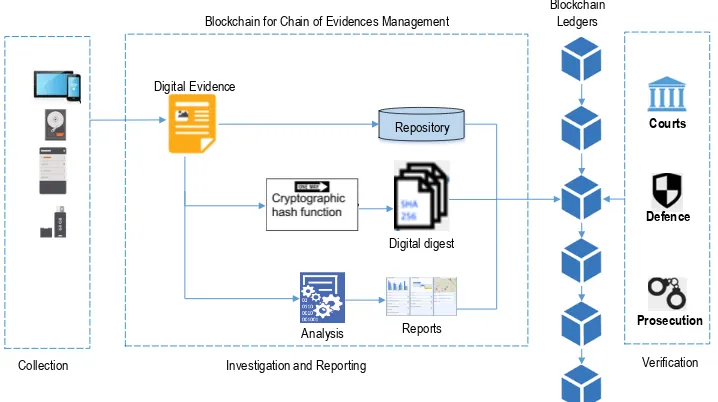
Figure 1: Blockchain-enabled forensic network in the Internet of Things
Source (Li et al., 2019).
Artificial intelligence (AI) and blockchain frameworks make the digital forensic process more efficient. Applying blockchain digital forensics in AI is essential in finance, logistics, health, supply chain, and government. The linkage between forensic blockchain and AI helps in filtering and managing cases. Blockchain-AI conversion takes several steps for the system to become fully operational. Evidence is presented in the blockchain, and then the blockchains endure data interchange and tokenization. As such processes occur, the AI monitors them in an advanced manner whereby AI specifications are, and intelligence calculations exchange sources within the tech stack. The figure below shows how AI and blockchain are linked to achieve proper digital forensics.
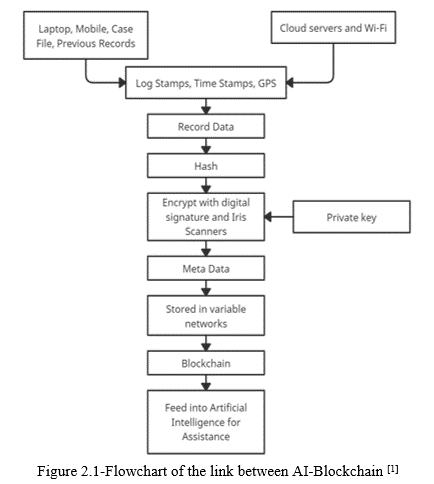
Figure 2: AI-Blockchain flowchart
Source: (Shrunga, 2022)
Through the application of AI-blockchain in digital forensics, Zhang et al. (2017) developed a process provenance that influences blockchain and cryptographic group signature technologies to provide privacy preservation and adequate evidence on the kept records. Zhang et al. (2017) state that process provenance integrates blockchain and cryptographic group signature methods to offer evidence of the existence and privacy protection of the records. The critical processes of the process provenance are the submission list, receiver, sender, provenance auditor, and certificate authority. A submission list captures the signatures of the senders and receivers. The receiver is the investigator who appeals for information from the cloud forensics fulfilled by the sender (Shrunga et al., 2022). The sender is the investigator responsible for gathering and distributing forensics information to the recipient. The sender is also responsible for sending the data to the provenance auditor after the receiver authenticates the submission. The provenance auditor obtains process records from the senders. After gathering a good number of records, the provenance auditor embeds the records in a blockchain network. The certificate authority officer is in charge of the group signature system. The figure below shows a systems overview of blockchain forensics in Artificial intelligence showing the link between the receiver, sender, blockchain and forensic auditor.
