Introduction
This report conducts a horizon scan of Softwire, an independent software development company based in Manchester, London, and Cambridge, UK. The firm delivers high-quality and innovative software solutions to its customers, such as Google deep mind and BBC. Horizon scanning aims to identify and analyze threats facing a company by reviewing underlying trends and solutions. After identifying major threats, a company can formulate mitigation measures that will increase the firm’s resilience and its ability to resume normal operation levels after a major threat. The report will use the ISO definitions of risk and threat as discussed in Appendix A. The report will provide a short review of Softwire limited and major services; further, it will describe threats and risks.
Company Overview
Softwire is a private UK-based software company that operates in Bristol, Manchester, and Cambridge. The company operates as part of the Computer systems design sector and has over 50 employees in three locations, with 30 percent of the workers being corporate leaders. It generates more than $ 26 billion in sales each year. The company provides exceptional services to its customers; its commitment to client satisfaction makes it a prominent market leader in software development and distribution.
The privately-owned company began its operations in 2000 with its headquarters in London. Today, it has over 500 workers and specializes in project rescue, custom software, Microsoft gold partners, and legacy migration. Other functions include software consultancy and mobile and application development. The wide range of Softwire products and services means that it is the leading brand in the digital sector. Softwire is a complete software partner for its clients from the design to the development and implementation stages. It manages the client’s projects from their initial stages to completion (Amershi et al., 2019). Also, they provide a one-stop-shop to its clients with “big” projects through their agreements with third parties such as ISPs, and web designers. The company’s project managers are capable and proactive in ensuring that the project runs smoothly and efficiently to provide excellent software solutions at relatively low costs.
Threats and Risk Analysis
The company’s relatively small size means that it has minimal financial resilience; its ability to withstand and bounce back from life events that affect its revenues is small. For instance, Softwire is much more susceptible to bankruptcy after disruption of their software development processes; for instance, shutting down of meta switch – their cloud-based messaging platform leads to a loss of millions in revenues. Therefore, good management skills are crucial. According to Lohr (2018), good management is essential for running a successful company. Managers supervise the company and make vital decisions that influence the company’s productivity. On the other hand, employers must understand the characteristics of good managers – this helps them recognize their duties in running the company.
Softwire products and services show that the company depends on information technology for production and logistics. Developing mobile apps and competing with the customer’s projects includes DevOps, clouds, artificial intelligence, machine learning, and data engineering protocols (Rigby et al., 2018). When you combine these services with their e-commerce system that compiles codes, the company is subject to cyber-attacks, poor management, and technical difficulties. The use of codes, artificial intelligence, and cloud servers means that the company can have technical difficulties, particularly when the system fails. Another threat is poor management – it involves making wrong estimates in coding, poor management of workers, and budget estimates. The situation threatens a company’s profitability and productivity (Sievi-Korte et al., 2019). In some cases, Softwire collaborates with its technical partners to complete certain projects – technical difficulties can affect the client’s project completion leading to the failure of projects.
Threat 1: Cyberattacks
Softwire is a private software development company based in London. The company specializes in delivering application consultancy and bespoke services, expert software development training, and custom-built software solutions. Therefore, the company is vulnerable to cyber security threats such as malware, phishing, and denial of service. According to Check Point Research, cyber-attacks contributed to 50 percent of the total attacks on SMEs and multinational businesses. The report also shows that attackers target small companies due to their lack of intelligent systems and financial resources. The most common cyber-attacks are malware. Lohr (2018) defines malware as files sent over a network or database that infects and virtually leak private information. It also gains unauthorized access to data and distorts the information – this hampers the company’s processes. When a user clicks the malware software, it blocks access to important network components, damaging projects and the failure of artificially intelligent systems.
Ringer et al. (2019) argue that malware attacks can occur in two ways; to install harmful software that steals crucial information and installing a malicious application that disrupts software development processes. Softwire relies on information technology for operational and logistical purposes to develop software; the application process includes five stages, research, idea process, design, implementation, and iteration. The five elements help programmers to answer questions of “who, how, where, when, and what .”A point of sale (POS) system to store sensitive client data makes the company a target for potential hackers. This data loss could lead to huge fines and loss of software codes (Rigby et al. (2018).
