Programming tasks Report
Through programming, several lessons are learned through the use of the assigned tasks and programming tools. Firstly, verifying the credit card numbers helps determine if the credit card number is valid. The coding accepts the 16 digit string, and then after running the numbers, the program should determine whether they are valid, and thus the clients consider updating them. The process applies to financial institutions which contain personal data and financial status. Thus, keeping the cards updated to avoid a personal data breach is applicable.
For instance, in the validation of the numbers, if doubling the numbers produces the sum greater than numbers such as nine, then the nine should be subtracted from the summation to get a single digit (Tanikella, 2020). Taking the totality of the digits, if the sum can be divided by ten, the results indicate that the card numbers are valid. The credit card validation thorough check-up is helpful for security since the auditors can know that they are not exposing the clients to breaches of their information. The use of regular information can help the management to catch up with the numbers. If they are invalid, the service providers can use JavaScript to check the validity of the cards instantly without making the clients wait for so long.
In the application of the BCH coding, they form the cyclic error codes to correct errors, and they are constructed using polynomials under the finite field. BCH coding contains a feature that is useful for precise control of the numbers in the symbol errors, and they are correctable using the codes. Therefore, BCH coding can be applied to correct two-bit errors in a problem (Walters & Roy 2020). The decoding of the BCH coding is accessible through the processes such as algebraic system decoding, which simplifies the designing and decoding of these codes through the use of power electronic hardware. For the BCG coding for the digit for ten to six generators, they identify the unusable numbers, and thus using the corrector, both single and doubled must correct errors. In this case, more than two errors must be detected and corrected.
The brute force password cracker used THC-Hydra cracker to identify any vulnerabilities in the client’s system. The process runs over millions of passwords, and thus it is an attack above 50 protocols and several operating systems (Tirado et al., 2018). The identification of the password by the Brute force is the simple passwords which are used by the majority of the people; on the chart below, the brute force identified the following weak password used by the majority of the people, such as “123456” 1234567890″ “password,” “12345678”, “123”, 1q2w3e4r” and “12′. In addition, the analysis identifies the passwords that contain a maximum of the six lower letters or numbers and the particular case where the passwords contain BCH (16, 6) codes.
From the analysis, it is clear that organizations should use strong passwords that are free from brute force attacks on online platforms by using passwords that contain many characters and then avoid using the typical number and letters patterns such as “:12334….9”.

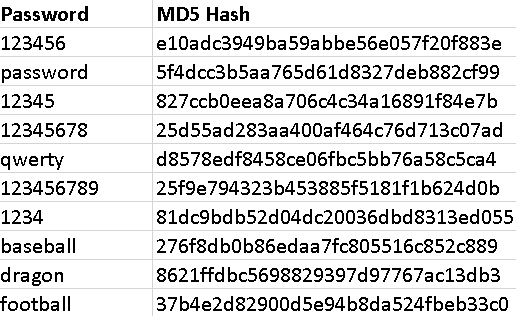
Through the rainbow tables to crack passwords, the table works through the principle such as trading on the time memory of the electronic device. Therefore, this indicates that the rainbow table pre-generates the computer-generated hashes and stores them together. The study by Trieu & Yang (2018) holds that this process is primarily applicable to users with slow computer processors since they do not have much time for computation. The rainbow table reduces the time needed to crack passwords since the user can save the tables and then generate all of them once. In an attempt to crack the database that contains the MD5 hashes and detect the commonly used passwords, It is observed that comparing the table with known inputs and the outputs with a bench of the unknown outputs. The analysis of the results of the matches is found, and then the passwords are displayed as shown below. The table below clearly shows that the standard used passwords are detected mainly by the rainbow table, such as ‘123456’, ‘password,’ ‘12345’,’12345678’, and others as indicated in the table below. These results indicate that people mostly tend to use the passwords following the easy patterns in the computers to remember them quickly, but this leads to vulnerabilities for the leakage of passwords by the passwords crackers. From the observation, people should avoid using patterned passwords on personal data tools to avoid losing the data to the computer crackers.
REFERENCE
Tanikella, U. (2020). Credit Card Approval Verification Model (Doctoral dissertation, California State University San Marcos).
Walters, M., & Roy, S. S. (2020, October). Constant-time BCH error-correcting code. In 2020 IEEE International Symposium on Circuits and Systems (ISCAS) (pp. 1-5). IEEE.
Tirado, E., Turpin, B., Beltz, C., Roshon, P., Judge, R., & Gagneja, K. (2018, July). A new distributed brute-force password cracking technique. In International conference on future network systems and security (pp. 117-127). Springer, Cham.
Trieu, K., & Yang, Y. (2018). Artificial intelligence-based password brute force attacks. Proc. MWAIS, 39.
 write
write