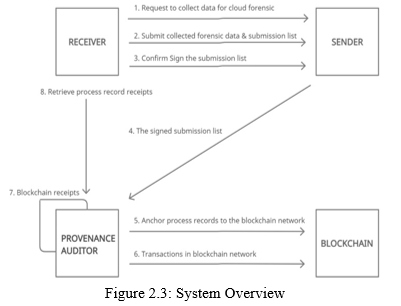
Figure 3: Systems Overview
Source: (Shrunga et al., 2022)
The application of blockchain technology in digital technology also occurs through a two-level blockchain system utilized in digital crime evidence management. Kim et al. (2021) proposed the system and demonstrated its significance in the integrity of digital crime evidence. Only authorized persons have access to cold and hot blockchains through the developed system. The two-level blockchain system stores the identity information, investigations, and evidence of digital crime videos through on-site investigators with verified identities. Although the system exhibits some limitations in applying it to different systems in general, it shows an improvement in the integrity of evidence in digital forensics. The figure below shows the two-level blockchain system’s design and how it protects digital evidence during an investigation process.
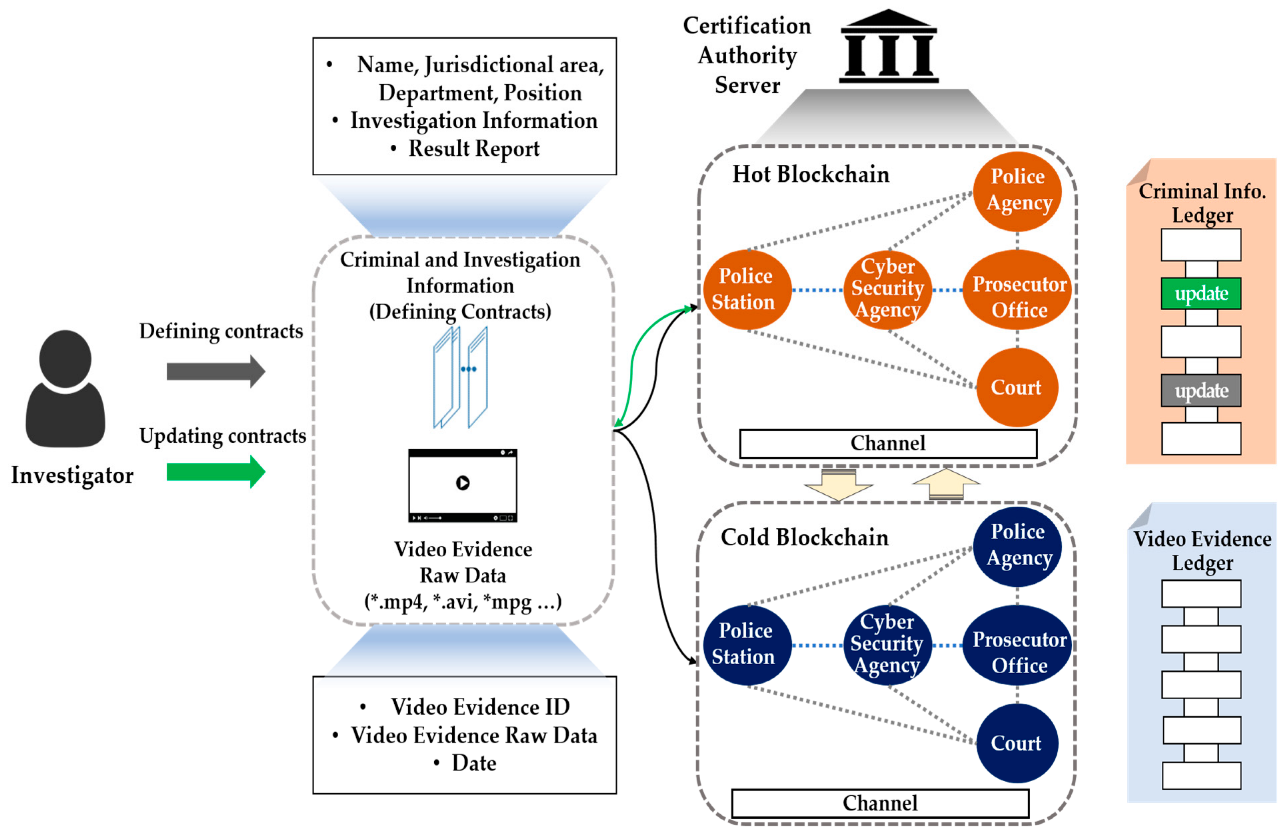
Figure 4: Two-level blockchain system’s design
Source; (Kim et al., 2021)
However, applying blockchain technology in digital forensics does not always guarantee a successful process. According to Ricci et al. (2019), challenges undermine blockchain-based distributed storage forensics, such as extracting files and metadata, which is vital in prosecution. An example is STORJ, a new blockchain service in digital forensics whereby the investigators must understand the suitable methodology for collecting digital evidence to avoid compromising the case outcome.