According to Khan et al. (2020), cyber-attack severity and frequency have increased significantly since 2019. The report shows that hackers targeted small companies with less than 100 employees. The mean cost of SMEs attacks in 2019 was $ 3.86 million, and it rose to $ 4.24 million in 2020 (Lohr, 2018). The statistics indicate that medium-sized enterprises do not install high-cost anti-virus and protection software. Softwire uses heavy infrastructure and complicated software to protect its systems; for instance, it uses encryption soft wares to secure cloud servers and the message transfer platform.
Figure 1: Cyber-attacks since 2009
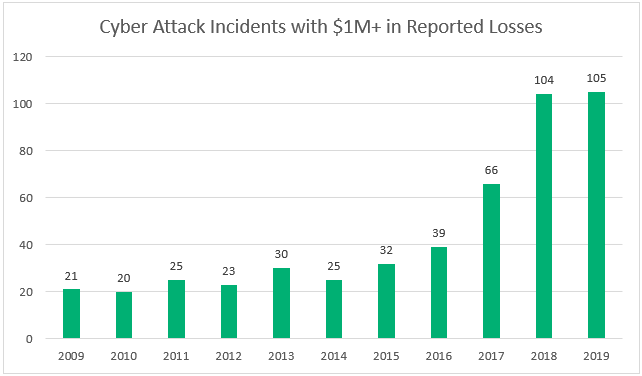
Source: Khan et al., 2020
Threat 2: Poor Management
According to Miciuła et al. (2020), poor management influences all aspects of life, particularly the employee-employer interaction. It plays a prominent role in leading to poor productivity, poor morale, and work-related stress. For instance, many people would neglect well-paid jobs and take lower positions in other companies because of poor management. Linkov et al. (2019) showed that 54 percent of small companies failed due to poor management. Senior executives failed in decision-making and imposed unnecessary levies that demotivated employees. The “dictatorship” employers did not give proper instructions leading to poor codes and failure of cloud projects (Lohr, 2018). The situation leaves employees trying to decipher what their boss needs, creating hatred and conflict.
Poor management emanates from poor time management. Managers that cannot regulate their time well by planning their activities in a schedule are ineffective. Kohtamäki et al. (2019) argue that time is a resource; supervisors should plan their activities well. Softwire is mainly engaged in software development; 95 percent of its production process would stop if the company fails to meet customer deadlines. Losing the crucial clientele may also lead to high losses since the company’s business model involves offering services to the established client base. Therefore, poor management is a threat, and Softwire executives should plan for it.
Poor management also originates from poor communication. Communication involves conveying and consigning messages to create a mutual understanding between company executives and their programmers. The hierarchical chain of command in Softwire creates good communication lines and channels between top executives and people at the bottom. An example of poor management is BHS which failed due to mismanagement. Despite its early success in 2009, the company failed in 2016, putting 11,000 jobs at risk and incurring a debt of $ 1.3 billion in the process (Khan et al., 2020).
Poor communication and issuing of instructions hamper product development. Sending the unintended message and linguistic barriers prevent the company from achieving its vision and goals. Though people can manage poor communication, proper management is key since 54 percent of leadership teams lack management training leading to disruption of the production process and severe losses (Hein et al., 2020).
Threat 3: Technical Difficulties
Technical risks are major threats to software development companies (Gupta et al., 2020). They arise when a part of the developer’s team is unfamiliar with the software requirements. In most cases, they emanate from numerous changes in the requirements of a project. If a client constantly alters software requirements, this creates confusion for programmers who constantly change the code. Another cause of technical difficulties is the complexity of the project. When a client asks for complex projects, the developers face challenges fulfilling the client’s requirements. However, proper preparation and training help mitigate this technical risk.
In some cases, software developers lower the functionality of an application to compensate for overruns in the scheduling and high budgets. Dönmez and Grote (2018) argue that there is a conflict between peak performance and attaining maximum functionality of a program. Most programmers prioritize peak performance rather than its operability to save on costs. For instance, Softwire may increase the efficiency of the SMS platform while reducing its reliability – this is dangerous since the app security is low, and the software development cycle is compromised. The technical risks are a threat to the company, and therefore Softwire should plan how to mitigate them (Dingsøyr et al., 2018).