Blockchain technology in threat hunting
Blockchain technology builds trust and enhances cyber security across networks and systems. However, in the contemporary world, cyber security appears vague due to fragmentation of networks and the existence of private and public clouds, making the achievement of cyber security efficiency challenging. The widespread application of blockchain technology in finance and currency exchange applications has increased security and trustworthiness. Despite the security, the technology is not immune to security threats. An open source and decentralized blockchain technology called Ethereum has shown high growth and is widespread. The technology is widely used in cryptocurrency but is still vulnerable and has several security risks. The use of machine learning algorithms through analyzing the behavioral patterns within Ethereum helps achieve insights for threat hunting.
Rabieinejad (2021) proposed a deep learning model for Ethereum in threat hunting and examined the model’s performance, whereby the performance evolution in terms of accuracy was 97.72% in attack detection while the attack classification was at 99.4%. The safety of Ethereum cryptocurrency requires proper security to minimize vulnerabilities and risks. The Escort helps in threat hunting through its vulnerability detection components, feature extraction of general smart contracts, and each specific vulnerability class. The other component is disentangling the two subtasks; extraction of smart contracts and vulnerability class. The Escort has shown to be more reliable in terms of efficiency and scalability. As demonstrated by Lutz et al. (2021) in Ethereum, the results of threat hunting by Escort indicated an average accuracy detection rate of 95% regarding the F1 scores across the vulnerability classes. The study also showed that when given an unknown smart contract, ESCORT can detect eight vulnerabilities in 0.02 seconds.
Escort-based machine learning was developed to overcome scalability and generalization limitations in blockchain cryptocurrencies. The escort is a deep neural network (DNN) based vulnerability detection framework. Experiments conducted through the network demonstrate that it’s a vital framework of machine learning that is significant in threat hunting. The comprehensive evaluation of Escort in smart contracts, as done by Lutz et al. (2021), shows that it has high accuracy levels in detecting vulnerabilities compared to the other machine learning frameworks. Escort indicated an average F1 score of 93% when used on the new vulnerability types. DNN-based vulnerability detection is widely used in cryptocurrencies, logistic companies, and governments to detect new vulnerabilities.
Other than Escort, models in blockchain technology have proved to be appropriate for threat hunting. Machine learning techniques such as contract ward, LSTM-based, AWD-LSTM-based, CNN-based, and GNN based have been used to perform automatic contract scanning. Contract-Ward detects vulnerabilities in smart contracts at the opcode level by removing bigram features from the simplified opcode and training individual binary ML classifiers for each vulnerability class (Lutz et al., 2021). However, the model exhibits some limitations, such as being not extensible to new limitation attacks, not scalable to new contracts, and requiring code for the smart contracts. LSTM-based machine learning utilizes a sequence learning approach to detect vulnerabilities in smart contracts. The code vectors obtained through the model help determine whether the smart contracts are safe or vulnerable to cyber threats. However, LSTM-based machine learning recorded a low vulnerability detection of 86%, as shown in the F1 score (Elmrabit et al., 2020).
The Convolutional neural networks (CNN-based machine learning transforms the contract bytecode into RGB color images for vulnerability detection. Like Escort, CNN-based machine learning uses a multiple-label classification, indicating low confidence when determining types of vulnerabilities. Although CNN-based machine learning is critical, it also exhibits some limitations, such as low confidence. Neutral graph networks (GNN) based machine learning focuses on multi-class detection of vulnerabilities. However, when compared to the Escort, the GNN-based machine learning also demonstrates a low F1 score (Lutz et al., 2021).
Conclusion
The application of blockchain technology has greatly improved digital forensics. The advantage of blockchain technology in digital forensics is that the investigator can self-verify the digital evidence through the hash function to create a verifiable evidence chain. Blockchain technology is successfully applied in digital forensics through IoT forensic chain, AI blockchain in digital forensics, and a two-level blockchain system for evidence management in digital crime.
Automated detection of software vulnerabilities remains a critical problem in software security. Existing programs for vulnerability detection suffer from faulty detection mechanisms. The traditional techniques that have been relied upon over the decades have shown high false positives and negatives, hence becoming unreliable. The static analysis-based tools have proved unreliable in threat hunting due to high false positives that tend to show the existence of vulnerability when it is not there. Although several recent studies, like the one on Escort, depict a promising result of achieving a 95% accuracy in detecting automatic vulnerabilities, such progress in deep learning is not widely achieved.
References
Elmrabit, N., Zhou, F., Li, F., & Zhou, H. (2020). Evaluation of machine learning algorithms for anomaly detection. In 2020 international conference on cyber security and protection of digital services (cyber security) (pp. 1-8). IEEE.
Kim, D., Ihm, S. Y., & Son, Y. (2021). A two-level blockchain system for digital crime evidence management. Sensors, 21(9), 3051.
Li, S., Qin, T., & Min, G. (2019). Blockchain-based digital forensics investigation framework in the internet of things and social systems. IEEE Transactions on Computational Social Systems, 6(6), 1433-1441.
Lone, A. H., & Mir, R. N. (2018). Forensic-chain: Ethereum blockchain-based digital forensics chain of custody. Scientific and Practical Cyber Security Journal. 1 (1), 21-27.
Lutz, O., Chen, H., Fereidooni, H., Sendner, C., Dmitrienko, A., Sadeghi, A. R., & Koushanfar, F. (2021). ESCORT: Ethereum smart contracts vulnerability detection using deep neural network and transfer learning. arXiv preprint arXiv:2103.12607.
Rabieinejad, E., Yazdinejad, A., & Parizi, R. M. (2021). A deep learning model for threat hunting in Ethereum blockchain. In 2021 IEEE 20th International Conference on Trust, Security, and Privacy in Computing and Communications (TrustCom) (pp. 1185-1190). IEEE.
Ricci, J., Baggili, I., & Breitinger, F. (2019). Blockchain-Based Distributed Cloud Storage Digital Forensics: Where’s the Beef? IEEE Security & Privacy, 17(1), 34-42.
Ryu, J. H., Sharma, P. K., Jo, J. H., & Park, J. H. (2019). A blockchain-based decentralized efficient investigation framework for IoT digital forensics. The Journal of Supercomputing, 75(8), 4372-4387.
Shrunga et al. (2022). A survey on blockchain-based digital forensics framework. https://doi.org/10.22214/ijraset.2022.41841
Ulybyshev, D., Villarreal-Vasquez, M., Bhargava, B., Mani, G., Seaberg, S., Conoval, P., & Kobes, J. (2018). (WIP) blockhub: Blockchain-based software development system for untrusted environments. In 2018 IEEE 11th International Conference on Cloud Computing (CLOUD) (pp. 582-585). IEEE.
Zhang, Y., Wu, S., Jin, B., & Du, J. (2017). A blockchain-based process provenance for cloud forensics. In 2017 3rd IEEE international conference on computer and communications (ICCC) (pp. 2470-2473). IEEE
 write
write