Beecham et al. (2021) study indicate that 32 percent of all software fails due to technical difficulties; the technical risks are mainly performance-based or functional. The risks affect the functionality of the software and the performance of cloud servers. At Softwire, technical risks affect data security, software integration, compliance, and large-system implementation. Identifying technical risks in the application development process allows the company to be ready, monitor the threat, and remedy it before calamities occur (Baldassarre et al., 2020).
Conclusion
Softwire is one of the leading software development companies in London, the UK, with estimated gross revenue of 32 billion. The company started in 2000 and currently offers custom software development, consultancy, and cloud services. The main threats facing Softwire are cyber-attacks, poor management, and technical difficulties. The company must undertake mitigation measures and plan how to counter the threats and ensure business continuity. Amershi et al. (2019) show that demonstrating continuity attracts potential customers, reduces monetary losses, and attracts investors. In the future, Softwire should obtain accreditation from management systems standards ISO 9001 to act as their checklist when engaging in software maintenance, supply, and development. Softwire should also uphold quality management systems standards (QMS) to ensure accurate planning, documentation, and configuration of their software products.
Appendix A
ISO definition of a threat
The threat is “a potential cause of an incident, that may result in harm of systems and organization” (ISO 20000: 2018)
References
Amershi, S., Begel, A., Bird, C., DeLine, R., Gall, H., Kamar, E., & Zimmermann, T. (2019, May). Software engineering for machine learning: A case study. In 2019 IEEE/ACM 41st International Conference on Software Engineering: Software Engineering in Practice (ICSE-SEIP) (pp. 291-300). IEEE.
Baldassarre, M. T., Barletta, V. S., Caivano, D., & Scalera, M. (2020). Integrating security and privacy in software development. Software Quality Journal, 28(3), 987-1018.
Beecham, S., Clear, T., Lal, R., & Noll, J. (2021). Do scaling agile frameworks address global software development risks? An empirical study. Journal of Systems and Software, 171, 110823.
Dingsøyr, T., Moe, N. B., Fægri, T. E., & Seim, E. A. (2018). Exploring software development at the very large-scale: a revelatory case study and research agenda for agile method adaptation. Empirical Software Engineering, 23(1), 490-520.
Dönmez, D., & Grote, G. (2018). Two sides of the same coin–how agile software development teams approach uncertainty as threats and opportunities. Information and Software Technology, 93, 94-111.
Gupta, V., Fernandez-Crehuet, J. M., & Hanne, T. (2020). Freelancers in the software development process: a systematic mapping study. Processes, 8(10), 1215.
Hein, A., Schreieck, M., Riasanow, T., Setzke, D. S., Wiesche, M., Böhm, M., & Krcmar, H. (2020). Digital platform ecosystems. Electronic Markets, 30(1), 87-98.
Khan, L. U., Pandey, S. R., Tran, N. H., Saad, W., Han, Z., Nguyen, M. N., & Hong, C. S. (2020). Federated learning for edge networks: Resource optimization and incentive mechanism. IEEE Communications Magazine, 58(10), 88-93.
Kohtamäki, M., Parida, V., Oghazi, P., Gebauer, H., & Baines, T. (2019). Digital servitization business models in ecosystems: A theory of the firm. Journal of Business Research, 104, 380-392.
Linkov, I., Baiardi, F., Florin, M. V., Greer, S., Lambert, J. H., Pollock, M., & Trump, B. D. (2019). Applying resilience to hybrid threats. IEEE Security & Privacy, 17(5), 78-83.
Lohr, S. (2018). Facial recognition is accurate if you’re a white guy. In Ethics of Data and Analytics (pp. 143-147). Auerbach Publications.
Miciuła, K., Miciuła, I., Kabus, J., & Piersiala, L. (2020). Sources of threats and methods of securing information in companies in Poland compared to other EU countries. Procedia Computer Science, 176, 2969-2978.
Rigby, D. K., Sutherland, J., & Noble, A. (2018). Agile at scale. Harvard Business Review, 96(3), 88-96.
Ringer, T., Palmskog, K., Sergey, I., Gligoric, M., & Tatlock, Z. (2019). QED at large: A survey of engineering of formally verified software. Foundations and Trends® in Programming Languages, 5(2-3), 102-281.
Sievi-Korte, O., Richardson, I., & Beecham, S. (2019). Software architecture design in global software development: An empirical study. Journal of Systems and Software, 158, 110400.
 write
write